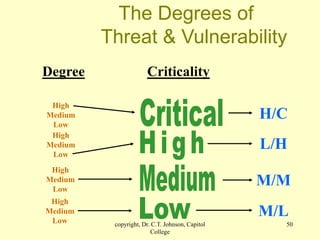
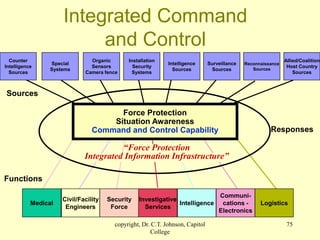
The document discusses physical security and risk management. It begins with definitions of physical security and describes different types of security areas like principles of safeguarding, critical and restricted areas, and security-controlled areas. The document then discusses historical examples of physical security structures like the Great Wall of China and Mesa Verde cliff dwellings. It also covers key risk management concepts such as assets, threats, vulnerabilities, risk analysis, and the risk management process of identifying risks and countermeasures. The overall topic is introducing principles of physical security and risk analysis.