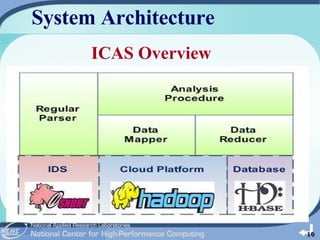
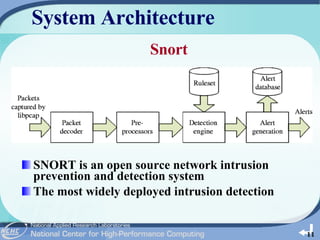
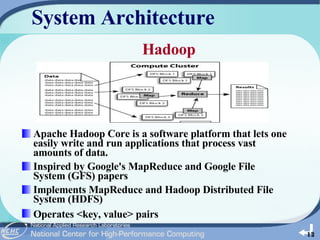
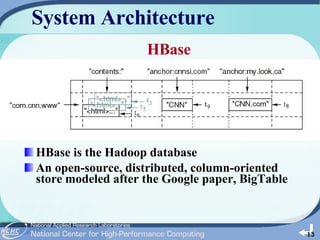
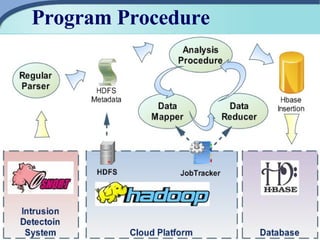
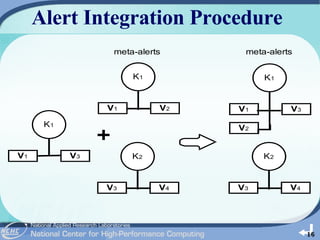
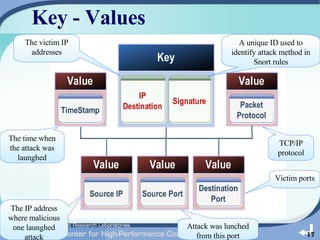
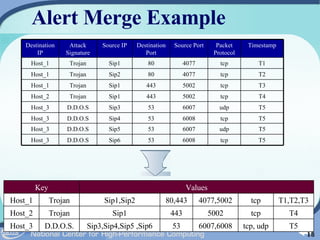
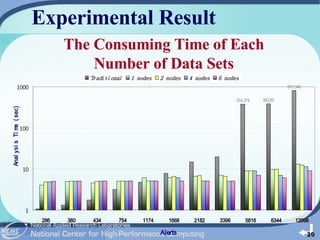
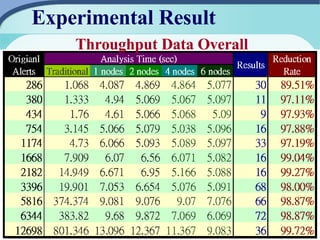
The document outlines the development of a cloud-based intrusion detection system (IDS) analysis system, named ICAS, aimed at improving alert management and analysis efficiency. It proposes using cloud computing technologies, such as Apache Hadoop and HBase, to process and store large volumes of IDS alerts, addressing issues like false positives and negative alerts. The conclusions suggest that ICAS provides a scalable and economical solution but highlights the need for further development and larger experiments.