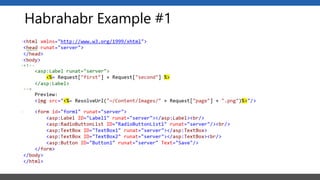
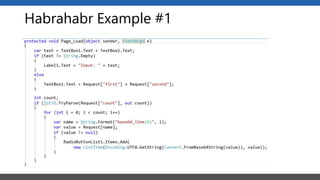
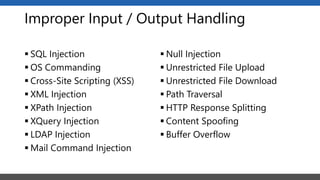
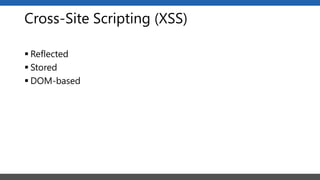
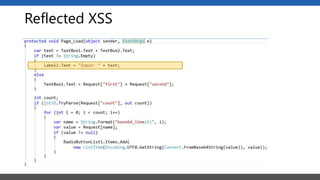
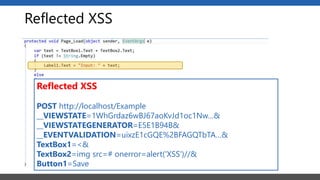
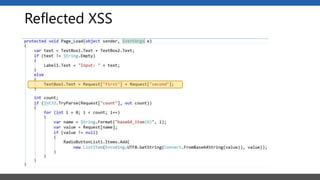
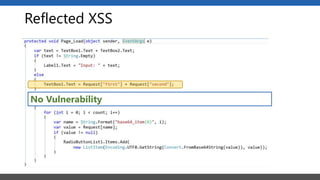
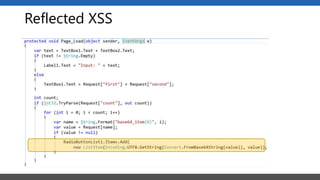
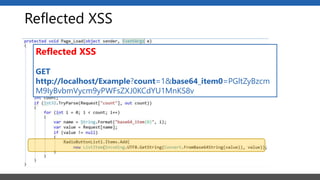
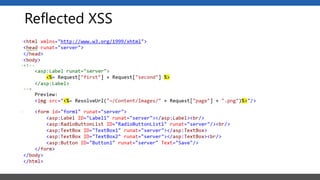
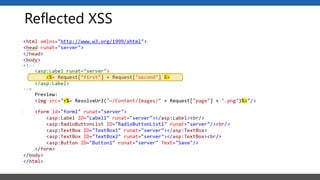
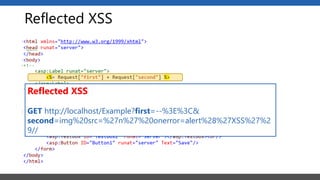
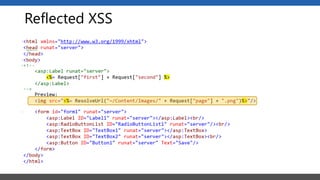
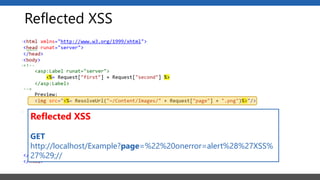
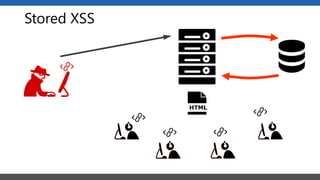
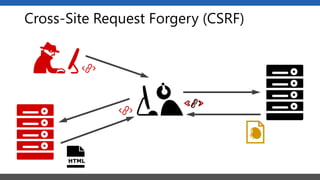
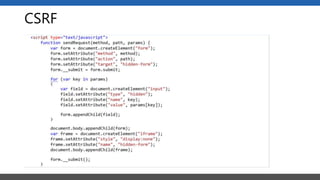
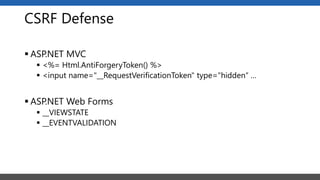
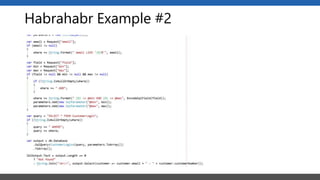
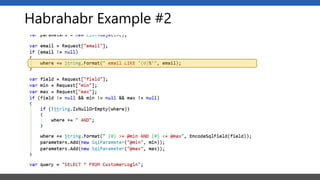
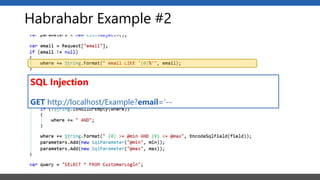
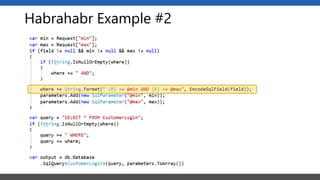
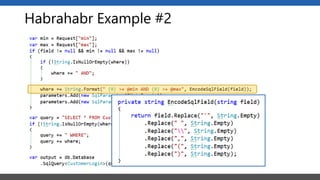
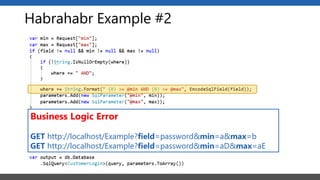
This document summarizes a presentation on application security practices for .NET applications. It discusses common vulnerabilities like cross-site scripting, SQL injection, and cross-site request forgery. It provides examples of these vulnerabilities using code snippets and HTTP requests. It also covers mitigation techniques, like input validation, output encoding, and anti-forgery tokens. The presentation recommends resources on the OWASP Top 10, secure coding best practices, and classification of security risks.