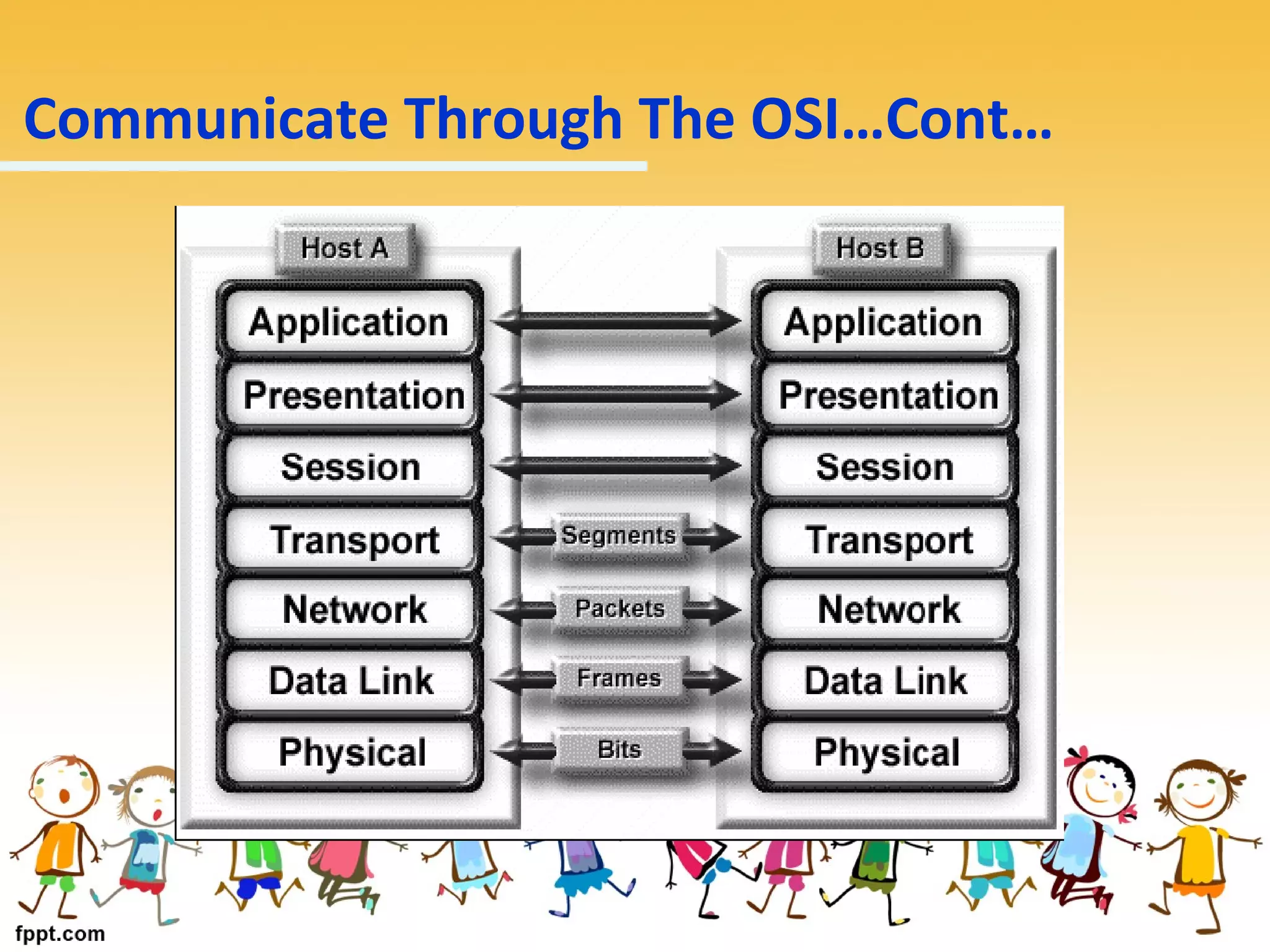
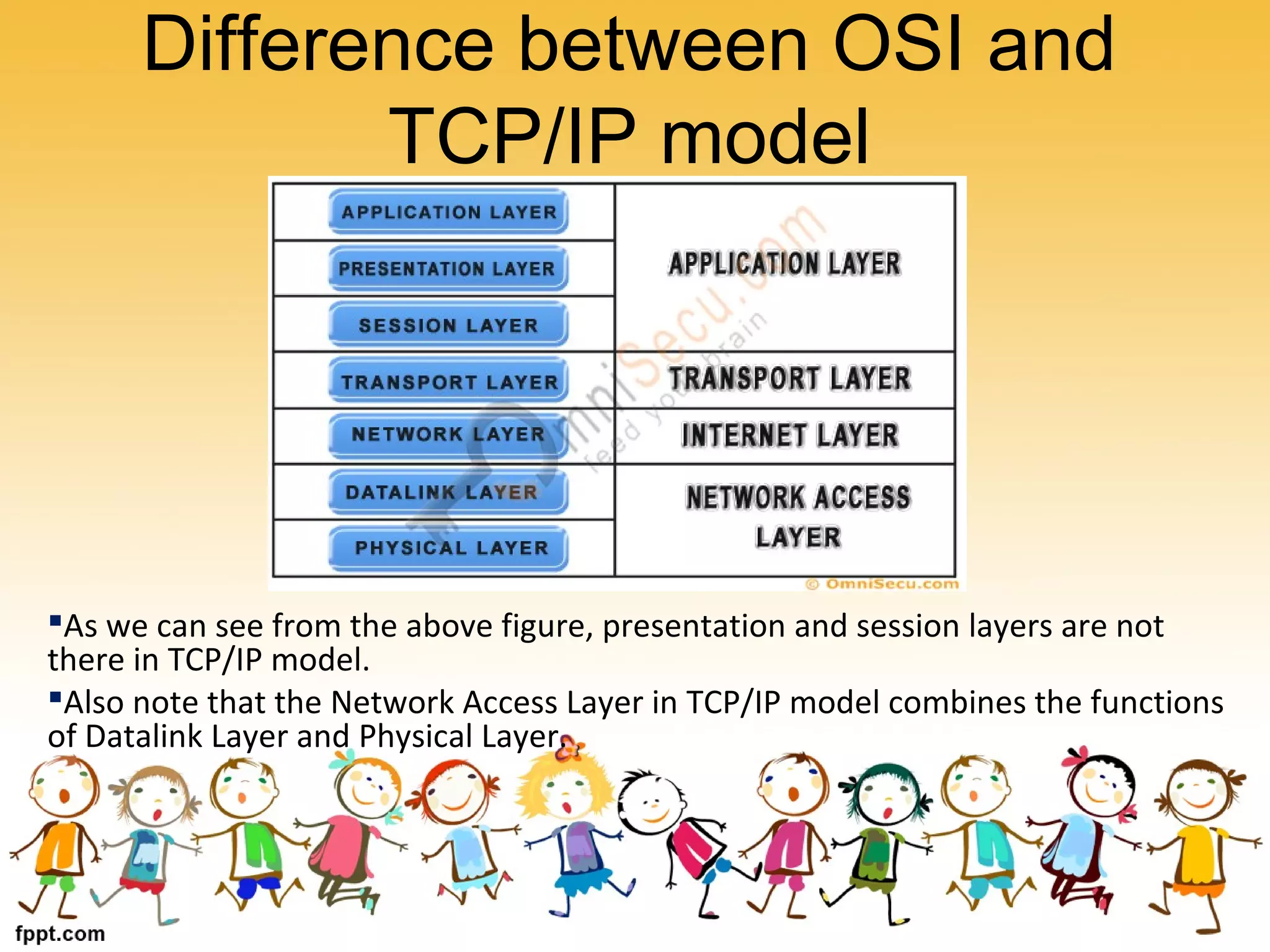
The document provides information about the OSI model and network protocols. It describes the seven layers of the OSI model from the physical layer to the application layer. It explains the functions of each layer, such as the physical layer being responsible for transmitting binary digits between devices and the transport layer ensuring packets are not lost during transmission. It also discusses the differences between TCP and UDP network protocols, with TCP providing reliable transmission and UDP being faster but less reliable. The document defines MAC addresses as unique identifiers for network devices and how they differ from IP addresses.