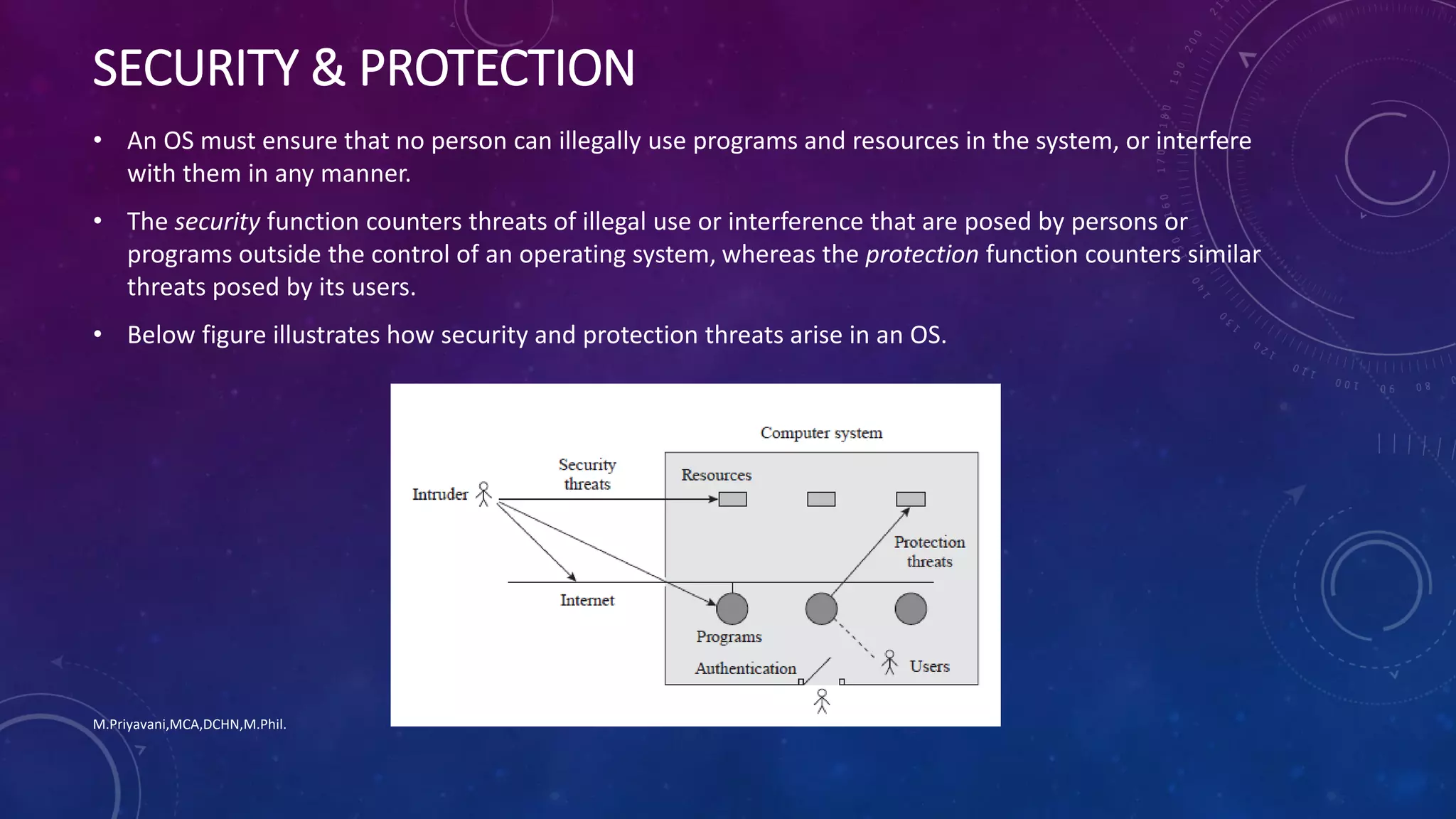
The document discusses the key functions and goals of an operating system from multiple perspectives:
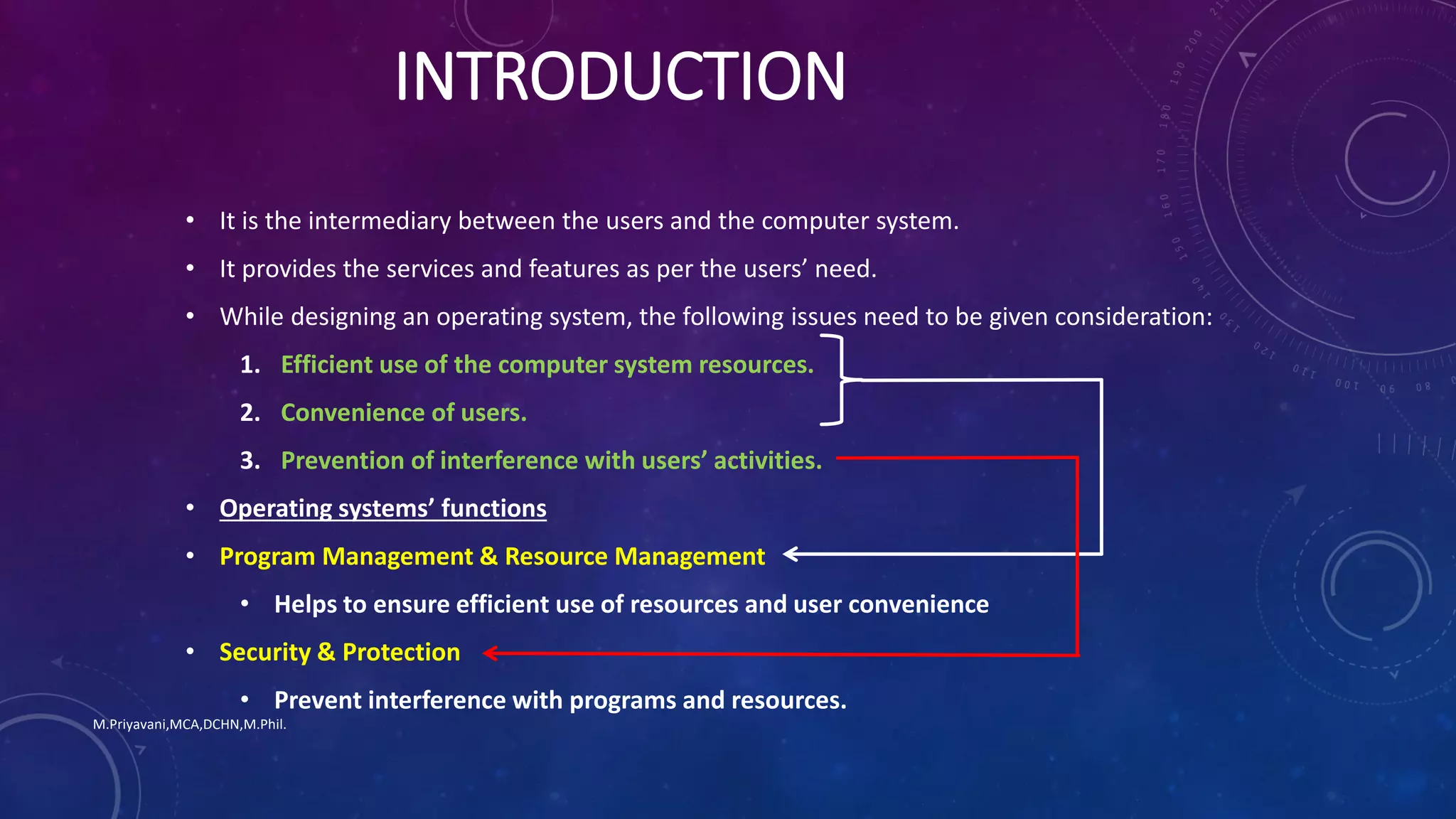
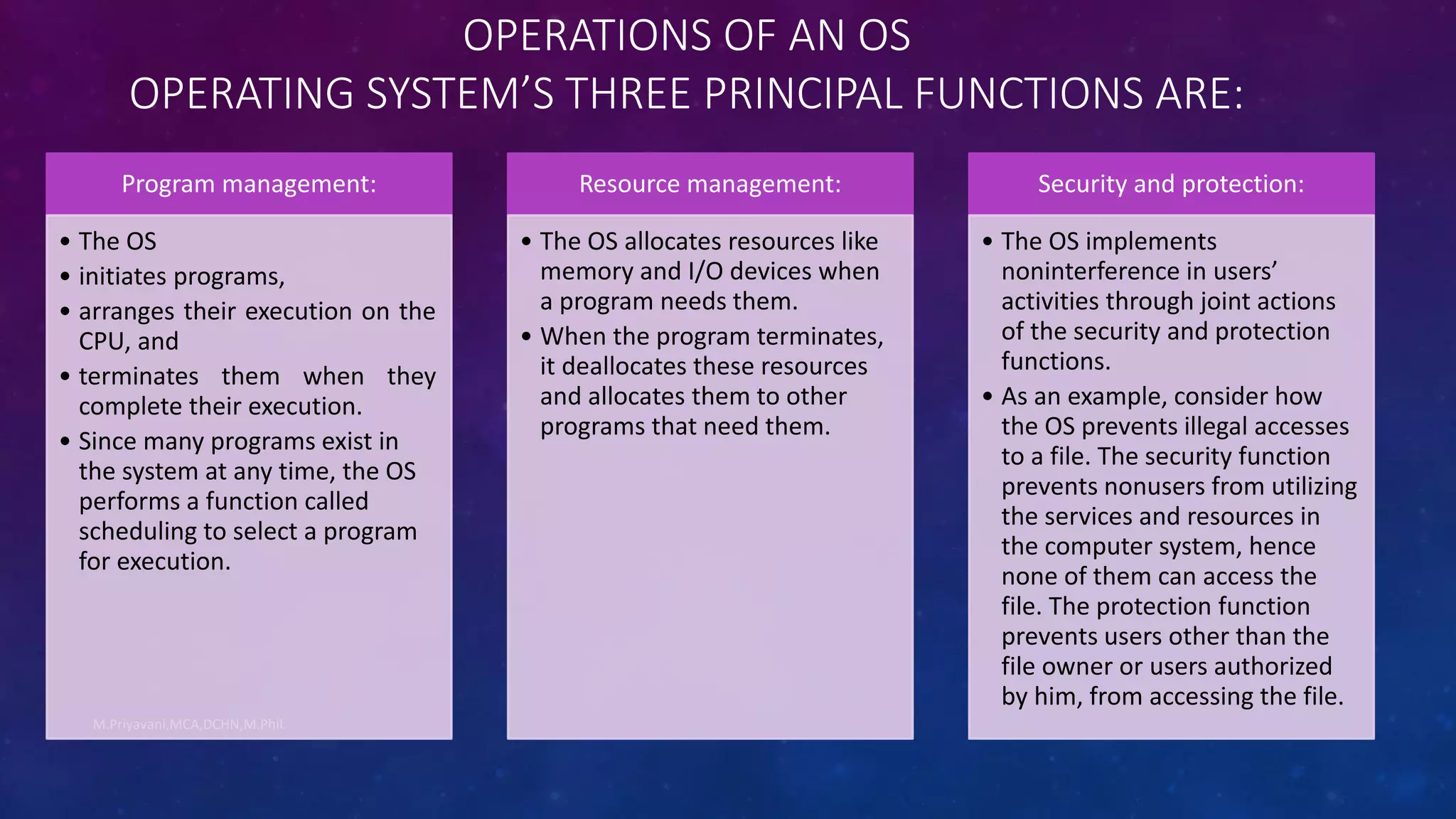
1. An operating system manages programs, allocates resources like memory and I/O devices, and provides security and protection between users. Its main goals are efficient use of computer resources, user convenience, and preventing interference between users.
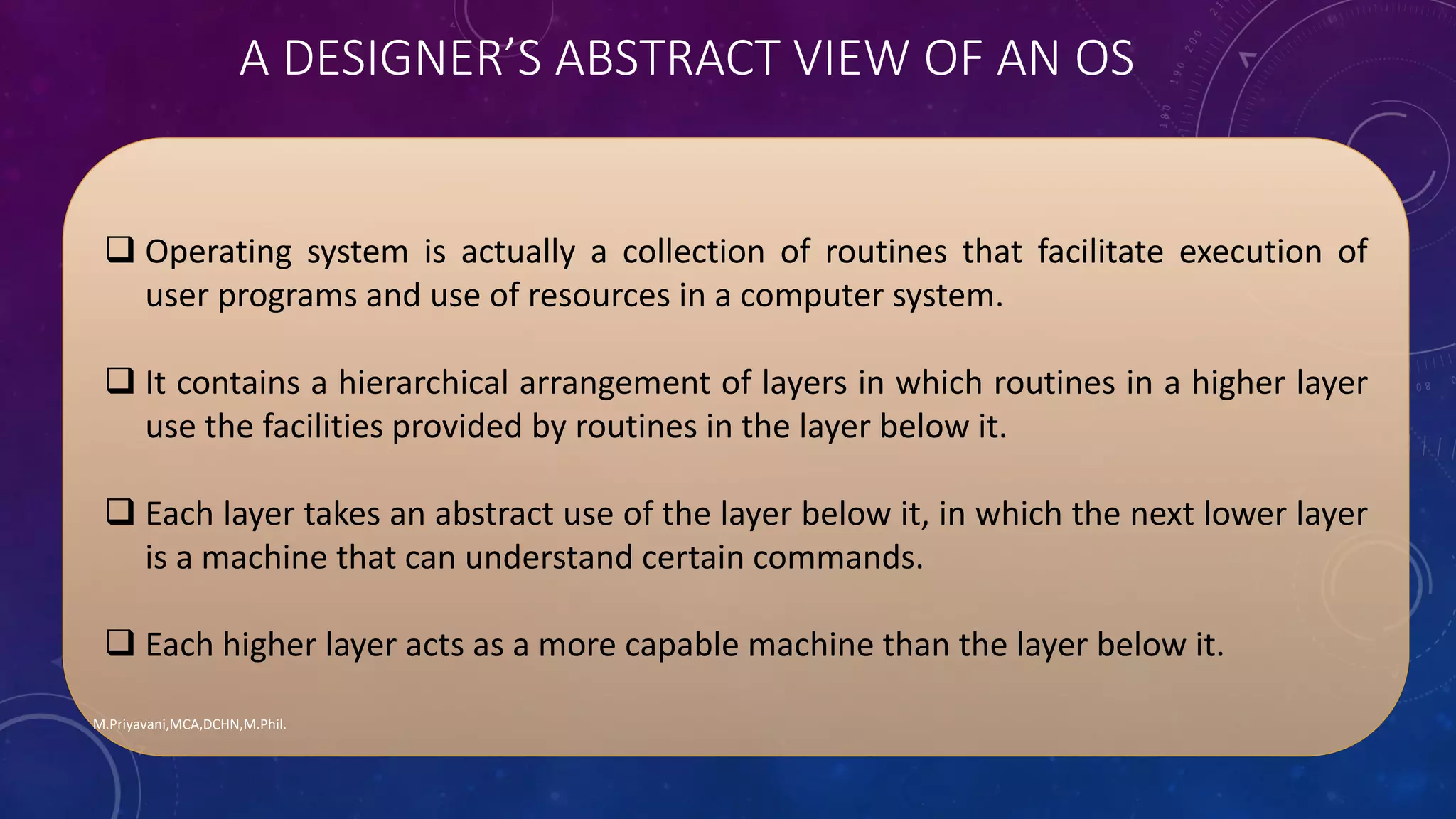
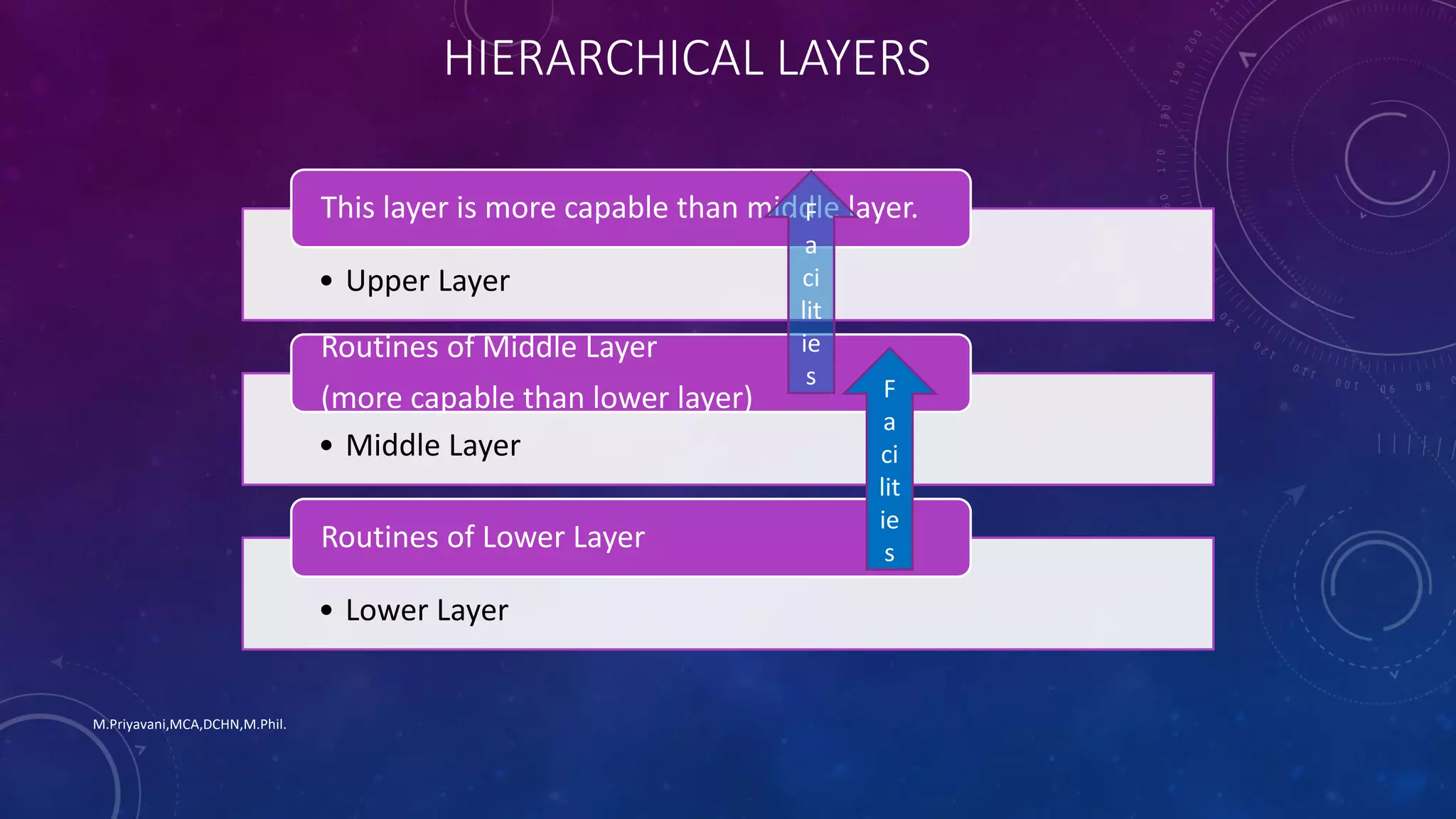
2. The OS can be viewed abstractly as a collection of layers, with higher layers acting as more capable machines than lower layers. This hierarchical view helps manage complexity and present generic schemes.
3. Scheduling is important for interleaving execution of programs on the CPU. The scheduler selects programs and specifies time limits before preempting programs to give others access. This impacts both efficiency and user