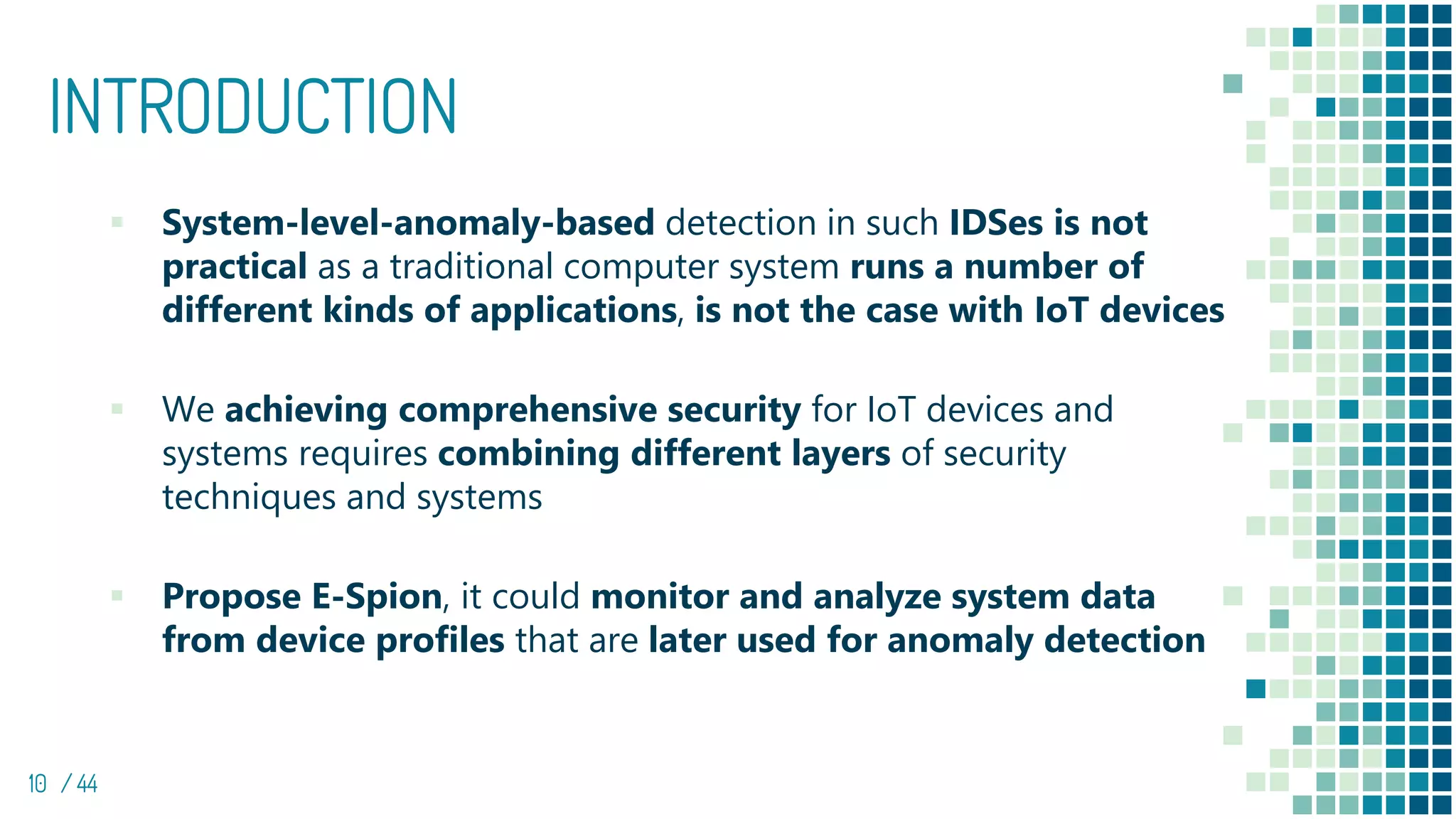
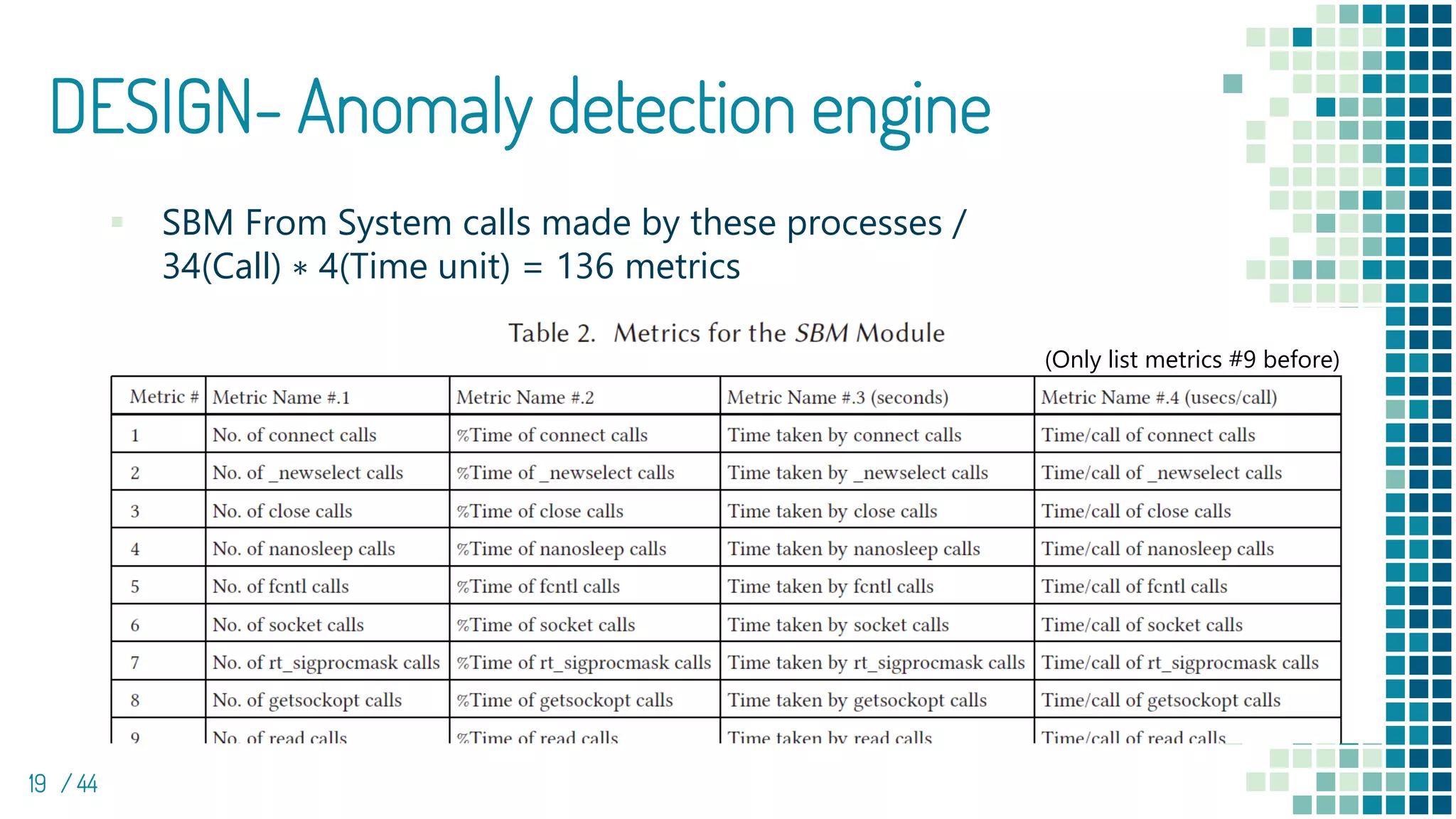
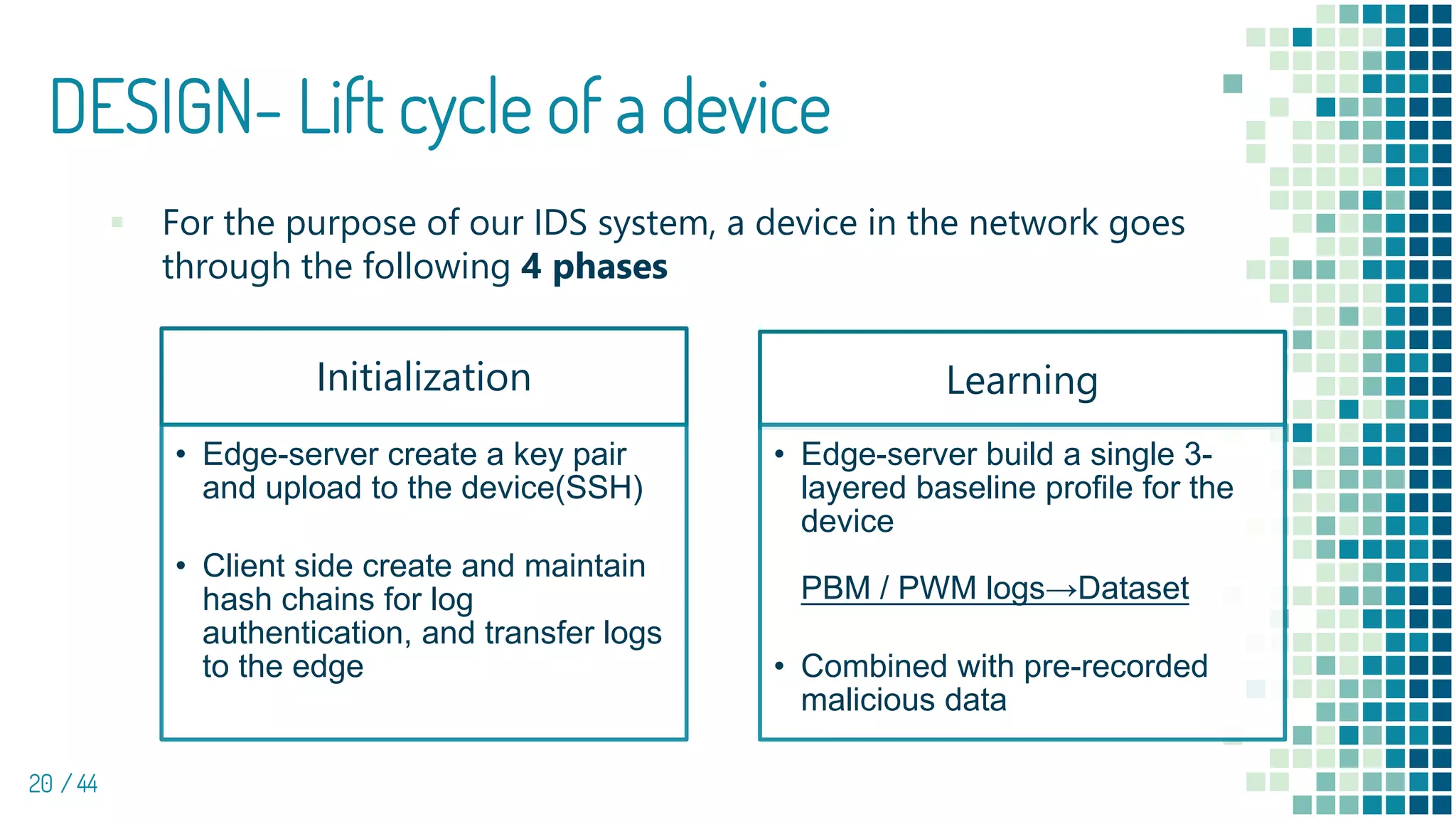
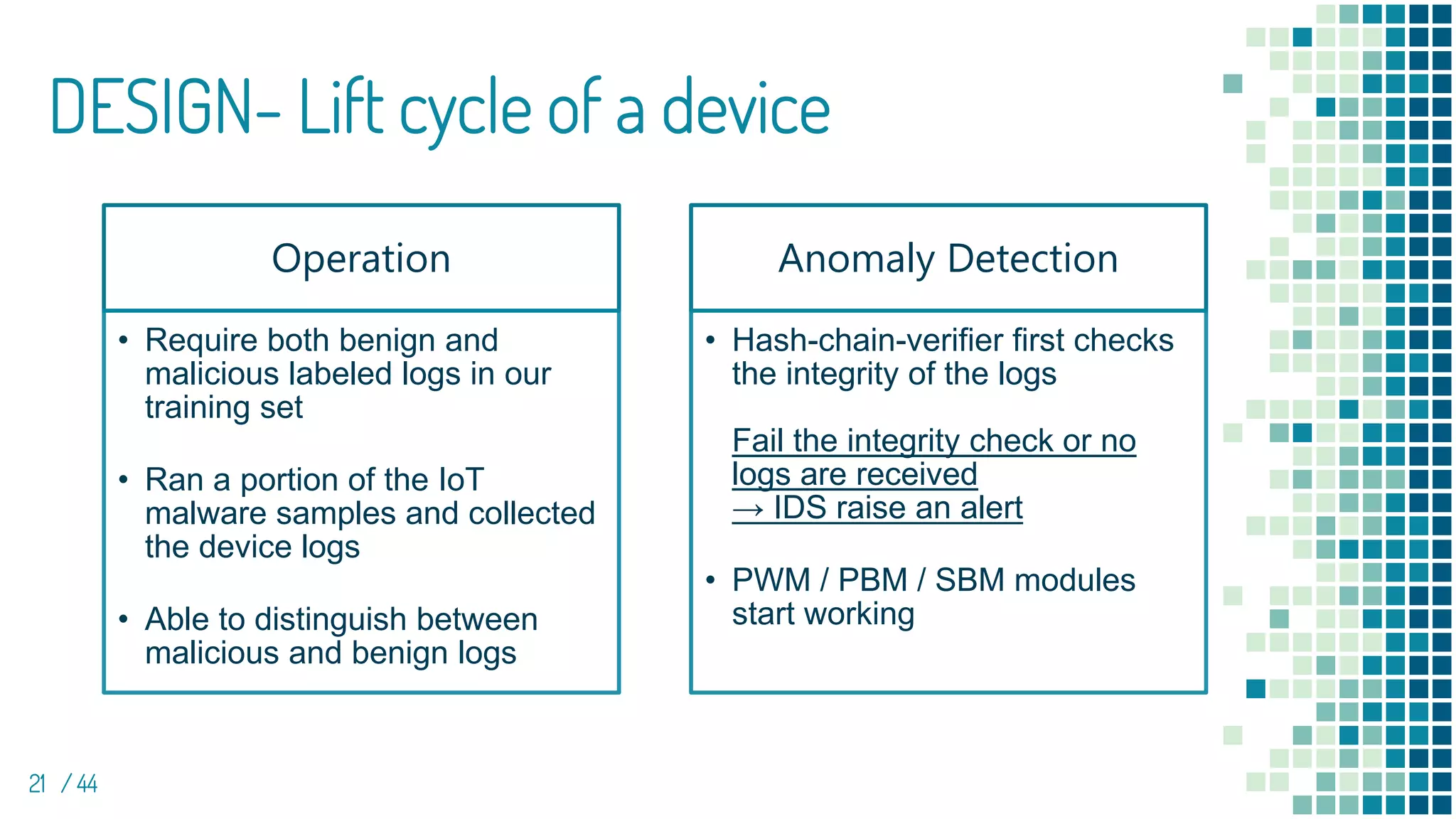
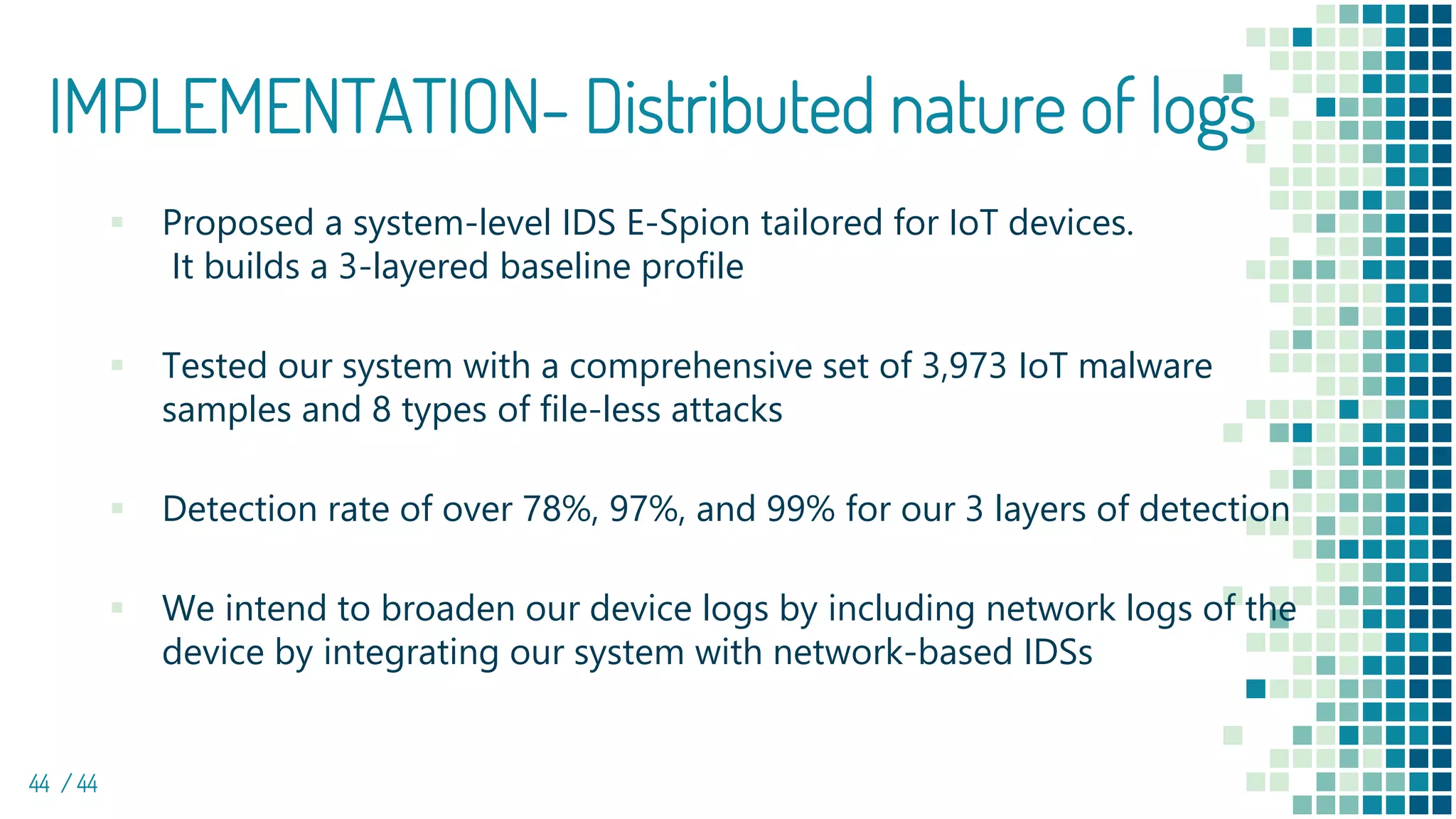
The document discusses the development of e-spion, an edge-based intrusion detection system designed specifically for IoT devices to address growing security concerns amidst increasingly sophisticated malware. The system employs a 3-layered behavior profiling architecture for anomaly detection, achieving a high detection rate across various types of attacks. It highlights the importance of combining device-level profiling with security techniques to enhance IoT security while conducting extensive evaluations against numerous malware samples.






![DESIGN- Hash chain verifier
22 / 44
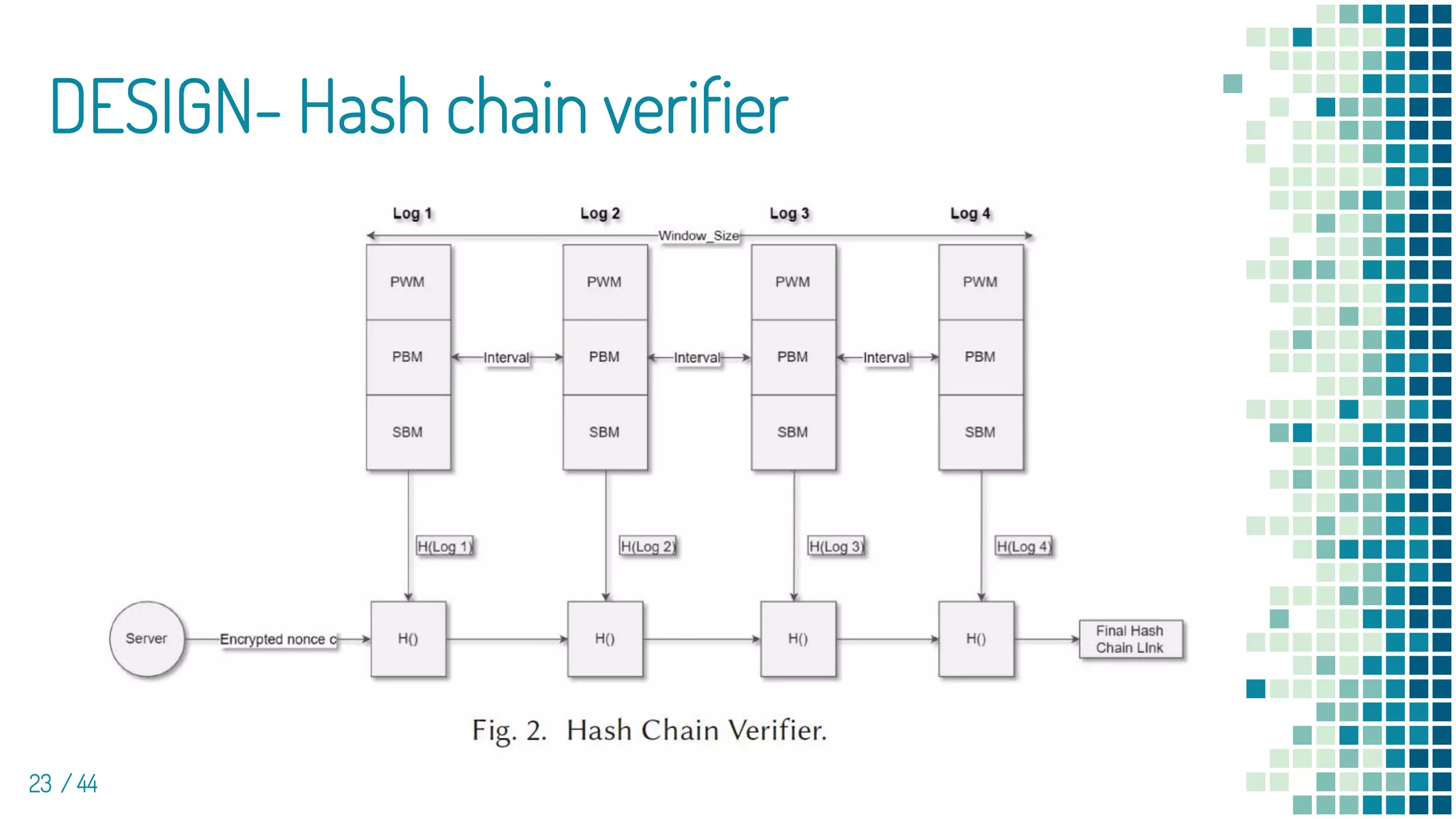
▪ Use the SHA256sum utility to compute the SHA-256
one-way hashes of the logs
▪ First commit logs to server
Log hash = hash (device 3 kind of log)
hash chain = hash( Log hash + Nonce[From server] )
▪ When first transfer received
▫ Match Authentication hash value, if not then raise an alert
▫ Delete First commit nonce from device (Server had been saved)
▫ After first commit, compute hash chain way will change to
hash chain = hash( previous Log hash + Log hash )](https://image.slidesharecdn.com/edge-basedintrusiondetectionforiotdevices-211202070112/75/Paper-sharing_Edge-based-intrusion-detection-for-IOT-devices-22-2048.jpg)








![Resource
▪ Edge-Based Intrusion Detection for IoT devices(2020) Vol. 11, No. 4, Article
18./ANAND MUDGERIKAR, PUNEET SHARMA, ELISA BERTINO /
Download form SCI-Hub [doi.org/10.1145/3382159]
▪ PPT template- Technology Pixels Presentation Template from
https://www.slidescarnival.com/mowbray-free-presentation-
template/1932#preview
▪ P7. Microsoft Stock images (royalty-free images)
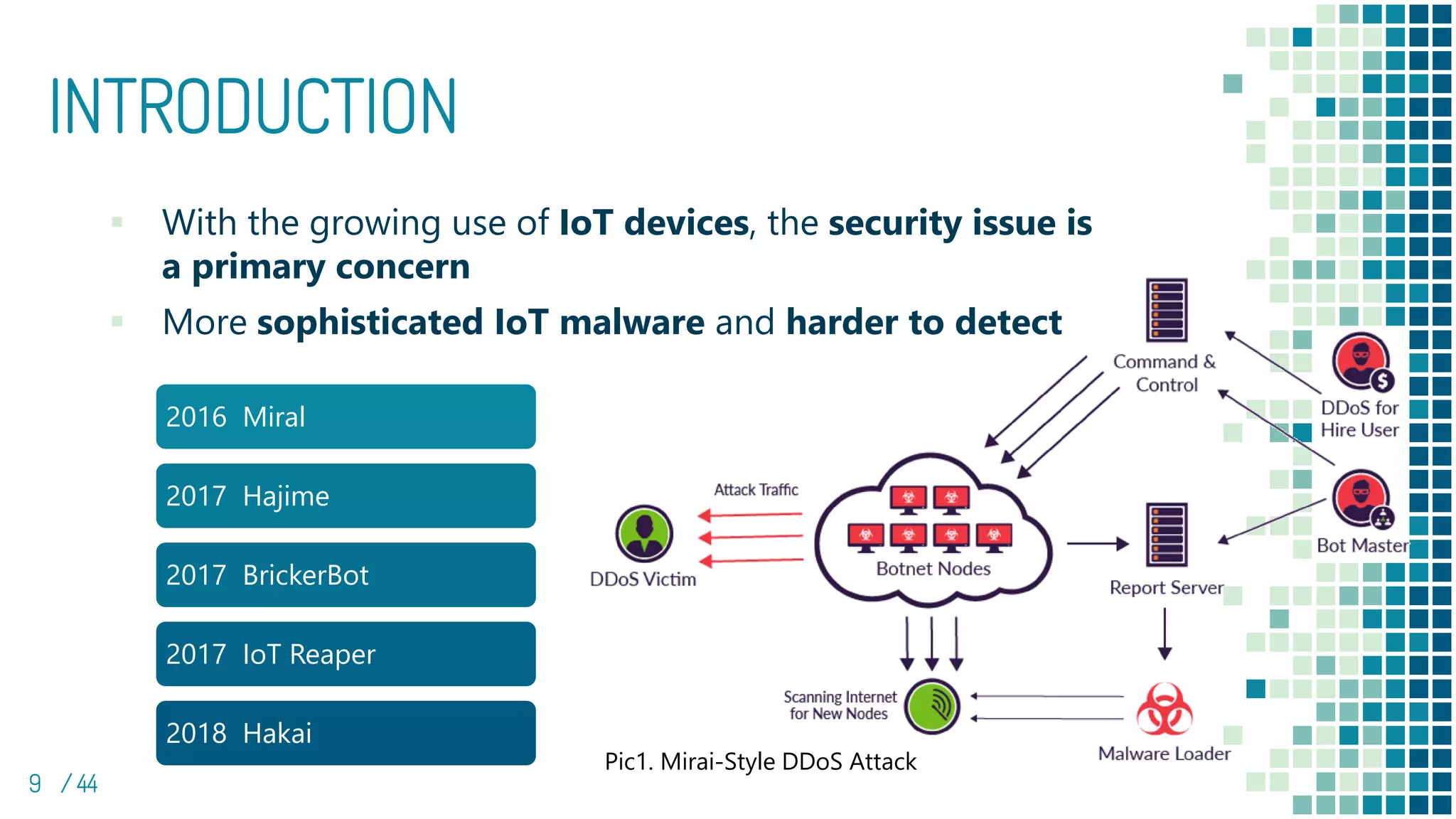
▪ P9. Pic1. Mirai-Style DDoS Attack from https://www.imperva.com/blog/how-to-
identify-a-mirai-style-ddos-attack/
▪ P12,14 Microsoft Bing images (CC images)
46 / 44](https://image.slidesharecdn.com/edge-basedintrusiondetectionforiotdevices-211202070112/75/Paper-sharing_Edge-based-intrusion-detection-for-IOT-devices-46-2048.jpg)
