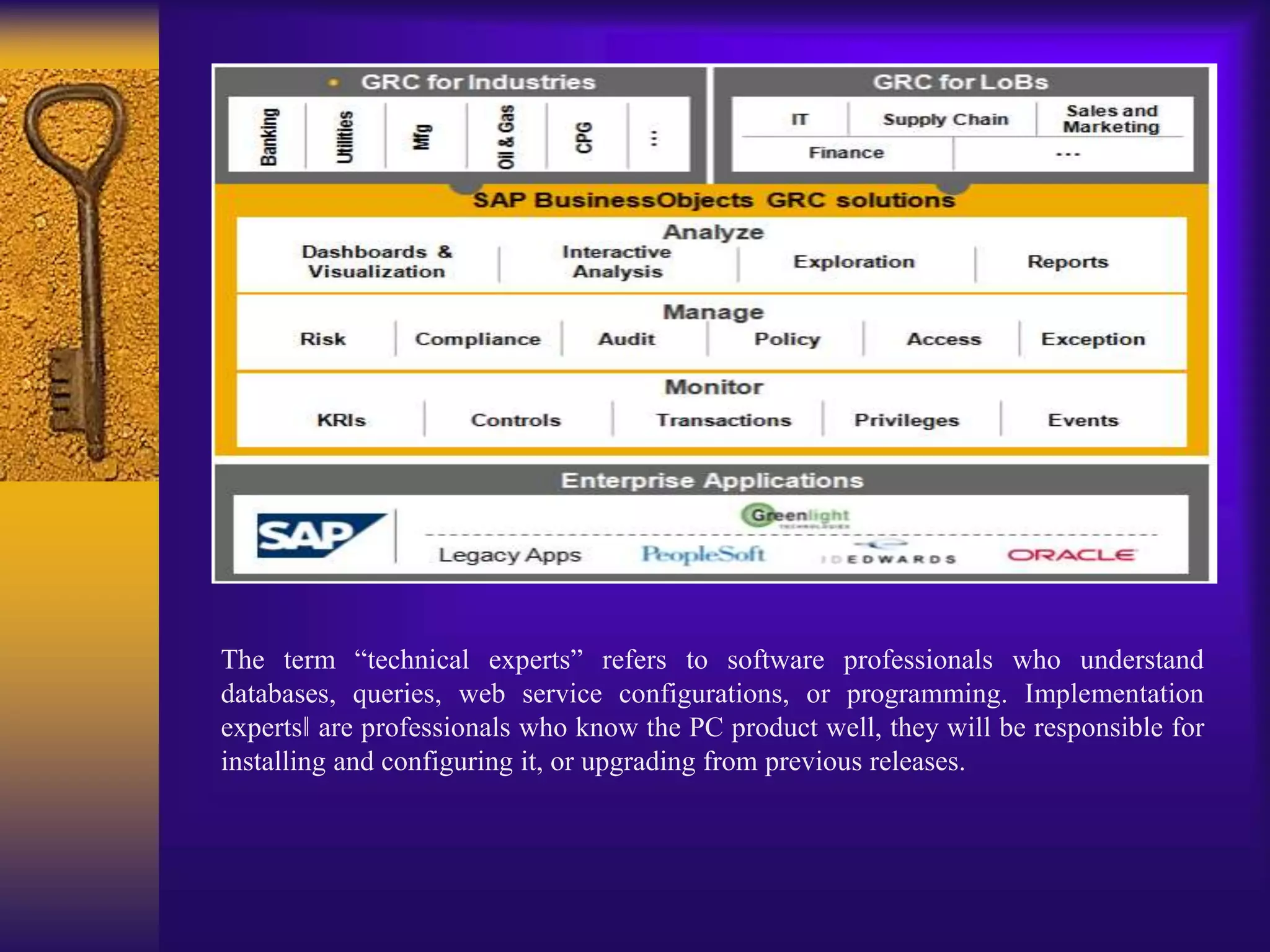
1) SAP Process Control is a software solution that enables organizations to manage compliance and policies. It allows monitoring of internal controls and proactively remediating issues.
2) The software provides automated monitoring of backend systems and processes. It extracts data from systems like SAP ERP and CRM and evaluates it using business rules to detect deficiencies.
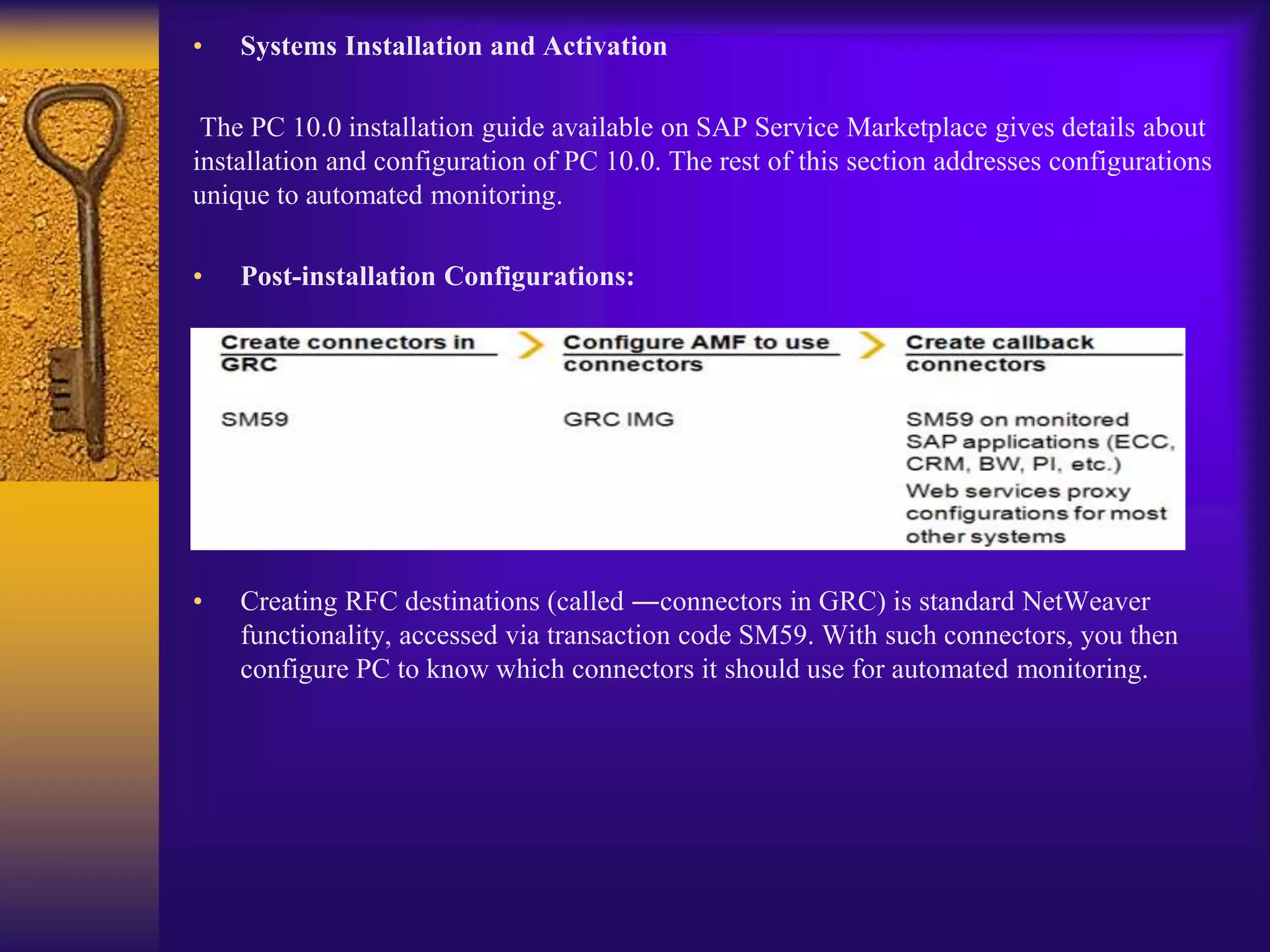
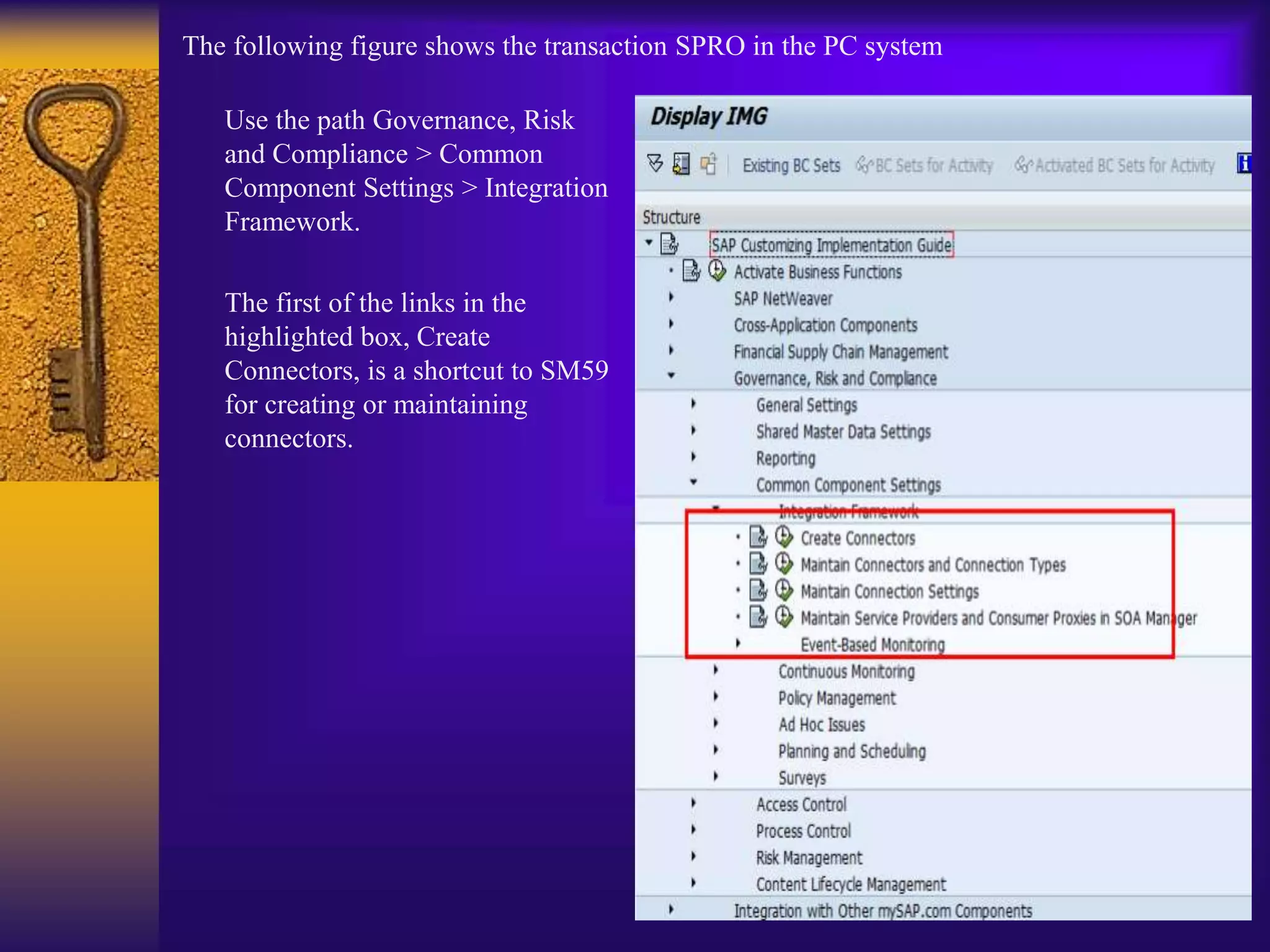
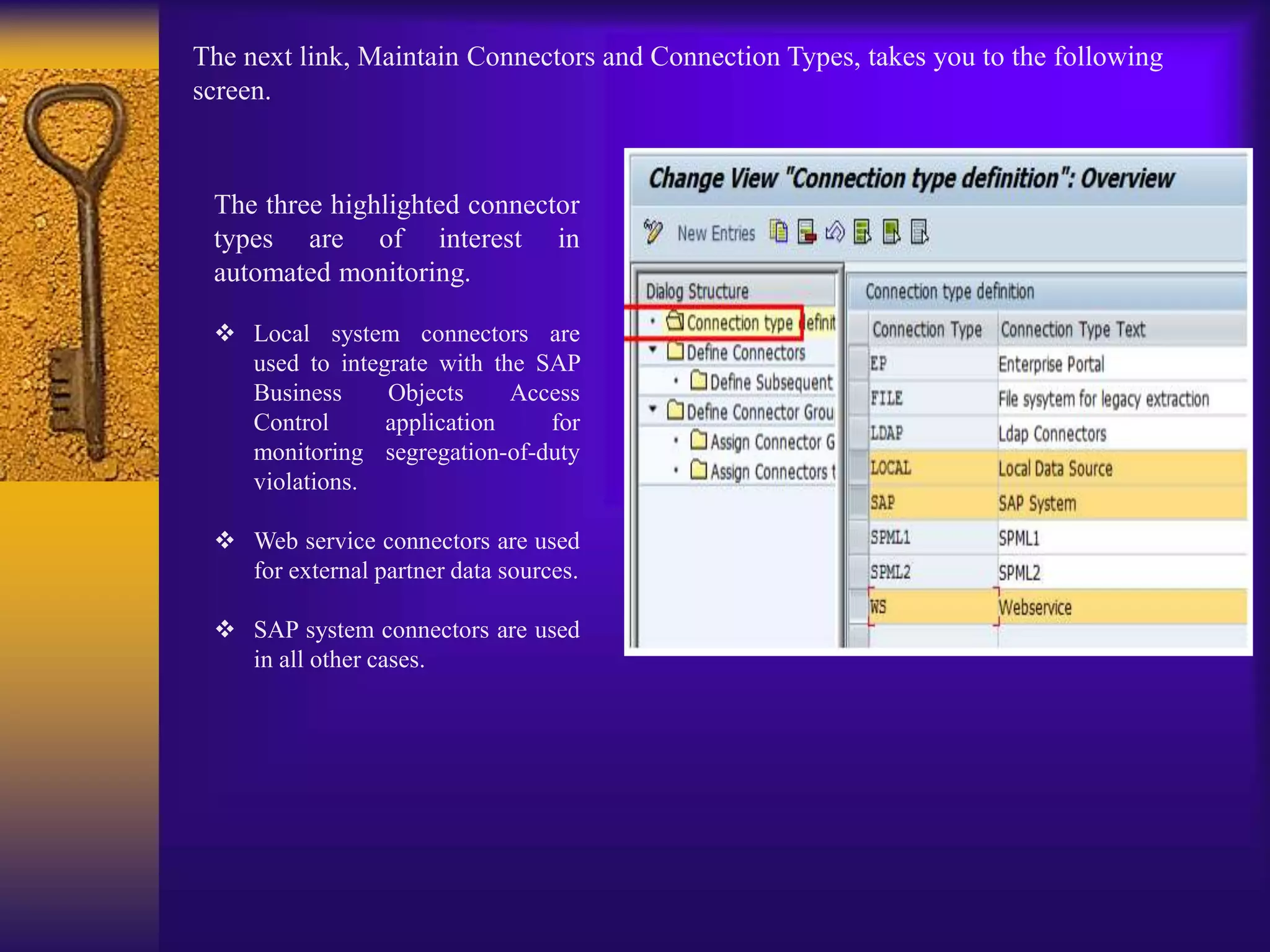
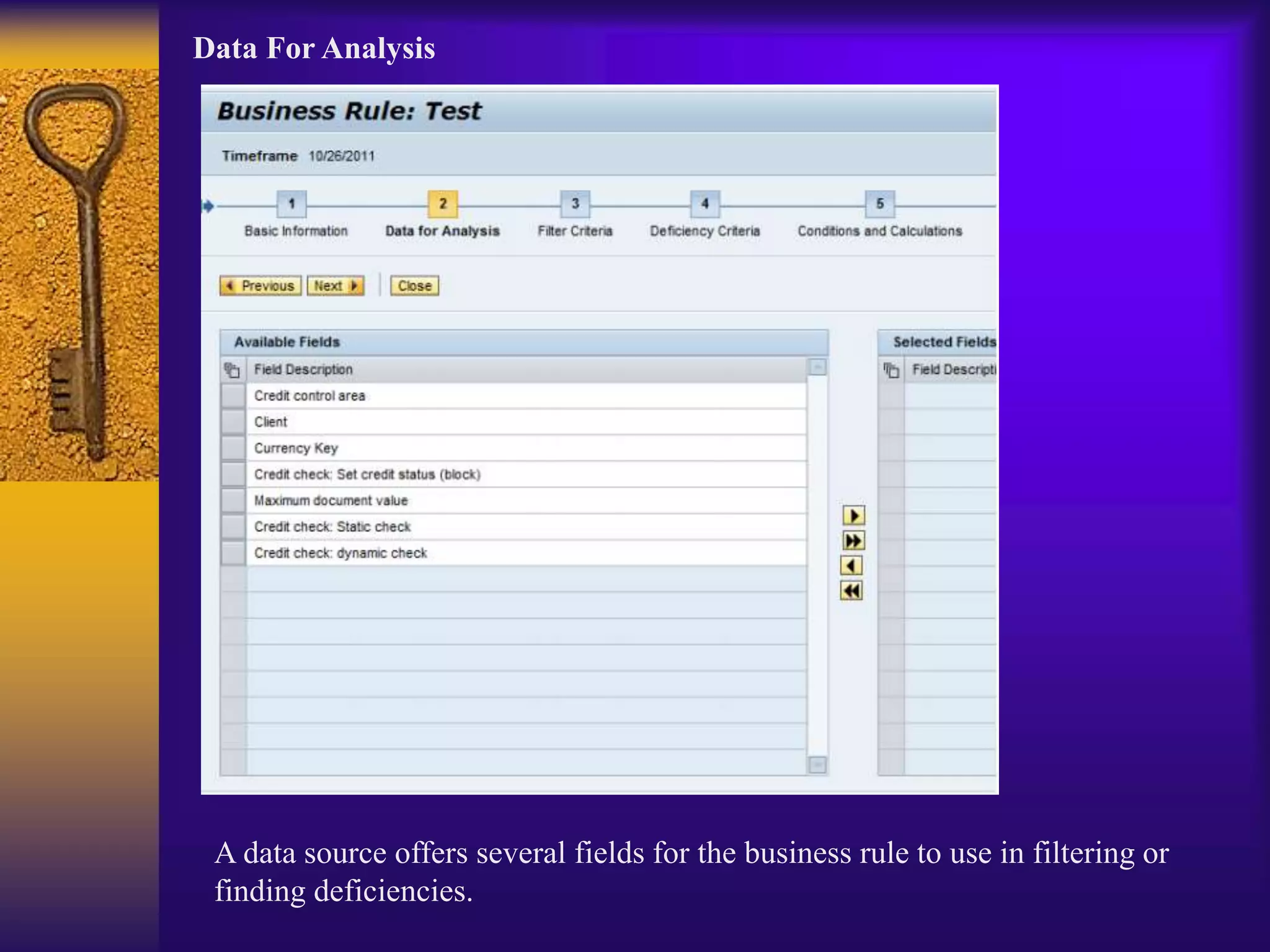
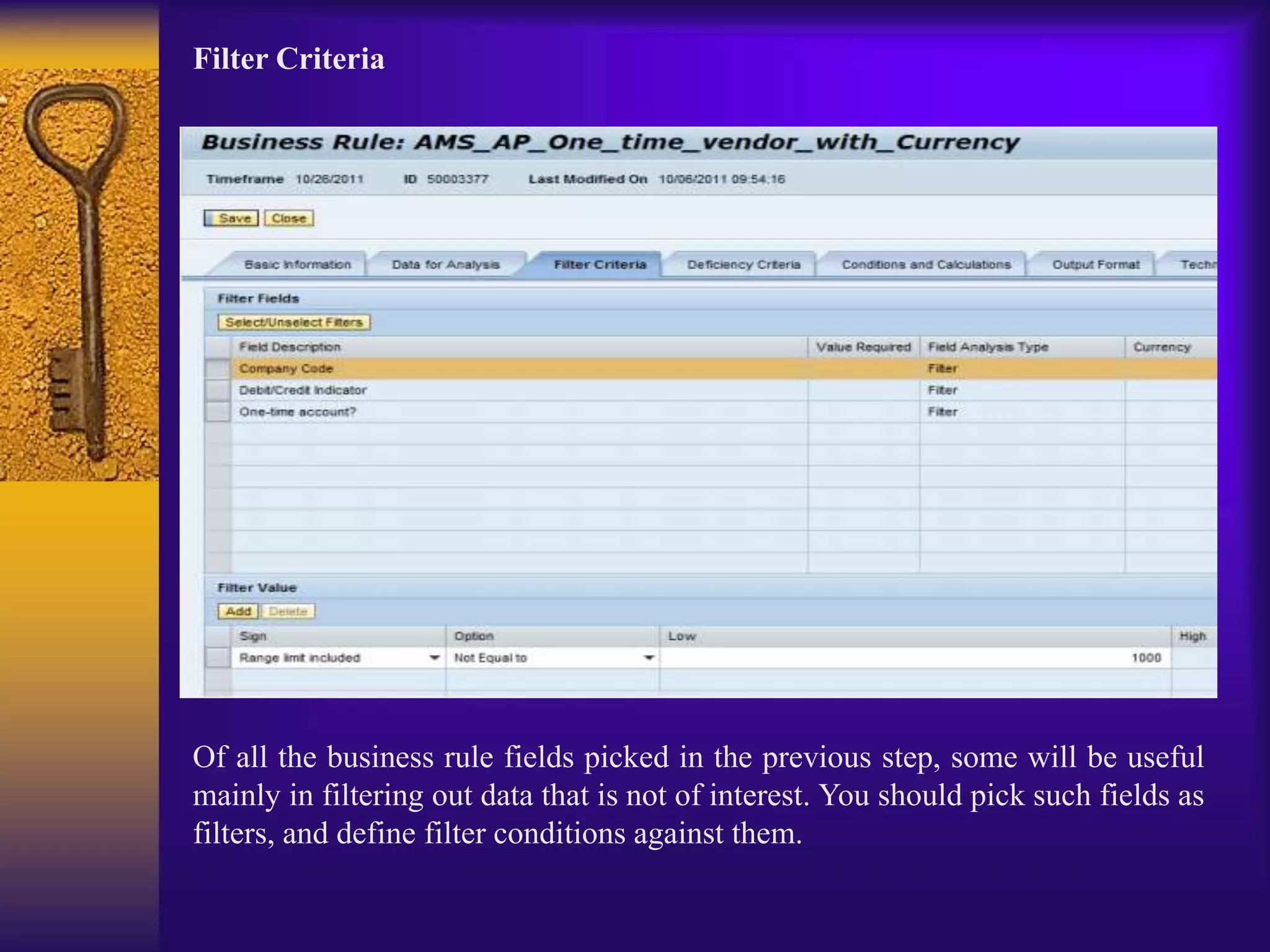
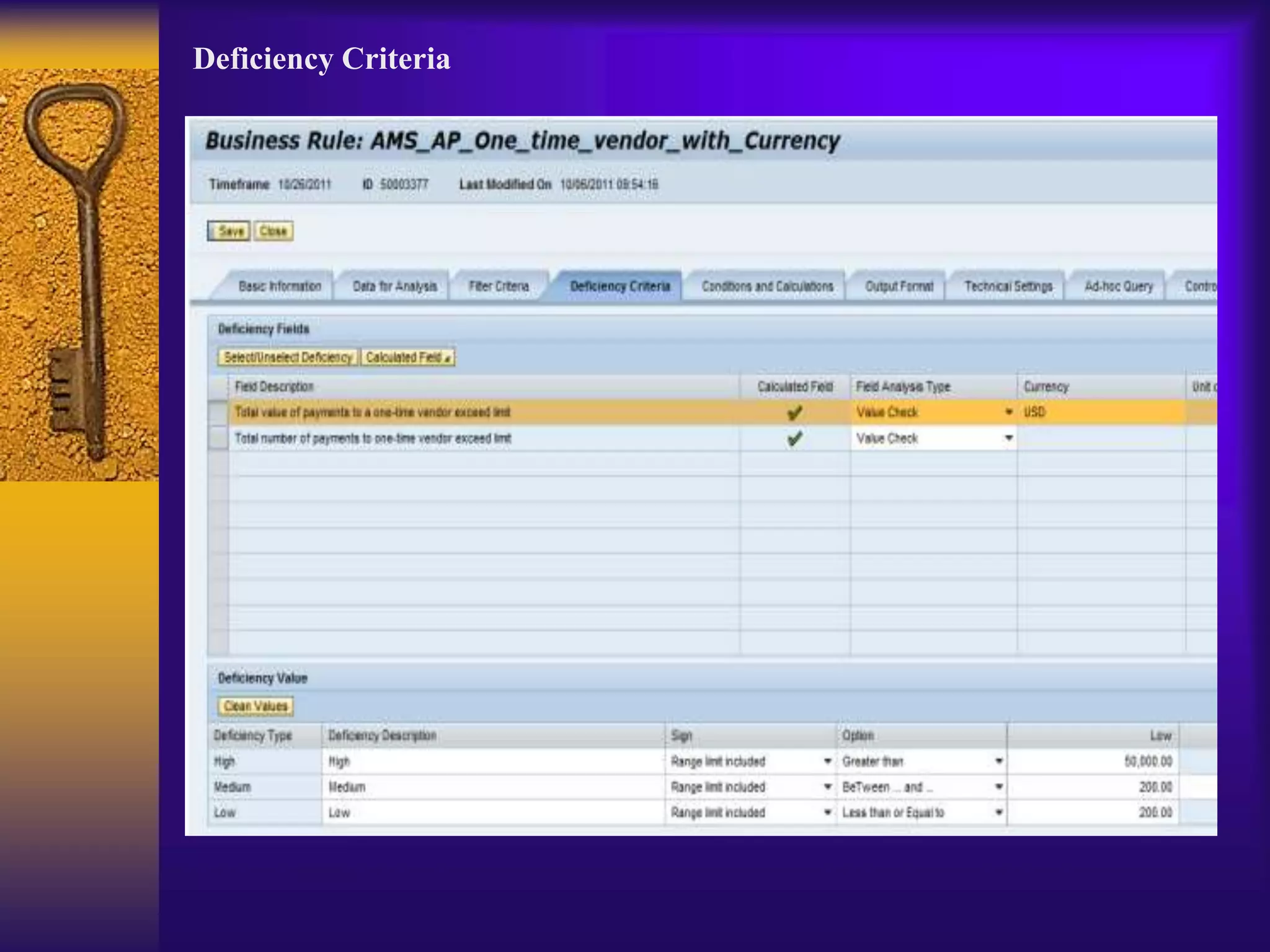
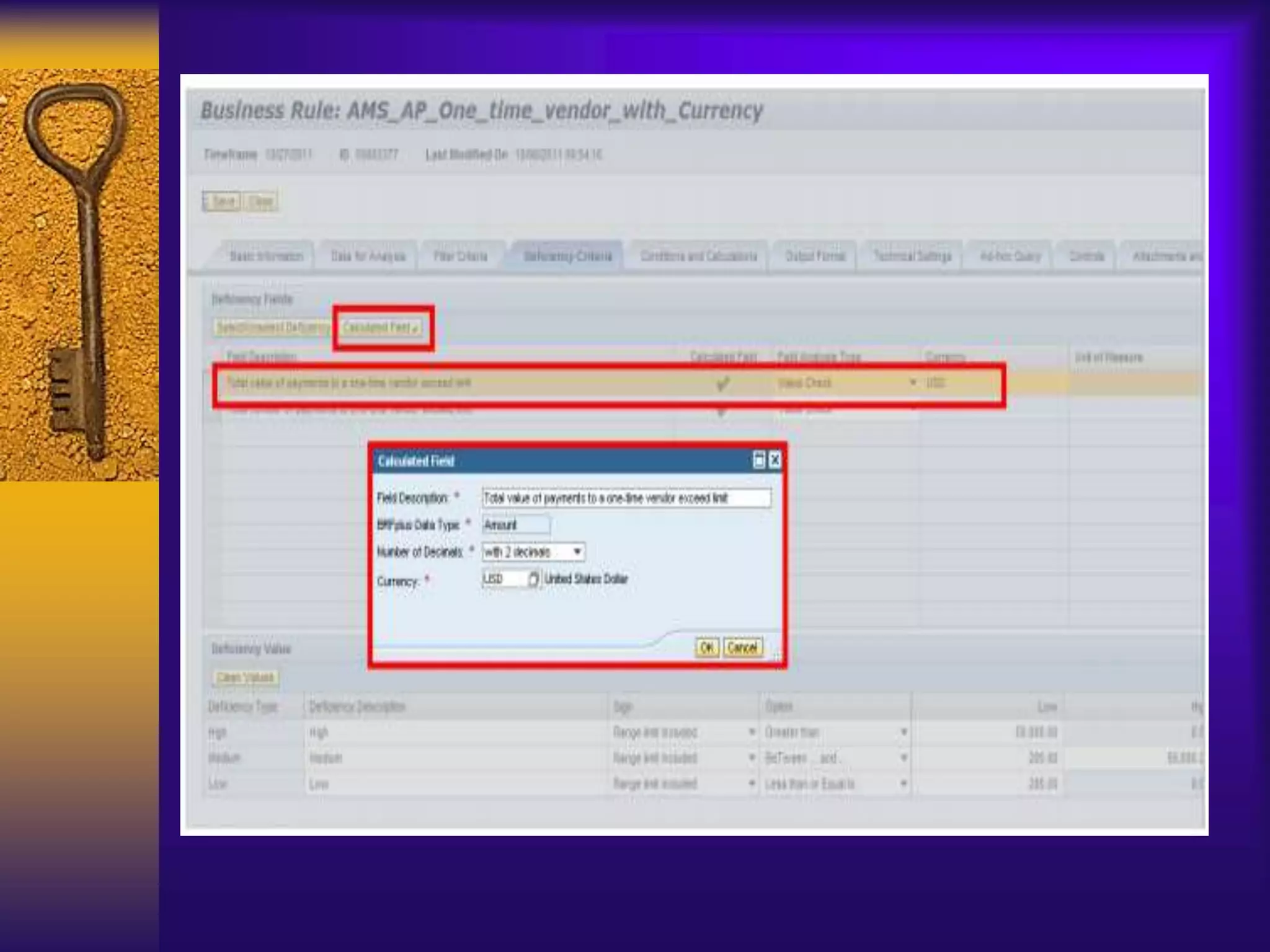
3) Configuration involves creating connectors to backend systems, defining data sources to specify how data is extracted, and building business rules to filter and evaluate the data to identify compliance issues.