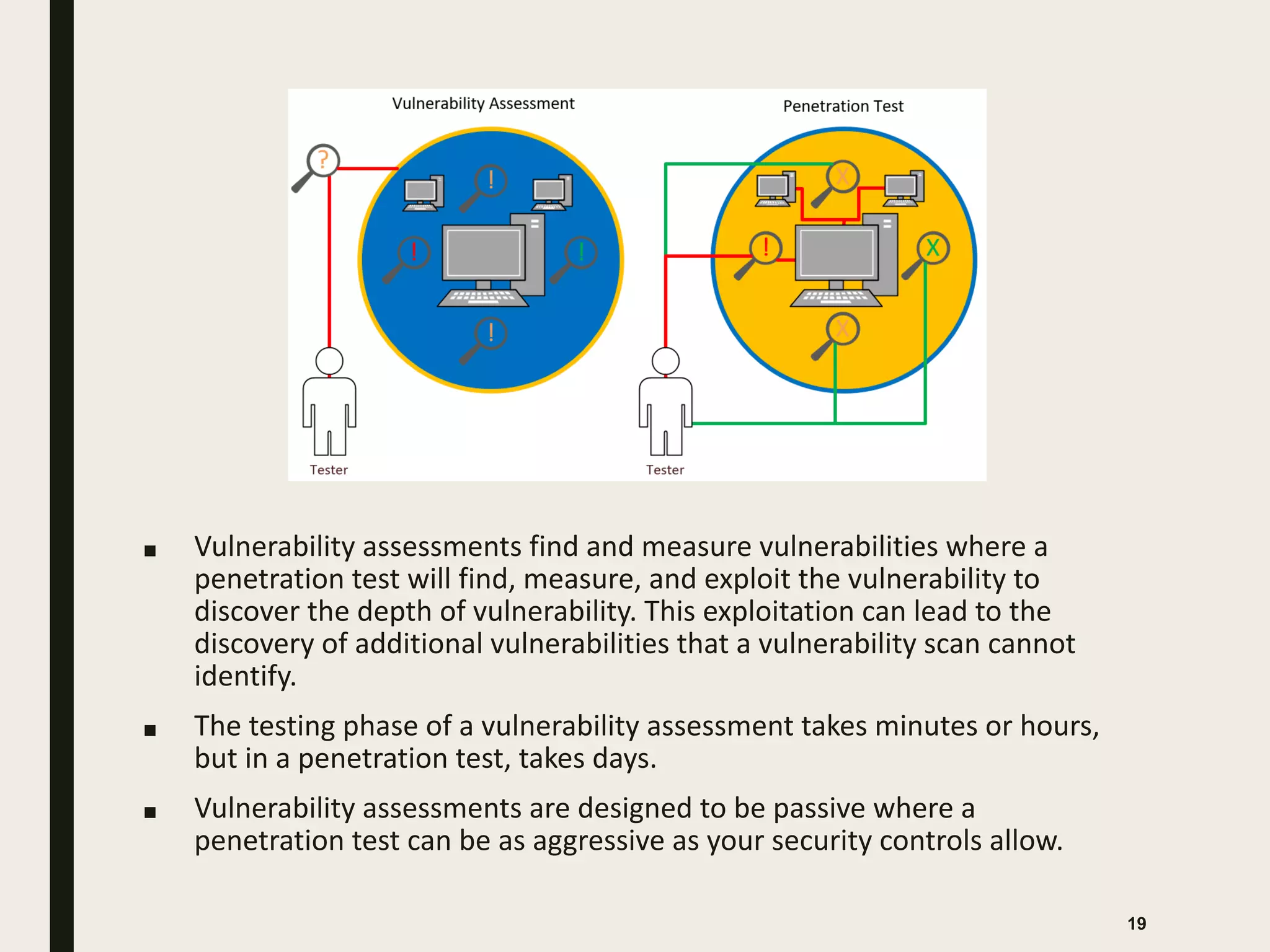
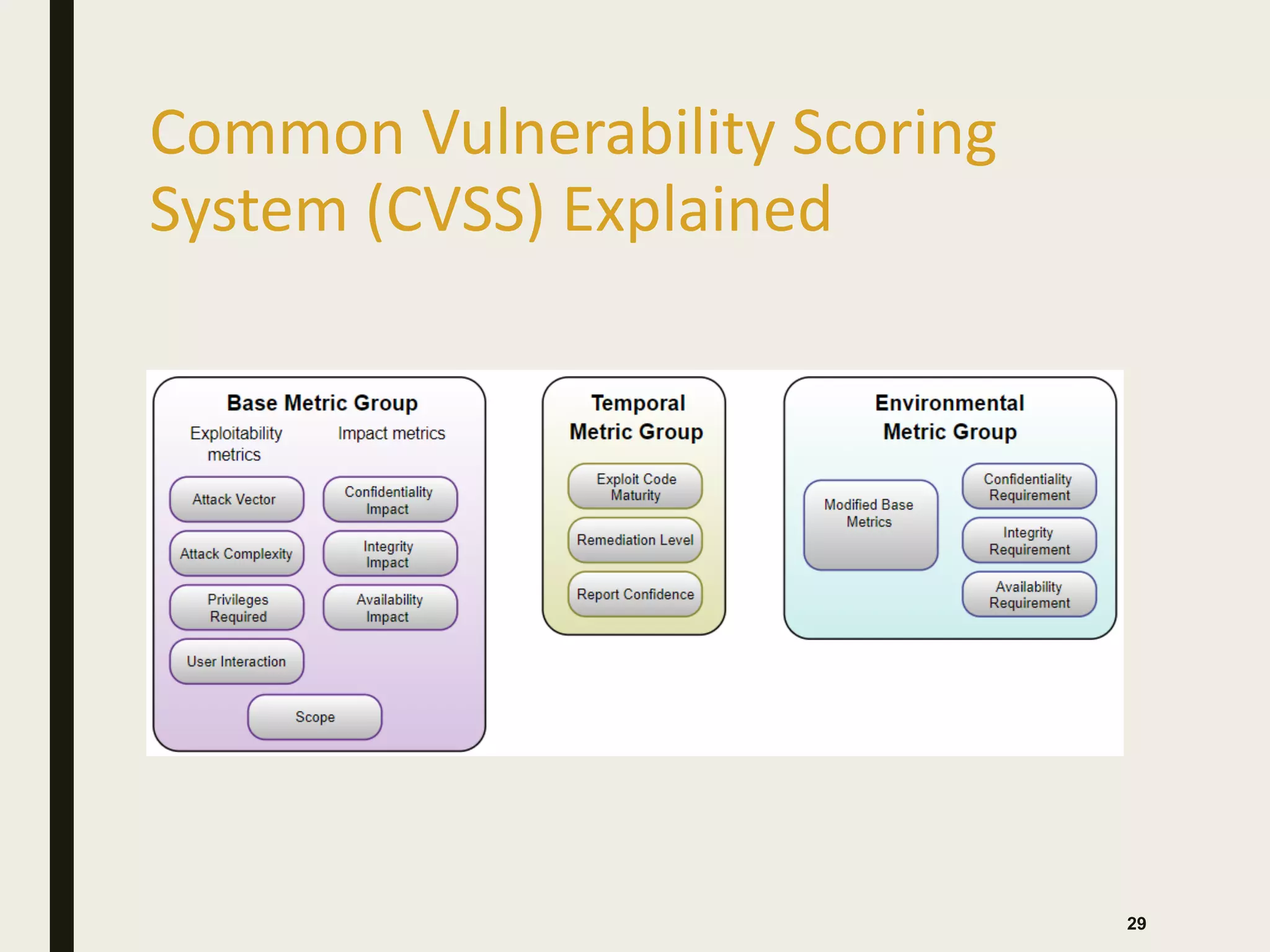
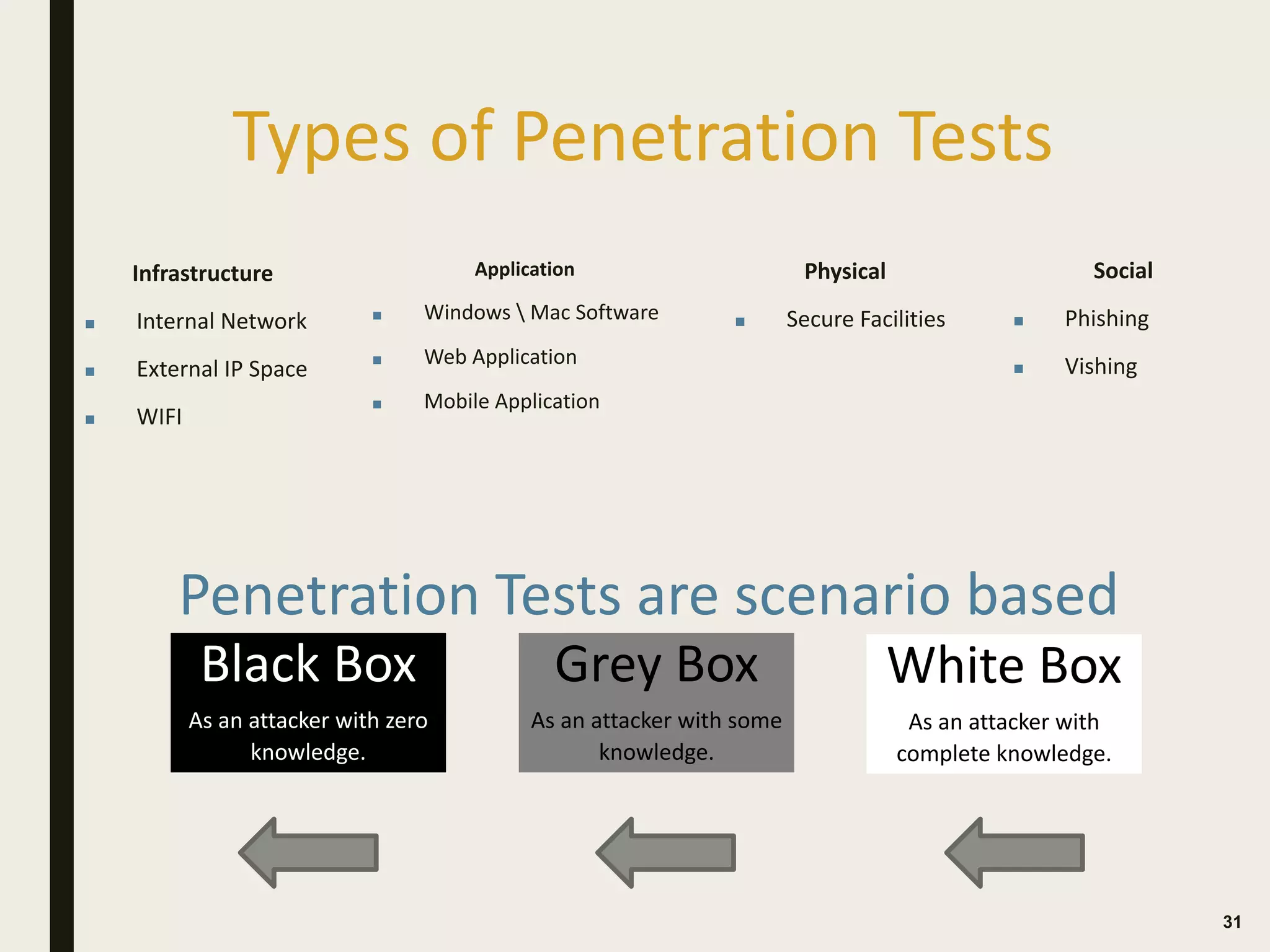
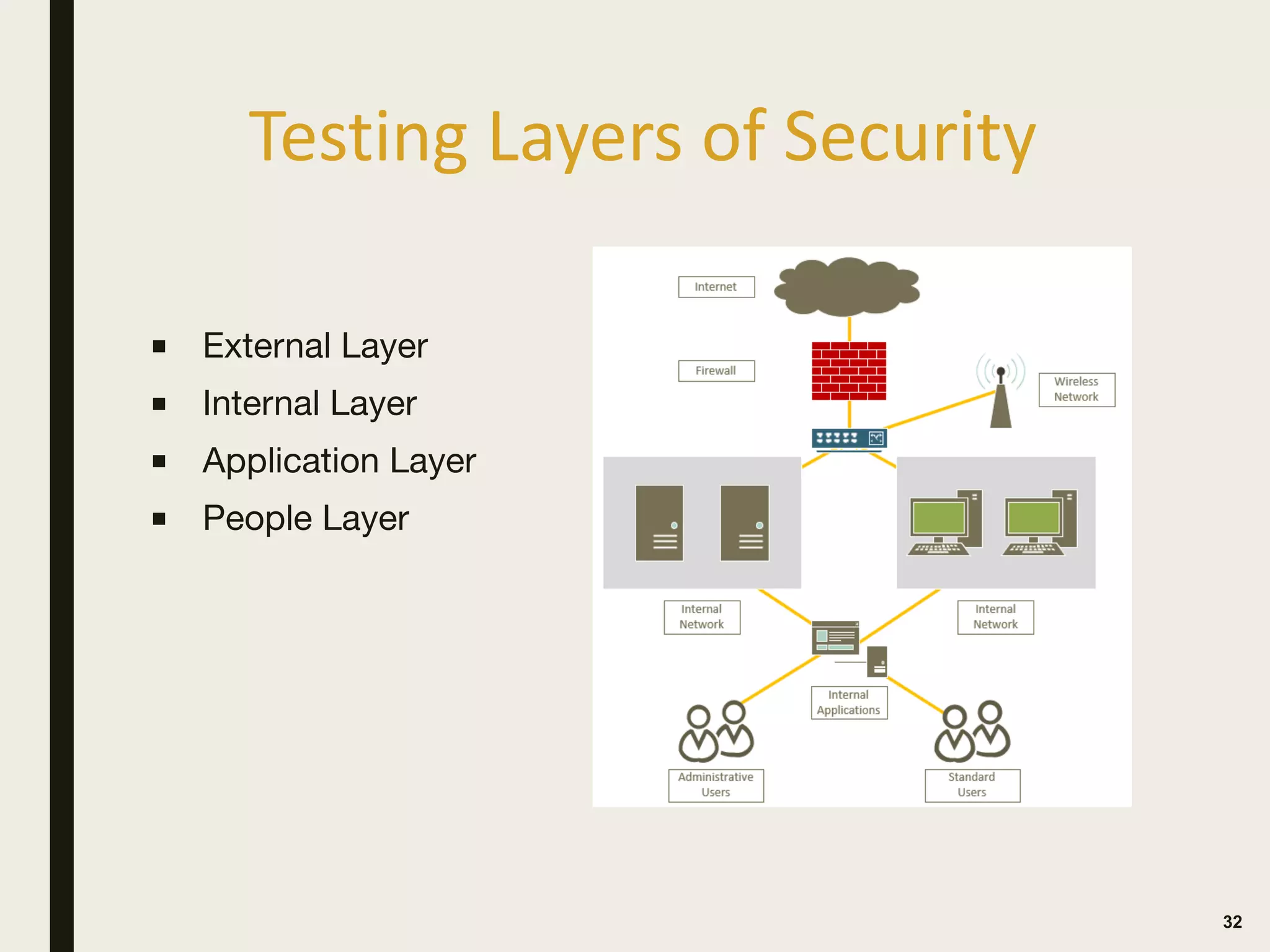
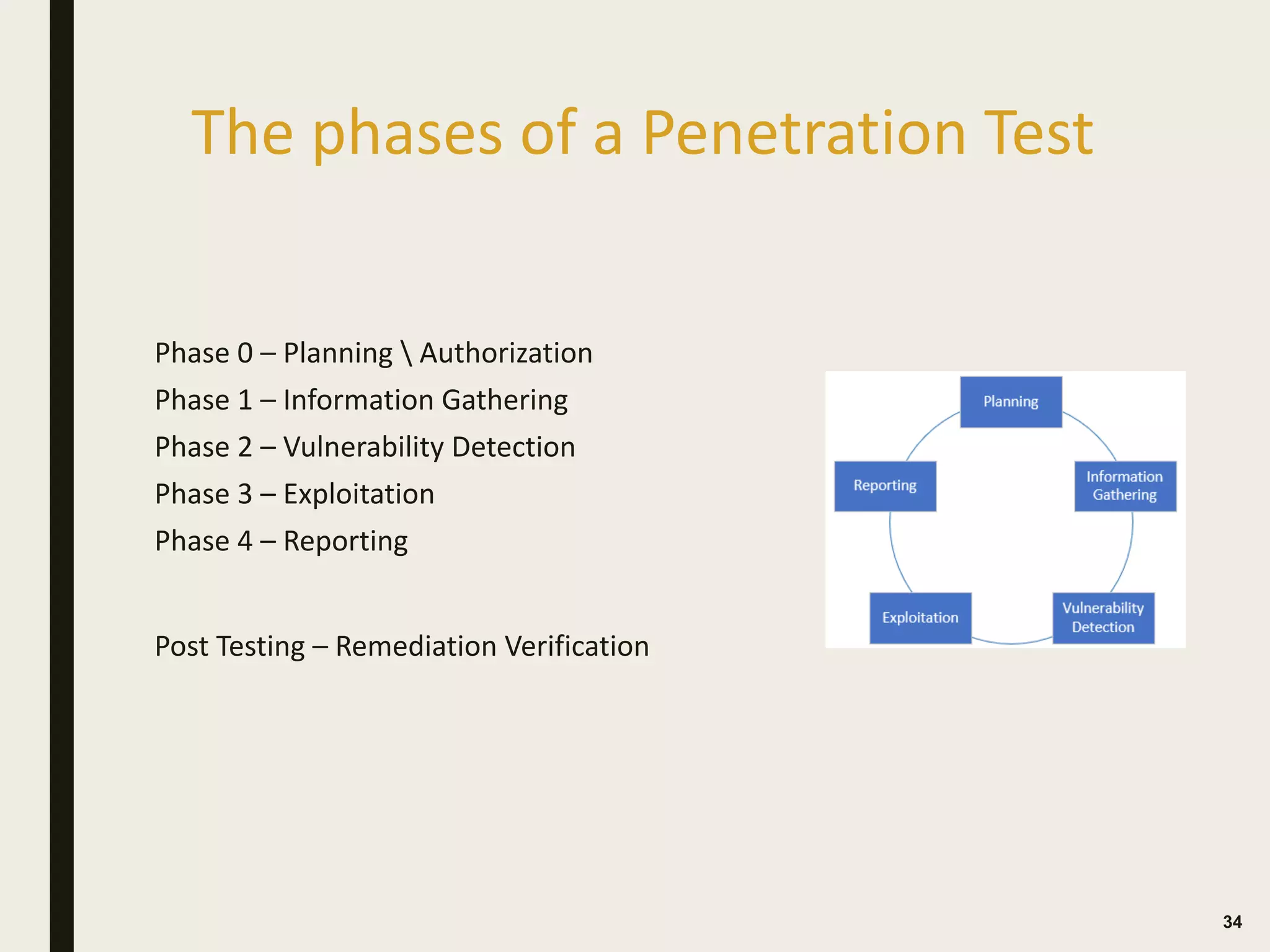
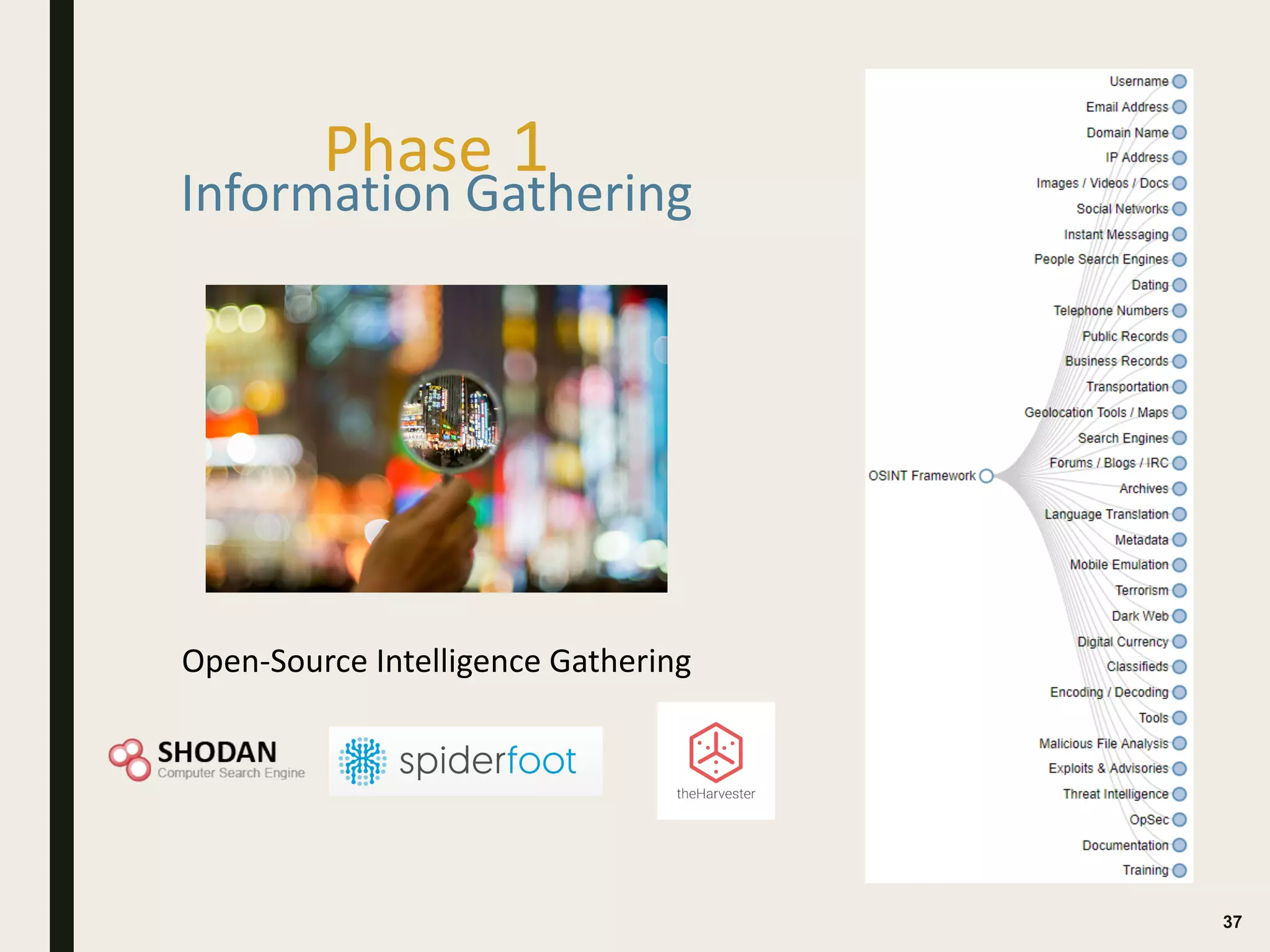
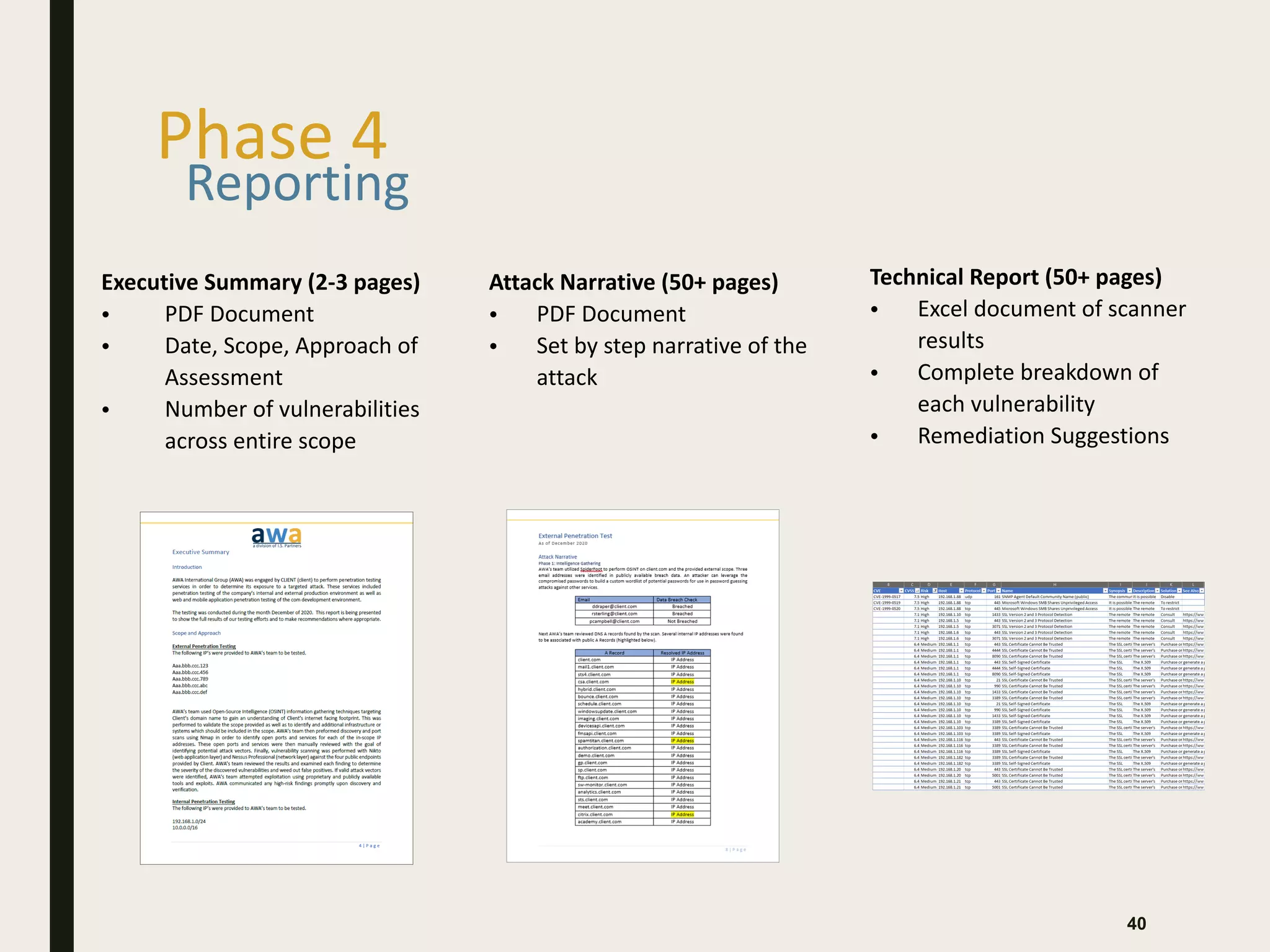
The document discusses the key differences between vulnerability assessments and penetration tests, outlining when and how organizations should implement these assessments based on risk evaluation. It emphasizes the importance of understanding inherent risks and establishing a risk appetite to determine appropriate mitigation measures, including the use of third-party assessments. Additionally, it details the processes and methodologies involved in conducting both types of assessments, highlighting the objectives and deliverables for each.