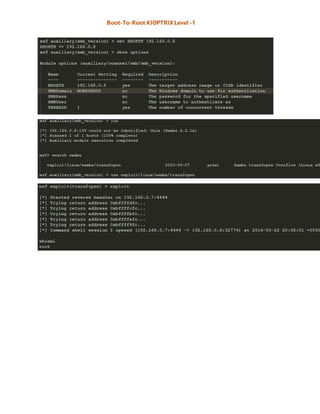
The document discusses the kioptrix level 1 boot-to-root challenge on Vulnhub, which aims to teach users basic tools and techniques for vulnerability assessment and exploitation. It outlines the steps to discover the vulnerable IP using netdiscover and nmap, identify open ports, and exploit vulnerabilities using tools like nikto and Metasploit. The author provides helpful resources and links for downloading the kioptrix VM and required exploits.