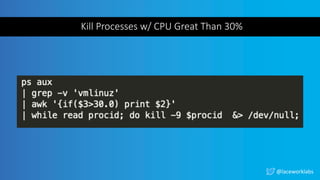
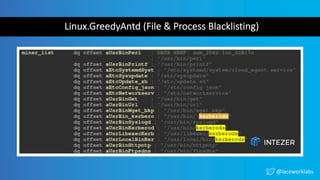
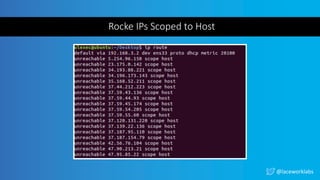
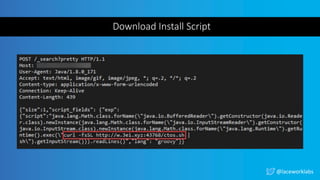
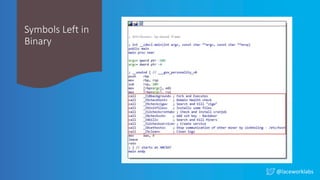
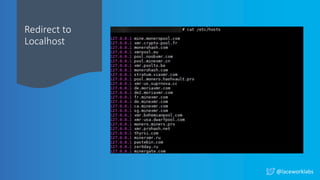
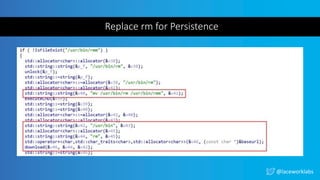
The document presents a case study titled 'Cloud Wars: Episode V - The Cryptojacker Strikes Back' by James Condon, detailing various attacks against cloud services including Redis, Confluence, and campaigns like Pacha vs Rocke. It discusses methods of exploitation, eradication tactics, and provides links to further reading on related cyber threats. The content emphasizes security measures and is aimed at enhancing cloud security awareness among professionals.