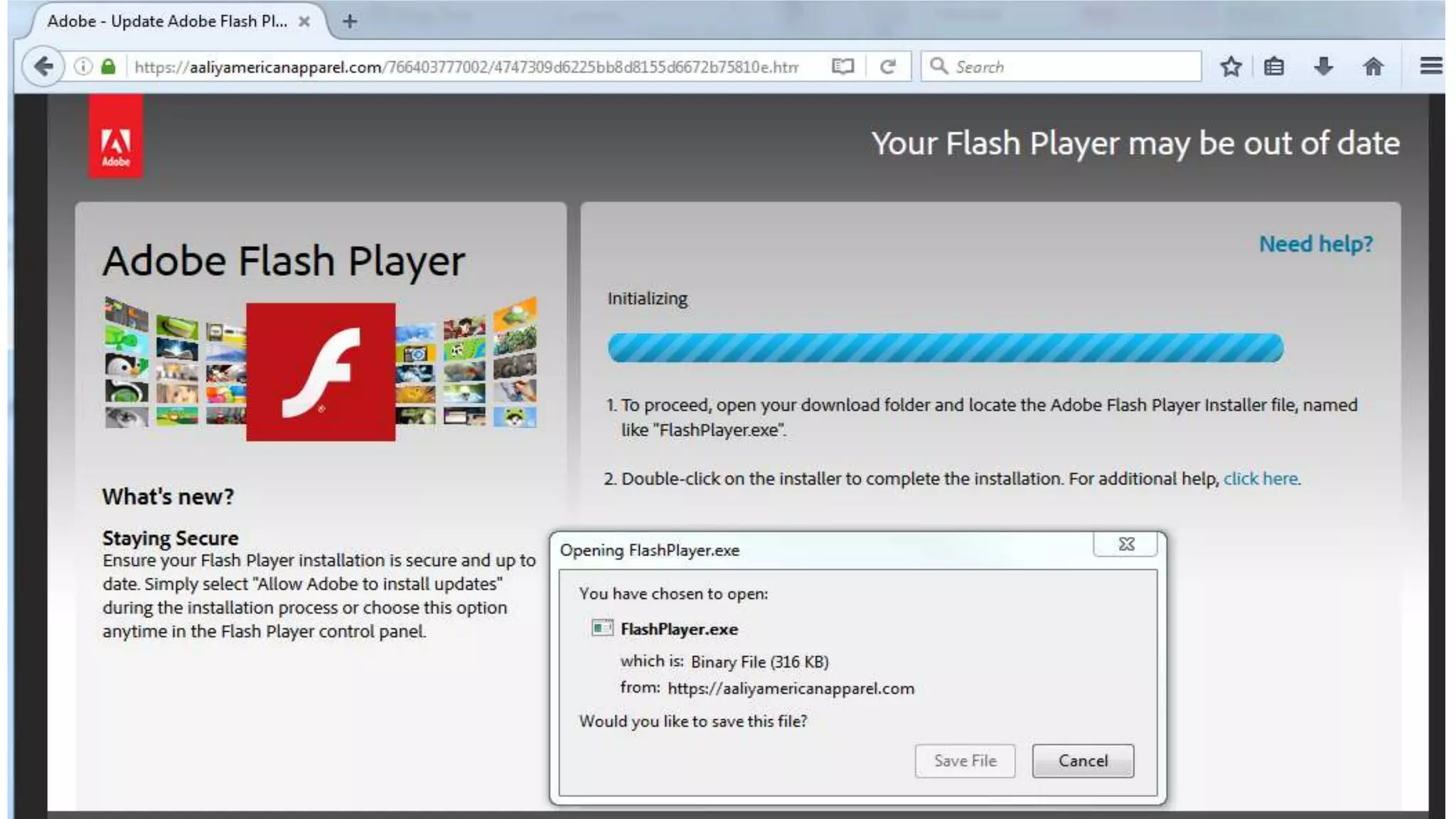
Cerdant celebrated its 15th anniversary in January 2017, having doubled its revenues and customer base to 700 in the past three years. The document highlights recent enhancements in security measures, including improved incident detection capabilities and challenges posed by evolving threats such as ransomware. It emphasizes the need for adaptation in security strategies, as traditional antivirus measures are becoming less effective due to the rise of sophisticated malware and encrypted web traffic.