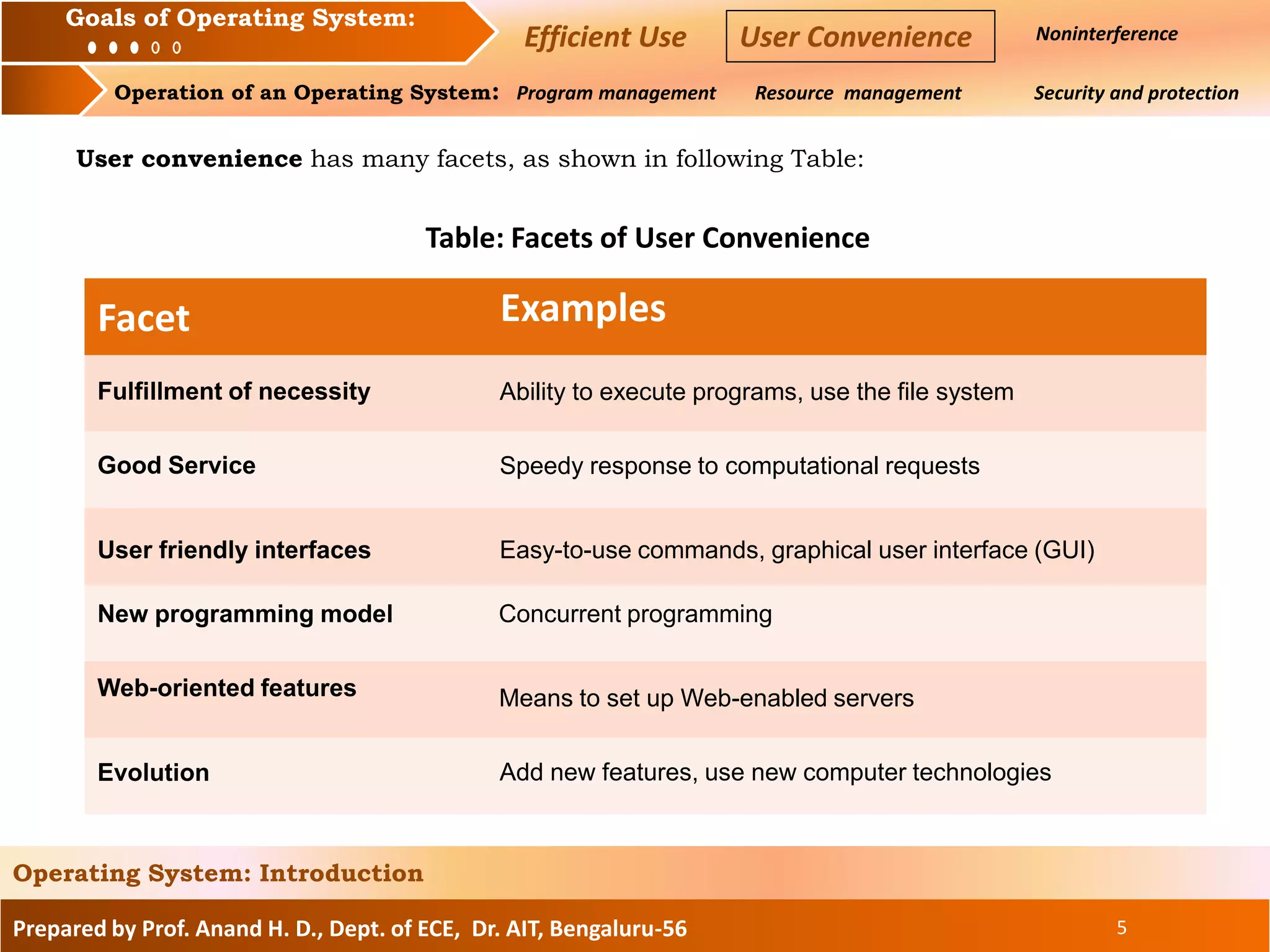
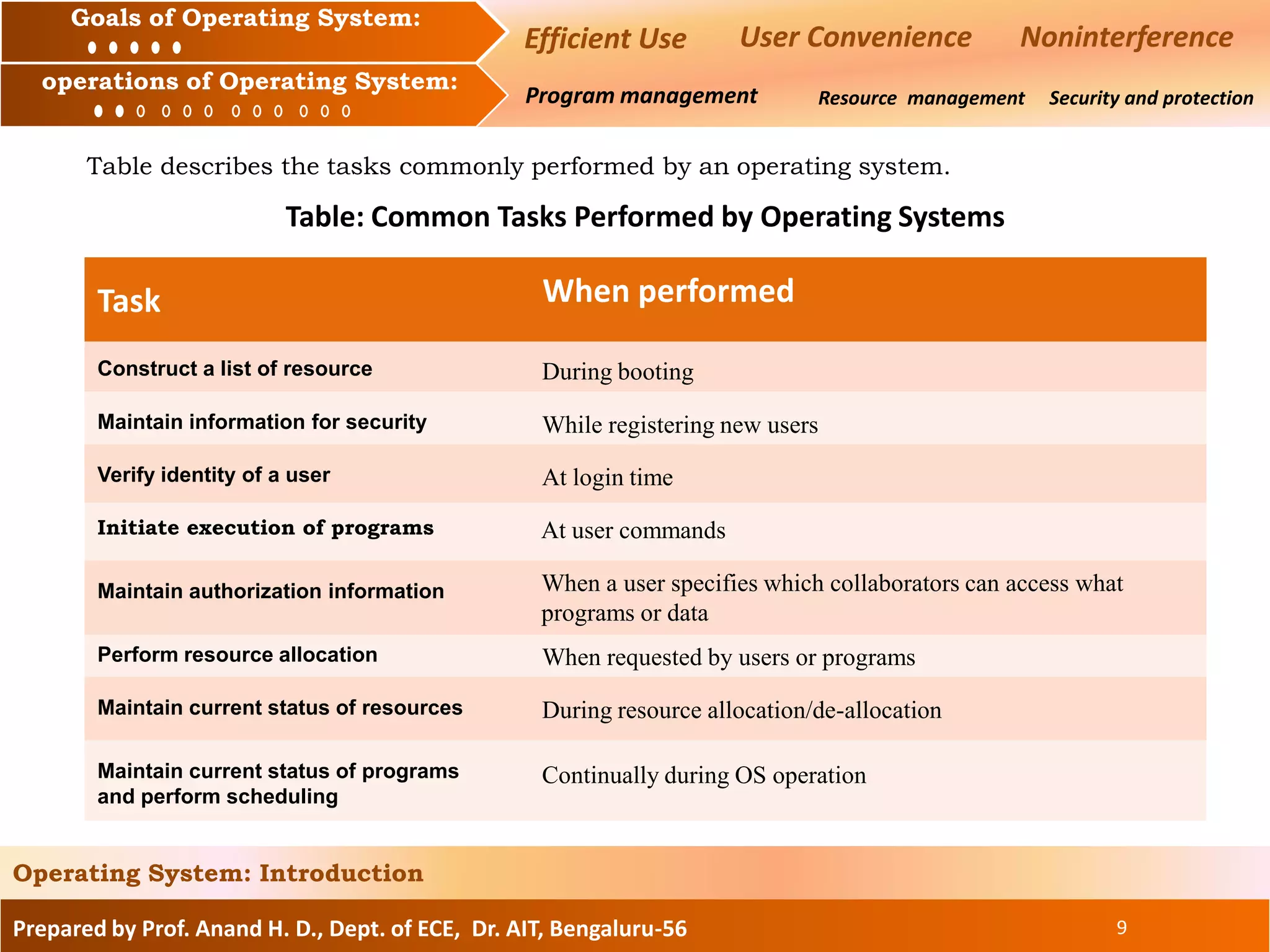
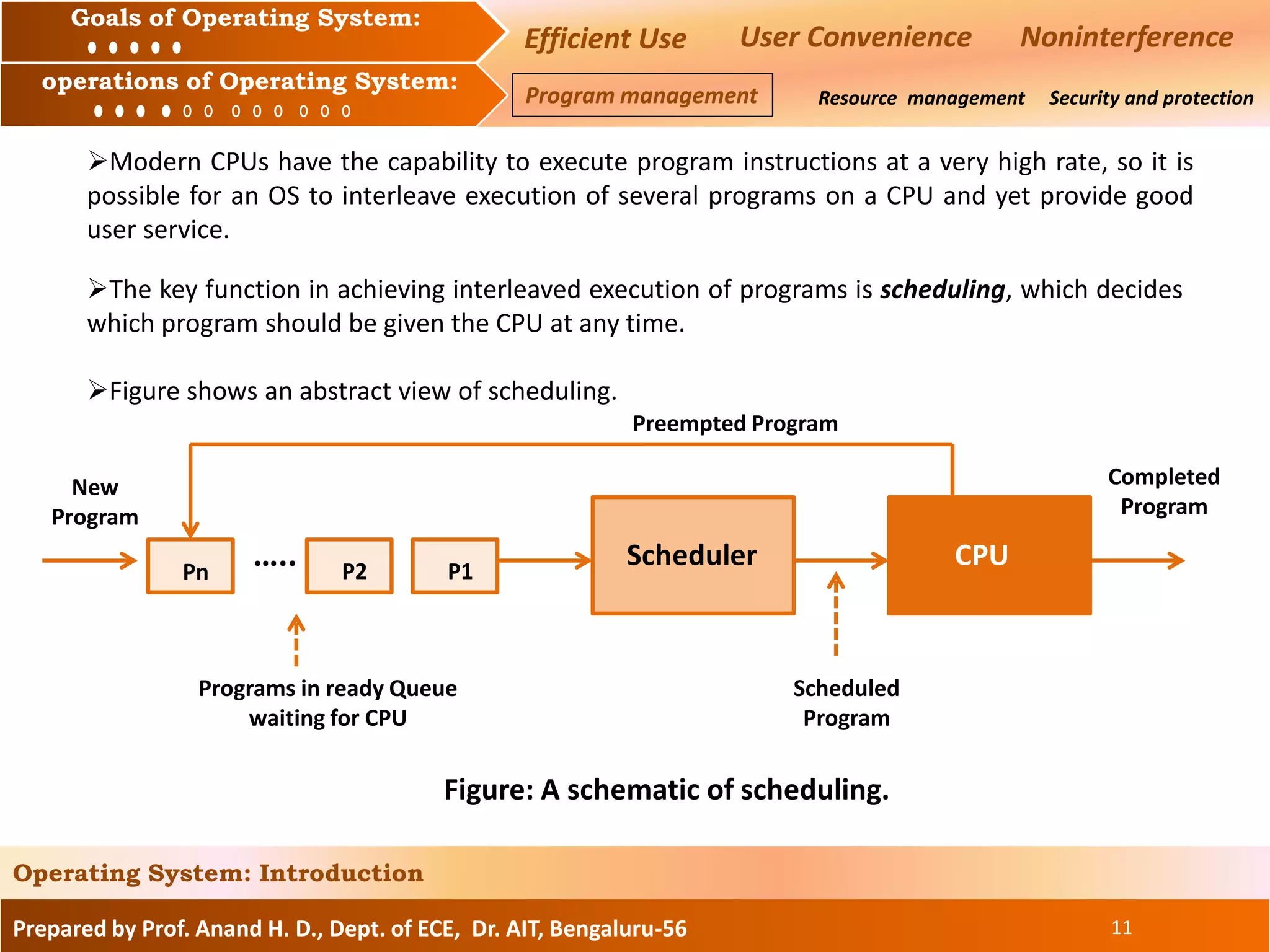
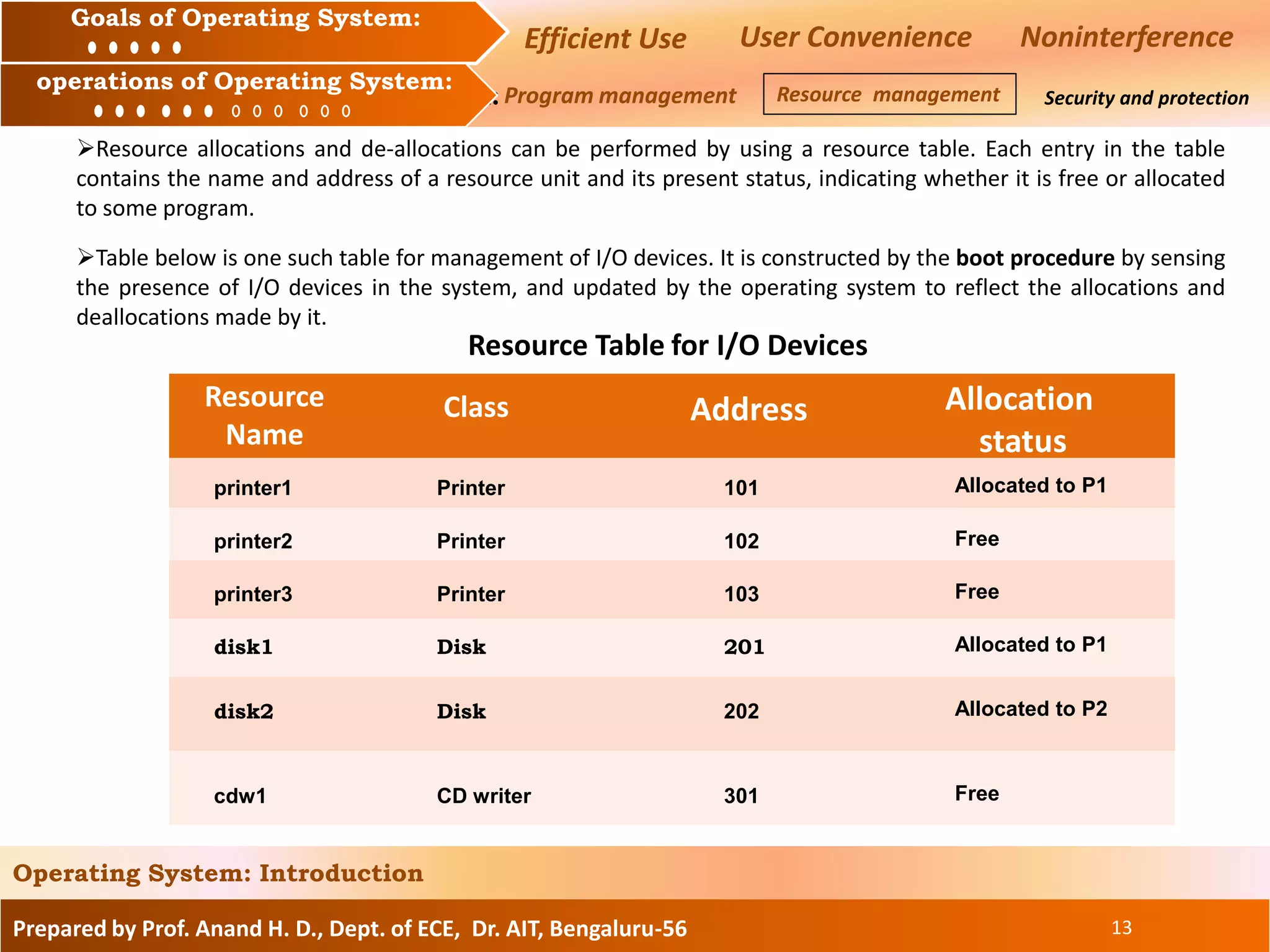
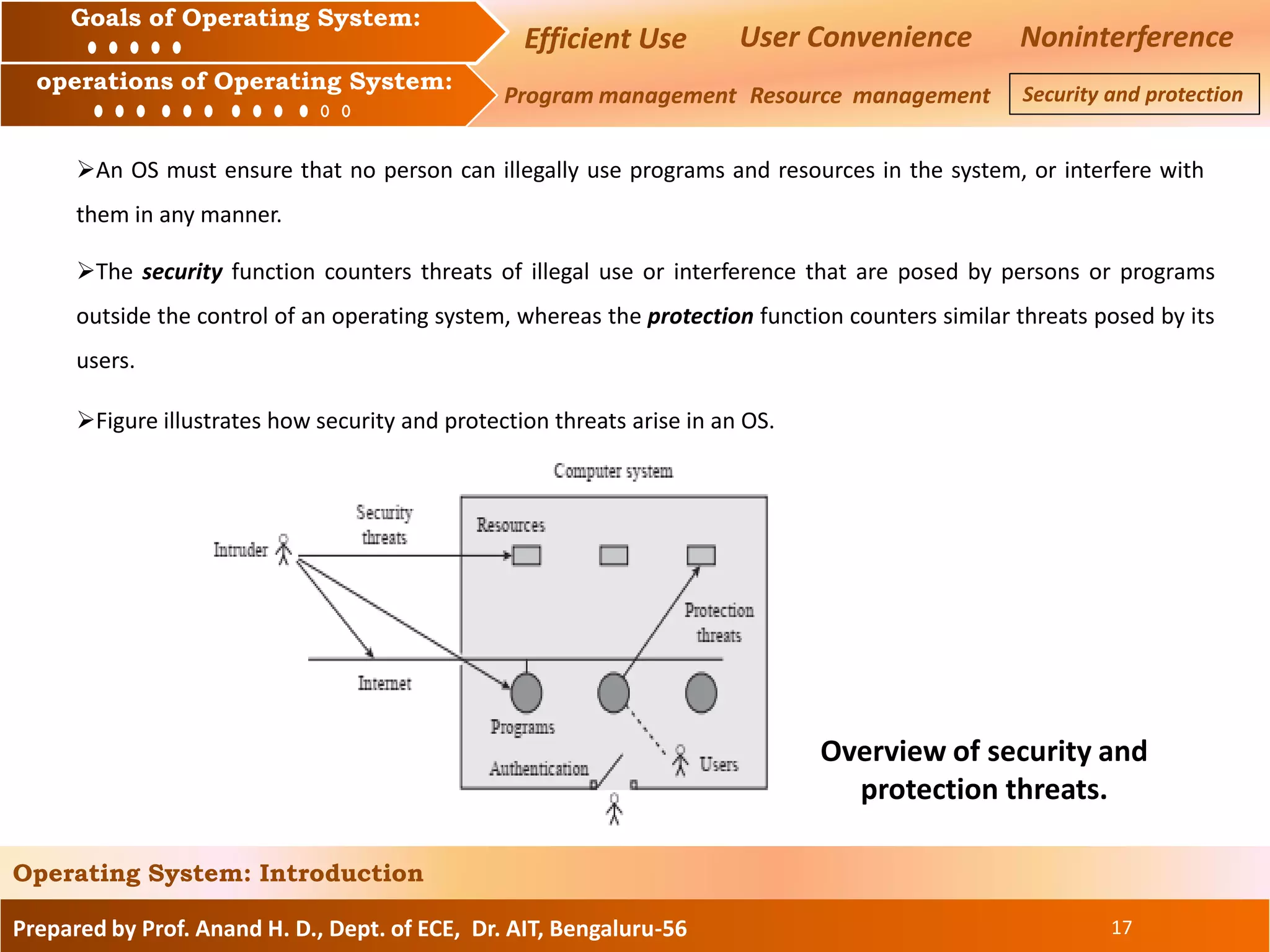
The document discusses the goals and operations of an operating system. The key goals of an operating system are efficient use of resources, user convenience, and preventing interference between users. The main operations of an operating system are program management, which involves executing and scheduling programs, resource management, which involves allocating and managing memory, CPU, and I/O devices, and security/protection which prevents unauthorized access to programs and data.