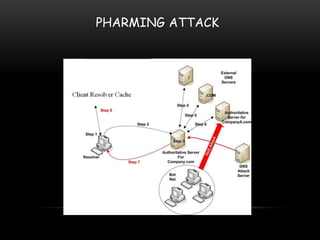
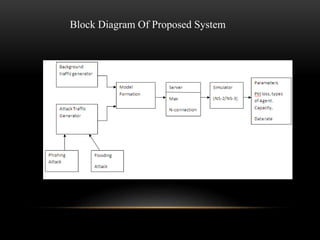
This document summarizes a synopsis on analyzing and preventing pharming attacks on hybrid networks. The objectives are to analyze pharming attacks using Java and prevent users from losing confidential information. Pharming attacks are increasing and are an enhanced version of phishing attacks. The proposed system detects pharming attacks through dual analysis of IP address checks and web page content comparisons. It uses character-level and word-level N-gram algorithms to compare legitimate and fraudulent pages. The system was implemented in Java due to its portability across operating systems. The goal is to avoid attacks from fake sites and prevent information loss.