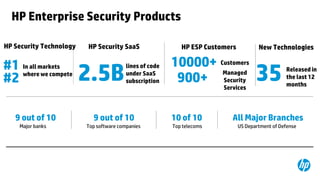
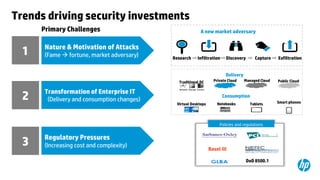
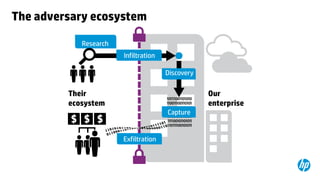
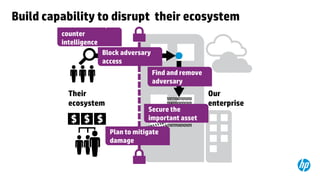
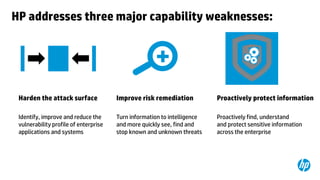
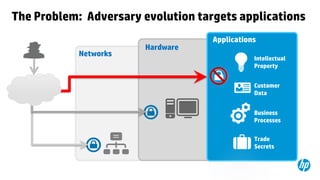
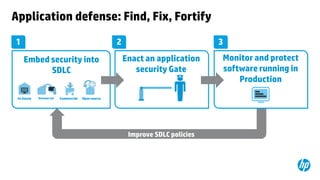
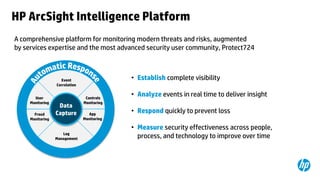
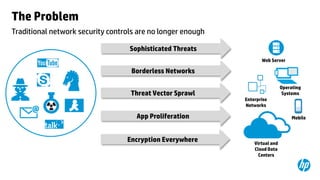
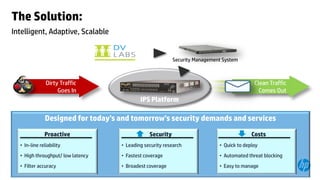
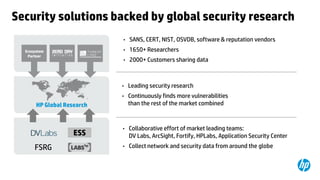
This document provides an overview of HP Enterprise Security Products. It discusses how HP addresses security challenges through technologies that harden attack surfaces, improve risk remediation, and proactively protect information. It also summarizes HP's security research capabilities, which include over 1,650 researchers, collaboration with 2,000 customers, and continuously finding more vulnerabilities than other vendors. The goal is to provide intelligent, adaptive, and scalable security management solutions backed by global security intelligence.