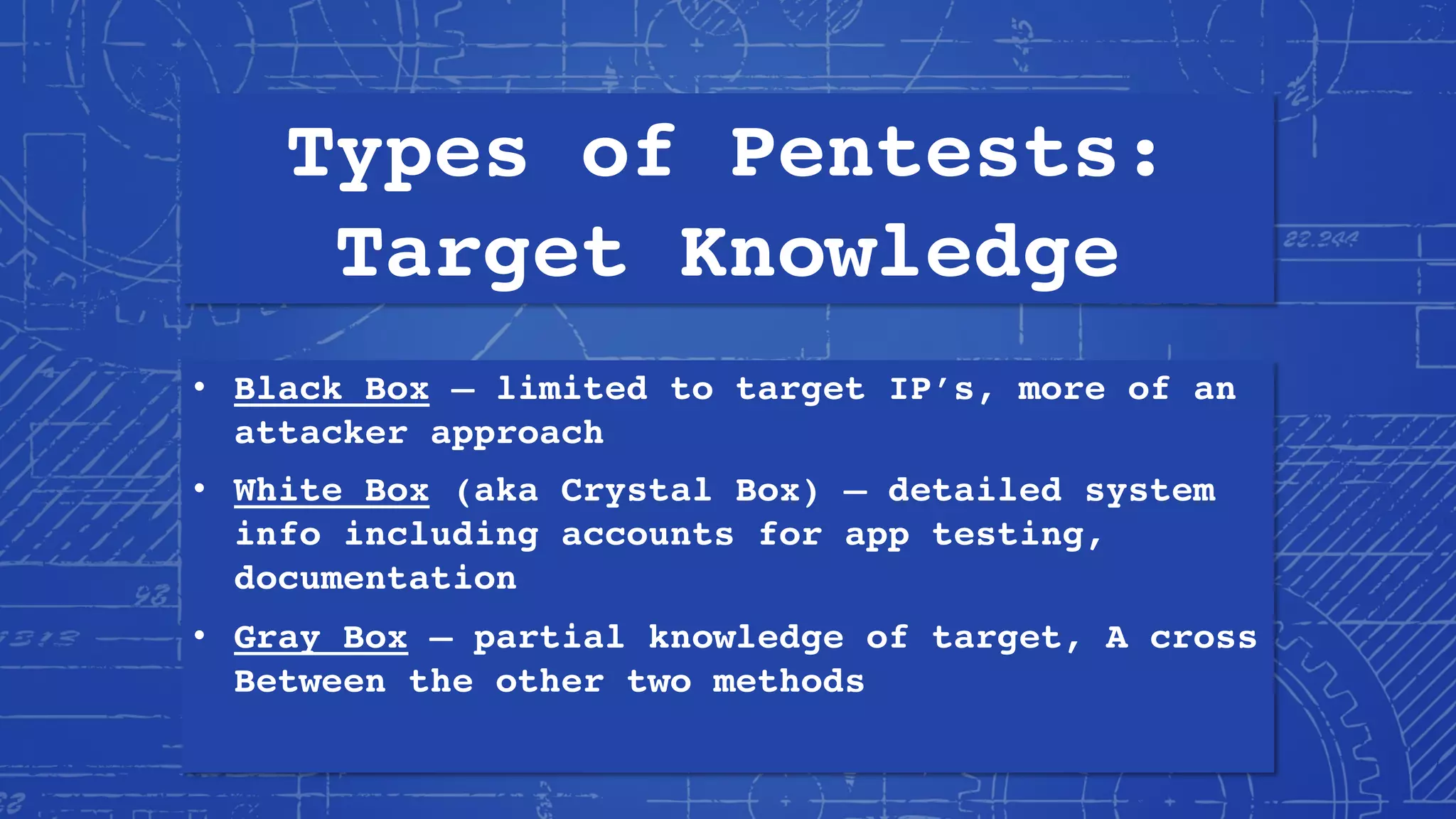
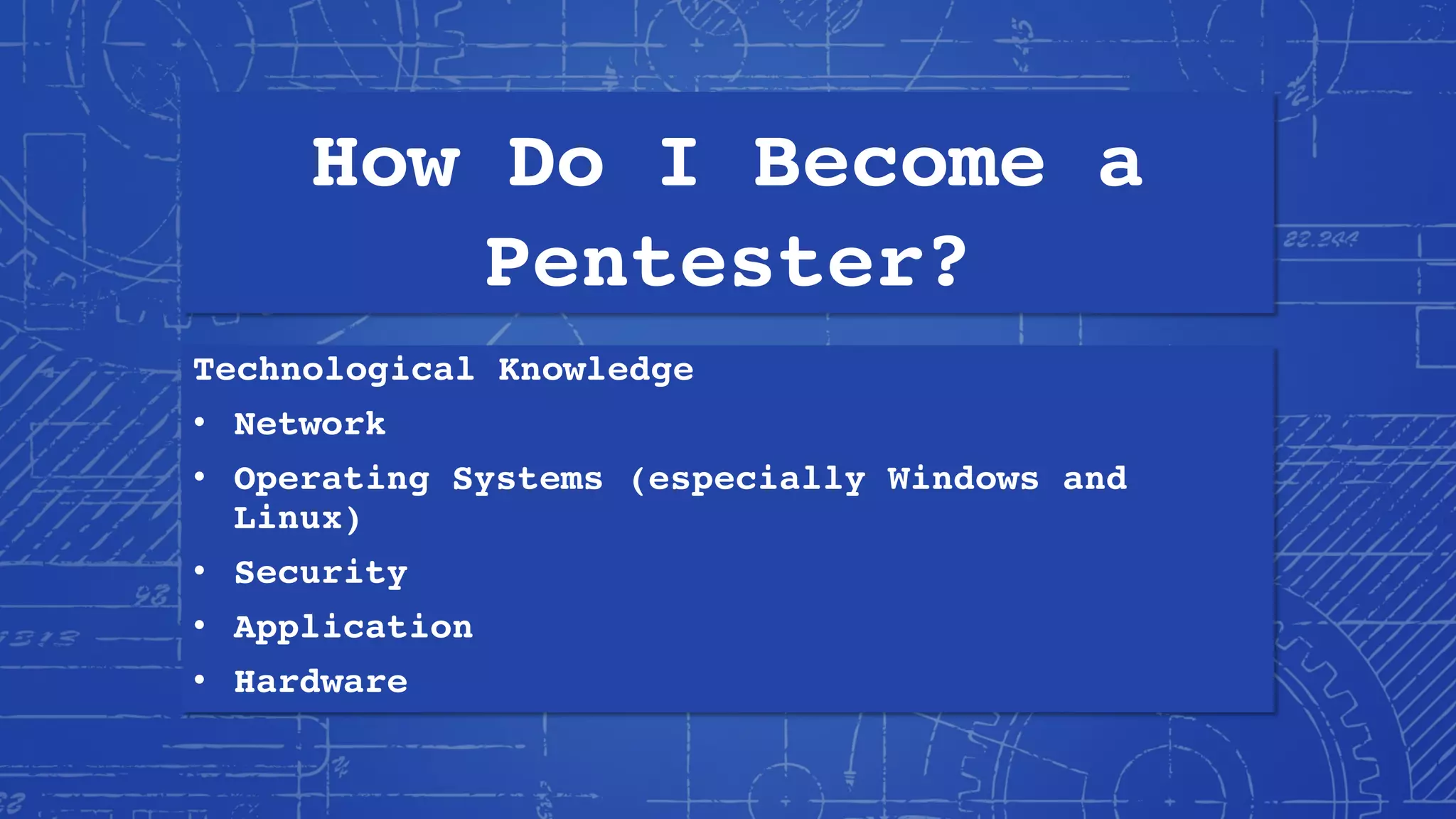
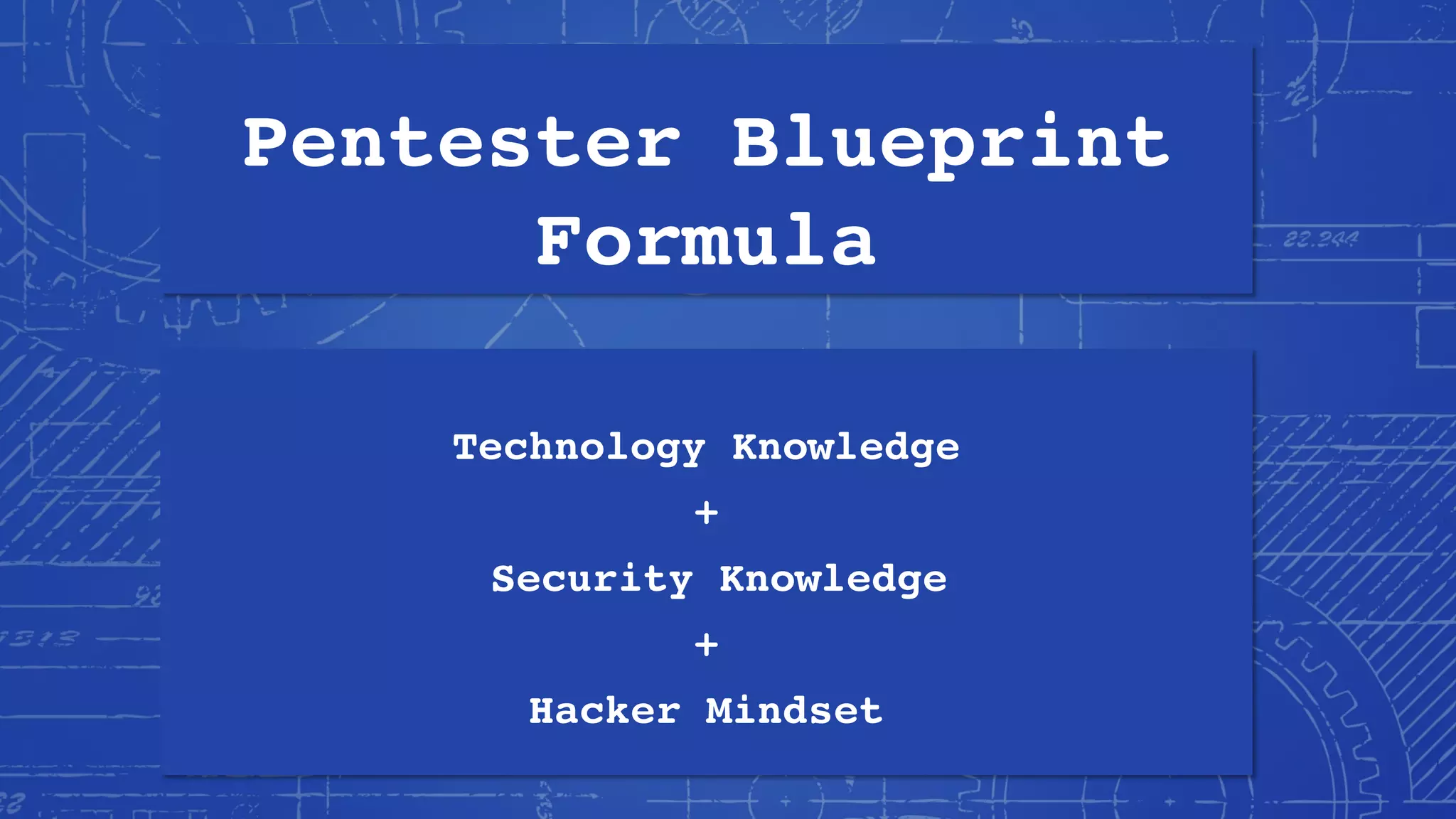
This document provides an overview of becoming a penetration tester or pentester. It discusses Phillip Wylie's background and experience in information security. It defines pentesting and explains why organizations use pentesting for security assessments and regulatory compliance. It outlines the skills, knowledge, and mindset needed to become a pentester including technological knowledge, hacking skills, and developing a "hacker mindset". It provides recommendations for building a home lab, recommended reading, learning resources, certifications, and tips for getting pentester jobs.