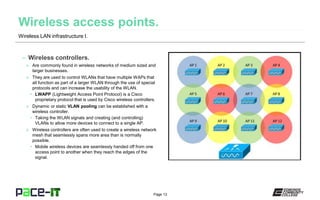
The document provides an overview of wireless LAN infrastructure, emphasizing the IEEE 802.11 standards that govern wireless network communication, including specifications for different protocols such as 802.11b, 802.11a, 802.11g, 802.11n, and 802.11ac. It highlights the importance of antennas in broadcasting RF signals, the role of wireless access points (WAPs) in connecting to wired networks, and the use of wireless controllers in managing larger networks. Additionally, it discusses technologies like MIMO and beamforming that enhance network performance and efficiency.