The document discusses the nature of viruses, specifically focusing on their impact on Linux compared to other operating systems like Windows and Mac. While Linux is not immune to viruses, it is generally safer due to its permissions structure, diverse distributions, and the large open-source community that quickly addresses vulnerabilities. Examples of Linux viruses are provided, but the document emphasizes that Linux's architecture makes it less susceptible to the harmful effects of viruses compared to other platforms.


















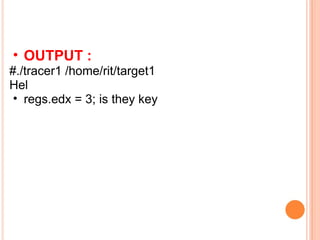
![/* target1.c */ int main() { char str[]=“Hello all n"; write(0, str, strlen(str)); return 0; } OUTPUT : Hello all](https://image.slidesharecdn.com/linuxvirus-12505961791703-phpapp01/85/Linux-Virus-24-320.jpg)
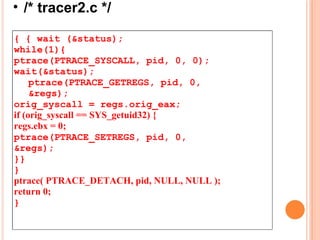
![/* tracer1.c */ if (pid == 0) { ptrace(PTRACE_TRACEME, 0, 0, 0); execl(argv[1], argv[1], NULL); } else { wait (&status); while(1) { ptrace(PTRACE_SYSCALL, pid, 0, 0); wait(&status); ptrace(PTRACE_GETREGS, pid, 0, ®s); orig_syscall = regs.orig_eax; if (orig_syscall == SYS_write) { regs.edx = 3; ptrace(PTRACE_SETREGS, pid, 0, ®s); }} }](https://image.slidesharecdn.com/linuxvirus-12505961791703-phpapp01/85/Linux-Virus-25-320.jpg)