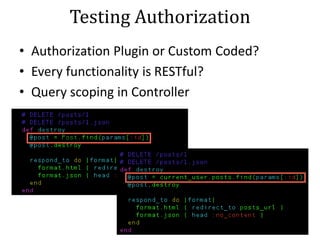
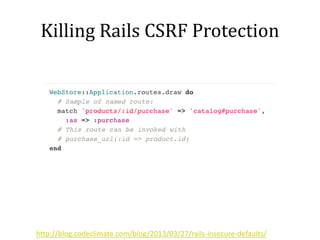
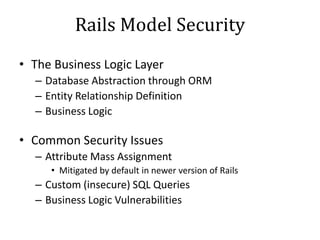
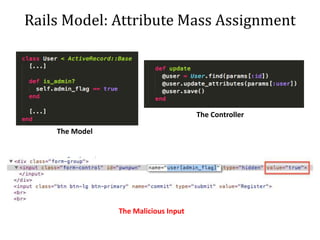
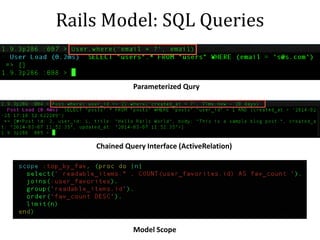
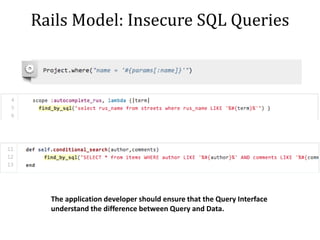
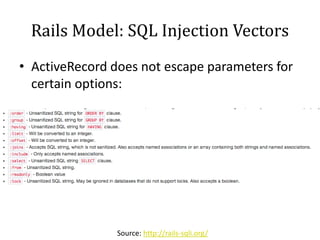
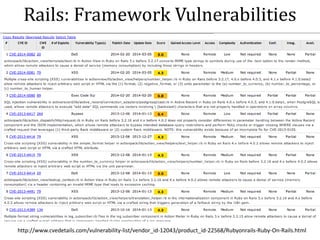
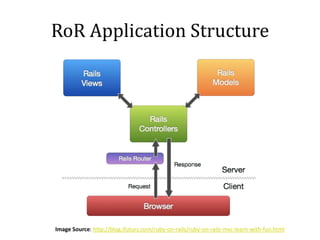
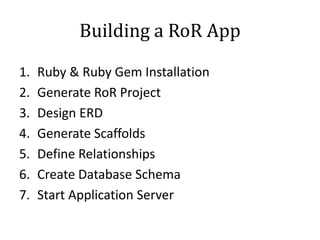
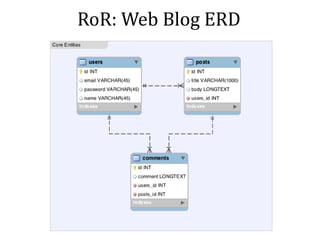
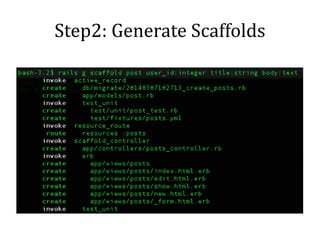
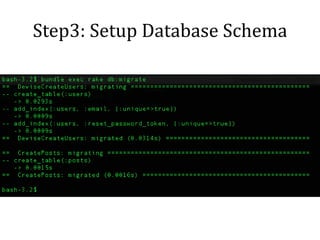
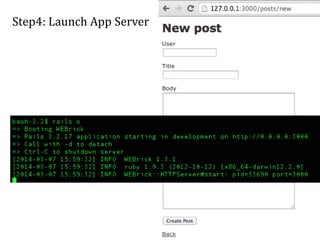
This document discusses breaking and penetration testing Ruby on Rails applications. It covers fingerprinting the Rails framework, testing the attack surface through routes, session security issues, authentication vulnerabilities, authorization testing, CSRF protection bypass, model attribute assignment and SQL injection issues, view rendering exploits, and insecure defaults. Recommended tools for analysis include Brakeman, grep searches, and the Ruby Mechanize and Nokogiri libraries. The document provides references for further Rails security best practices.








![Fingerprinting Rails Applications
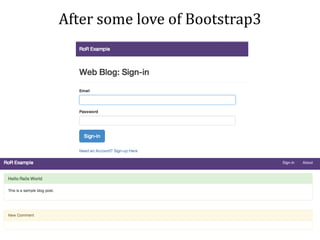
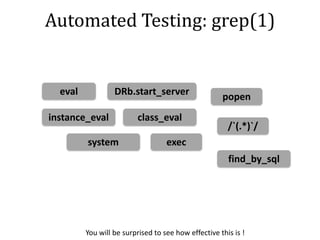
• No generic and definitive technique!
– It’s a cat & mouse game really.
• Heuristics
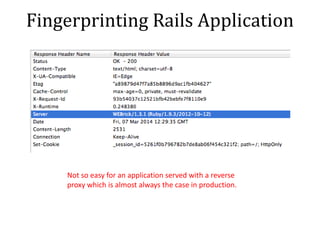
– Session Identifier
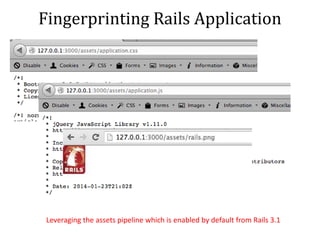
– Asset Pipeline
– [ … ]](https://image.slidesharecdn.com/rubyror-140609115622-phpapp01/85/Ruby-on-Rails-Penetration-Testing-18-320.jpg)


![Authentication
• Multiple Popular Authentication Plugin
– Devise
– RESTful Authentication
– […]
• Devise
– Auto-generated Registration, Confirmation, Login,
Forgot Password etc.
– Controller filter for enforcing authentication.](https://image.slidesharecdn.com/rubyror-140609115622-phpapp01/85/Ruby-on-Rails-Penetration-Testing-28-320.jpg)