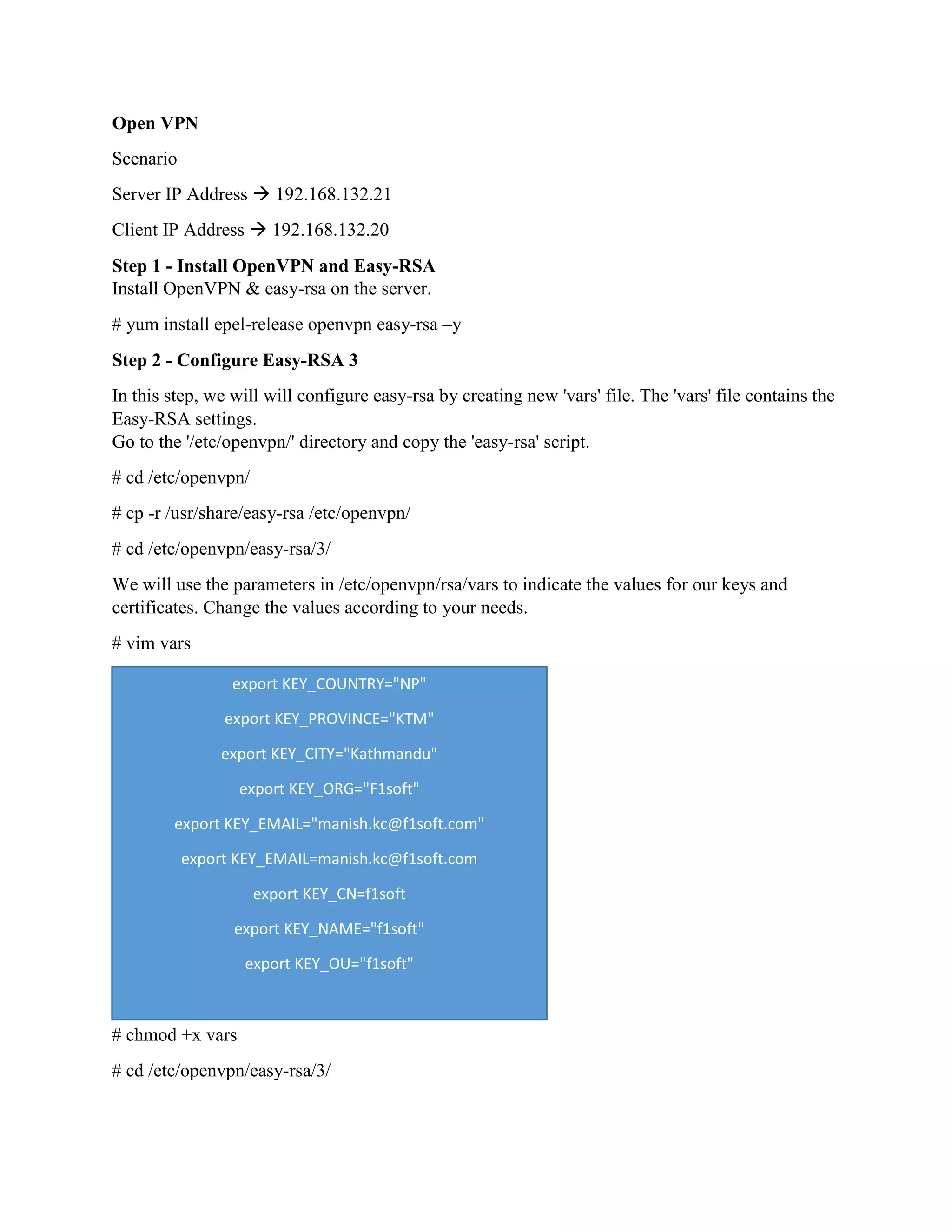
The document describes the steps to set up an OpenVPN server with Easy-RSA on a Linux system. It involves:
1. Installing OpenVPN and Easy-RSA packages and configuring Easy-RSA parameters and keys like CA, server, client, DH.
2. Generating certificates and keys for the OpenVPN server and client.
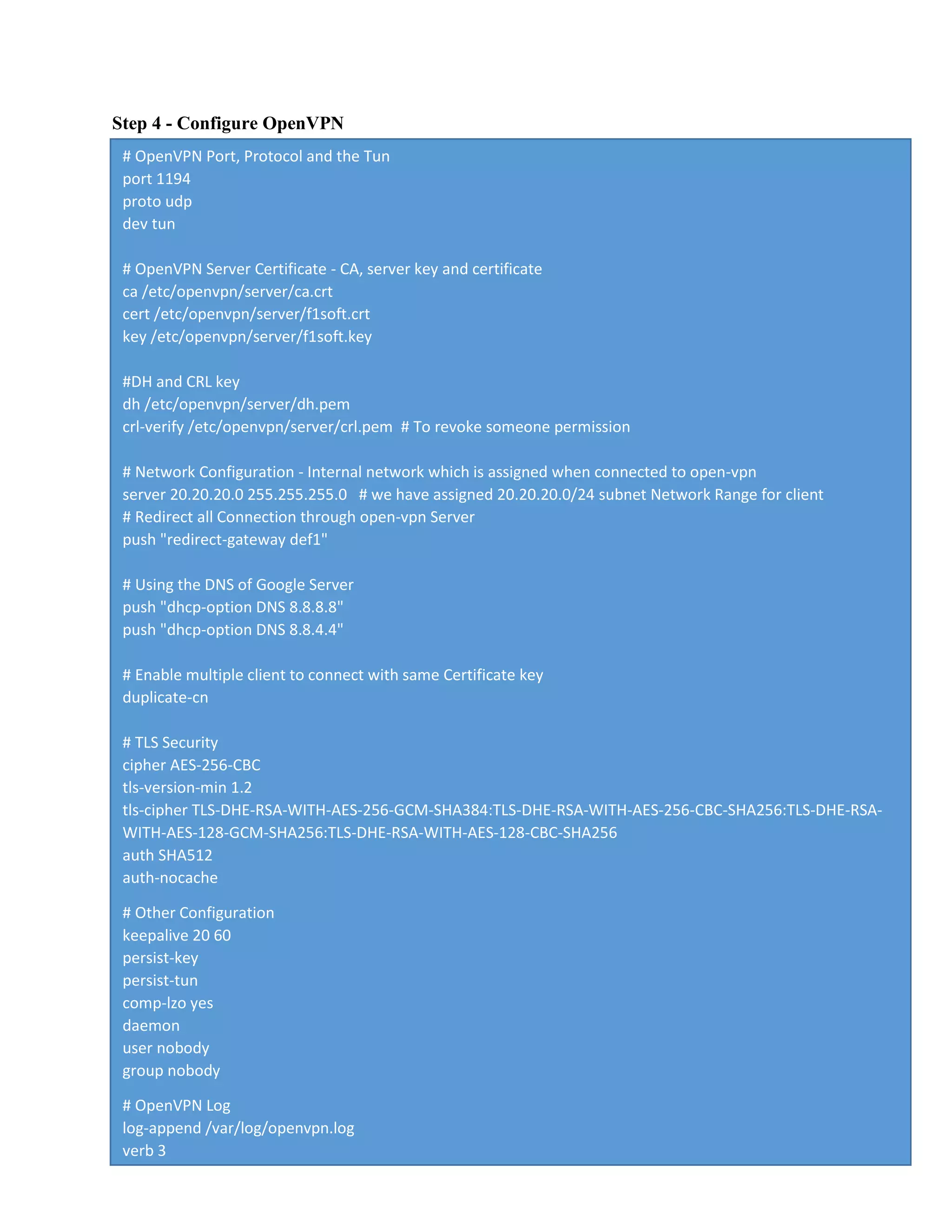
3. Configuring the OpenVPN server file with settings for port, protocol, network, authentication and other parameters.
4. Enabling port forwarding, starting the OpenVPN service, and verifying logs as the service starts.
![Step 3 - Build OpenVPN Keys
We will build the OpenVPN keys based on the easy-rsa 'vars' file that we've created. We will
build the CA key, Server and Client keys, DH and CRL PEM file.
We will build all those keys using the 'easyrsa' command line. Go to the '/etc/openvpn/easy-rsa/3'
directory.
# cd /etc/openvpn/easy-rsa/3/
Initialization and Build CA
# ./easyrsa init-pki
# ./easyrsa build-ca
[root@localhost 3]# ./easyrsa init-pki
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa/3/pki
[root@localhost 3]# ./easyrsa build-ca
Generating a 2048 bit RSA private key
..........+++
...................................................................+++
writing new private key to '/etc/openvpn/easy-rsa/3/pki/private/ca.key.h5pdSfY8qR'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated into your
certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:
CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/etc/openvpn/easy-rsa/3/pki/ca.crt](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-2-2048.jpg)
![Build key for Server
# ./easyrsa gen-req openvpn-server nopass
# ./easyrsa sign-req server openvpn-server
# openssl verify -CAfile pki/ca.crt pki/issued/openvpn-server.crt
[root@localhost 3]# ./easyrsa gen-req openvpn-server nopass
Generating a 2048 bit RSA private key
........................................................................+++
..............+++
writing new private key to '/etc/openvpn/easy-rsa/3/pki/private/openvpn
server.key.vzztQHFiy7'
-----
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you
can leave some blank
For some fields there will be a default value,If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [openvpn-server]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/3/pki/reqs/openvpn-server.req
key: /etc/openvpn/easy-rsa/3/pki/private/openvpn-server.key
[root@localhost 3]# ./easyrsa sign-req server openvpn-server
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request has not been cryptographically
verified. Please be sure it came from a trusted source or that you have verified the request checksum with the
sender.
Request subject, to be signed as a server certificate for 3650 days:
subject=
commonName = openvpn-server
Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes
Using configuration from ./openssl-1.0.cnf
Enter pass phrase for /etc/openvpn/easy-rsa/3/pki/private/ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:' openvpn-server '
Certificate is to be certified until Jul 22 15:50:28 2029 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa/3/pki/issued/openvpn-server.crt
[root@localhost 3]# openssl verify -CAfile pki/ca.crt pki/issued/openvpn-server.crt
pki/issued/openvpn-server.crt: OK](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-3-2048.jpg)
![Build key for Client
# ./easyrsa gen-req client01 nopass
# ./easyrsa sign-req client client01
# openssl verify -CAfile pki/ca.crt pki/issued/client01.crt
[root@localhost 3]# ./easyrsa gen-req client01 nopass
Note: using Easy-RSA configuration from: ./vars
Generating a 2048 bit RSA private key
.......................+++
......................+++
writing new private key to '/etc/openvpn/easy-rsa/3/pki/private/client01.key.dOKxCAo7ET'
-----
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [client01]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/3/pki/reqs/client01.req
key: /etc/openvpn/easy-rsa/3/pki/private/client01.key
[root@localhost 3]# ./easyrsa sign-req client client01
Note: using Easy-RSA configuration from: ./vars
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request has not been cryptographically
verified. Please be sure it came from a trusted source or that you have verified the request checksum with the
sender.
Request subject, to be signed as a client certificate for 3650 days:
subject=
commonName = client01
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes
Using configuration from ./openssl-1.0.cnf
Enter pass phrase for /etc/openvpn/easy-rsa/3/pki/private/ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'client01'
Certificate is to be certified until Jul 22 16:28:50 2029 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa/3/pki/issued/client01.crt
[root@localhost 3]# openssl verify -CAfile pki/ca.crt pki/issued/client01.crt
pki/issued/client01.crt: OK](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-4-2048.jpg)
![Build Diffie-Hellman Key
# ./easyrsa gen-dh
[root@localhost 3]# ./easyrsa gen-dh
Note: using Easy-RSA configuration from: ./vars
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
...................................................................................................................................................................................
.+.....................+................................................................+.....................................................................................+
......................................................................+...........................................................................................................
...............................................................................+..................................................................................................
...................................................................................................................................................................................
.................................+.........................+......................................................................................................+....+.......
.+.......................................................................................................................+.........................+............................
..........................................................................................................................................+...................................+..
.................+.......................................................+....................................+...................+............................................
................+..........................................................................................................................................................+.....
.......................................................................+..........................................+..............................................................
...........+.............................................................................................................................................................+.......
................................................+.................................................................................................................................
...........................................................................................................+......................................................................
.............................................+...................................................................................................................+...............
.......+..........................................................................................................................................................................
............................................+.....................................................................................................................................
.....+................+..................................................+...................................................+....+...+......................................
..........................................................................................+.......................................................................................
....+.............................................................................................................................................................................
...................................................+.................................................................................+...........................................
...............................+...........+...................... ...........+........................+..................................++*++*
DH parameters of size 2048 created at /etc/openvpn/easy-rsa/3/pki/dh.pem](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-5-2048.jpg)
![Optional: Generate the CRL Key
The CRL (Certificate Revoking List) key will be used for revoking the client key. If you have
multiple client certificates on your vpn server, and you want to revoke some key, you just need
to revoke using the easy-rsa command.
If you want to revoke some key, run the command as below.
# ./easyrsa revoke someone
# ./easyrsa gen-crl
[root@localhost 3]# ./easyrsa revoke client02
Note: using Easy-RSA configuration from: ./vars
Please confirm you wish to revoke the certificate with the following subject:
subject=
commonName = client02
Type the word 'yes' to continue, or any other input to abort.
Continue with revocation: yes
Using configuration from ./openssl-1.0.cnf
Enter pass phrase for /etc/openvpn/easy-rsa/3/pki/private/ca.key:
Revoking Certificate D2A6B677A78A2C506D676D0C0EEFDF5F.
Data Base Updated
IMPORTANT!!!
Revocation was successful. You must run gen-crl and upload a CRL to your infrastructure in order to prevent
the revoked cert from being accepted.
[root@localhost 3]# ./easyrsa gen-crl
Note: using Easy-RSA configuration from: ./vars
Using configuration from ./openssl-1.0.cnf
Enter pass phrase for /etc/openvpn/easy-rsa/3/pki/private/ca.key:
An updated CRL has been created.
CRL file: /etc/openvpn/easy-rsa/3/pki/crl.pem](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-6-2048.jpg)

![In this step, we will create new configuration 'server.conf' for the openvpn server.
Go to the '/etc/openvpn/' directory and create new configuration file 'server.conf' using vi.
# cd /etc/openvpn/
# vim server.conf
Save and exit.
The configuration for OpenVPN has been created.
Step 5 - Enable Port-Forwarding
In this step, we will enable Port-forwarding kernel module.
Enable the port-forwarding kernel module by running following commands.
# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf
# sysctl –p
Starting & Stopping the Service
Start the openvpn service and enable it to launch automatically everytime at system boot.
Note: what name.conf you create at step 4 will be the service i.e. if you create test.conf the you
have to start using systemctl start openvpn@test
# systemctl start openvpn@server
# systemctl enable openvpn@server
[root@localhost ~]# systemctl status openvpn@server
● openvpn@server.service - OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 2019-07-28 06:15:20 +0545; 29s ago
Main PID: 6840 (openvpn)
Status: "Initialization Sequence Completed"
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
└─6840 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf
Jul 28 06:15:19 localhost.localdomain systemd[1]: Starting OpenVPN Robust And Highly Flexible Tunneling
Applicati...r...Jul 28 06:15:20 localhost.localdomain systemd[1]: Started OpenVPN Robust And Highly Flexible
Tunneling Applicatio...ver.Hint: Some lines were ellipsized, use -l to show in full.](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-9-2048.jpg)
![Logs while starting the server
Sun Jul 28 06:47:45 2019 OpenVPN 2.4.7 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO]
[LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Feb 20 2019
Sun Jul 28 06:47:45 2019 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06
Sun Jul 28 06:47:45 2019 Diffie-Hellman initialized with 2048 bit key
Sun Jul 28 06:47:45 2019 ROUTE_GATEWAY 192.168.132.2/255.255.255.0 IFACE=ens33
HWADDR=00:50:56:3e:36:15
Sun Jul 28 06:47:45 2019 TUN/TAP device tun0 opened
Sun Jul 28 06:47:45 2019 TUN/TAP TX queue length set to 100
Sun Jul 28 06:47:45 2019 /sbin/ip link set dev tun0 up mtu 1500
Sun Jul 28 06:47:45 2019 /sbin/ip addr add dev tun0 local 20.20.20.1 peer 20.20.20.2
Sun Jul 28 06:47:45 2019 /sbin/ip route add 20.20.20.0/24 via 20.20.20.2
Sun Jul 28 06:47:45 2019 Could not determine IPv4/IPv6 protocol. Using AF_INET
Sun Jul 28 06:47:45 2019 Socket Buffers: R=[212992->212992] S=[212992->212992]
Sun Jul 28 06:47:45 2019 UDPv4 link local (bound): [AF_INET][undef]:1194
Sun Jul 28 06:47:45 2019 UDPv4 link remote: [AF_UNSPEC]
Sun Jul 28 06:47:45 2019 GID set to nobody
Sun Jul 28 06:47:45 2019 UID set to nobody
Sun Jul 28 06:47:45 2019 MULTI: multi_init called, r=256 v=256
Sun Jul 28 06:47:45 2019 IFCONFIG POOL: base=20.20.20.4 size=62, ipv6=0
Sun Jul 28 06:47:45 2019 Initialization Sequence Completed](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-10-2048.jpg)
![Client logs while connecting to open-vpn server
root@localhost client]# openvpn --config client01.ovpn
Sun Jul 28 13:22:57 2019 OpenVPN 2.4.7 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)]
[LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Feb 20 2019
Sun Jul 28 13:22:57 2019 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06
Sun Jul 28 13:22:57 2019 TCP/UDP: Preserving recently used remote address:
[AF_INET]192.168.132.21:1194
Sun Jul 28 13:22:57 2019 Socket Buffers: R=[212992->212992] S=[212992->212992]
Sun Jul 28 13:22:57 2019 UDP link local: (not bound)
Sun Jul 28 13:22:57 2019 UDP link remote: [AF_INET]192.168.132.21:1194
Sun Jul 28 13:22:57 2019 TLS: Initial packet from [AF_INET]192.168.132.21:1194, sid=61588936 583f6808
Sun Jul 28 13:22:57 2019 VERIFY OK: depth=1, CN=f1soft.com
Sun Jul 28 13:22:57 2019 VERIFY KU OK
Sun Jul 28 13:22:57 2019 Validating certificate extended key usage
Sun Jul 28 13:22:57 2019 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web
Server Authentication
Sun Jul 28 13:22:57 2019 VERIFY EKU OK
Sun Jul 28 13:22:57 2019 VERIFY OK: depth=0, CN=f1soft.com
Sun Jul 28 13:22:57 2019 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-
SHA384, 2048 bit RSA
Sun Jul 28 13:22:57 2019 [f1soft.com] Peer Connection Initiated with [AF_INET]192.168.132.21:1194
Sun Jul 28 13:22:59 2019 SENT CONTROL [f1soft.com]: 'PUSH_REQUEST' (status=1)
Sun Jul 28 13:22:59 2019 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-
option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route 20.20.20.1,topology net30,ping 20,ping-restart 60,ifconfig
20.20.20.6 20.20.20.5,peer-id 0,cipher AES-256-GCM'
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: timers and/or timeouts modified
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: --ifconfig/up options modified
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: route options modified
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: peer-id set
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: adjusting link_mtu to 1625
Sun Jul 28 13:22:59 2019 OPTIONS IMPORT: data channel crypto options modified
Sun Jul 28 13:22:59 2019 Data Channel: using negotiated cipher 'AES-256-GCM'
Sun Jul 28 13:22:59 2019 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jul 28 13:22:59 2019 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jul 28 13:22:59 2019 ROUTE_GATEWAY 192.168.132.2/255.255.255.0 IFACE=ens33
HWADDR=00:0c:29:47:82:03
Sun Jul 28 13:22:59 2019 TUN/TAP device tun0 opened
Sun Jul 28 13:22:59 2019 TUN/TAP TX queue length set to 100
Sun Jul 28 13:22:59 2019 /sbin/ip link set dev tun0 up mtu 1500
Sun Jul 28 13:22:59 2019 /sbin/ip addr add dev tun0 local 20.20.20.6 peer 20.20.20.5
Sun Jul 28 13:22:59 2019 /sbin/ip route add 192.168.132.21/32 dev ens33
Sun Jul 28 13:22:59 2019 /sbin/ip route add 0.0.0.0/1 via 20.20.20.5
Sun Jul 28 13:22:59 2019 /sbin/ip route add 128.0.0.0/1 via 20.20.20.5
Sun Jul 28 13:22:59 2019 /sbin/ip route add 20.20.20.1/32 via 20.20.20.5
Sun Jul 28 13:22:59 2019 Initialization Sequence Completed](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-12-2048.jpg)
![Server logs while connecting to open-vpn server
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 TLS: Initial packet from [AF_INET]192.168.132.20:50282,
sid=229911de 9b6d7502
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 VERIFY OK: depth=1, CN=f1soft.com
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 VERIFY OK: depth=0, CN=f1soft
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_VER=2.4.7
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_PLAT=linux
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_PROTO=2
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_NCP=2
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_LZ4=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_LZ4v2=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_LZO=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_COMP_STUB=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_COMP_STUBv2=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 peer info: IV_TCPNL=1
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-
AES256-GCM-SHA384, 2048 bit RSA
Sun Jul 28 06:55:55 2019 192.168.132.20:50282 [f1soft] Peer Connection Initiated with
[AF_INET]192.168.132.20:50282
Sun Jul 28 06:55:55 2019 f1soft/192.168.132.20:50282 MULTI_sva: pool returned IPv4=20.20.20.10,
IPv6=(Not enabled)
Sun Jul 28 06:55:55 2019 f1soft/192.168.132.20:50282 MULTI: Learn: 20.20.20.10 ->
f1soft/192.168.132.20:50282
Sun Jul 28 06:55:55 2019 f1soft/192.168.132.20:50282 MULTI: primary virtual IP for
f1soft/192.168.132.20:50282: 20.20.20.10
Sun Jul 28 06:55:56 2019 f1soft/192.168.132.20:50282 PUSH: Received control message: 'PUSH_REQUEST'
Sun Jul 28 06:55:56 2019 f1soft/192.168.132.20:50282 SENT CONTROL [f1soft]: 'PUSH_REPLY,redirect-
gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route 20.20.20.1,topology net30,ping
20,ping-restart 60,ifconfig 20.20.20.10 20.20.20.9,peer-id 1,cipher AES-256-GCM' (status=1)
Sun Jul 28 06:55:56 2019 f1soft/192.168.132.20:50282 Data Channel: using negotiated cipher 'AES-256-
GCM'
Sun Jul 28 06:55:56 2019 f1soft/192.168.132.20:50282 Outgoing Data Channel: Cipher 'AES-256-GCM'
initialized with 256 bit key
Sun Jul 28 06:55:56 2019 f1soft/192.168.132.20:50282 Incoming Data Channel: Cipher 'AES-256-GCM'
initialized with 256 bit key](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-13-2048.jpg)
![Logs of client in windows
Sun Jul 28 13:34:02 2019 OpenVPN 2.4.7 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11]
[AEAD] built on Apr 25 2019
Sun Jul 28 13:34:02 2019 Windows version 6.2 (Windows 8 or greater) 64bit
Sun Jul 28 13:34:02 2019 library versions: OpenSSL 1.1.0j 20 Nov 2018, LZO 2.10
Enter Management Password:
Sun Jul 28 13:34:02 2019 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Sun Jul 28 13:34:02 2019 Need hold release from management interface, waiting...
Sun Jul 28 13:34:02 2019 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'state on'
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'log all on'
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'echo all on'
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'bytecount 5'
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'hold off'
Sun Jul 28 13:34:02 2019 MANAGEMENT: CMD 'hold release'
Sun Jul 28 13:34:02 2019 TCP/UDP: Preserving recently used remote address:
[AF_INET]192.168.132.21:1194
Sun Jul 28 13:34:02 2019 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Jul 28 13:34:02 2019 UDP link local: (not bound)
Sun Jul 28 13:34:02 2019 UDP link remote: [AF_INET]192.168.132.21:1194
Sun Jul 28 13:34:02 2019 MANAGEMENT: >STATE:1564300142,WAIT,,,,,,
Sun Jul 28 13:34:02 2019 MANAGEMENT: >STATE:1564300142,AUTH,,,,,,
Sun Jul 28 13:34:02 2019 TLS: Initial packet from [AF_INET]192.168.132.21:1194, sid=f41be3ac d2ff3b47
Sun Jul 28 13:34:02 2019 VERIFY OK: depth=1, CN=f1soft.com
Sun Jul 28 13:34:02 2019 VERIFY KU OK
Sun Jul 28 13:34:02 2019 Validating certificate extended key usage
Sun Jul 28 13:34:02 2019 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web
Server Authentication
Sun Jul 28 13:34:02 2019 VERIFY EKU OK
Sun Jul 28 13:34:02 2019 VERIFY OK: depth=0, CN=f1soft.com
Sun Jul 28 13:34:02 2019 Control Channel: TLSv1.2, cipher TLSv1.2 DHE-RSA-AES256-GCM-SHA384,
2048 bit RSA
Sun Jul 28 13:34:02 2019 [f1soft.com] Peer Connection Initiated with [AF_INET]192.168.132.21:1194
Sun Jul 28 13:34:03 2019 MANAGEMENT: >STATE:1564300143,GET_CONFIG,,,,,,
Sun Jul 28 13:34:03 2019 SENT CONTROL [f1soft.com]: 'PUSH_REQUEST' (status=1)
Sun Jul 28 13:34:03 2019 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-
option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route 20.20.20.1,topology net30,ping 20,ping-restart 60,ifconfig
20.20.20.6 20.20.20.5,peer-id 0,cipher AES-256-GCM'
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: timers and/or timeouts modified
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: --ifconfig/up options modified
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: route options modified
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modifiedSun Jul 28
13:34:03 2019 OPTIONS IMPORT: peer-id set
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: adjusting link_mtu to 1625
Sun Jul 28 13:34:03 2019 OPTIONS IMPORT: data channel crypto options modified
Sun Jul 28 13:34:03 2019 Data Channel: using negotiated cipher 'AES-256-GCM'](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-15-2048.jpg)
![Sun Jul 28 13:34:03 2019 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jul 28 13:34:03 2019 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jul 28 13:34:03 2019 interactive service msg_channel=604
Sun Jul 28 13:34:03 2019 ROUTE_GATEWAY 10.20.222.1/255.255.255.0 I=14
HWADDR=28:d2:44:71:04:ef
Sun Jul 28 13:34:03 2019 open_tun
Sun Jul 28 13:34:03 2019 TAP-WIN32 device [Ethernet 2] opened: .Global{D4A1E2D0-2F5A-4E79-B928-
04BB0AF5D34F}.tap
Sun Jul 28 13:34:03 2019 TAP-Windows Driver Version 9.23
Sun Jul 28 13:34:03 2019 Notified TAP-Windows driver to set a DHCP IP/netmask of
20.20.20.6/255.255.255.252 on interface {D4A1E2D0-2F5A-4E79-B928-04BB0AF5D34F} [DHCP-serv:
20.20.20.5, lease-time: 31536000]
Sun Jul 28 13:34:03 2019 Successful ARP Flush on interface [27] {D4A1E2D0-2F5A-4E79-B928-04BB0AF5D34F}
Sun Jul 28 13:34:04 2019 MANAGEMENT: >STATE:1564300144,ASSIGN_IP,,20.20.20.6,,,,
Sun Jul 28 13:34:09 2019 TEST ROUTES: 2/2 succeeded len=1 ret=1 a=0 u/d=up
Sun Jul 28 13:34:09 2019 C:Windowssystem32route.exe ADD 192.168.132.21 MASK 255.255.255.255
10.20.222.1
Sun Jul 28 13:34:09 2019 Route addition via service succeeded
Sun Jul 28 13:34:09 2019 C:Windowssystem32route.exe ADD 0.0.0.0 MASK 128.0.0.0 20.20.20.5
Sun Jul 28 13:34:09 2019 Route addition via service succeeded
Sun Jul 28 13:34:09 2019 C:Windowssystem32route.exe ADD 128.0.0.0 MASK 128.0.0.0 20.20.20.5
Sun Jul 28 13:34:09 2019 Route addition via service succeeded
Sun Jul 28 13:34:09 2019 MANAGEMENT: >STATE:1564300149,ADD_ROUTES,,,,,,
Sun Jul 28 13:34:09 2019 C:Windowssystem32route.exe ADD 20.20.20.1 MASK 255.255.255.255
20.20.20.5
Sun Jul 28 13:34:09 2019 Route addition via service succeeded
Sun Jul 28 13:34:09 2019 Initialization Sequence Completed
Sun Jul 28 13:34:09 2019 MANAGEMENT:
>STATE:1564300149,CONNECTED,SUCCESS,20.20.20.6,192.168.132.21,1194,,](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-16-2048.jpg)
![Server logs while connecting to open-vpn server
Sun Jul 28 07:09:36 2019 192.168.132.1:58348 TLS: Initial packet from [AF_INET]192.168.132.1:58348,
sid=484d086a b6f6f99a
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 VERIFY OK: depth=1, CN=f1soft.com
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 VERIFY OK: depth=0, CN=f1soft
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_VER=2.4.7
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_PLAT=win
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_PROTO=2
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_NCP=2
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_LZ4=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_LZ4v2=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_LZO=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_COMP_STUB=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_COMP_STUBv2=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_TCPNL=1
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 peer info: IV_GUI_VER=OpenVPN_GUI_11
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-
AES256-GCM-SHA384, 2048 bit RSA
Sun Jul 28 07:09:42 2019 192.168.132.1:58348 [f1soft] Peer Connection Initiated with
[AF_INET]192.168.132.1:58348
Sun Jul 28 07:09:42 2019 f1soft/192.168.132.1:58348 MULTI_sva: pool returned IPv4=20.20.20.6, IPv6=(Not
enabled)
Sun Jul 28 07:09:42 2019 f1soft/192.168.132.1:58348 MULTI: Learn: 20.20.20.6 ->
f1soft/192.168.132.1:58348
Sun Jul 28 07:09:42 2019 f1soft/192.168.132.1:58348 MULTI: primary virtual IP for
f1soft/192.168.132.1:58348: 20.20.20.6
Sun Jul 28 07:09:43 2019 f1soft/192.168.132.1:58348 PUSH: Received control message: 'PUSH_REQUEST'
Sun Jul 28 07:09:43 2019 f1soft/192.168.132.1:58348 SENT CONTROL [f1soft]: 'PUSH_REPLY,redirect-
gateway def1,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route 20.20.20.1,topology net30,ping
20,ping-restart 60,ifconfig 20.20.20.6 20.20.20.5,peer-id 0,cipher AES-256-GCM' (status=1)
Sun Jul 28 07:09:43 2019 f1soft/192.168.132.1:58348 Data Channel: using negotiated cipher 'AES-256-GCM'
Sun Jul 28 07:09:43 2019 f1soft/192.168.132.1:58348 Outgoing Data Channel: Cipher 'AES-256-GCM'
initialized with 256 bit key
Sun Jul 28 07:09:43 2019 f1soft/192.168.132.1:58348 Incoming Data Channel: Cipher 'AES-256-GCM'
initialized with 256 bit key](https://image.slidesharecdn.com/openvpn-190729132424/75/Open-VPN-Server-17-2048.jpg)
