Embed presentation
Downloaded 11 times

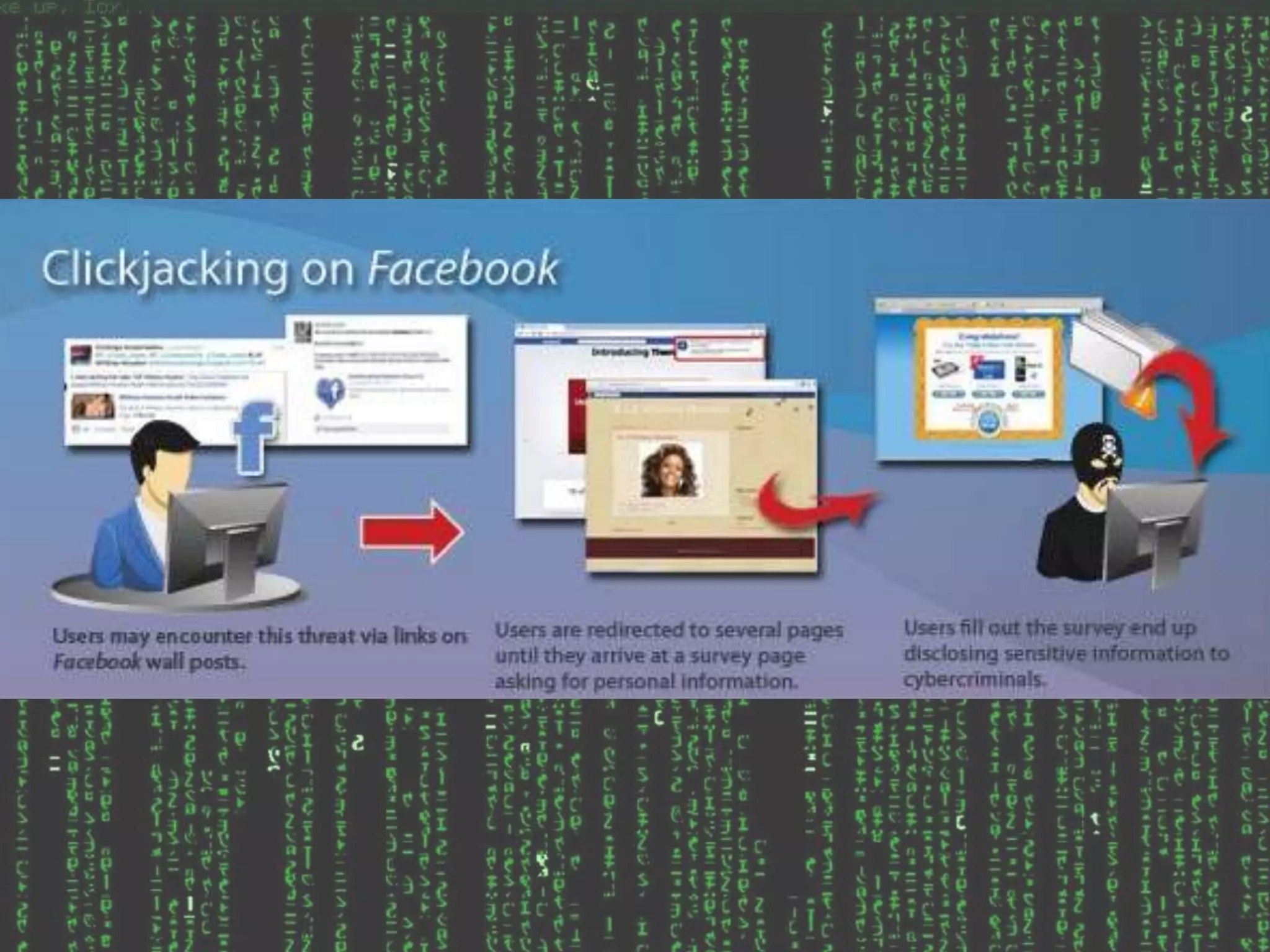

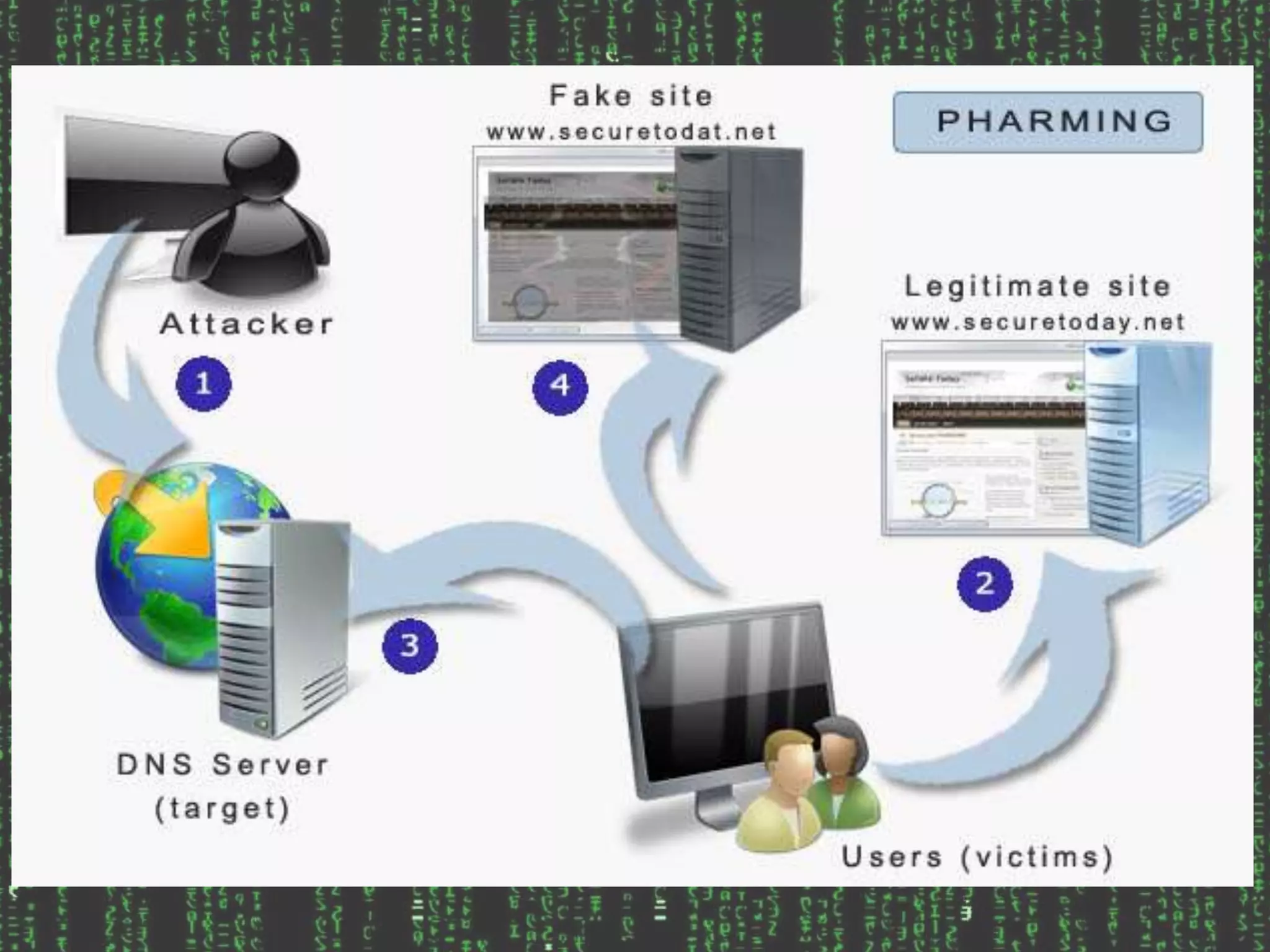
Phishing, pharming, and clickjacking are forms of hijacking information from computer users to steal identities. Phishing uses fraudulent emails and legitimate-looking websites to extract financial information, with 23% of recipients opening phishing emails. Clickjacking tricks users into clicking buttons or links that run malicious software. Pharming redirects users from real websites to fraudulent ones to steal confidential data, having redirected at least 1,300 internet domains. These tactics undermine online security and privacy.






