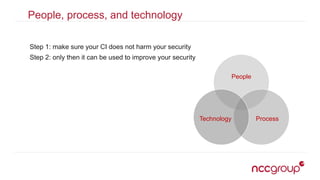
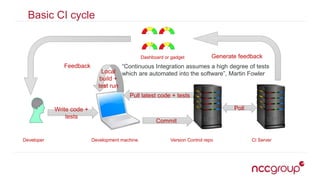
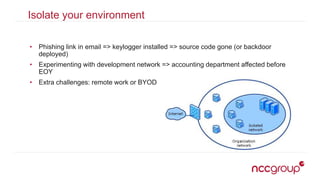
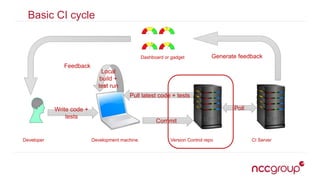
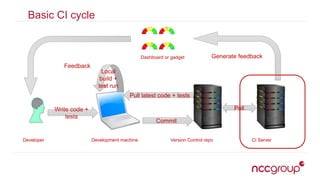
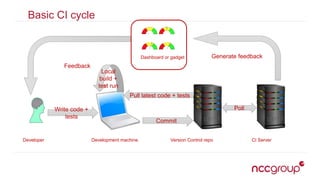
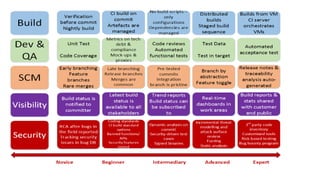
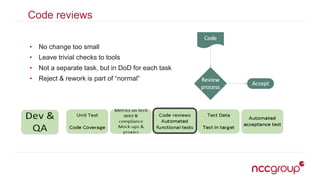
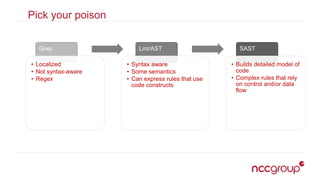
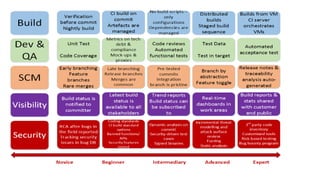
The document outlines best practices for securing the continuous integration (CI) process, emphasizing the importance of ensuring that CI does not compromise security before using it to enhance security. It discusses the significance of strong version control, maintaining isolated environments, and incorporating feedback mechanisms for developers. Additionally, it highlights issues such as malicious software and the necessity of automated tests, static analysis, and dynamic analysis to enhance security within the CI pipeline.