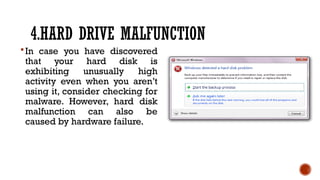
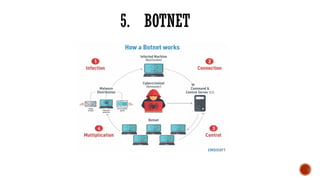
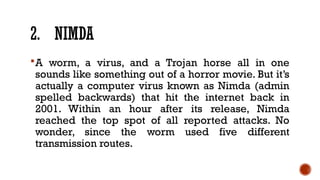
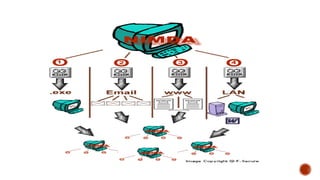
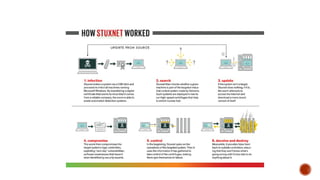
The document provides an overview of computer viruses, explaining their nature as self-replicating programs that infect host systems, causing damage and data theft. It details symptoms of infection, types of malware, notable examples of viruses, and preventive measures, emphasizing the importance of antivirus software and safe computing practices. Additionally, it outlines how to identify and respond to a computer virus attack.