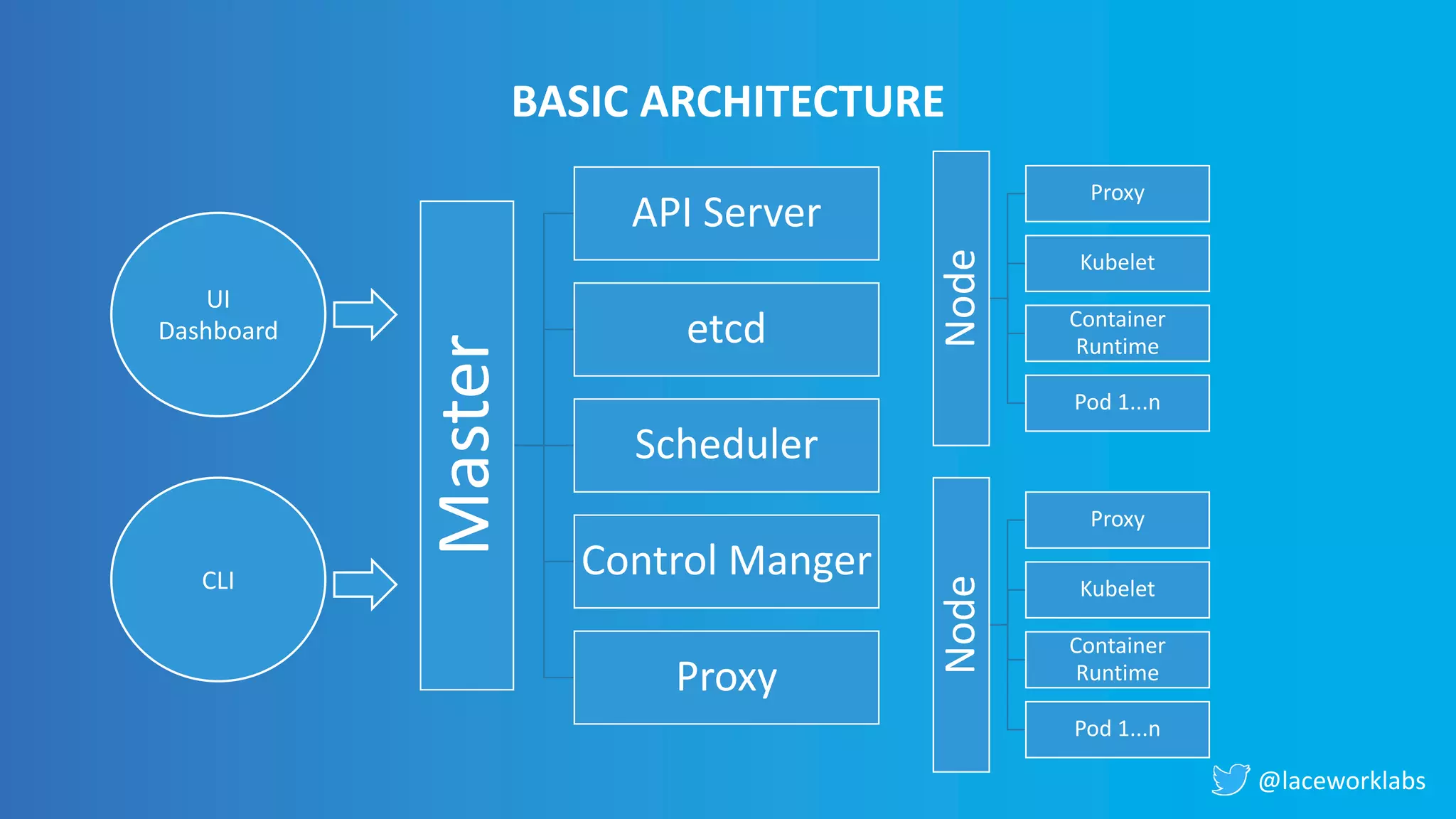
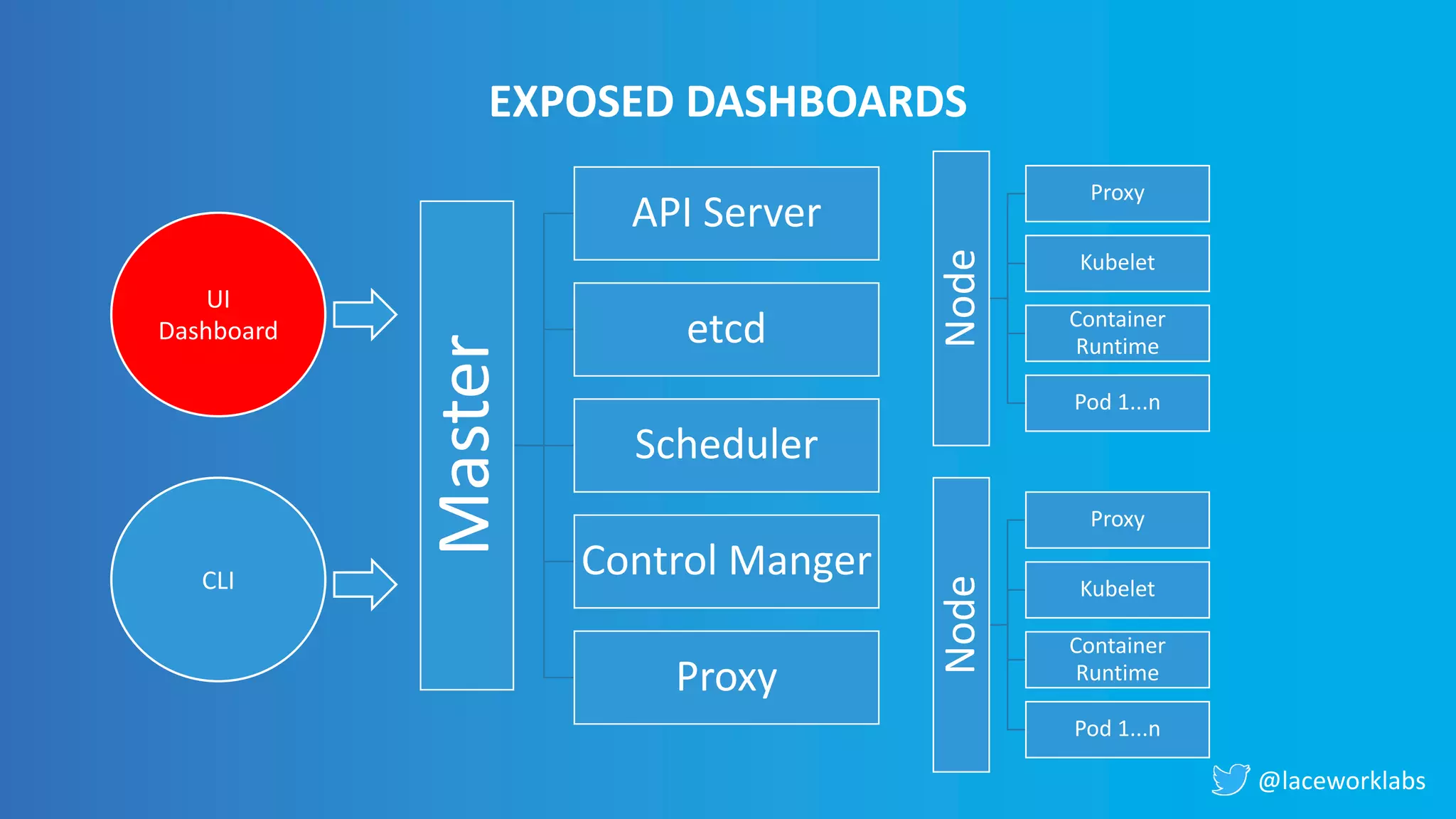
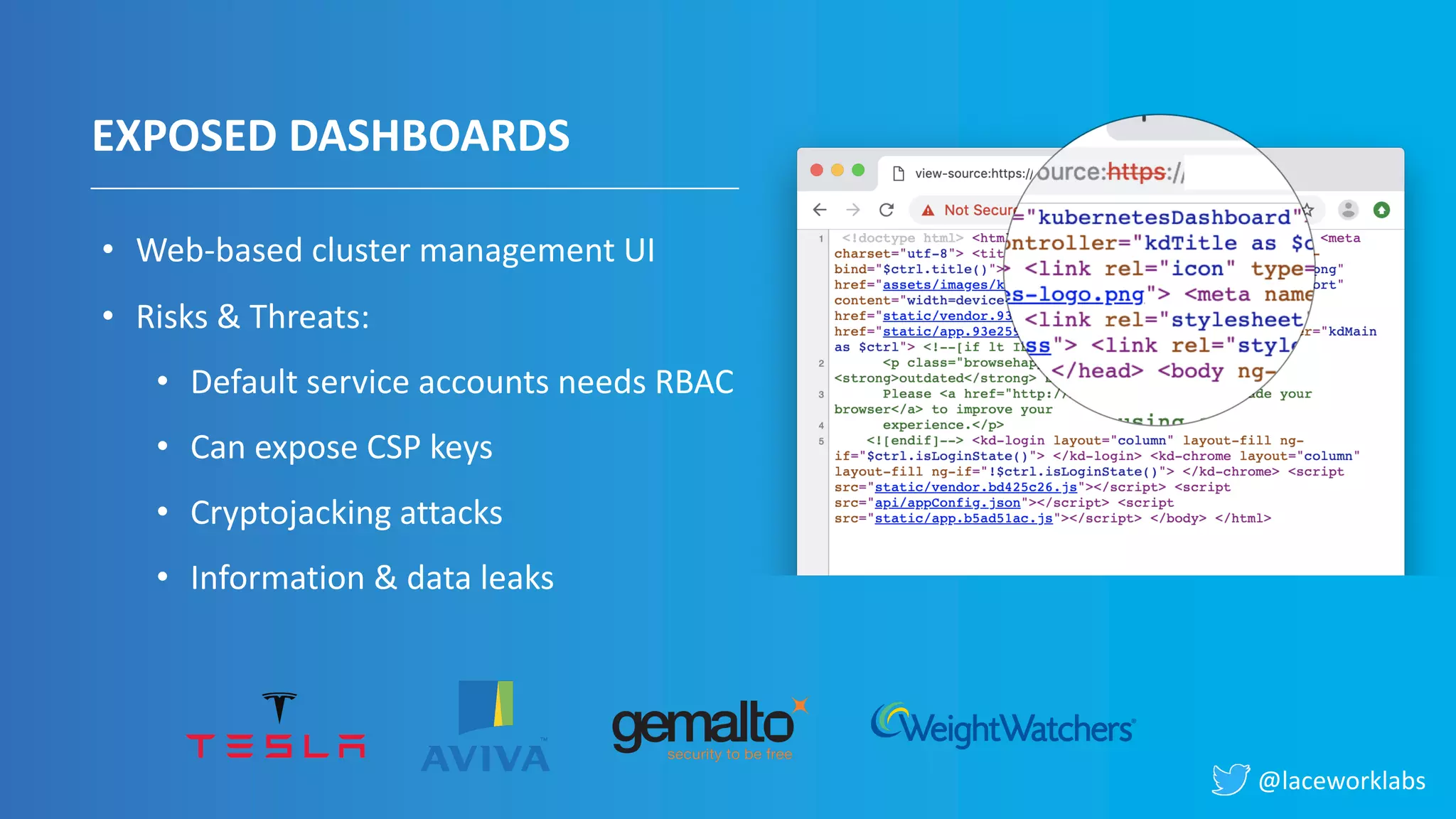
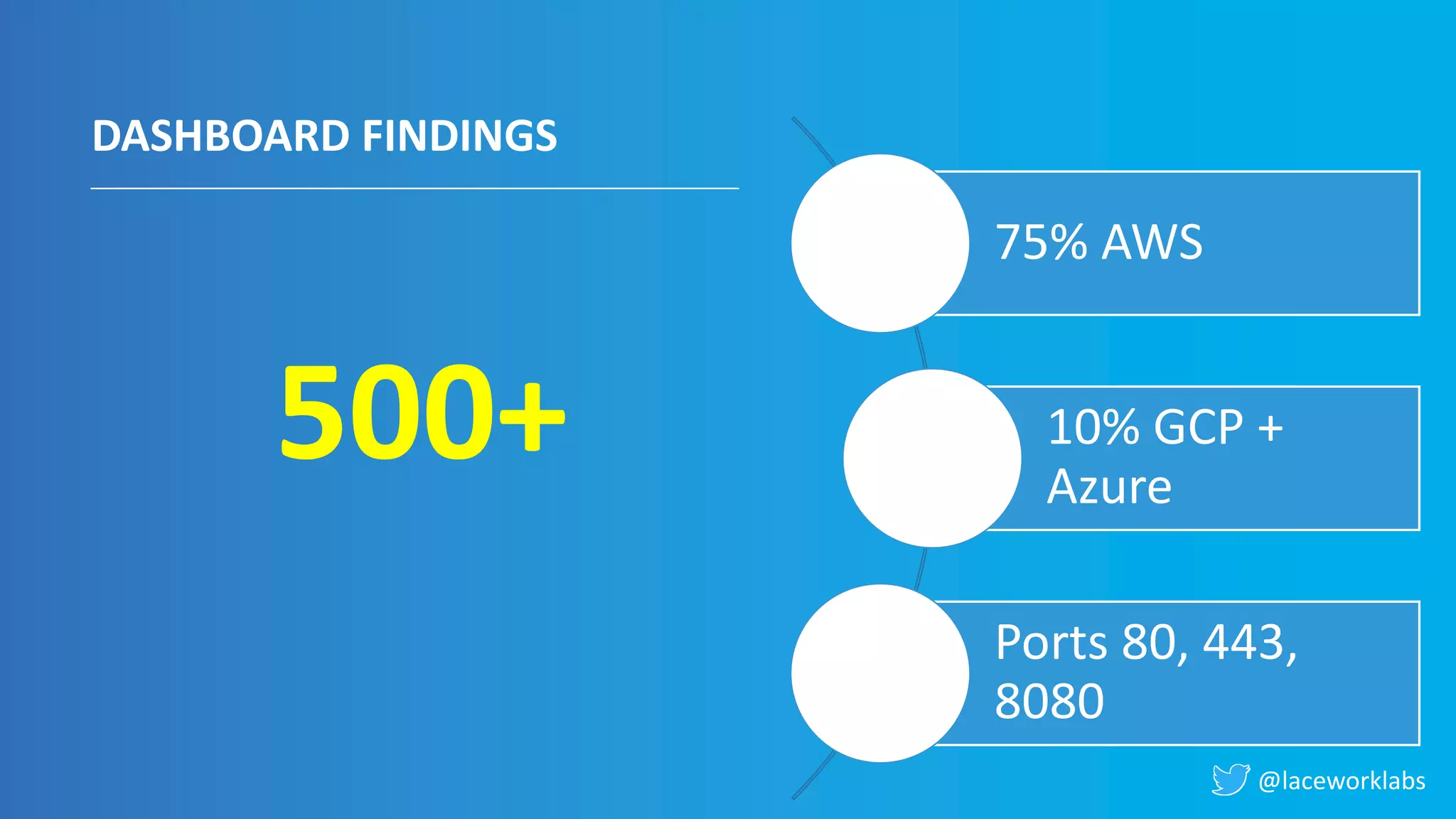
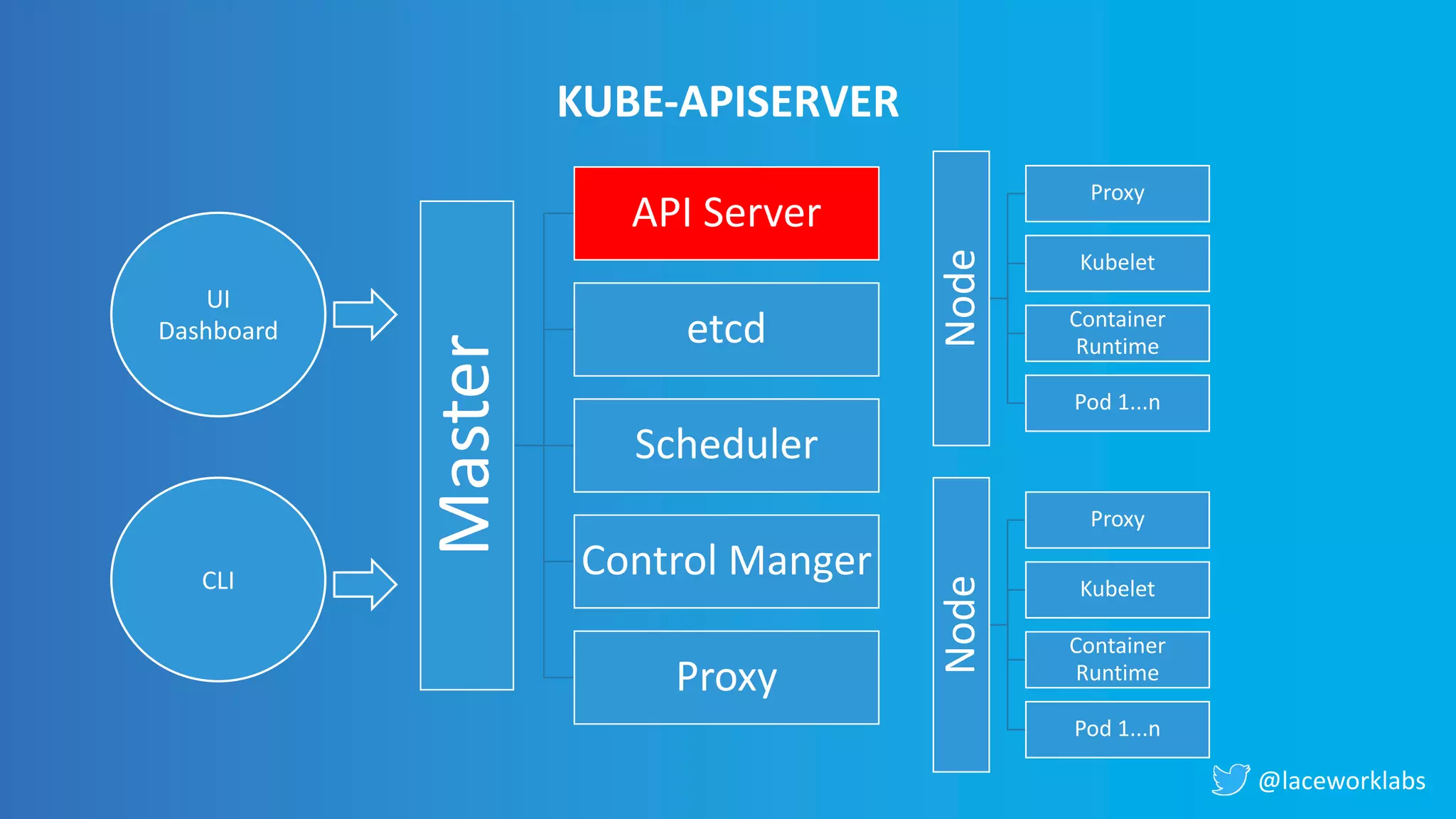
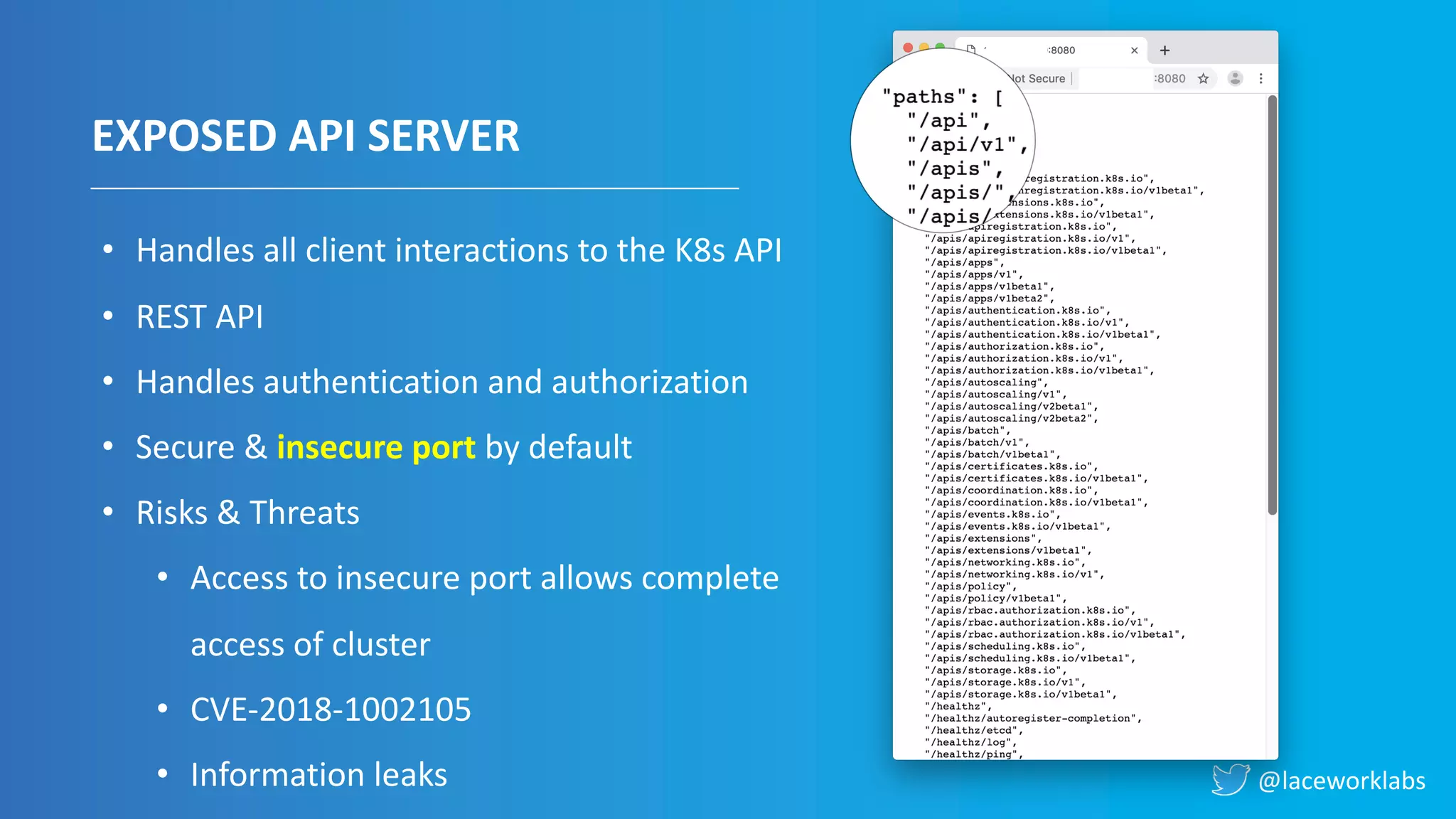
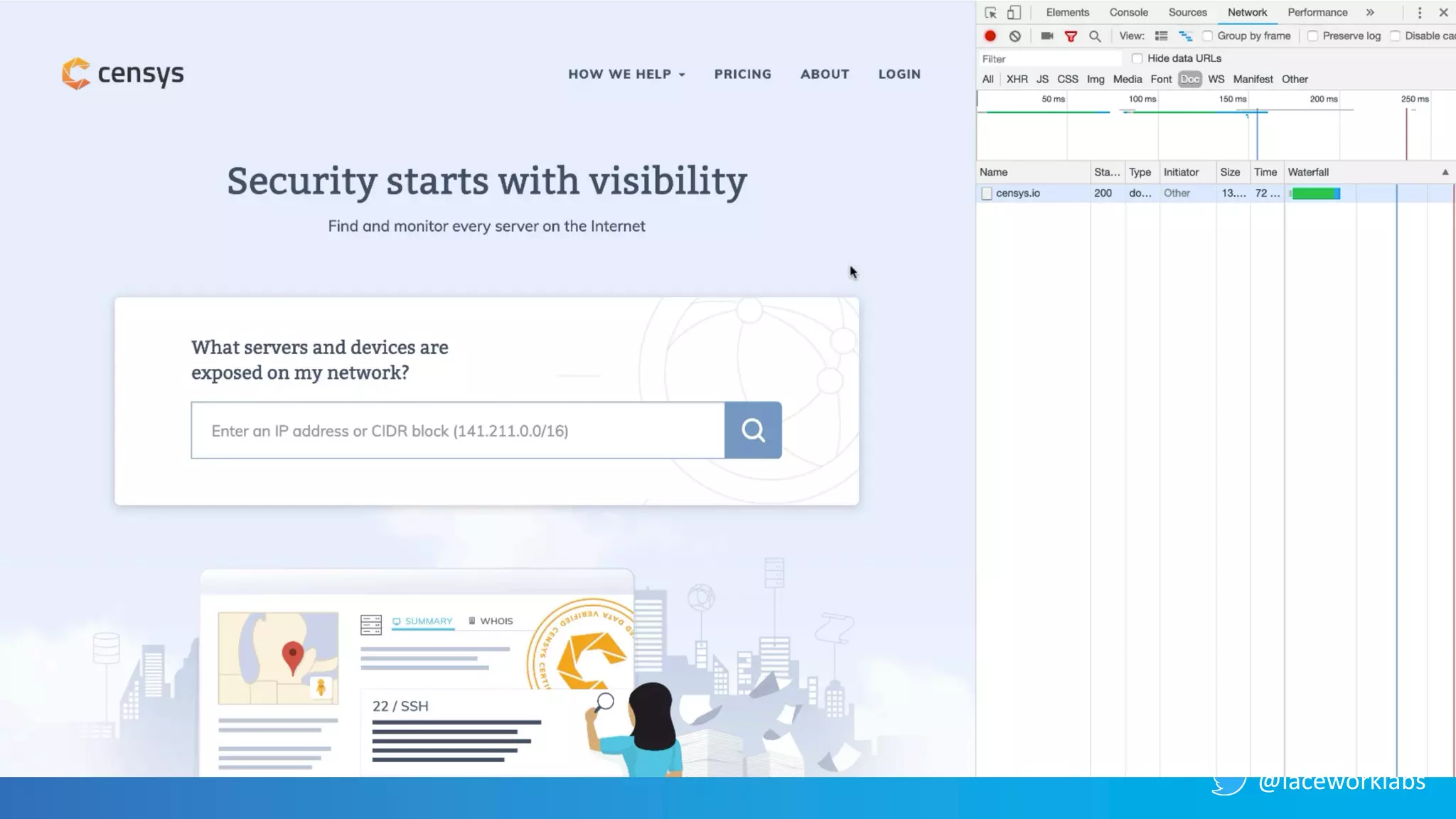
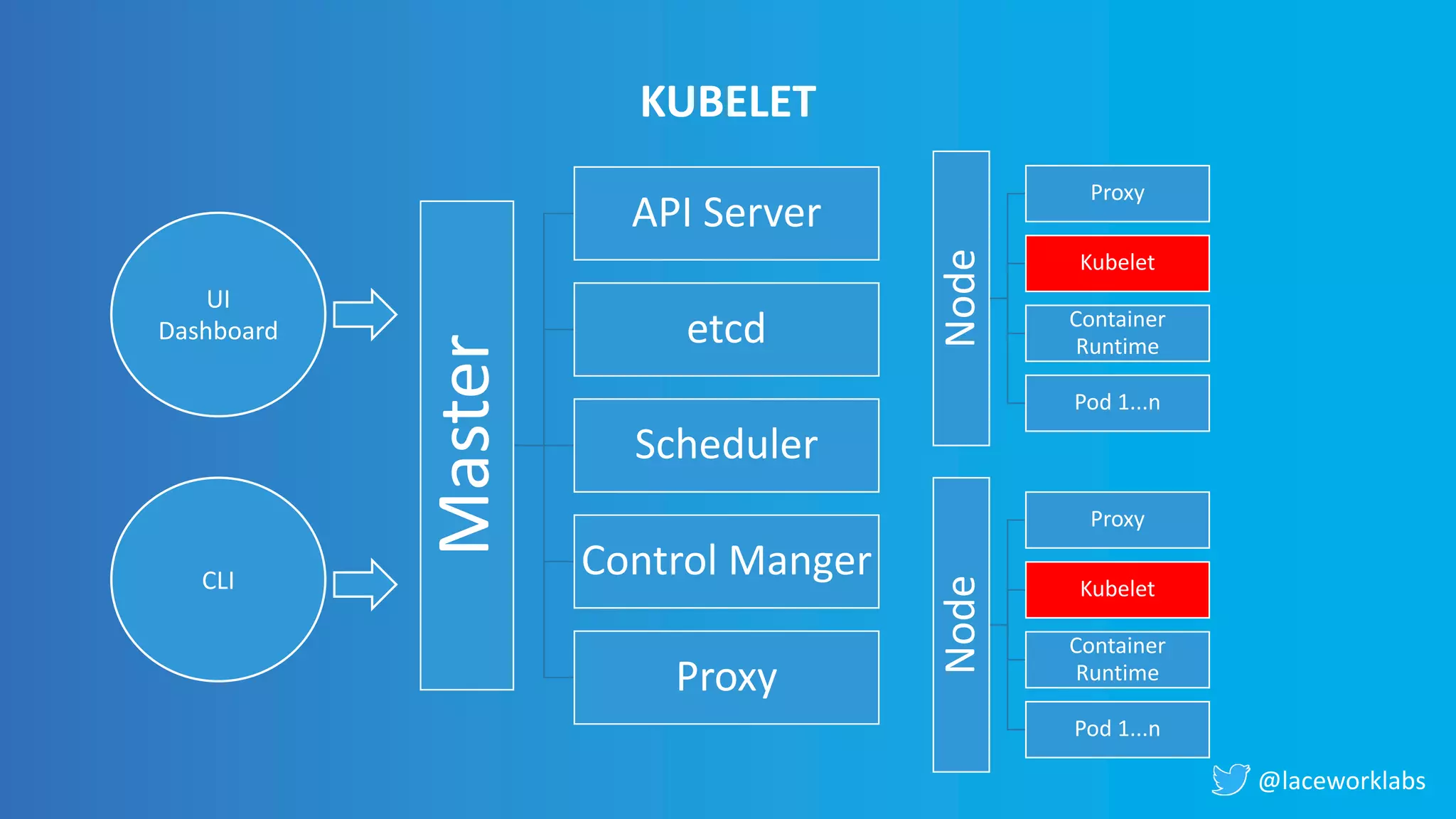
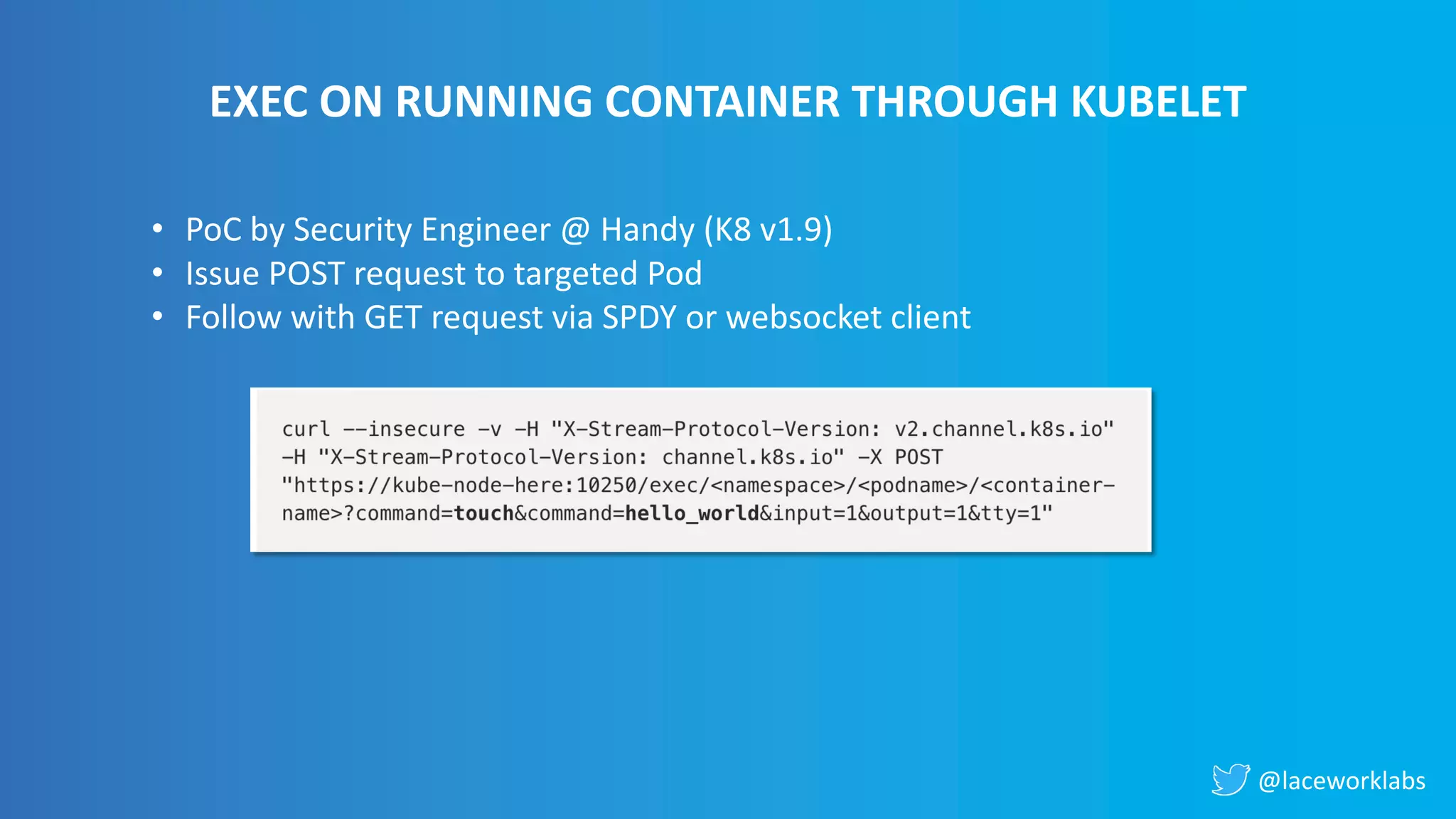
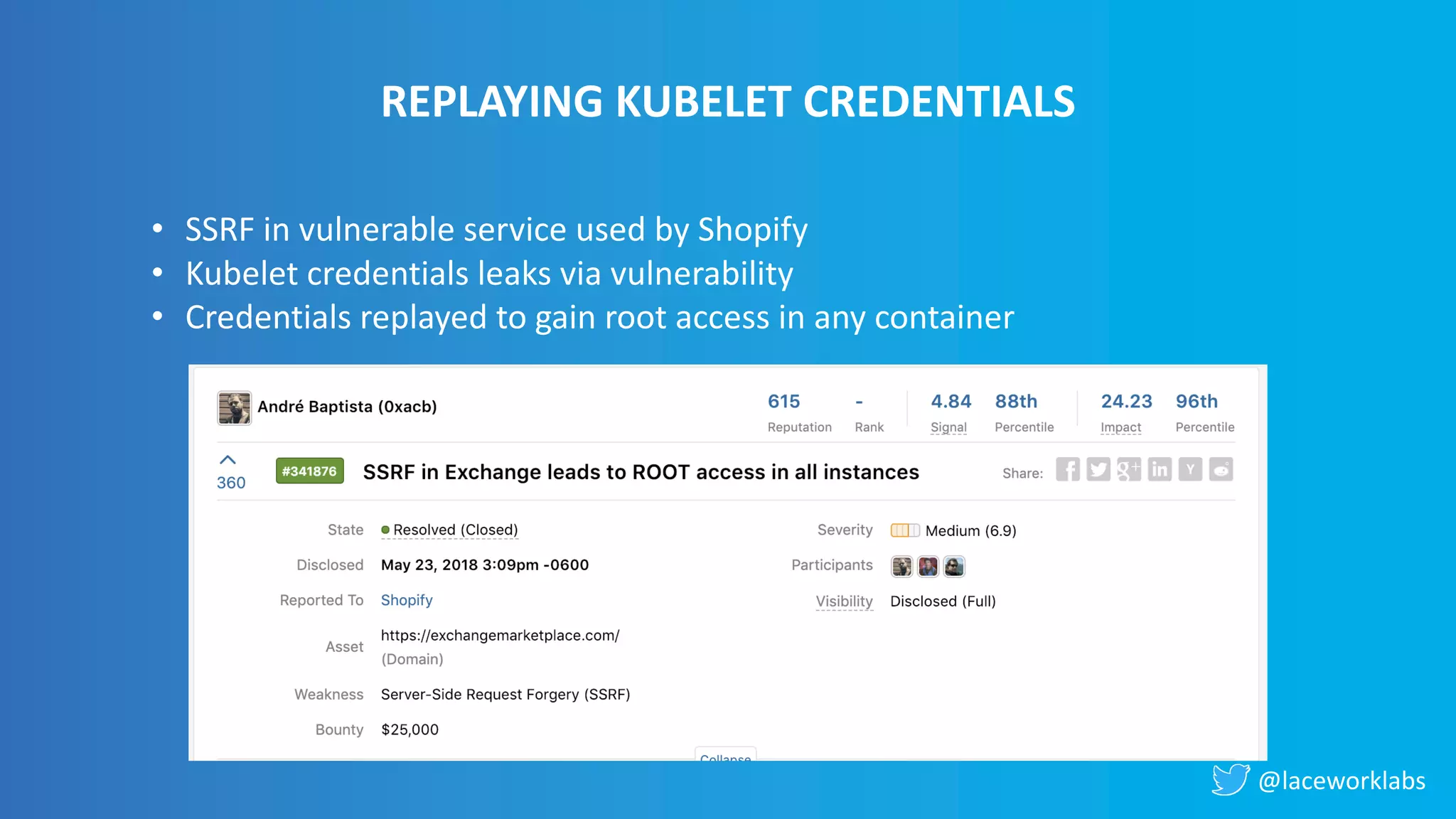
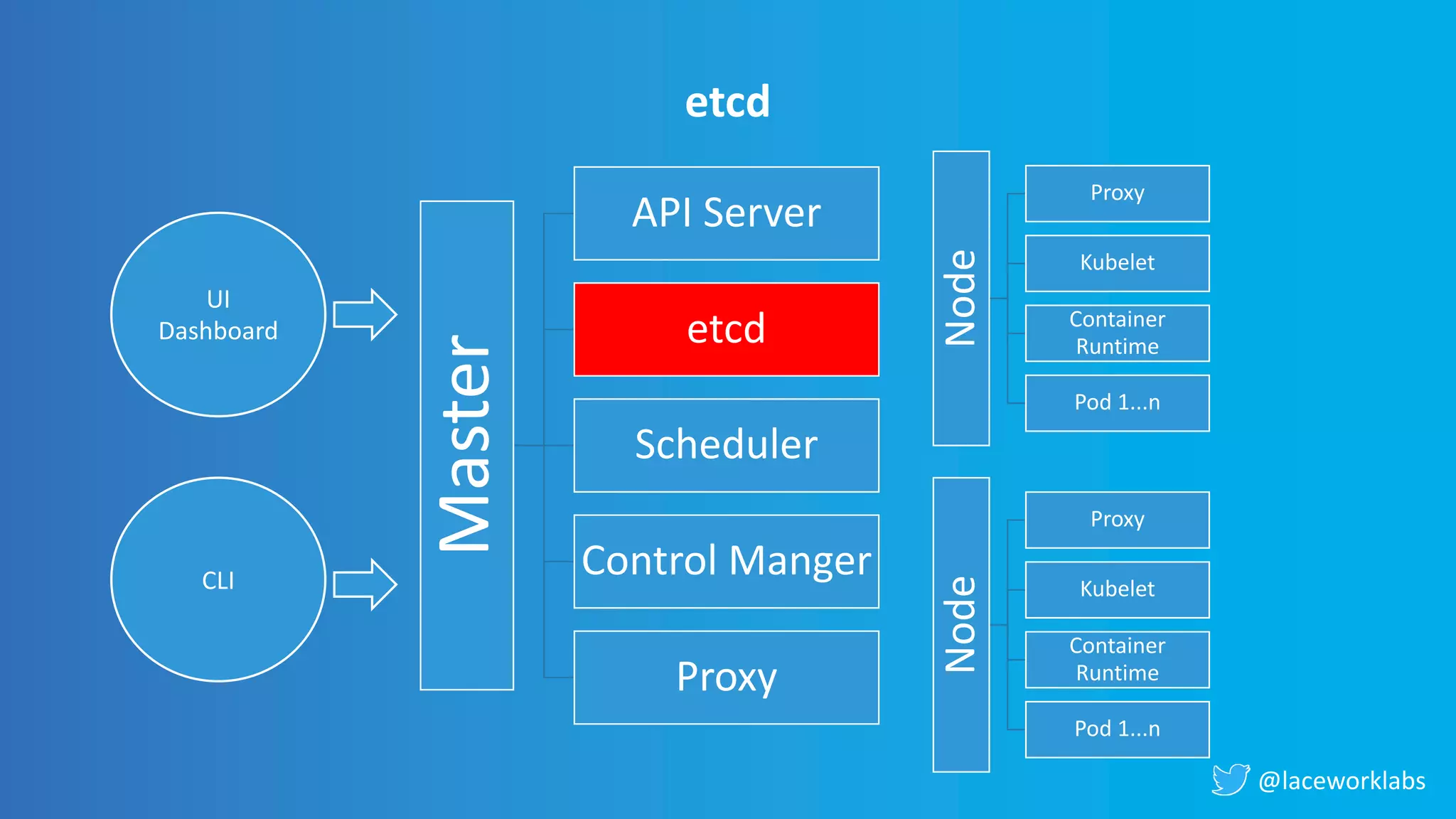
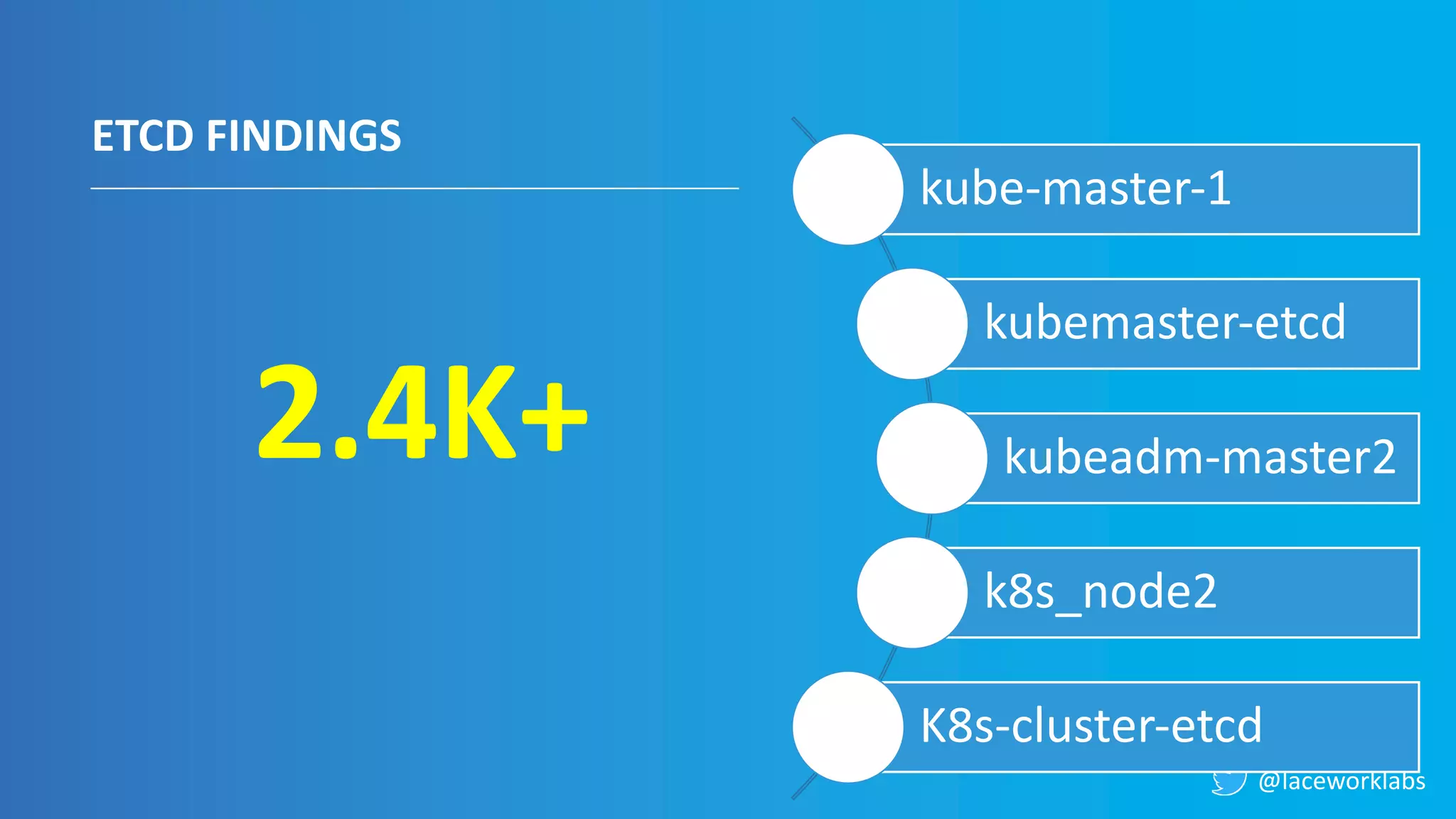
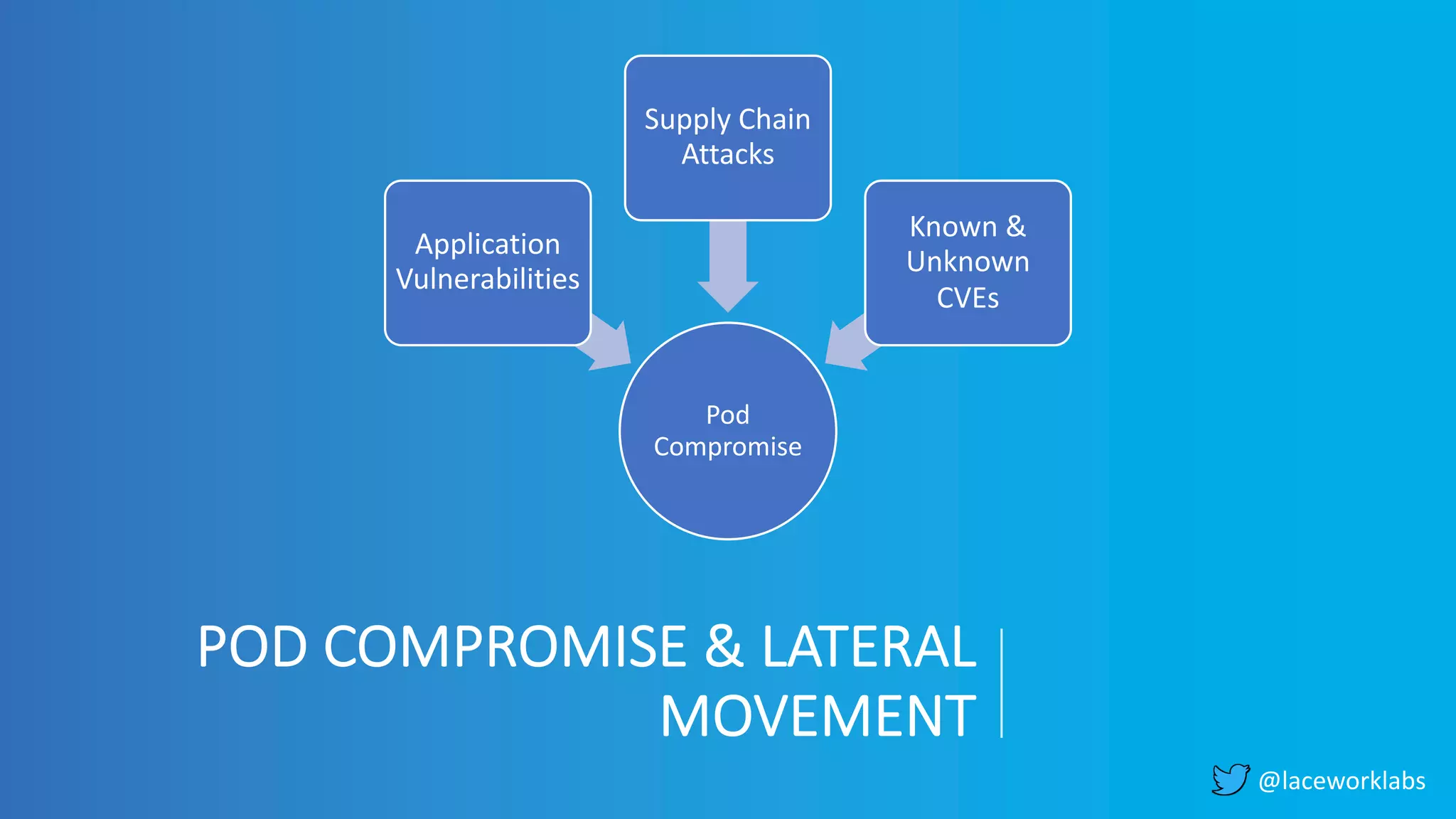
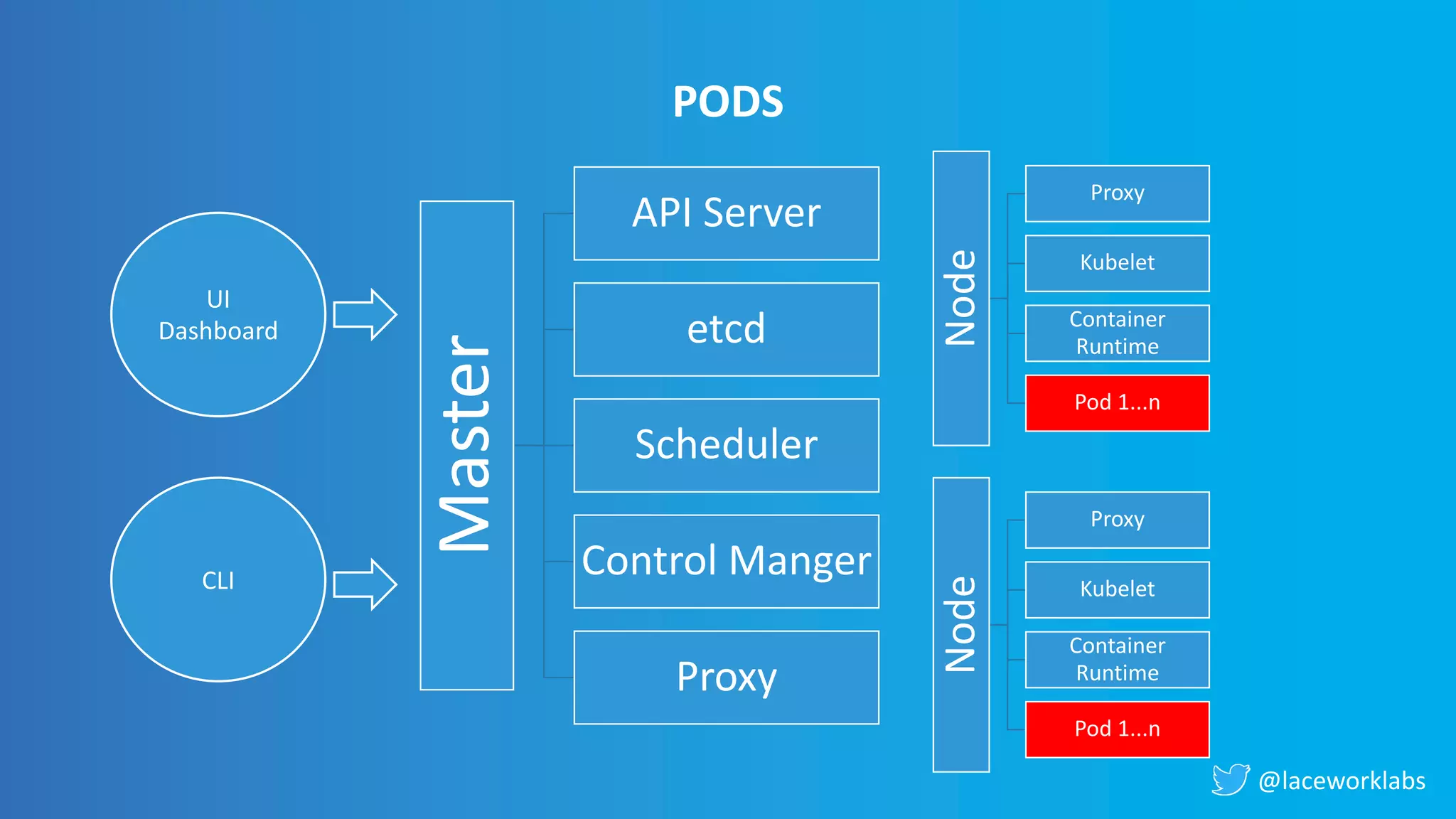
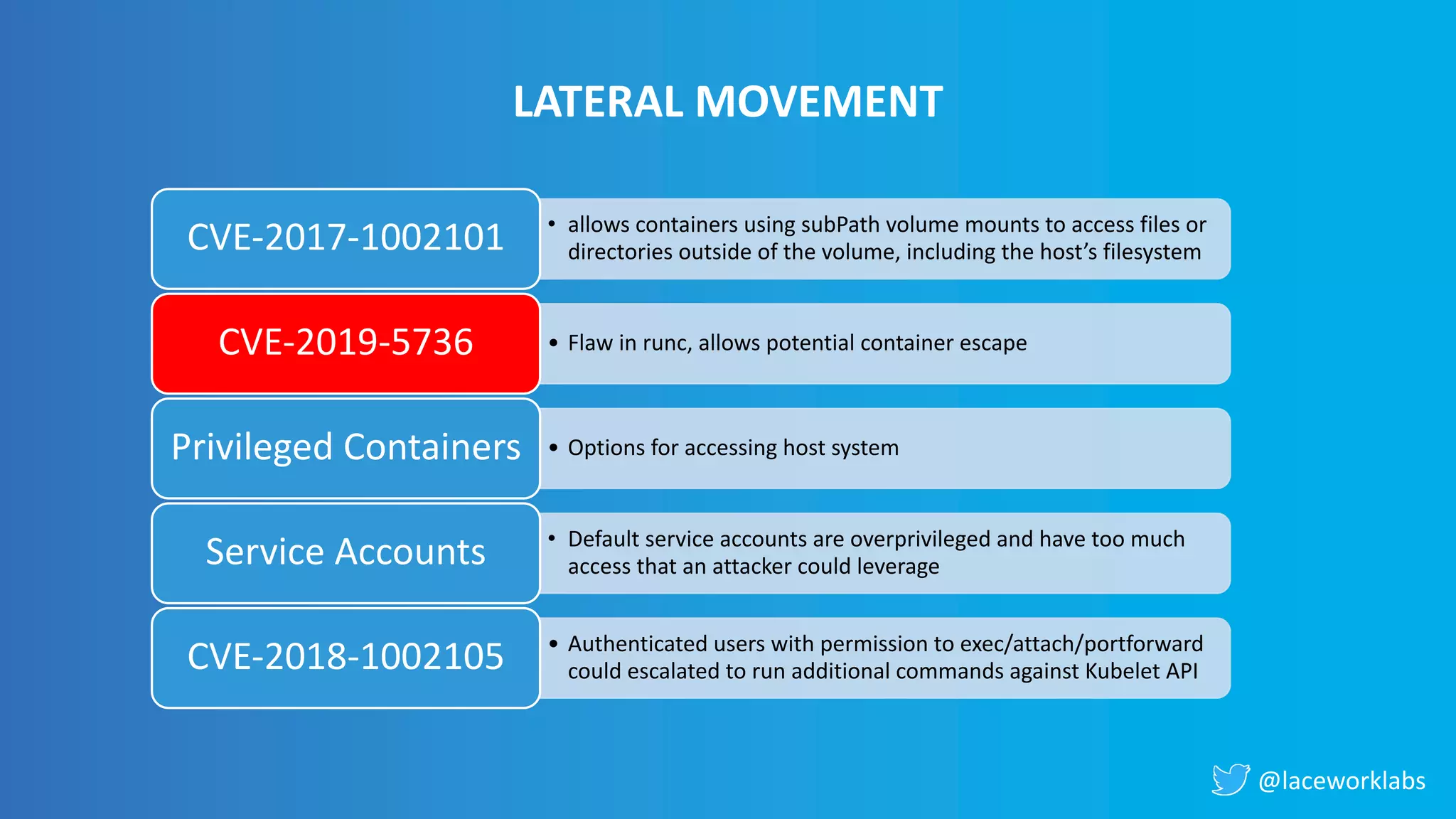
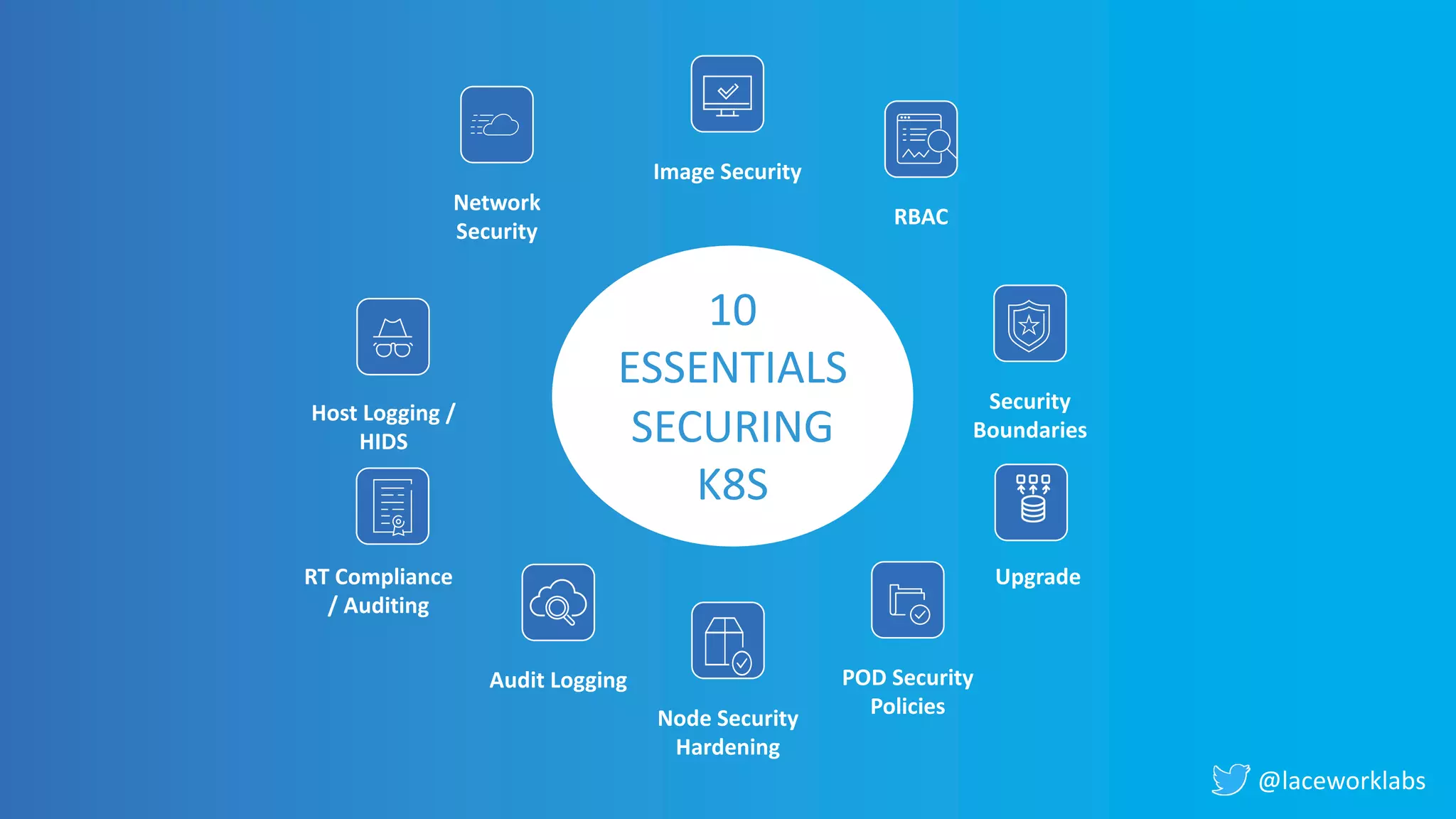
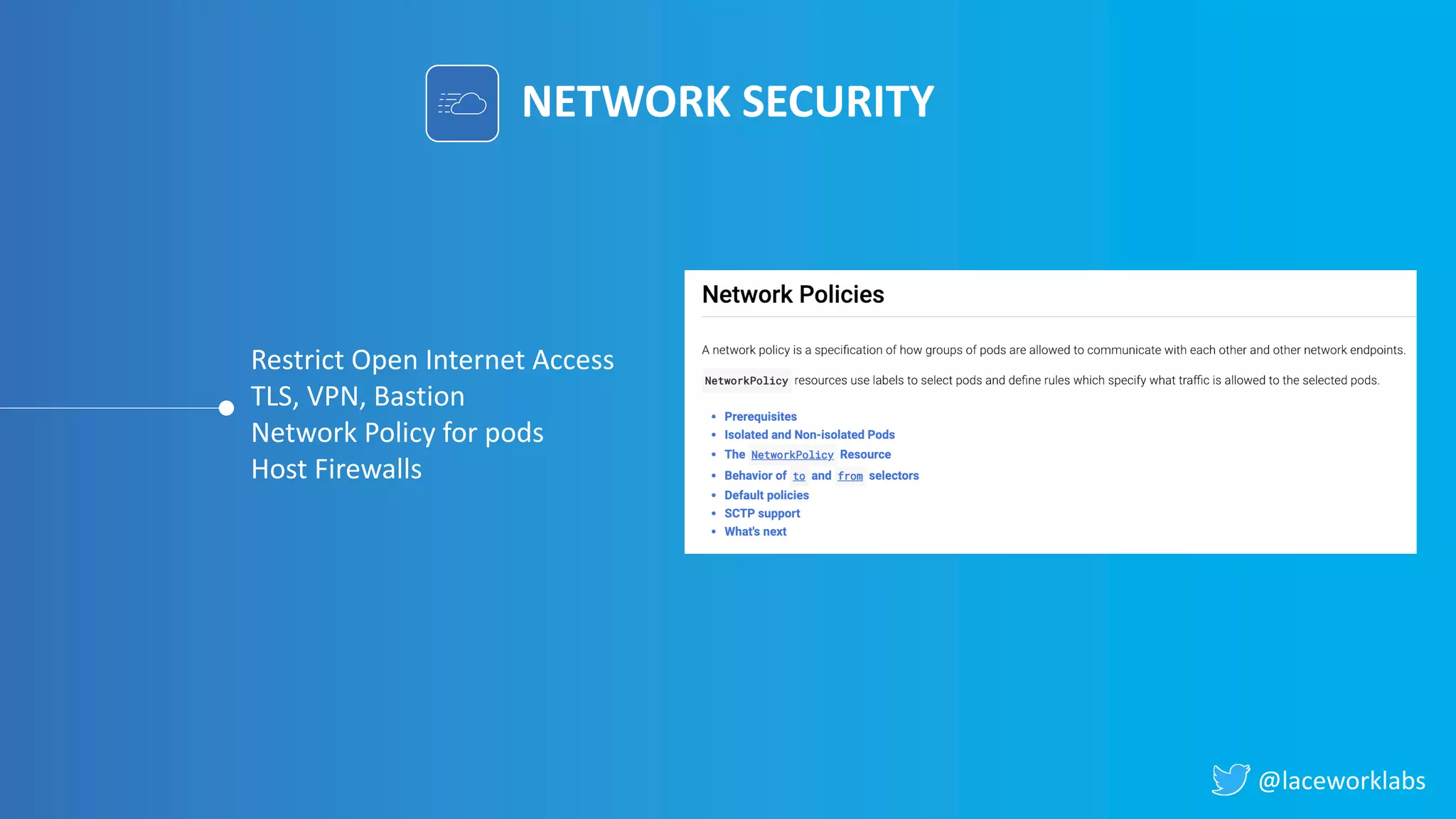
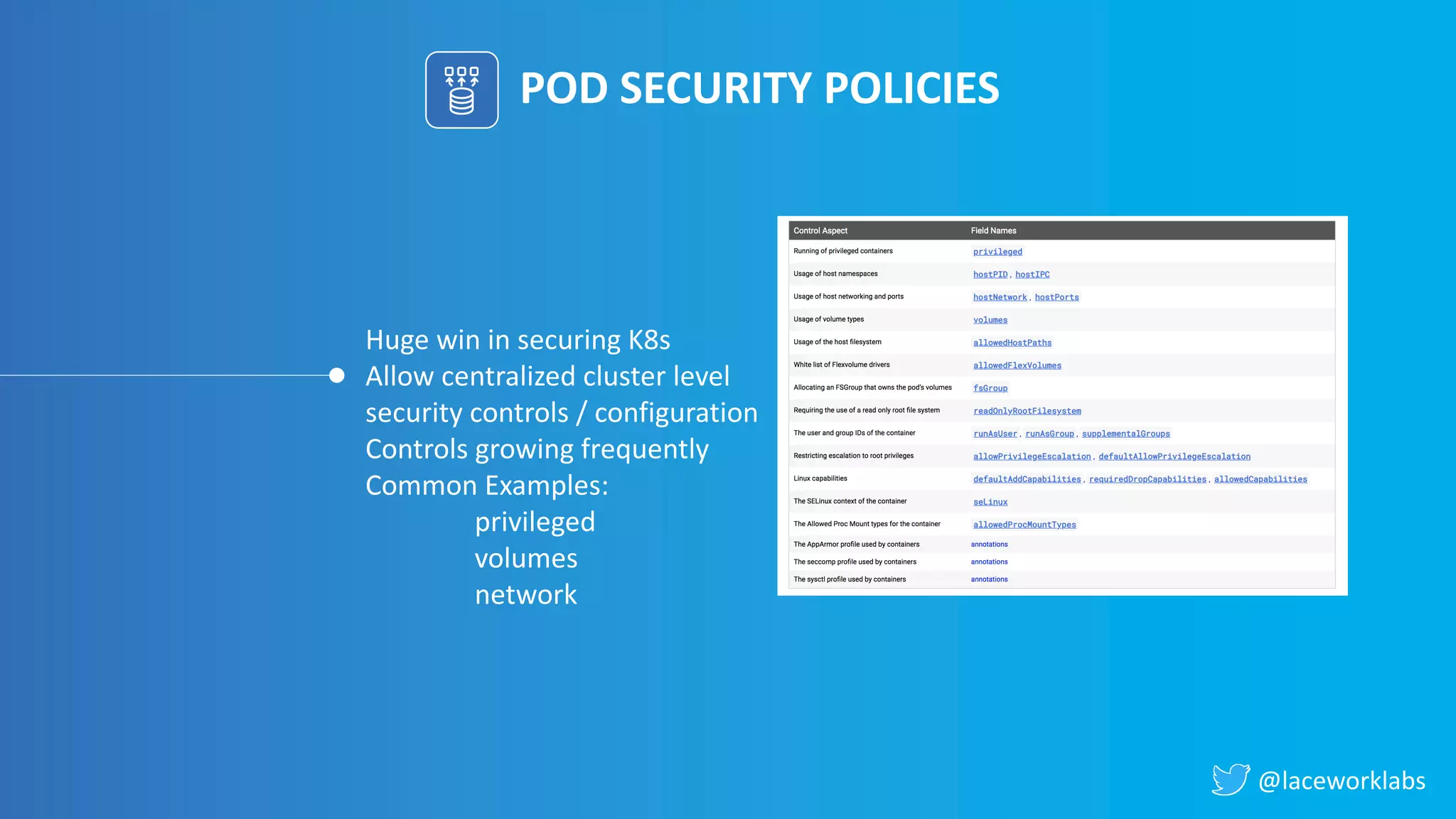
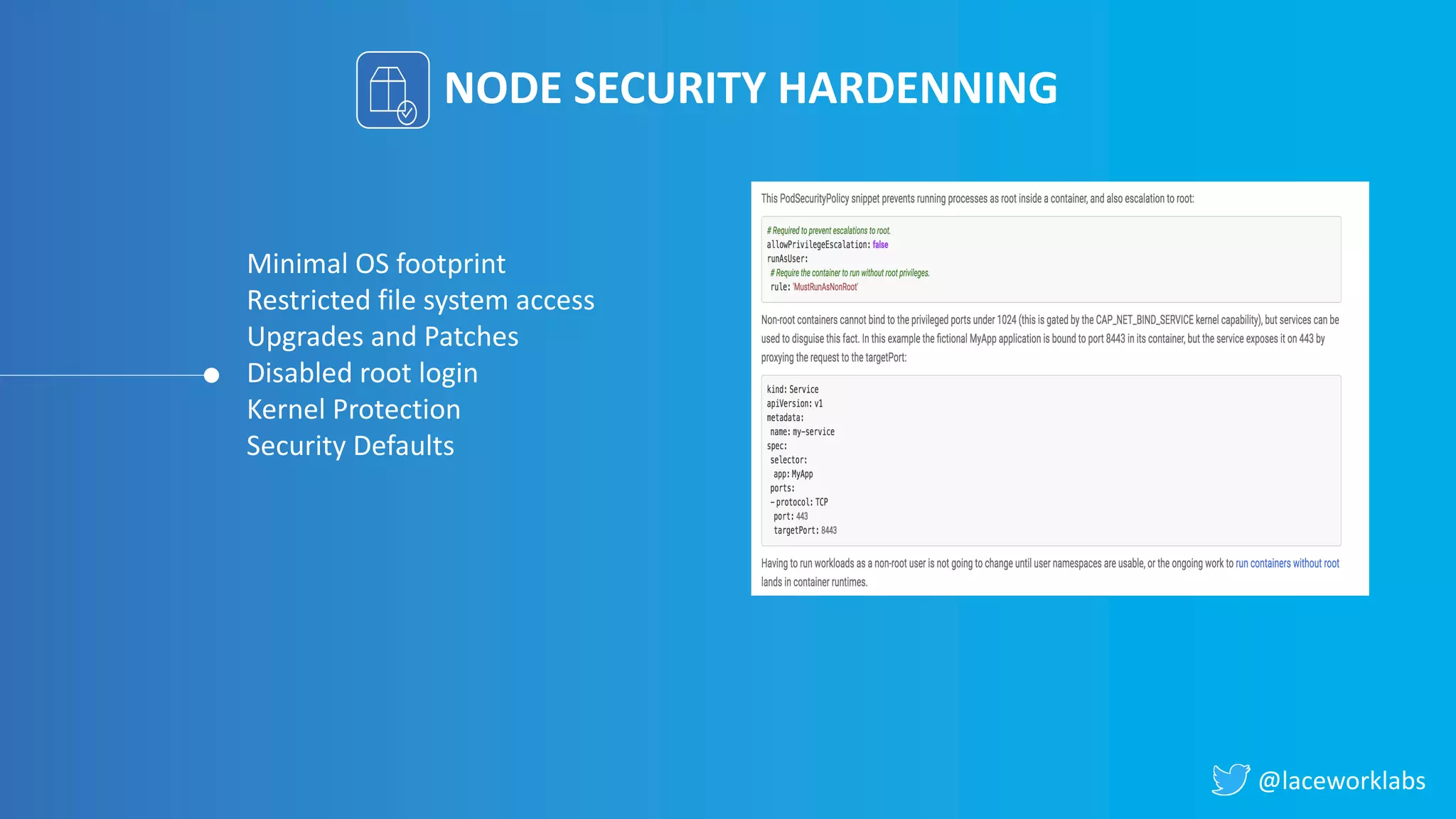
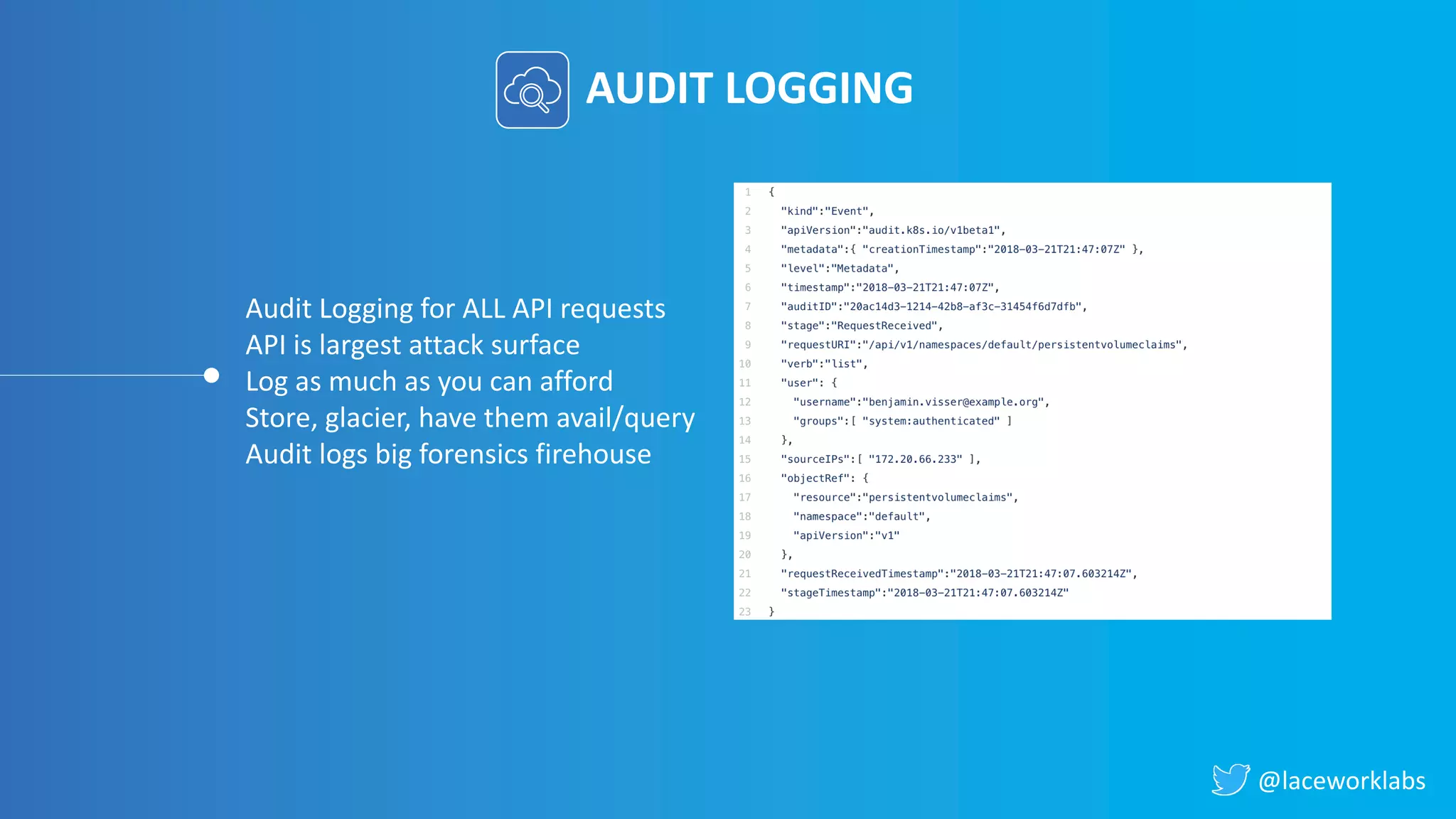
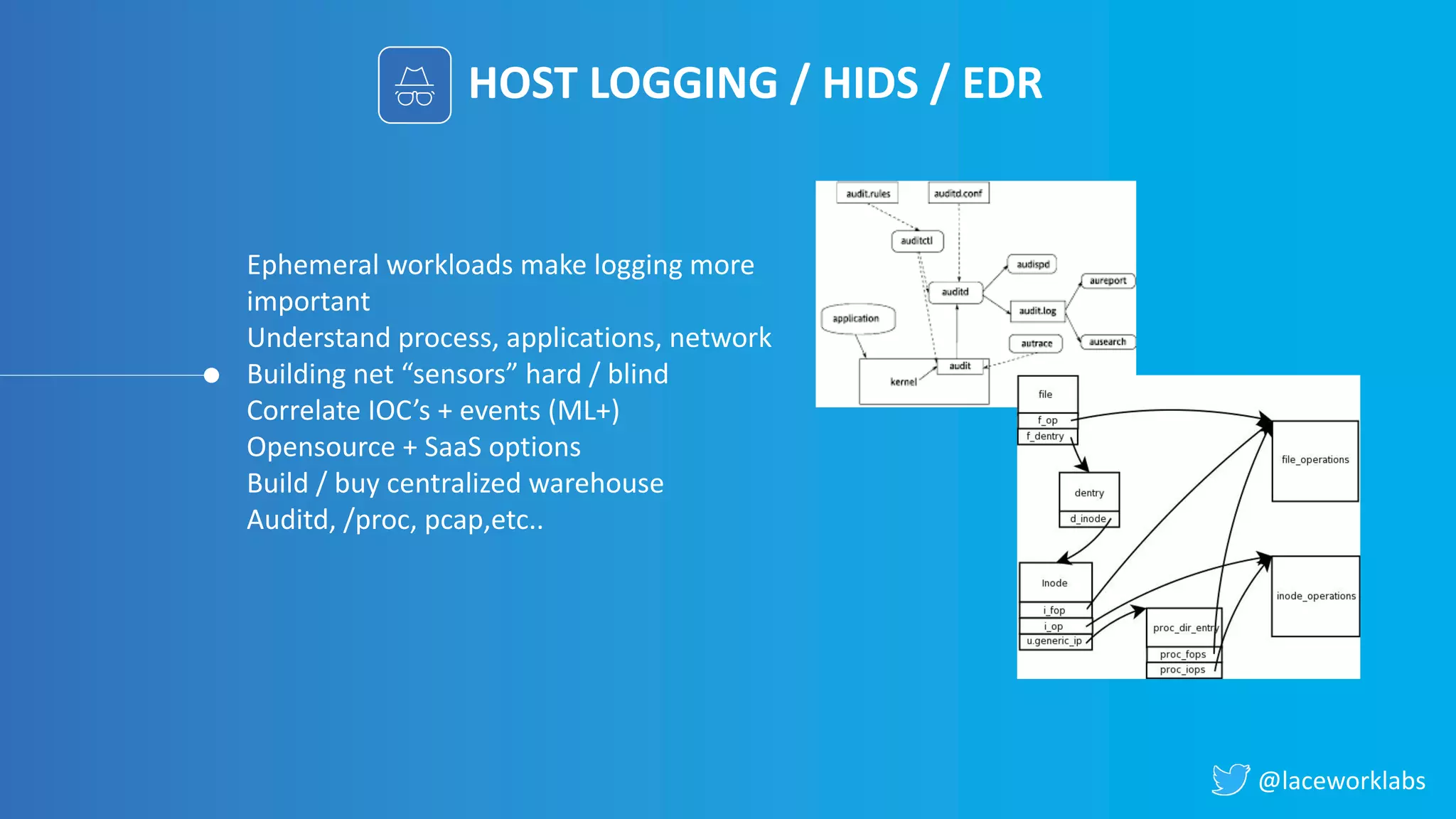
James Condon presented a guide to securing Kubernetes. He began with an overview of Kubernetes architecture and then discussed major risk vectors like exposed Kubernetes components and pod compromise. He demonstrated finding exposed Kubernetes dashboards, API servers, kubelets, and etcd clusters. Condon recommended 10 essential practices for securing Kubernetes, including network security, role-based access control, security boundaries, upgrading, and audit logging. He concluded with resources for further information.