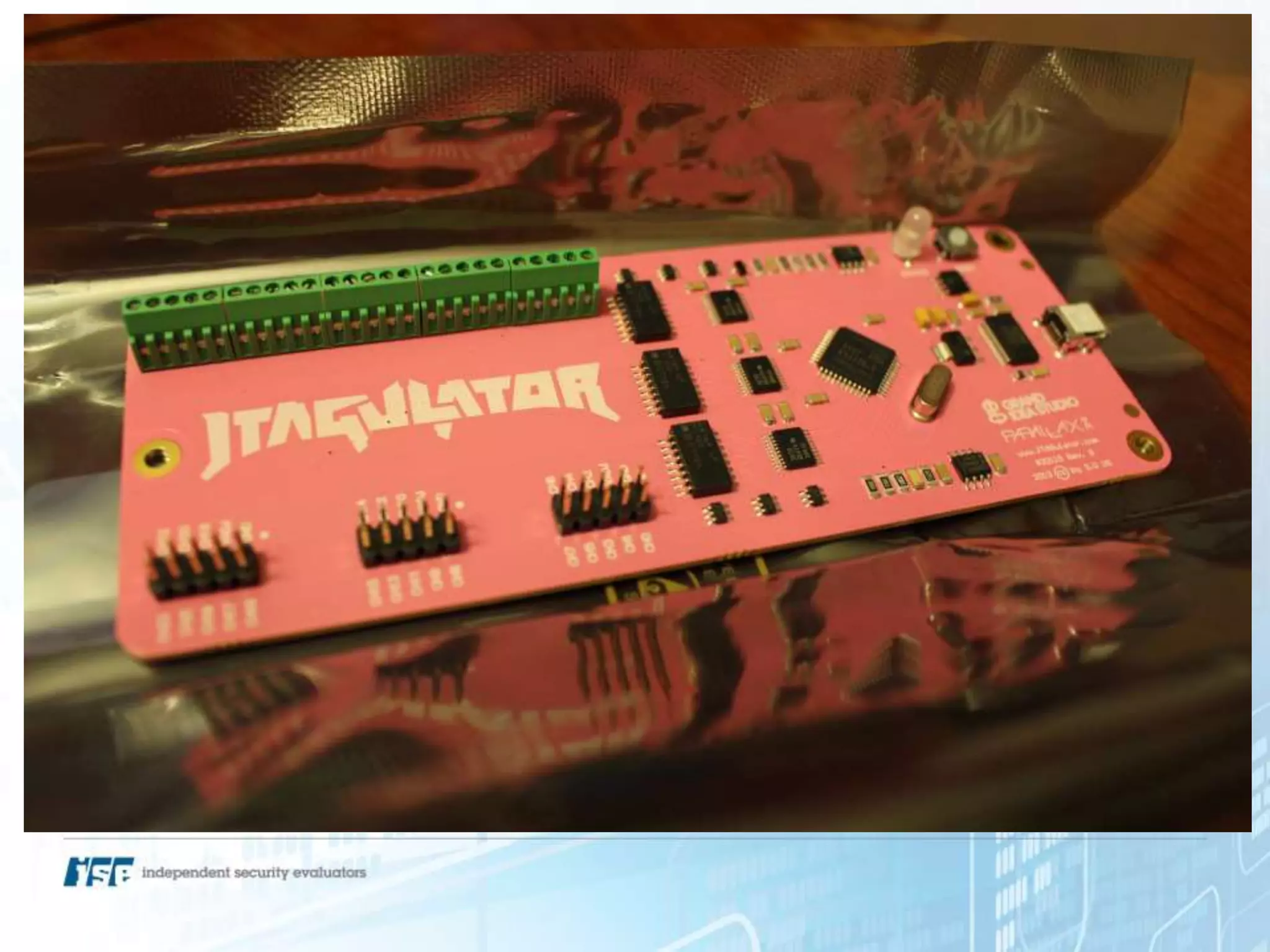
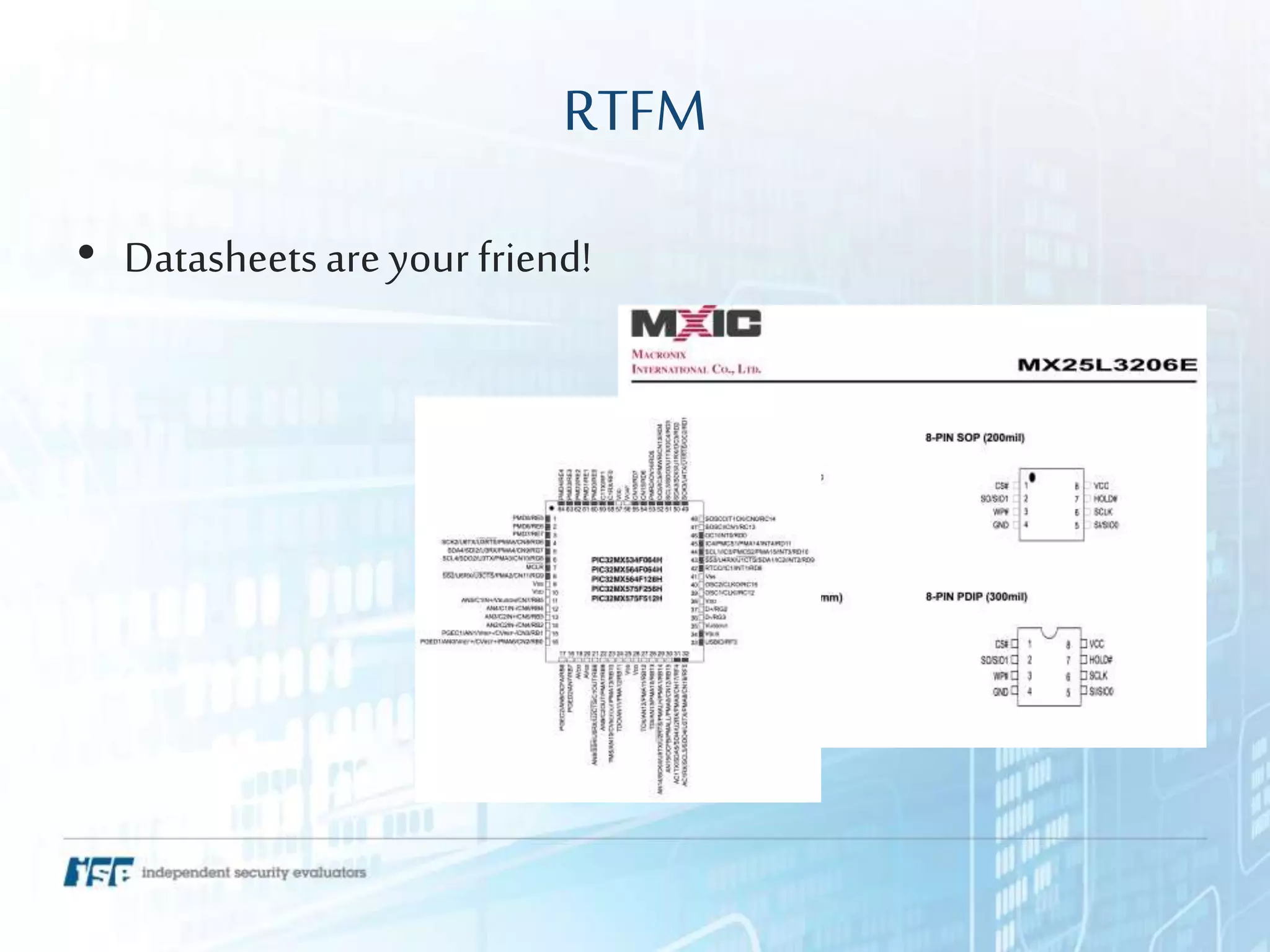
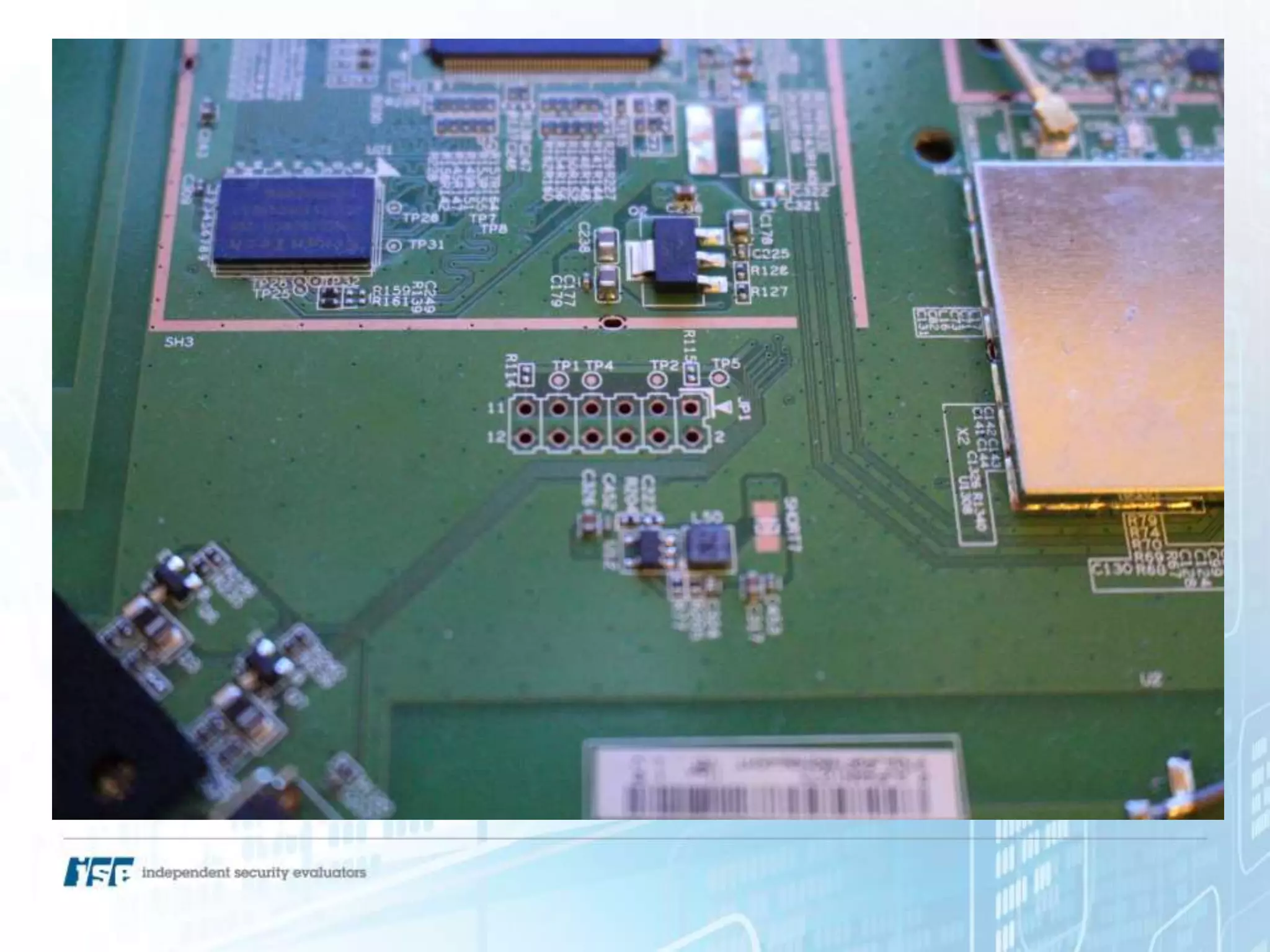
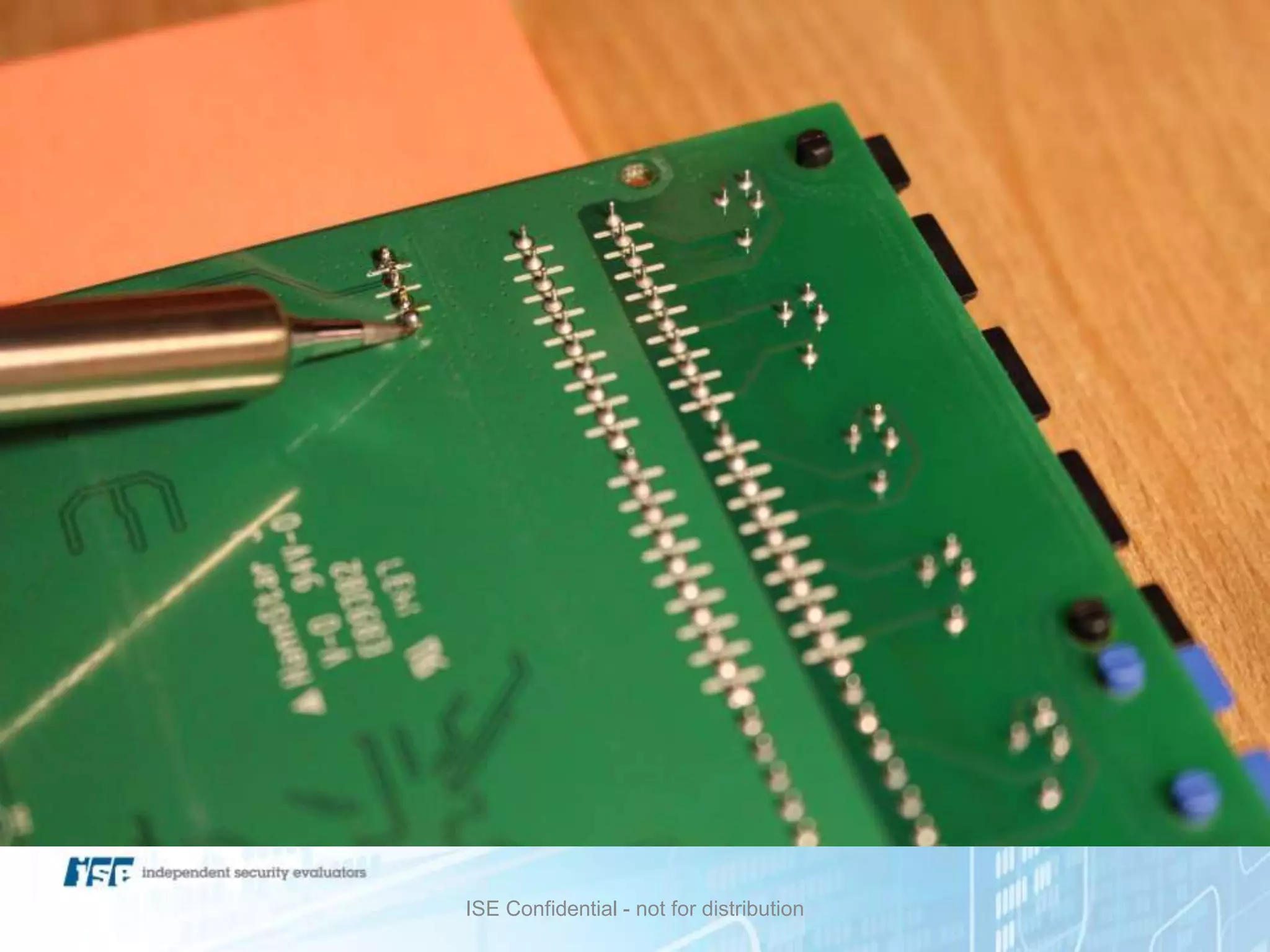
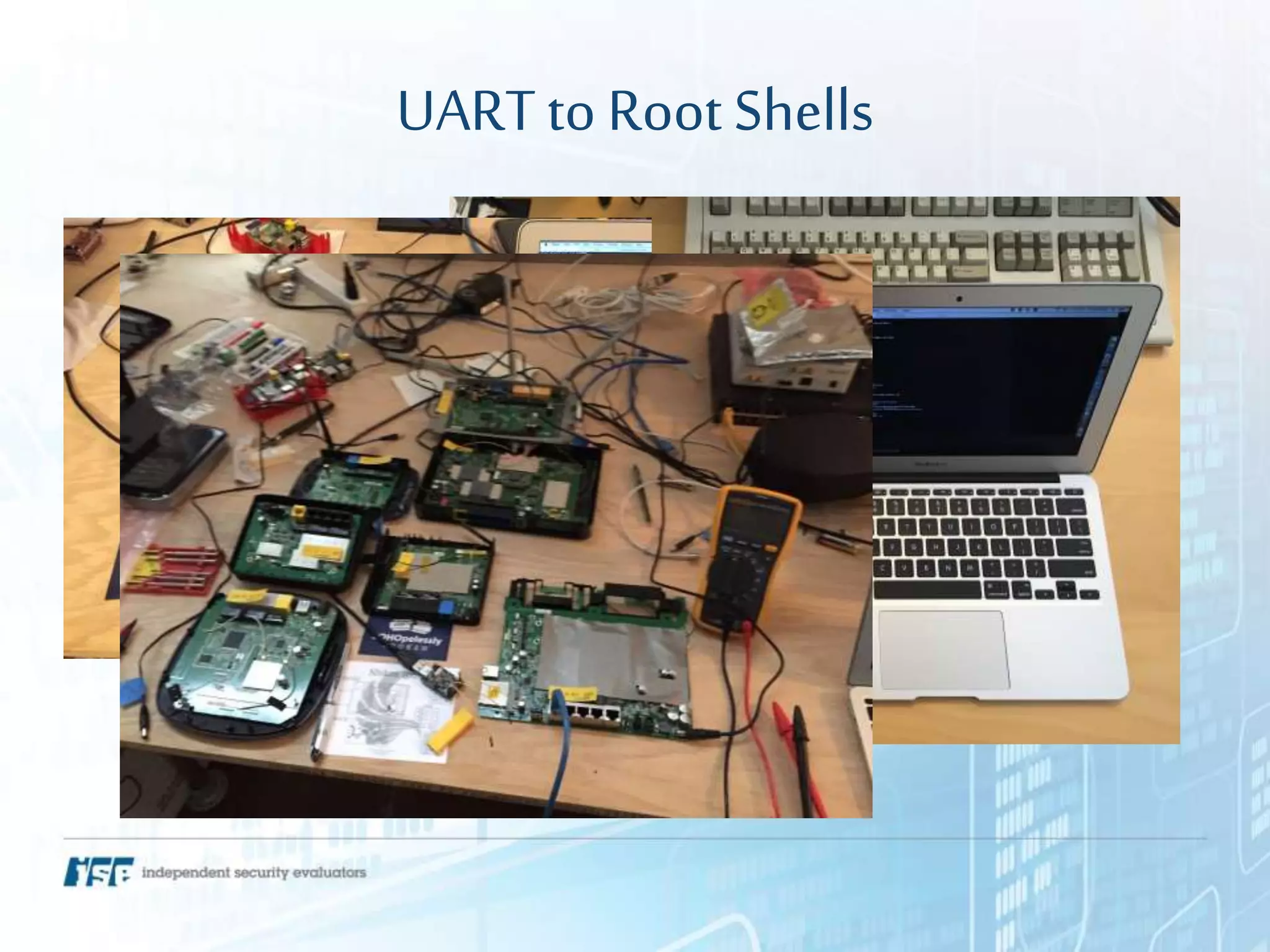
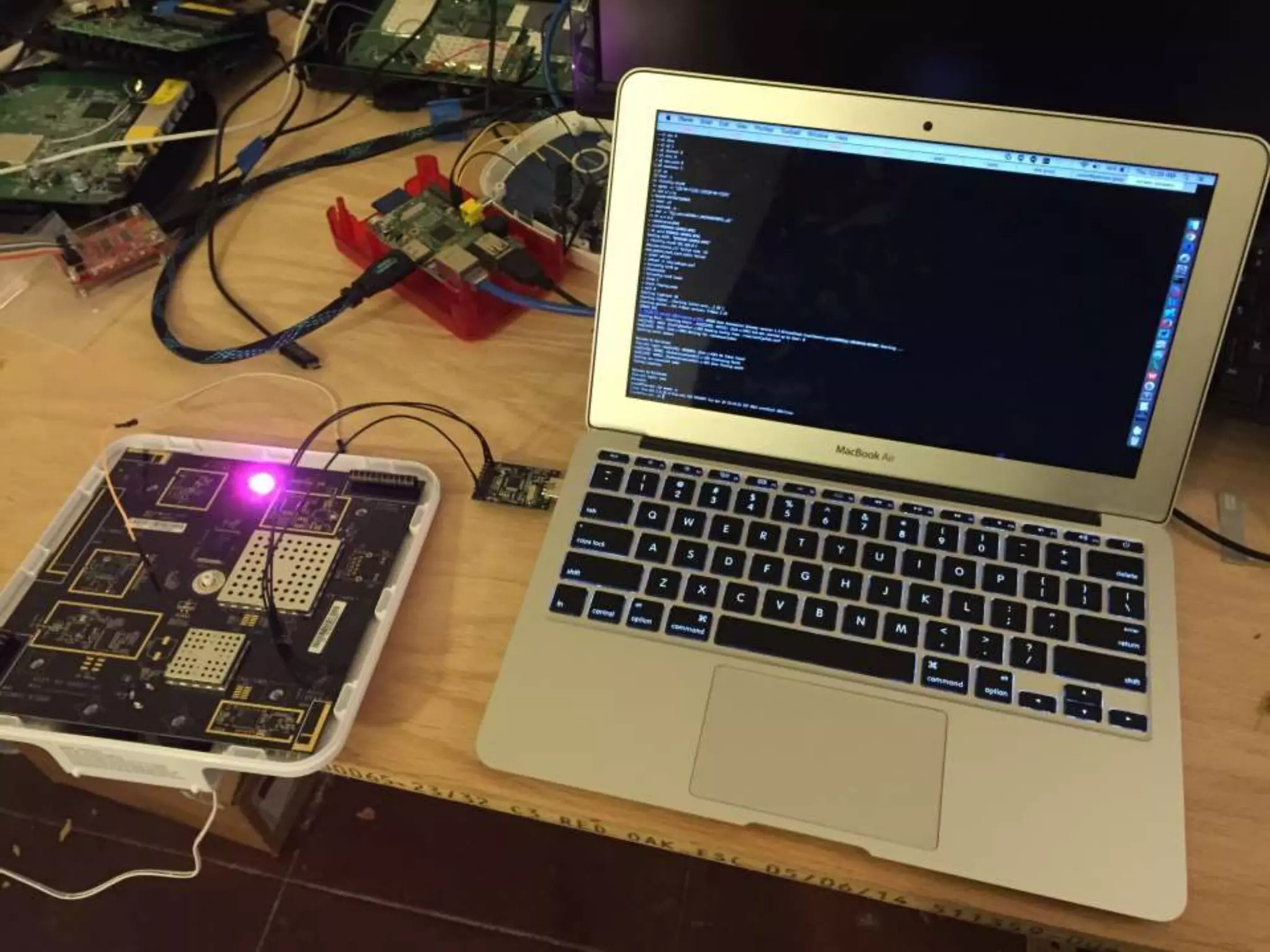
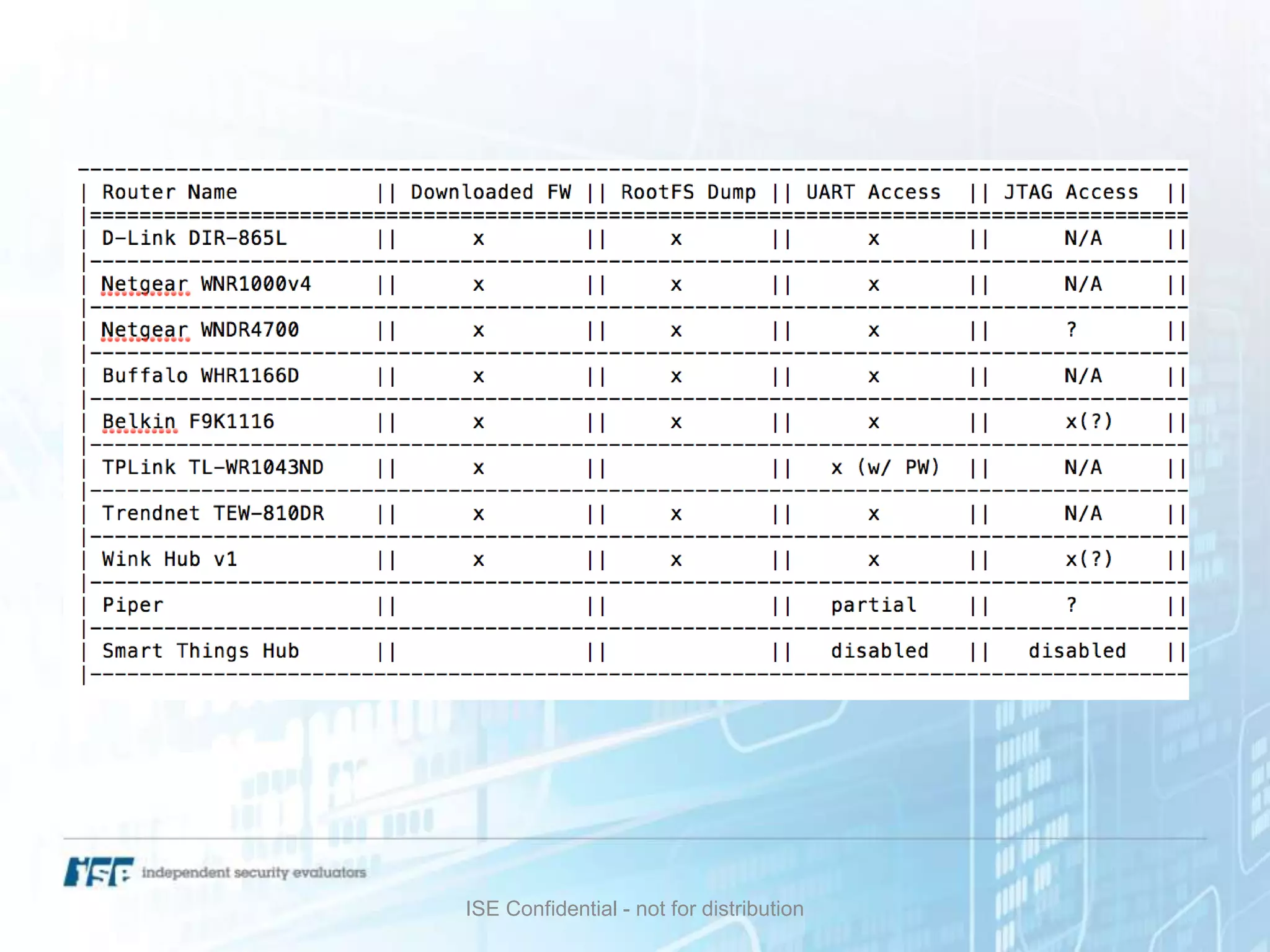
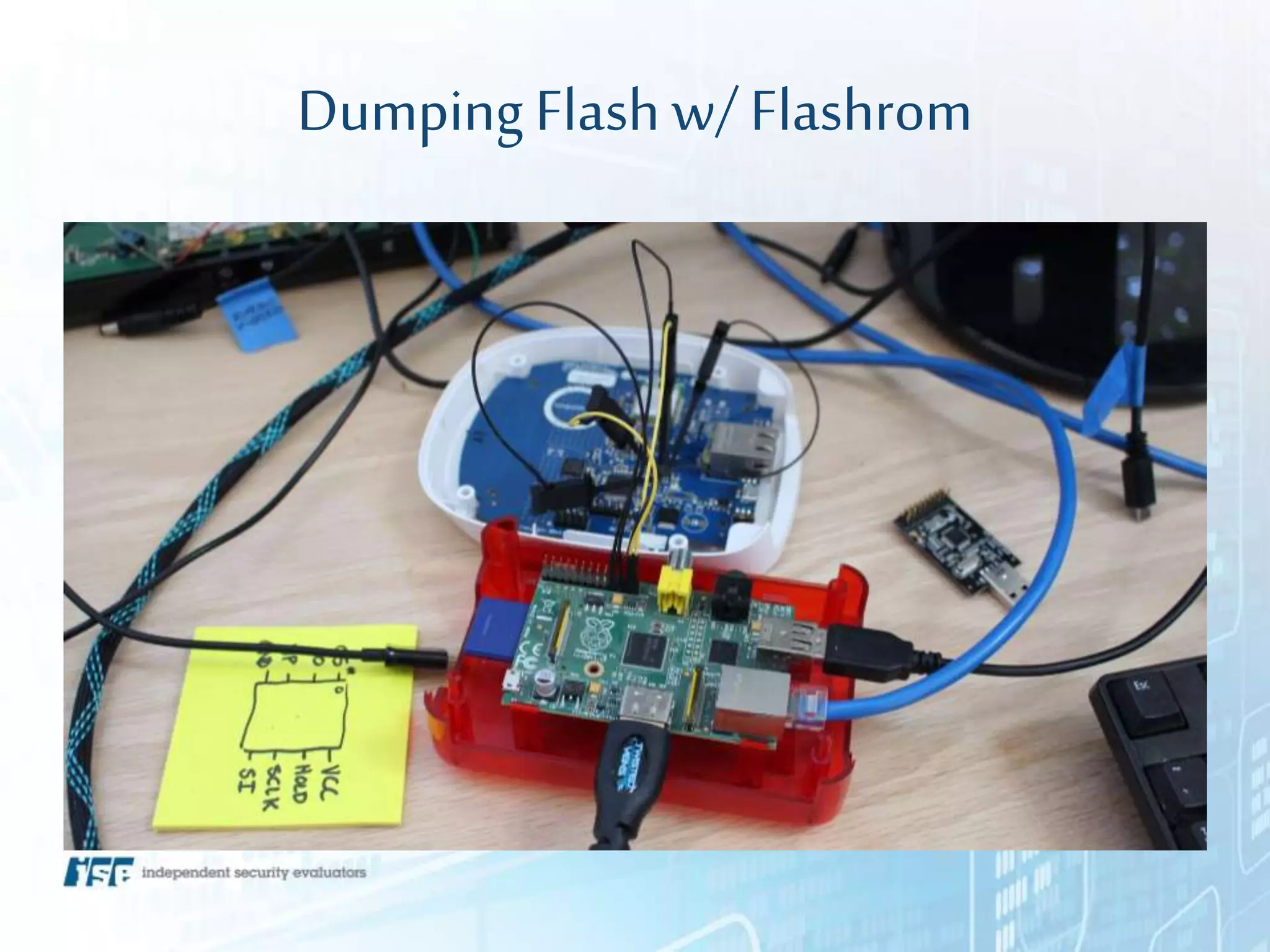
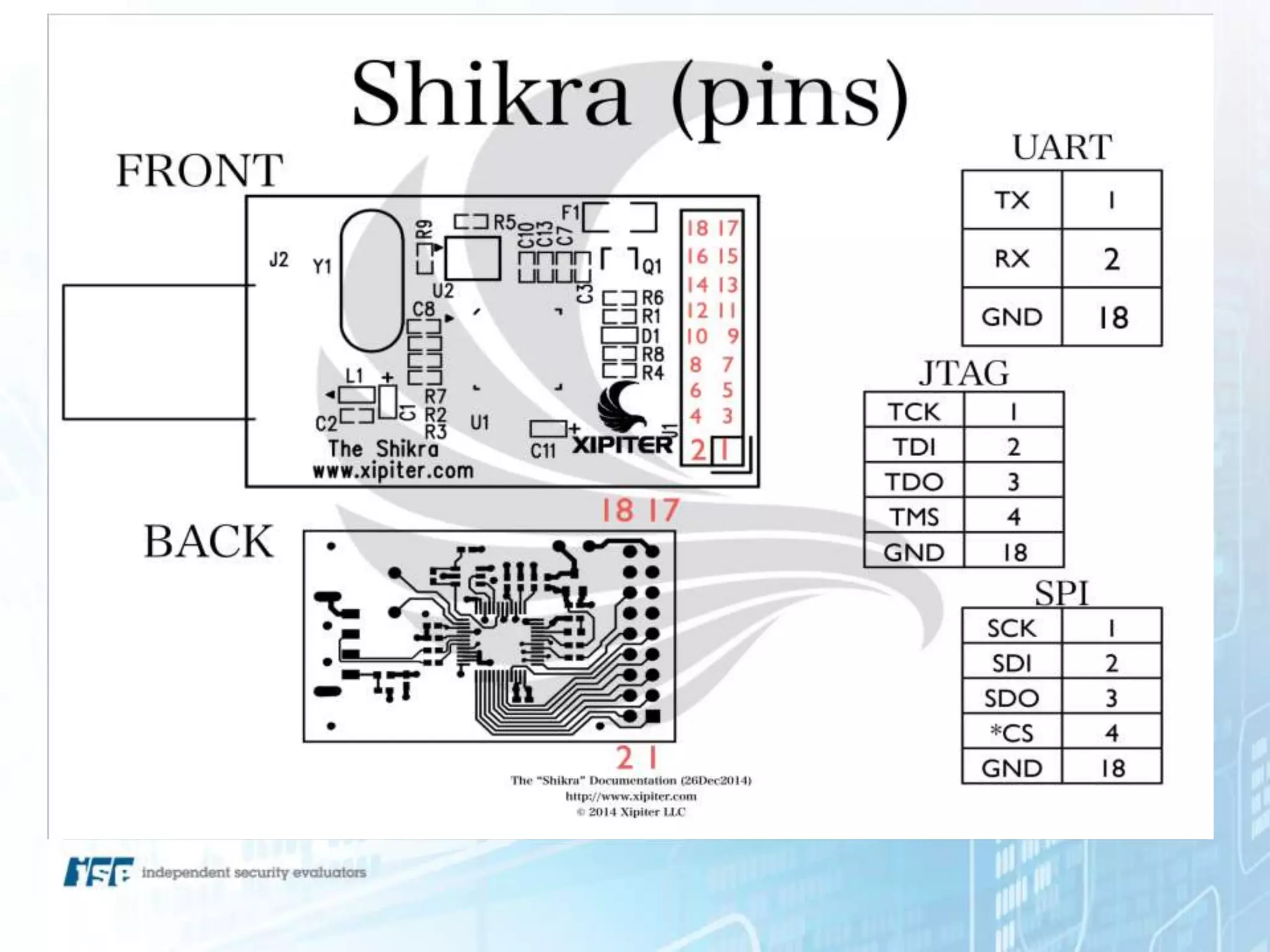
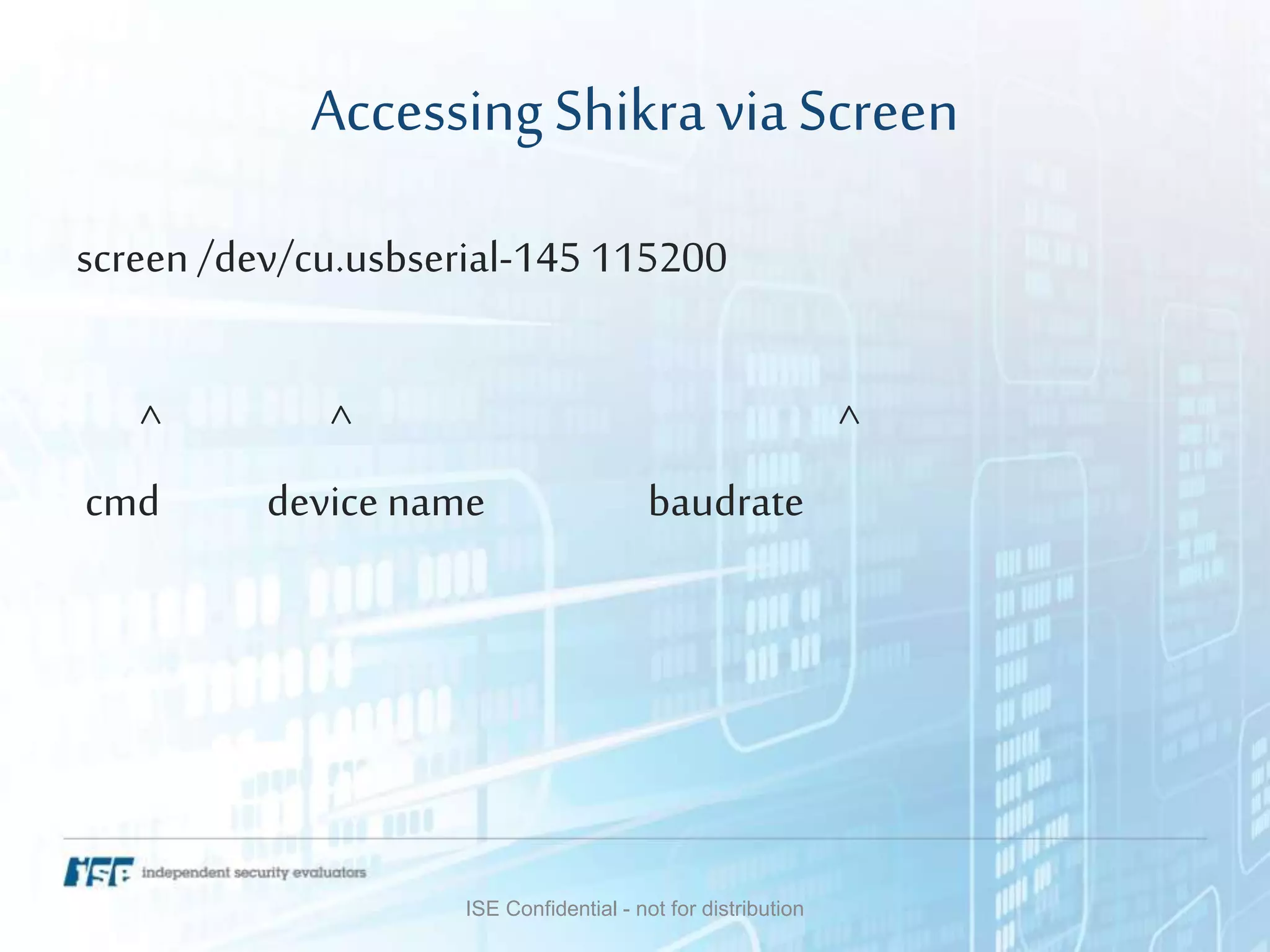
The document presents a workshop on hardware attacks and IoT research led by Chase Schultz, a senior security consultant. It covers the significance of hardware hacking, methodologies for exploiting devices, and tools used in the process, emphasizing the importance of understanding hardware components and communication interfaces. Additionally, it invites attendees to engage hands-on and explore further resources for learning.