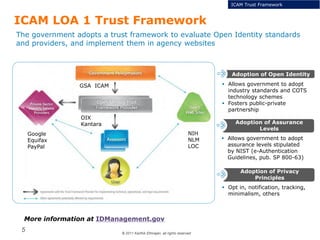
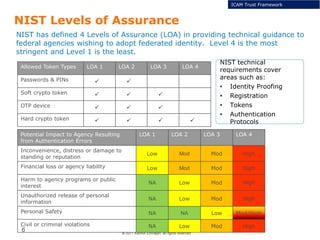
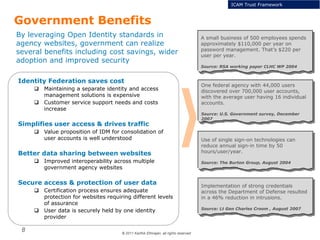
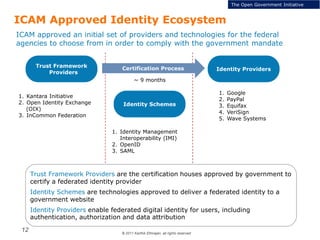
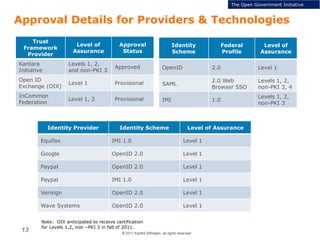
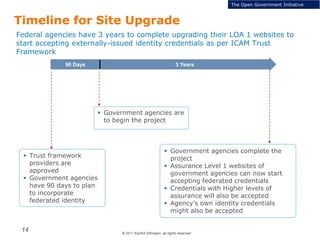
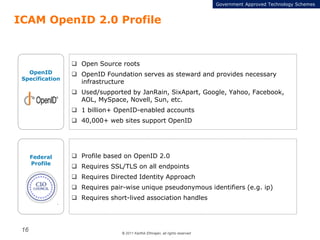
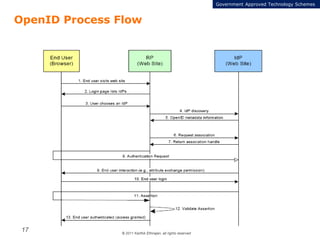
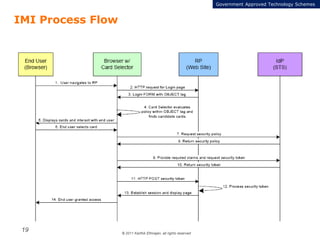
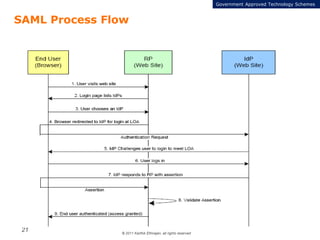
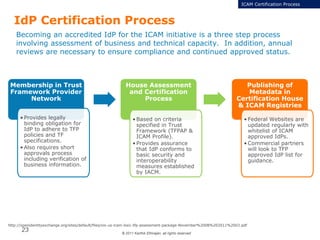
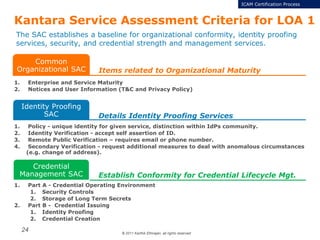
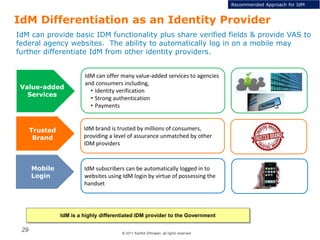
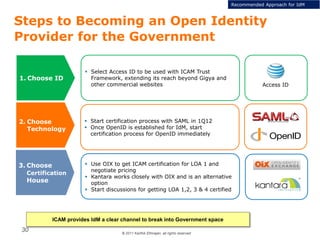
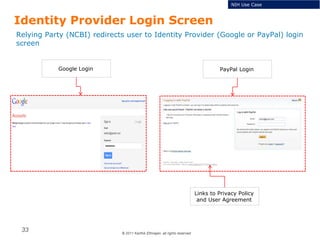
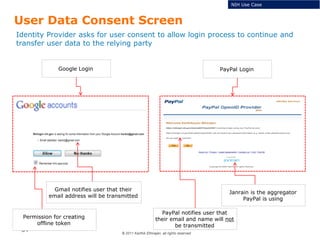
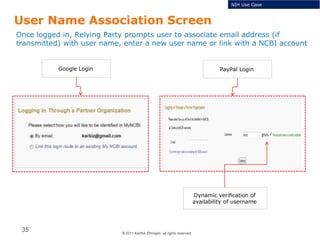
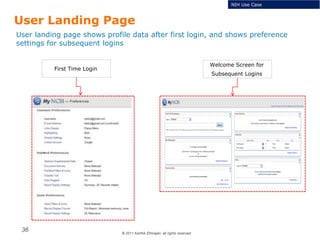
The document summarizes the ICAM certification process for identity providers seeking approval to participate in the U.S. government's Open Identity initiative. It outlines a three-step certification process involving membership with a trust framework provider, assessment and certification by a certification house, and publishing of metadata in approved registries. It provides details on assessment criteria from Kantara and the Open Identity Exchange that identity providers must meet regarding organizational maturity, identity proofing, and privacy. The goal is to assure identity providers conform to security, interoperability, and privacy measures established by ICAM for the Open Government initiative.