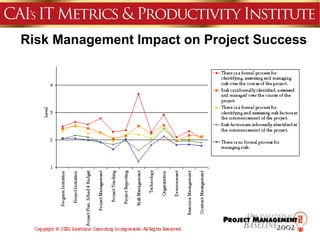
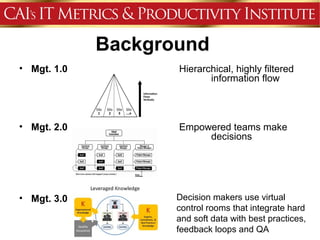
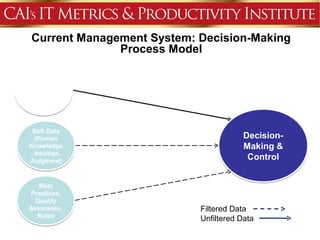
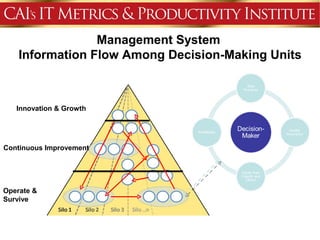
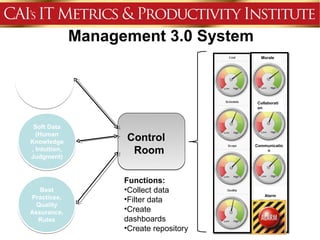
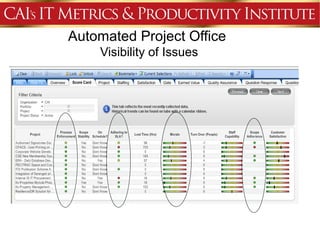
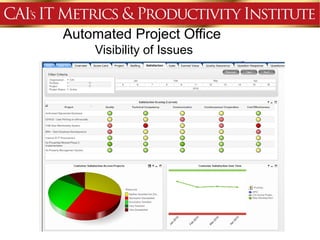
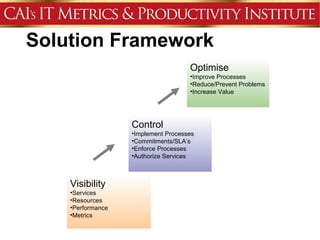
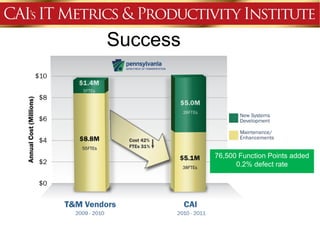
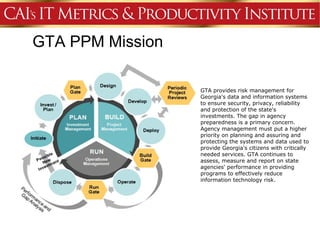
This document discusses an agenda for a presentation on IT project management best practices and risk management. The agenda includes introductions, discussing IT project management basics and industry best practices, IT risk management thought leadership, managing application support risks using Management 3.0 principles, an application management case study, and managing project risks. It also provides background on the presenting organization, Computer Aid Inc., which is an IT consulting firm.