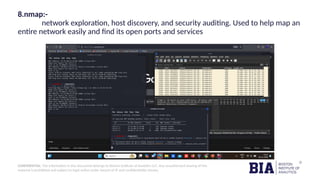
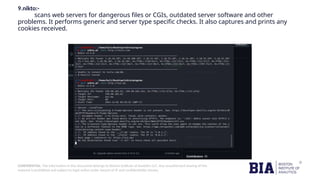
This document outlines methods and tools used for reconnaissance in cybersecurity, emphasizing the importance of gathering information about target systems to identify vulnerabilities for potential attacks. It distinguishes between active and passive reconnaissance techniques and lists several tools such as Nmap, TheHarvester, and Wireshark for conducting these activities. The document also advises on protective measures organizations can take to defend against reconnaissance attacks.