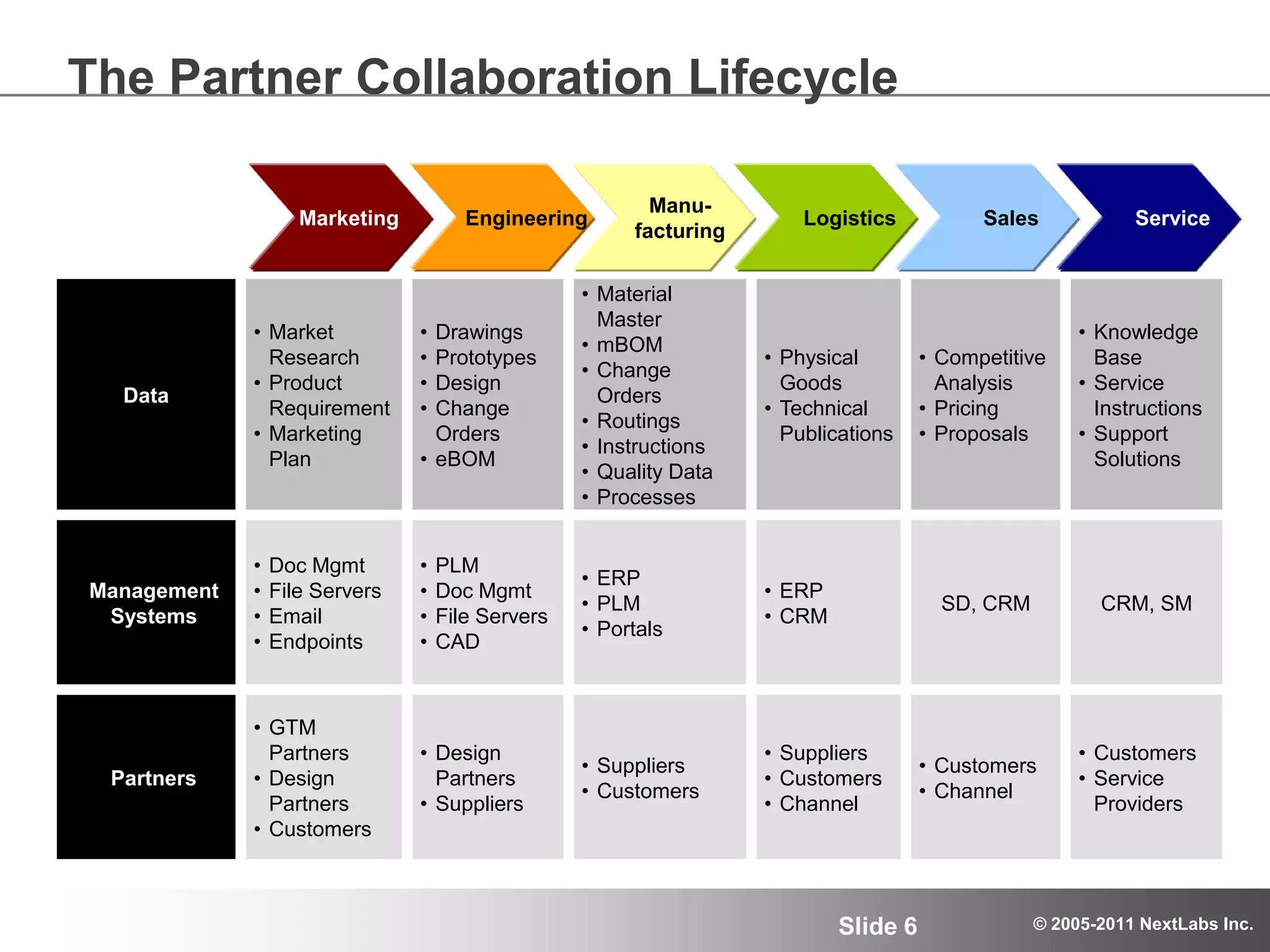
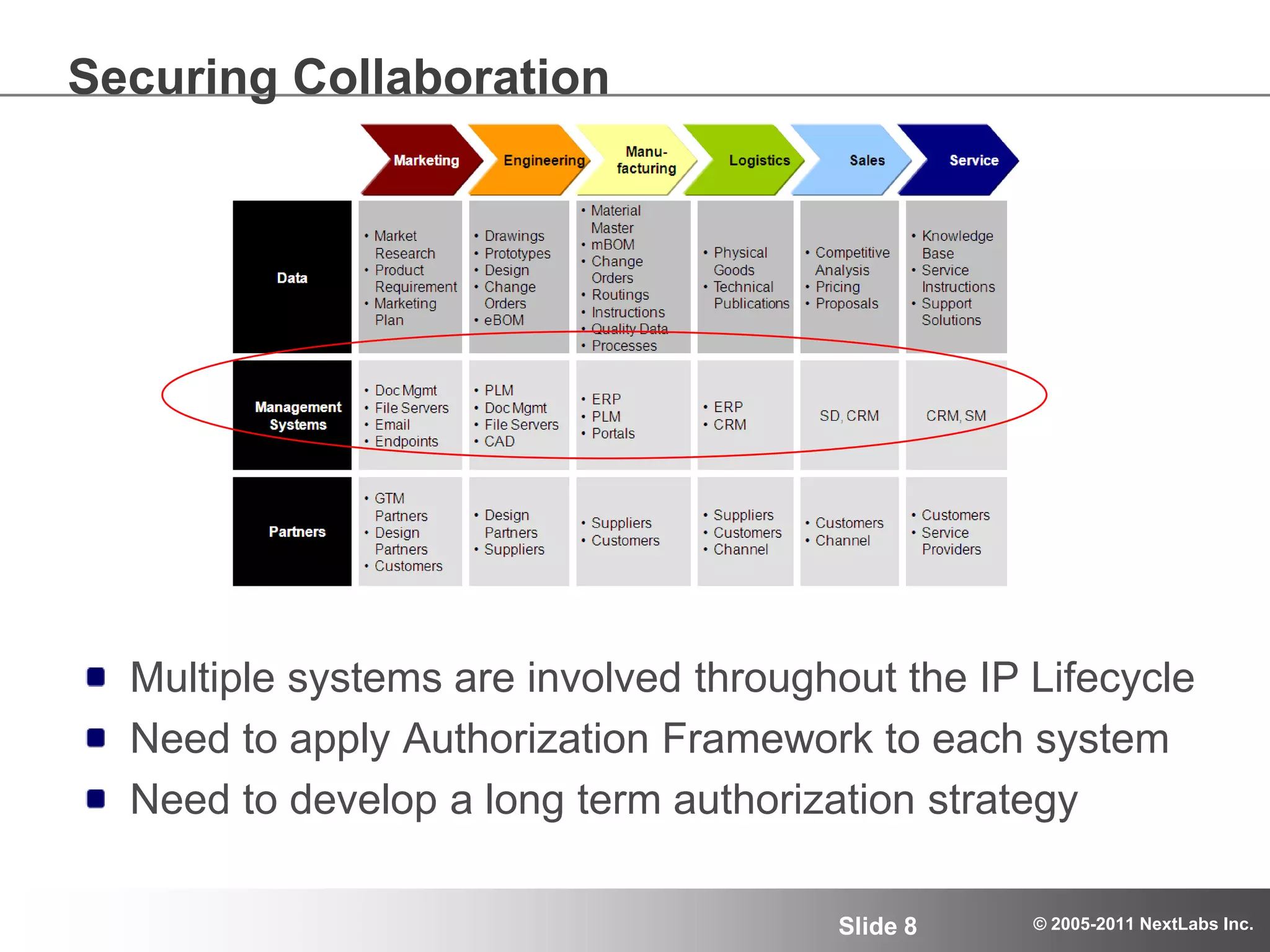
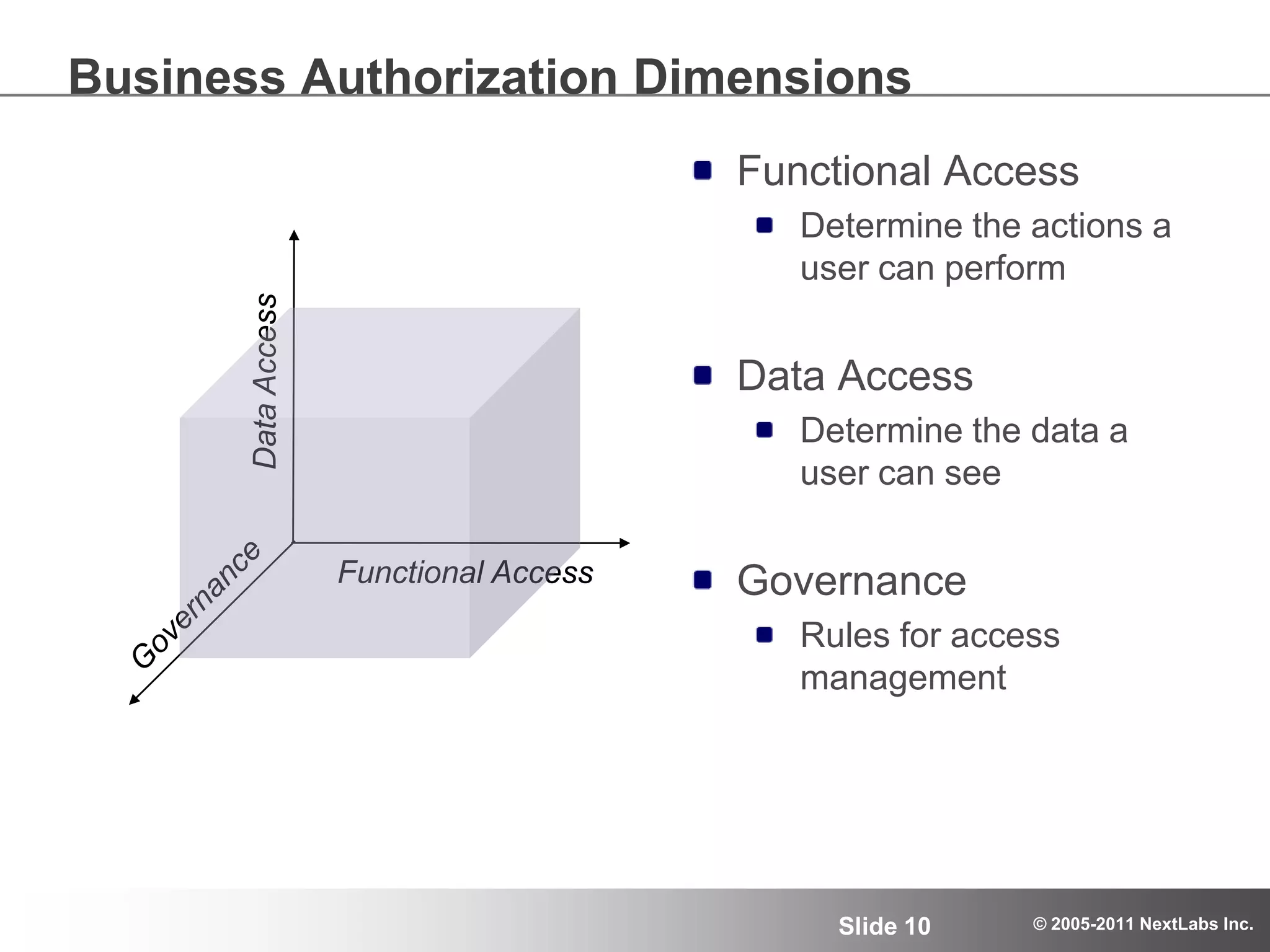
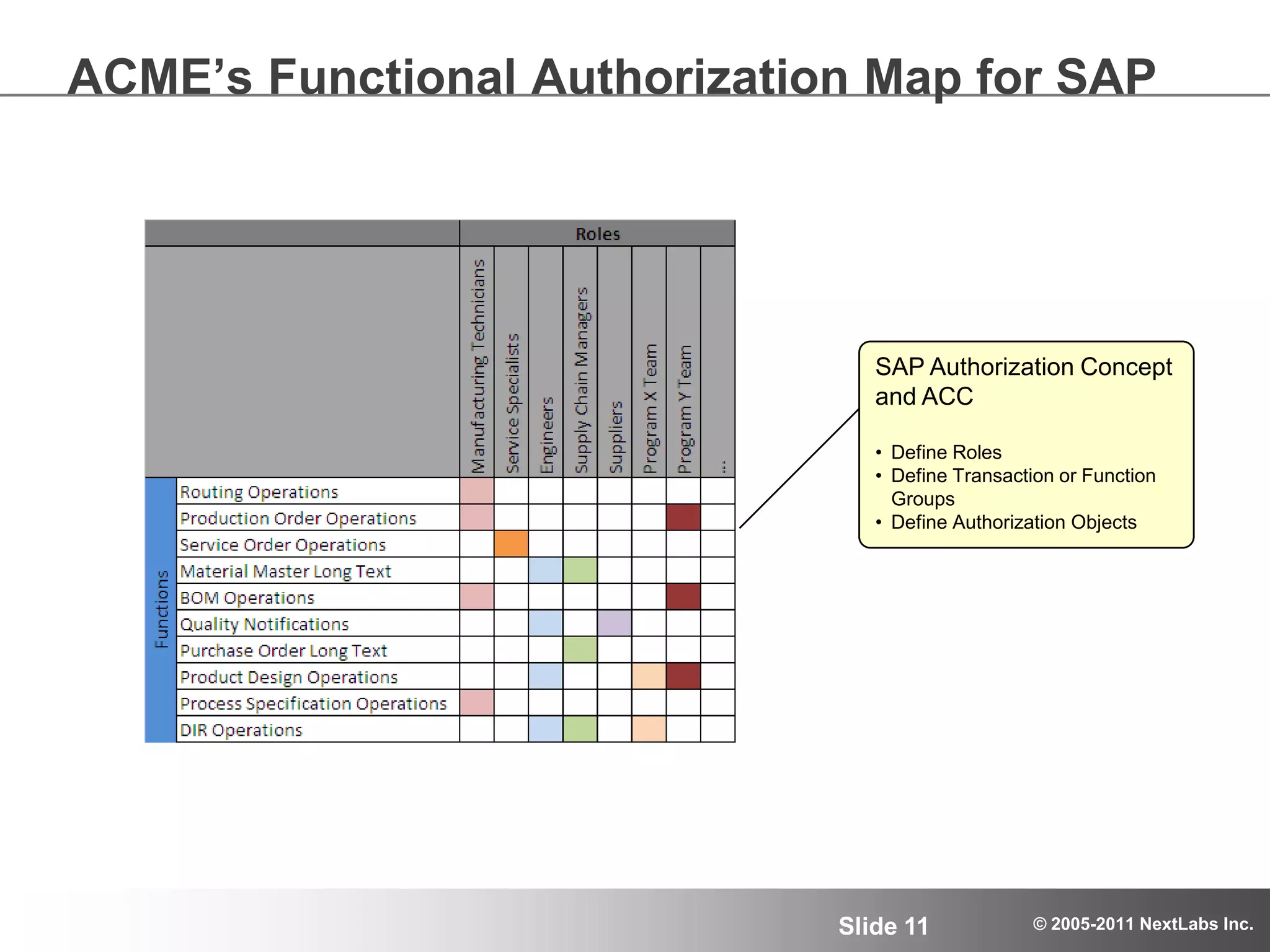
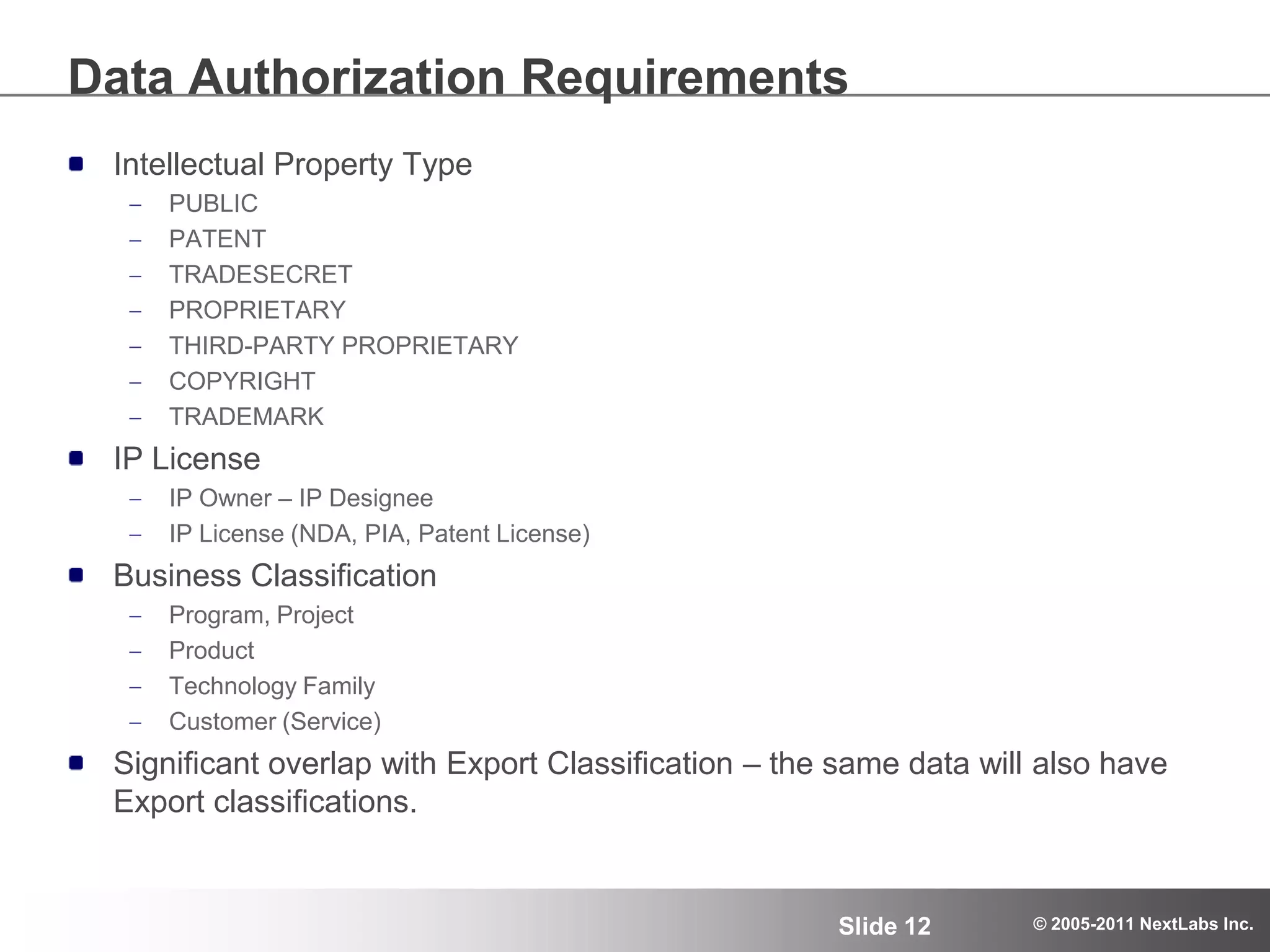
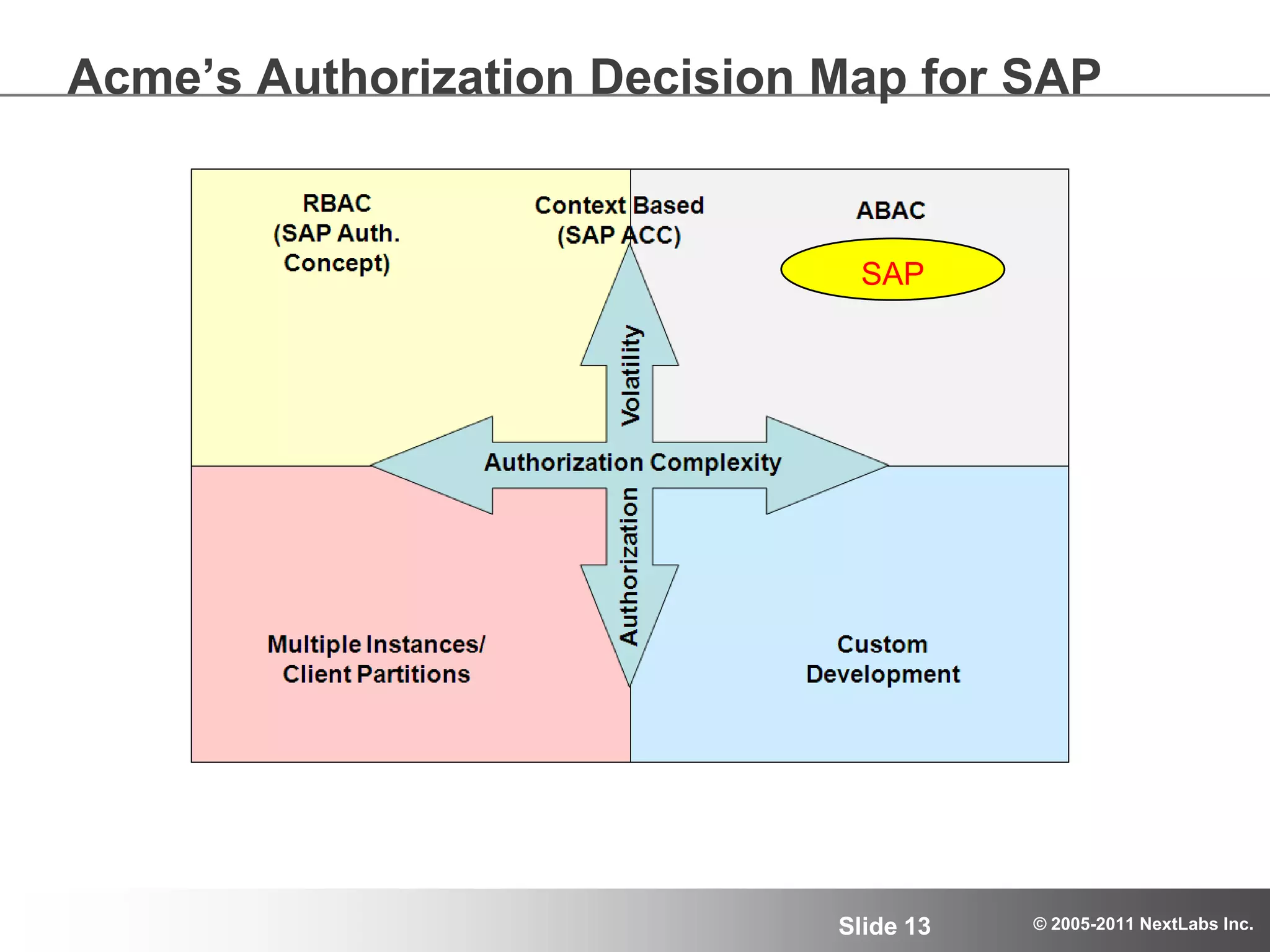
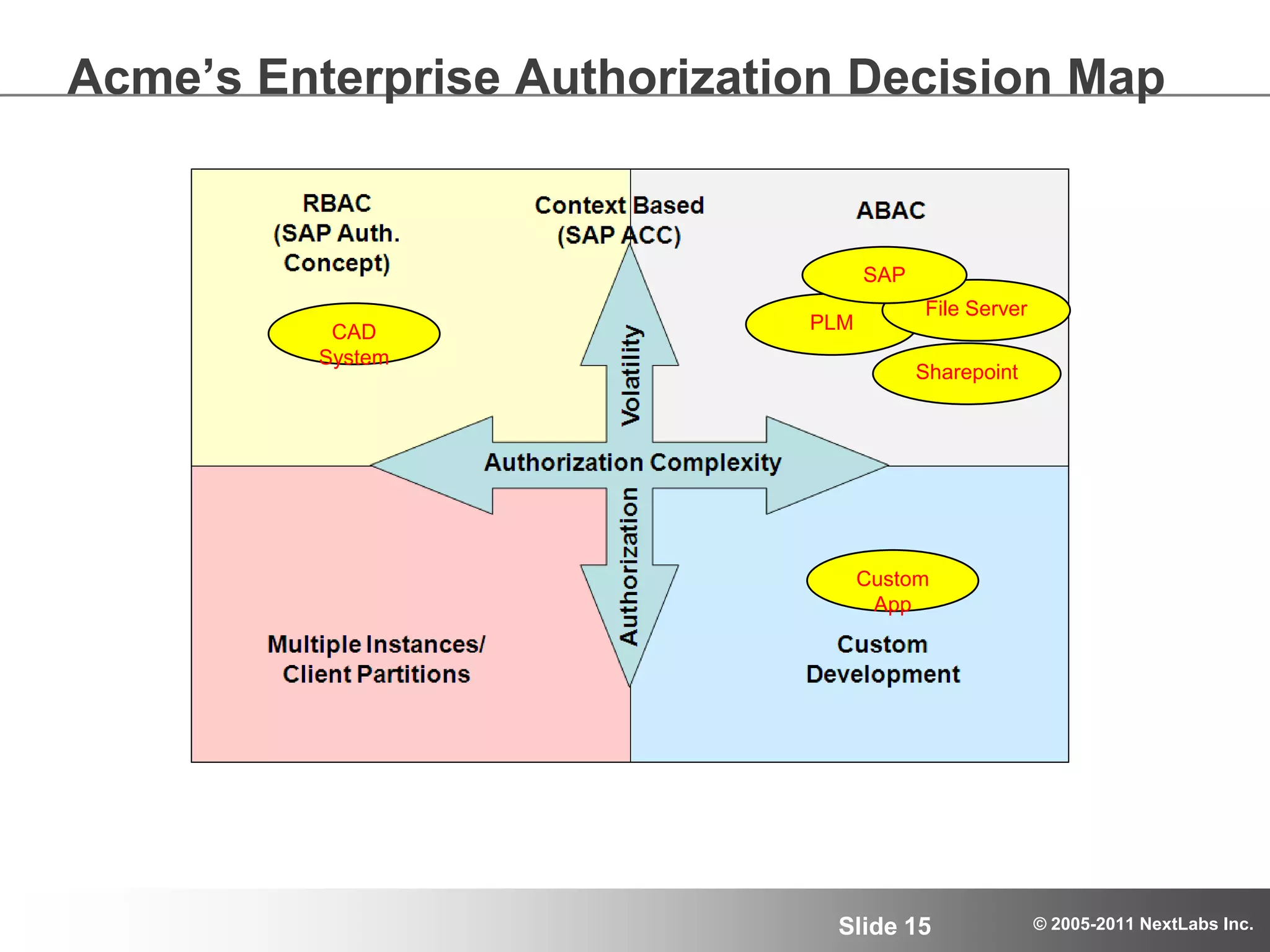
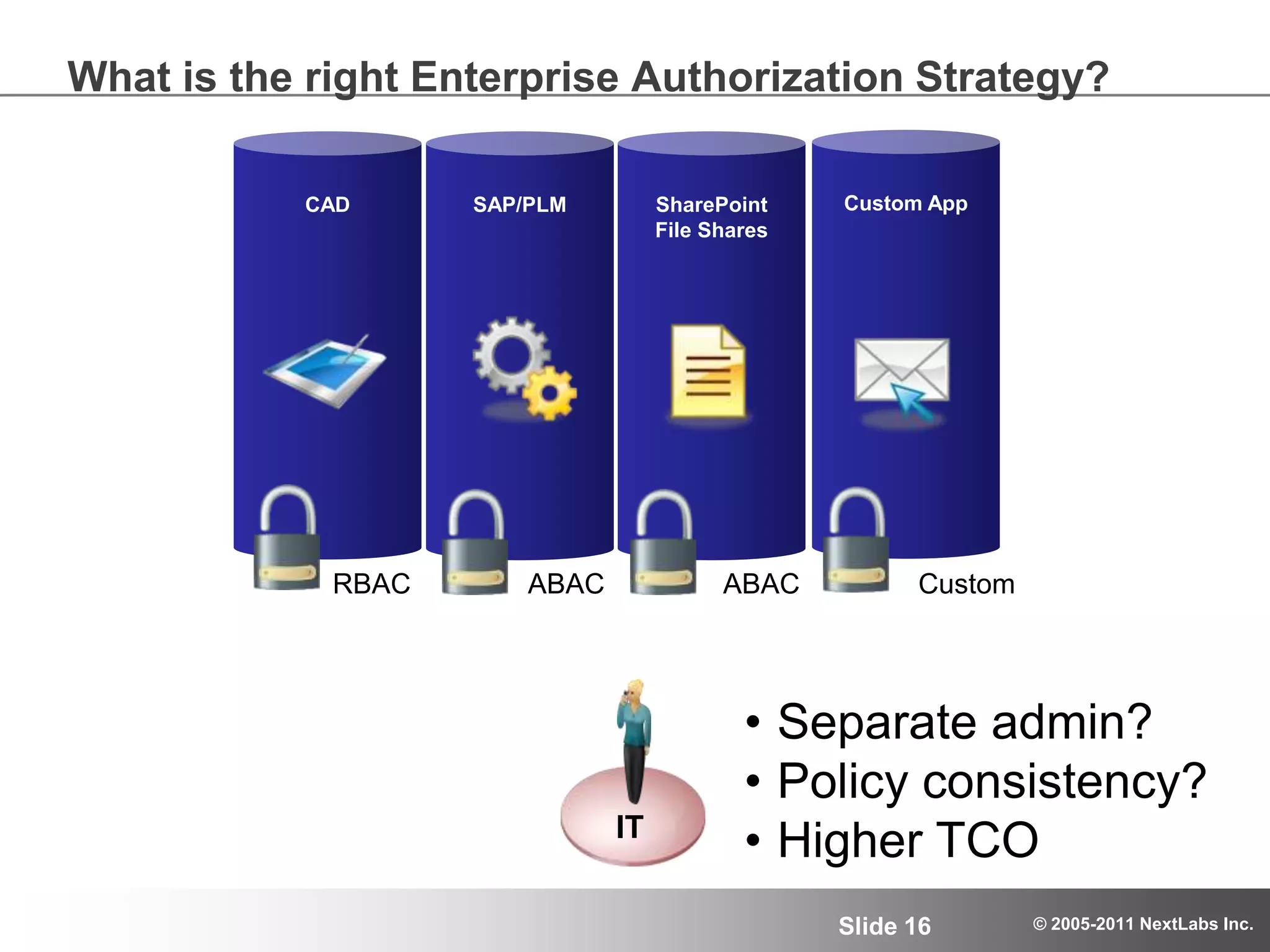
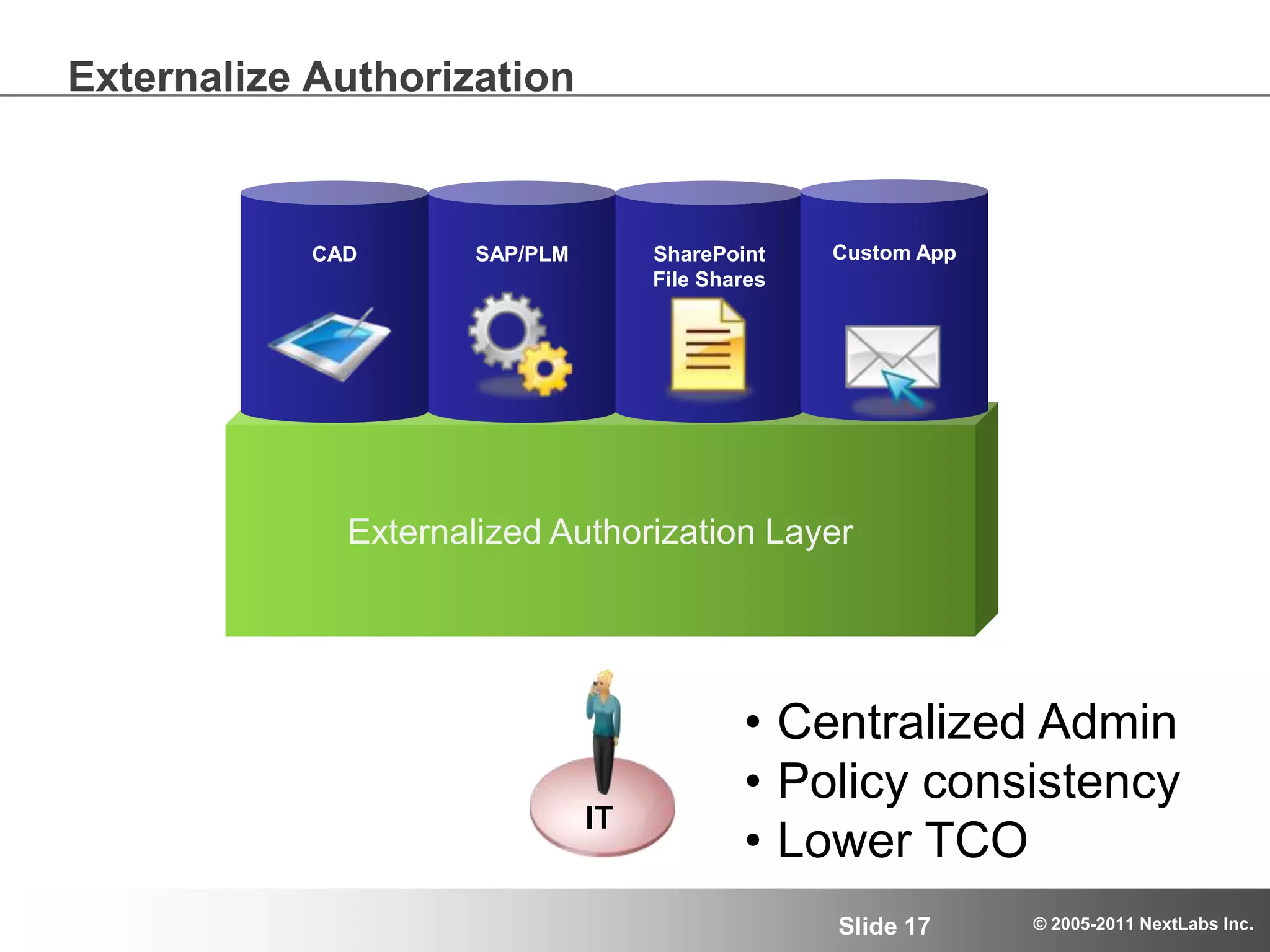
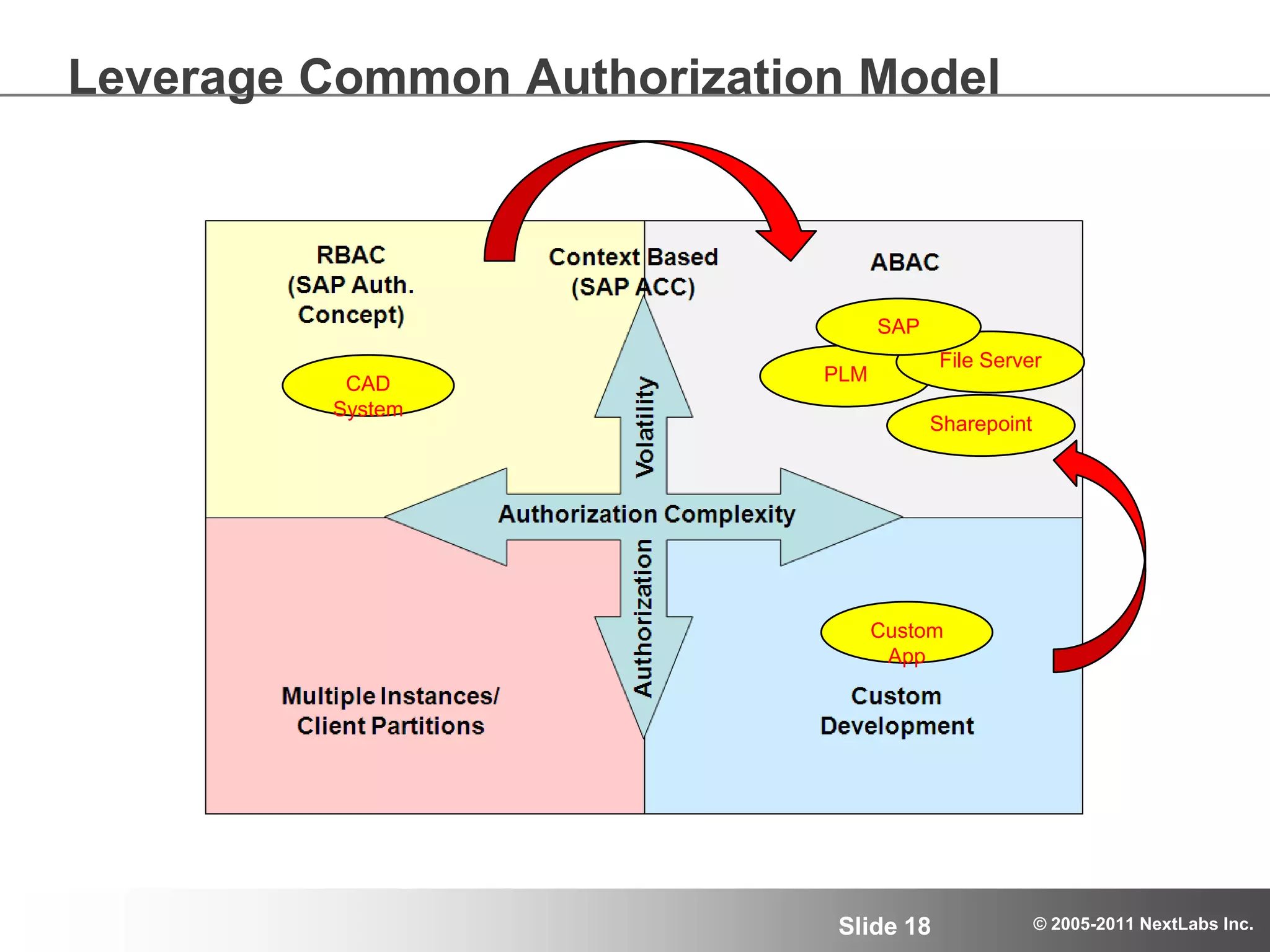
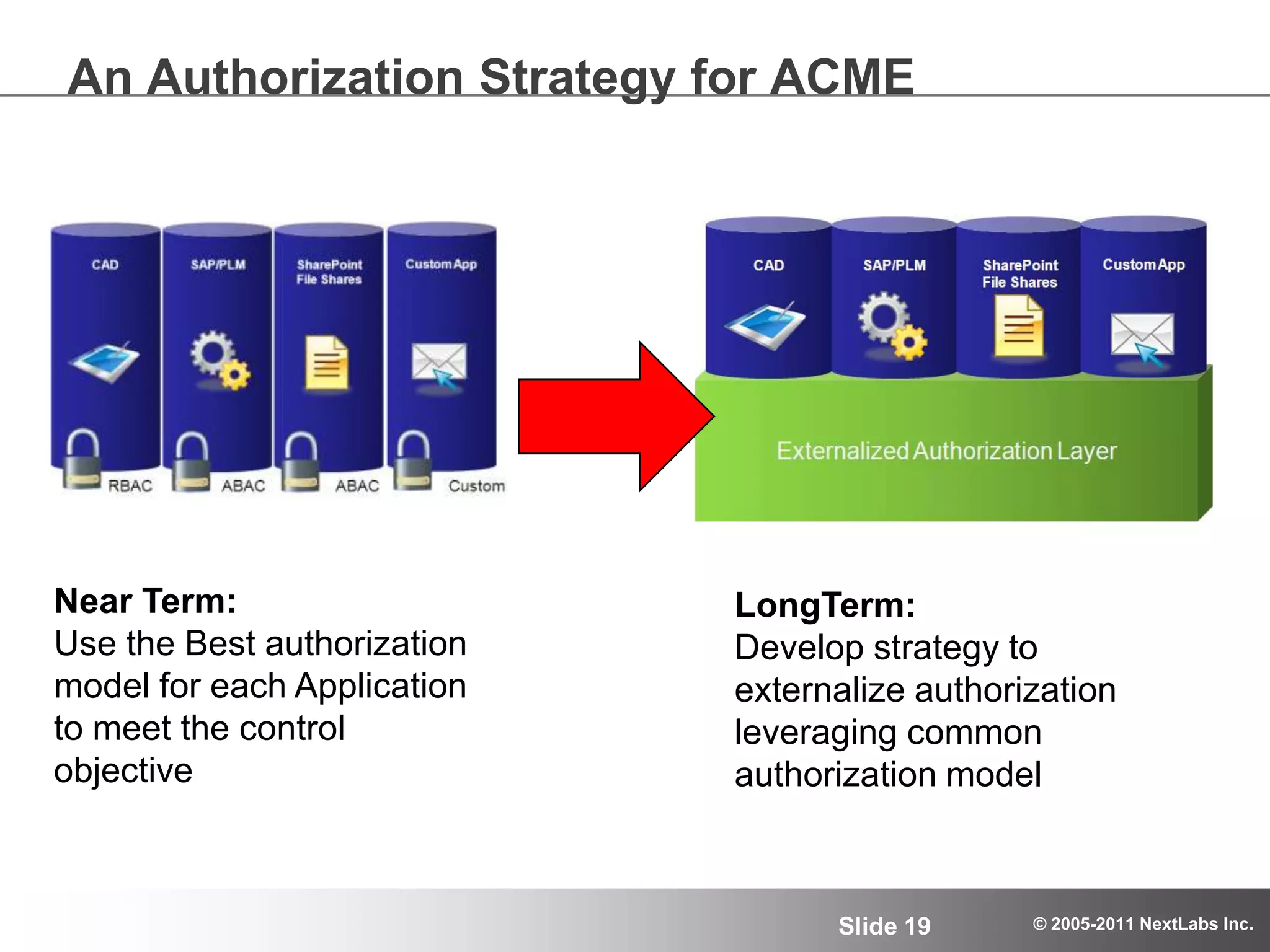
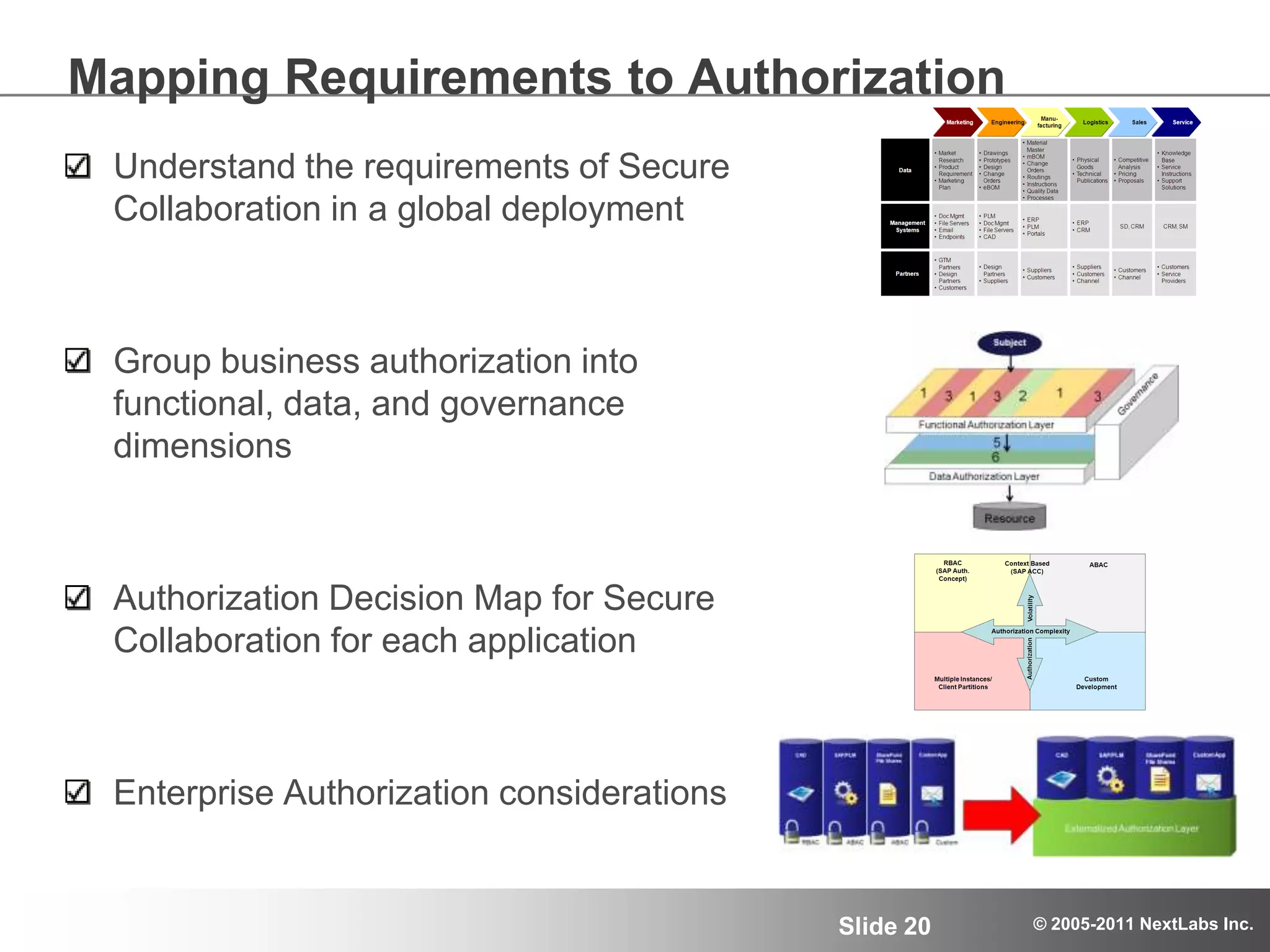
The document details an advanced authorization model for secure partner collaboration within global SAP deployments, focusing on the partner collaboration lifecycle and authorization tools. It discusses enterprise authorization considerations, the separation of authorization dimensions, and the importance of an effective long-term authorization strategy through practical models and tools. Additionally, the content emphasizes the need for managing intellectual property and ensuring compliance in diverse operational contexts.