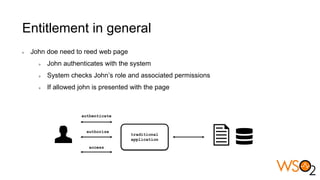
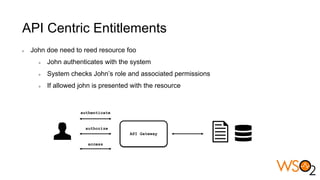
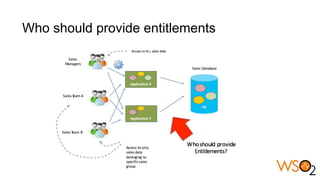
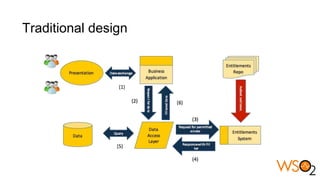
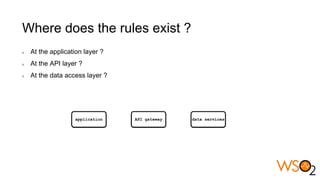
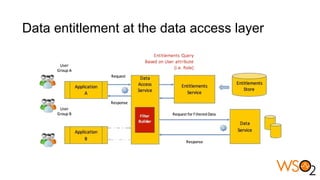
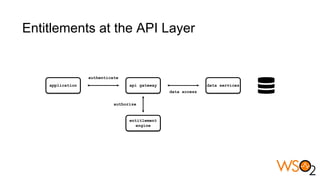
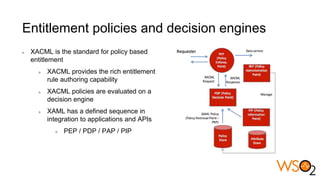
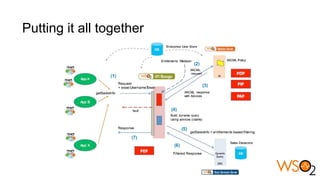
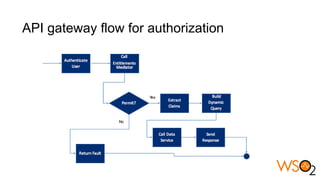
The document discusses data entitlement in an API-centric architecture, emphasizing the importance of authentication, authorization, and managing permissions effectively. It highlights complexities such as maintenance challenges and the need for a modern entitlement design that is reusable, centrally manageable, and responsive to changing business needs. Additionally, it outlines the benefits of using a standardized approach with mechanisms like XACML for policy-based entitlement and suggests that a data service mindset is essential for managing entitlements.