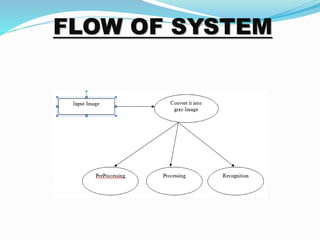
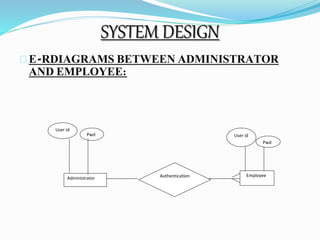
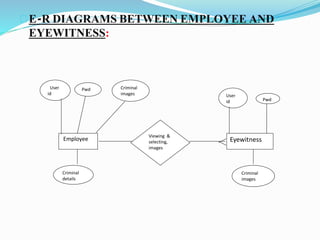
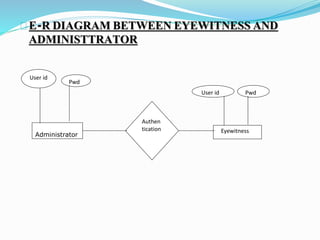
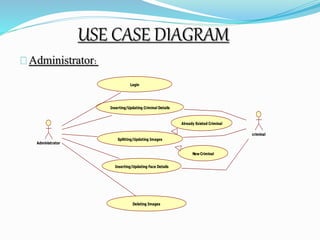
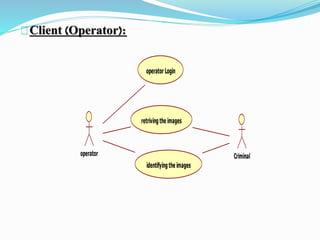
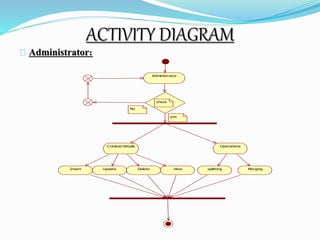
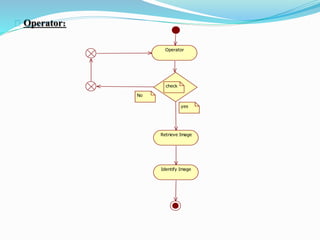
This document describes a proposed prisoner face detection system with 4 group members and a faculty guide. It discusses the existing manual criminal identification system and its limitations. The proposed system would use face detection and image slicing to allow eyewitnesses to identify criminals by facial features stored in a database. It provides advantages like being less complex and requiring no direct contact. The system design involves administrators adding criminal data and images and operators retrieving images for eyewitnesses.