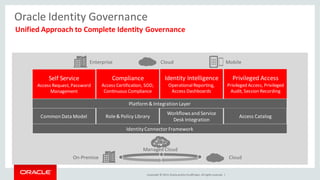
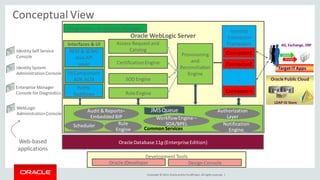
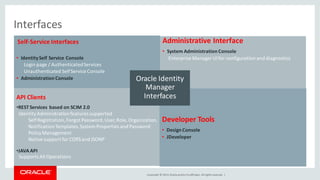
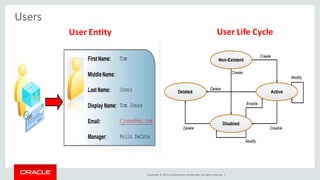
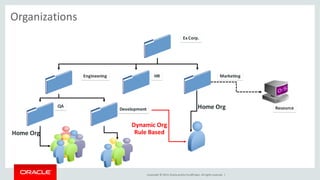
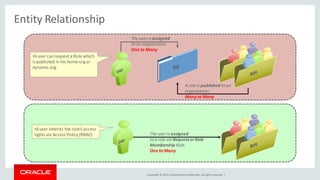
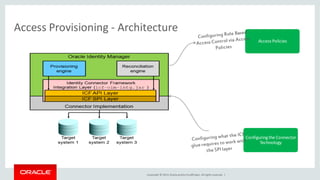
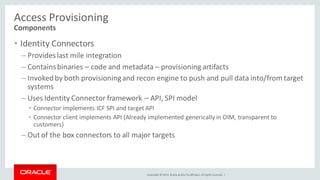
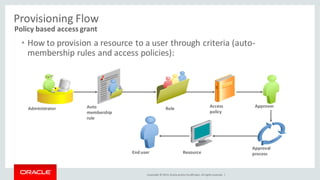
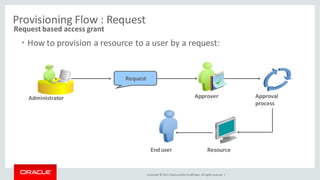
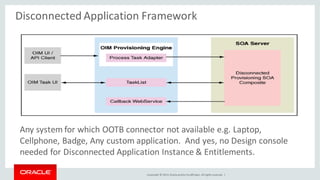
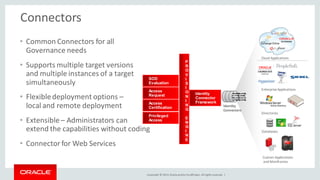
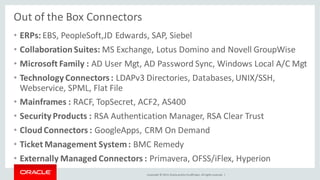
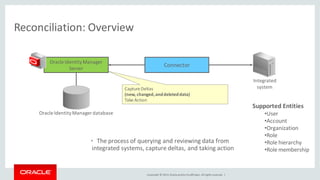
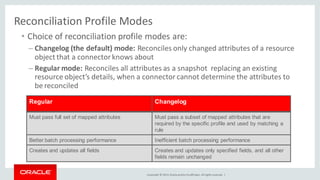
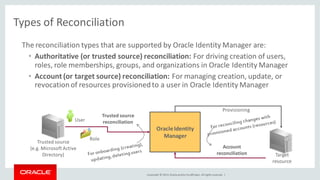
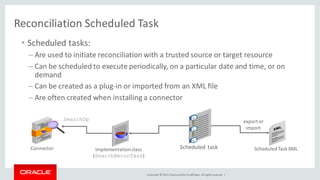
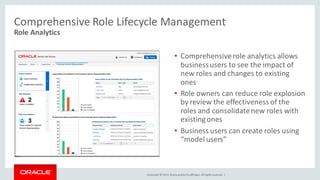
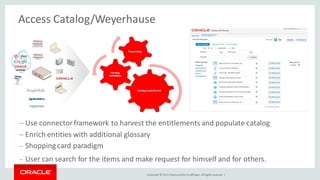
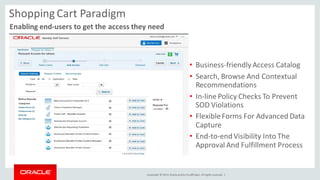
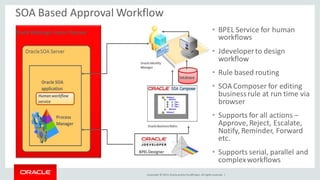
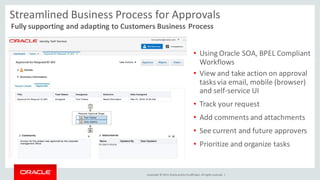
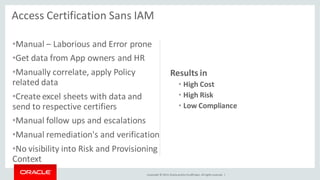
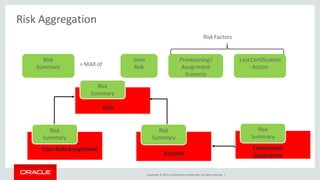
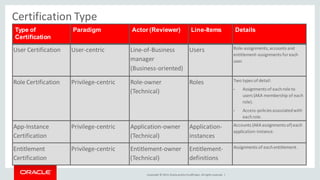
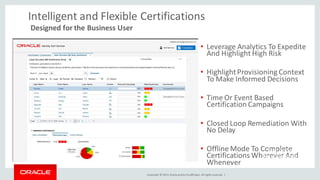
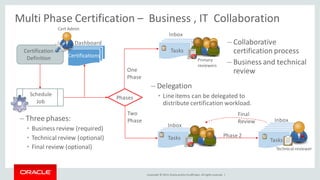
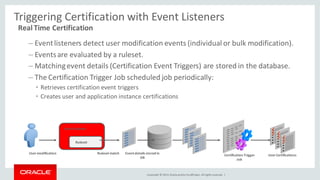
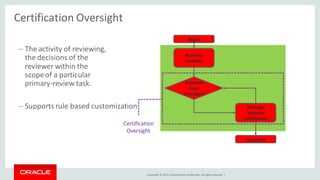
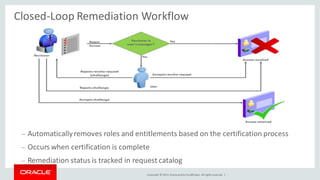
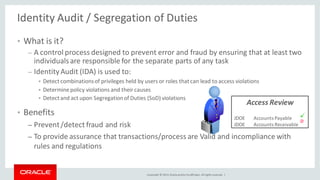
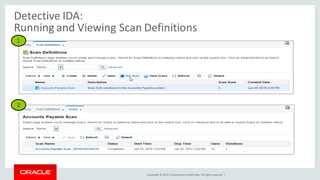
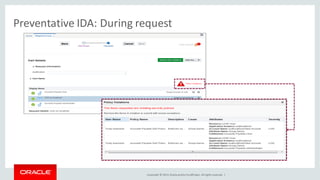
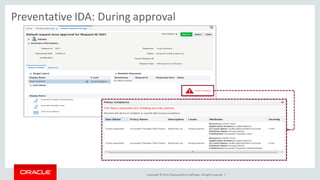
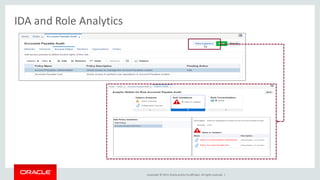
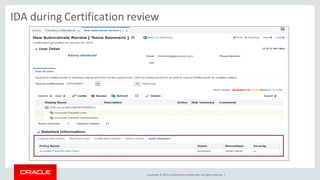
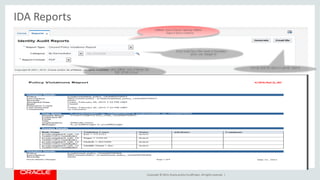
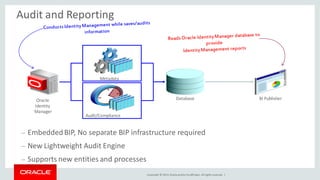
The document discusses Oracle Identity Governance, a unified identity and access governance solution. It addresses challenges of managing access across enterprise, mobile, and cloud applications. The solution provides identity administration, access request management, access risk management, privileged access management, and other features. It uses a modular architecture with components like self-service interfaces, runtime engines, connectors, and common services.