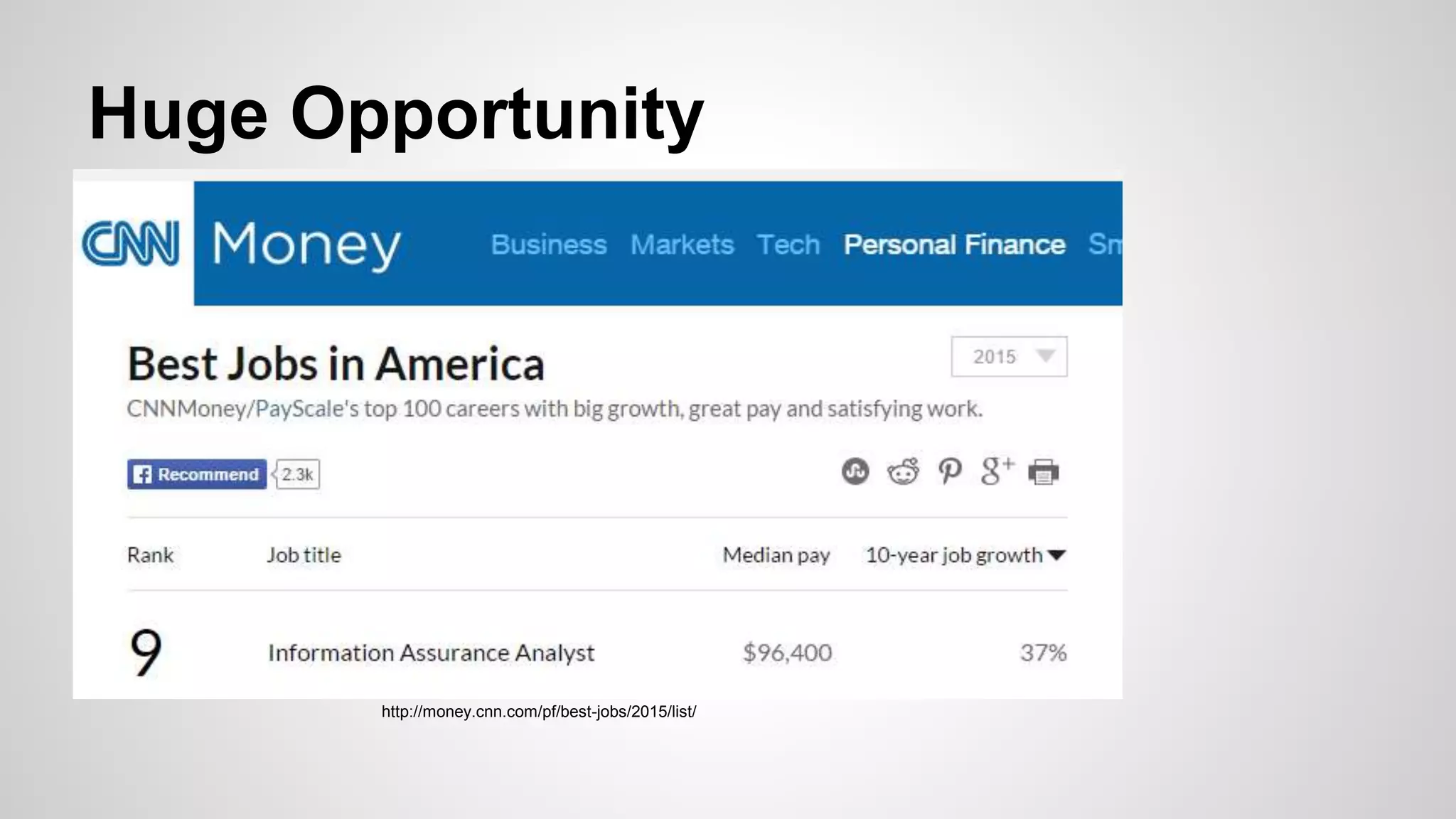
The document outlines the importance of penetration testing in identifying security vulnerabilities and emphasizes the need for a dedicated hacking lab environment for skill development. It provides a comprehensive guide on setting up a practice ground, including tools, techniques, and resources for learning. Additionally, it discusses opportunities in the field, such as bug bounty programs and the importance of responsible disclosure in the security community.


![● Information Security Engineer
● Mastered Science of Information
Assurance from Northeastern University,
Boston (MA)
● Occasionally blog at
infosecforever.blogspot.com
● @MaverickRocky02
● lokesh [dot] pidawekar [at] gmail [dot] com](https://image.slidesharecdn.com/wallofsheepworkshop-150811055859-lva1-app6891/75/Hacker-s-Practice-Ground-Wall-of-Sheep-workshops-Defcon-2015-3-2048.jpg)

















![Questions
Email - lokesh[dot]pidawekar[at]gmail[dot]com](https://image.slidesharecdn.com/wallofsheepworkshop-150811055859-lva1-app6891/75/Hacker-s-Practice-Ground-Wall-of-Sheep-workshops-Defcon-2015-27-2048.jpg)