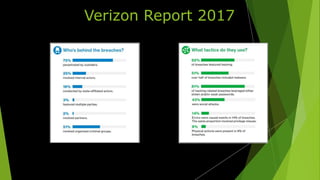
The document discusses strategies to improve cybersecurity and reduce the risk of data breaches, emphasizing the importance of understanding security odds based on the 2017 Verizon report. Key recommendations include enforcing strong password policies, implementing multi-factor authentication, network segmentation, and employee training to mitigate the human factor in security incidents. The author encourages taking incremental steps to enhance security practices and highlights that no system is completely hack-proof, but appropriate measures can deter most attacks.