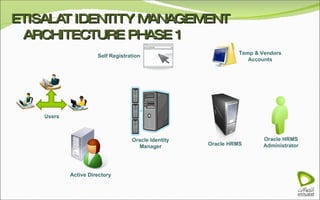
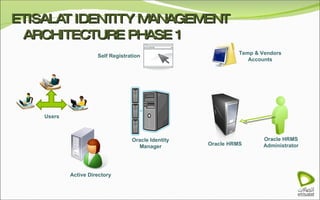
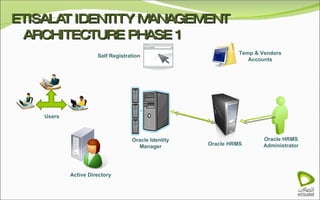
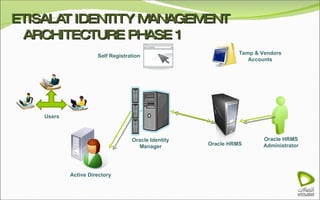
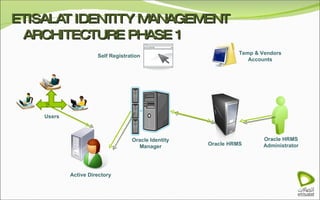
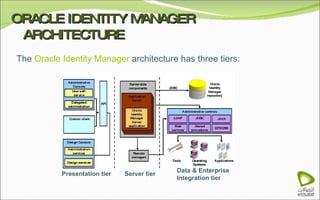
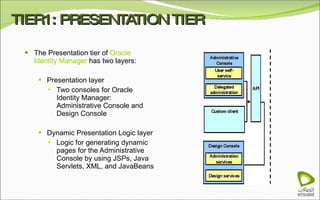
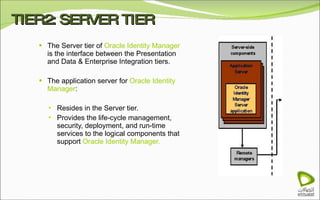
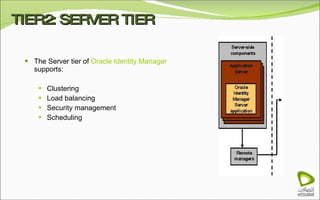
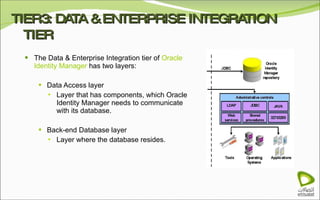
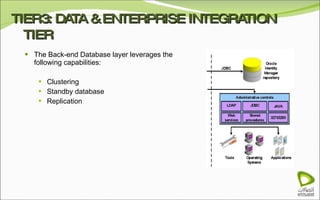
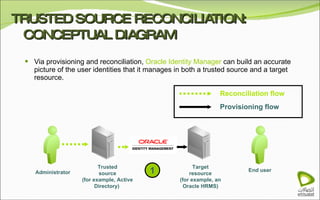
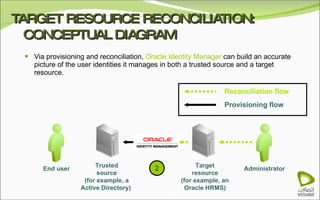
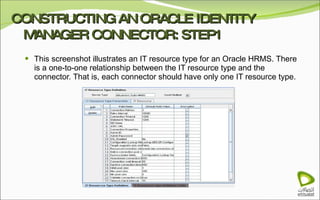
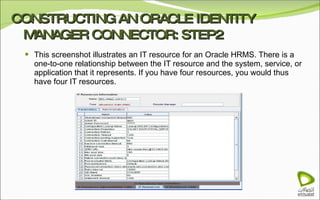
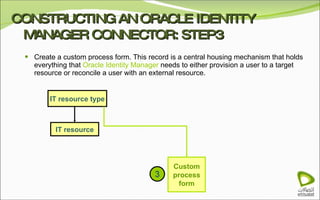
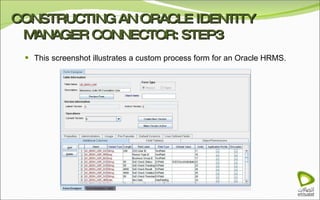
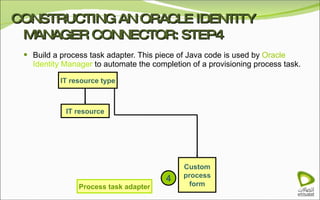
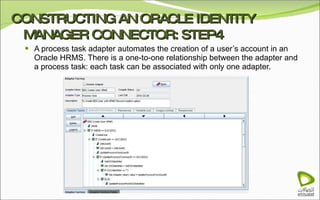
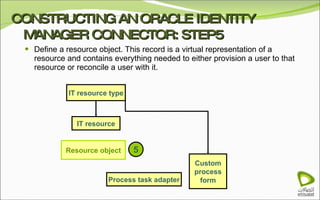
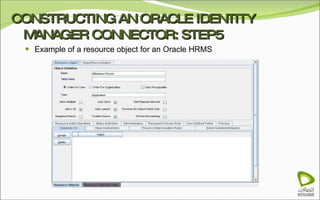
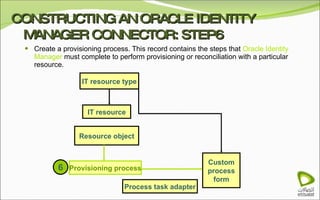
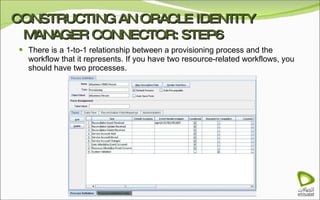
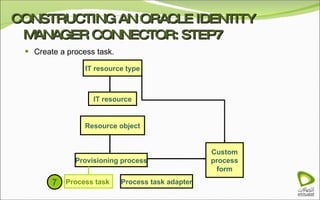
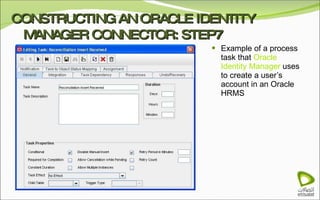
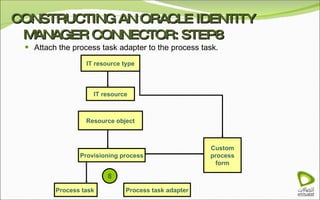
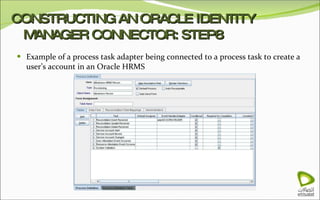
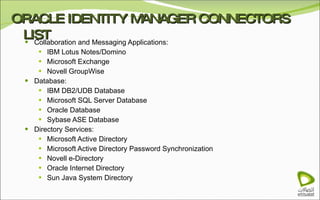
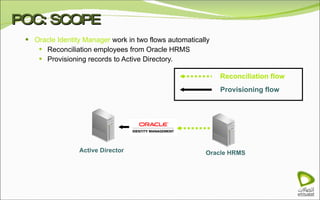
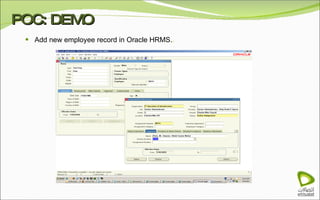
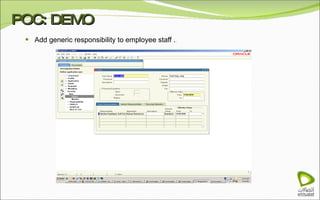
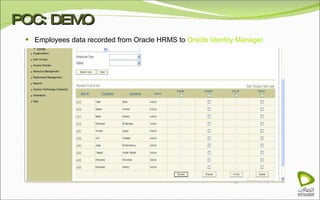
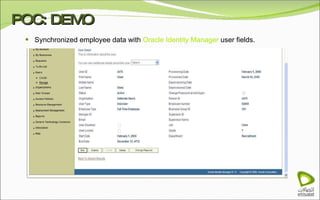
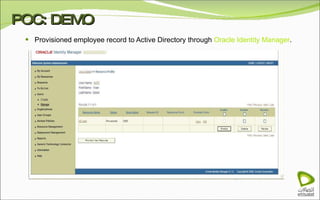
The document discusses Oracle Identity Manager, including its architecture and capabilities. It describes Oracle Identity Manager as an application that handles tasks related to managing user access privileges, such as creating, modifying, and removing access privileges. It then outlines Oracle Identity Manager's architecture, which includes presentation, server, and data/enterprise integration tiers. The presentation tier includes administrative and design consoles. The server tier provides services to logical components. And the data/enterprise integration tier includes data access and backend database layers.