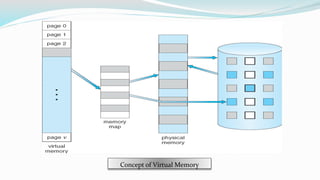
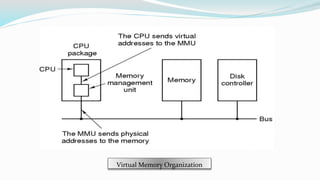
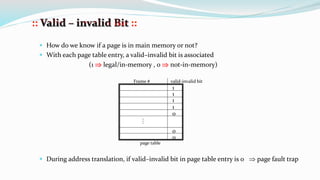
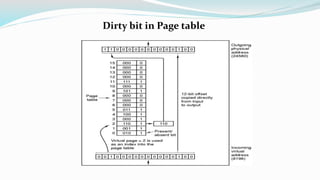
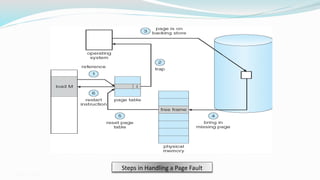
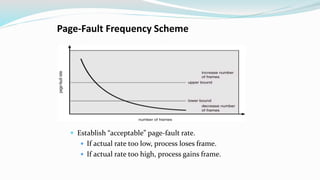
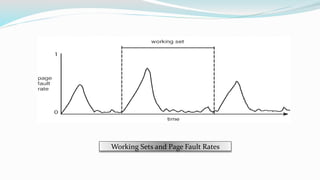
The document discusses virtual memory organization, which separates logical and physical address spaces, allowing for larger logical address spaces than physical memory. It explains mechanisms for handling page faults, including the role of page tables and the strategies to maintain an acceptable page-fault rate while minimizing system performance impacts. The document also introduces concepts like locality of reference and working sets, emphasizing the importance of keeping frequently accessed pages in memory to reduce thrashing.