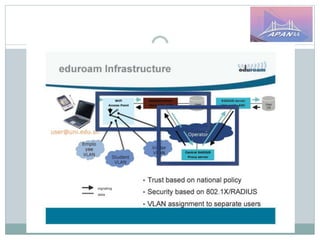
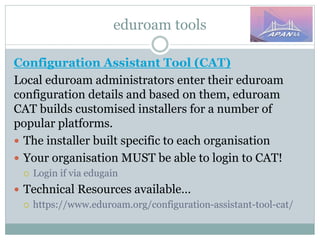
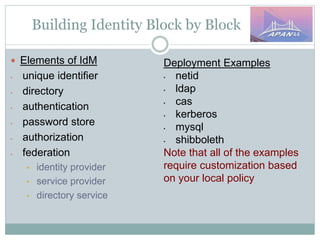
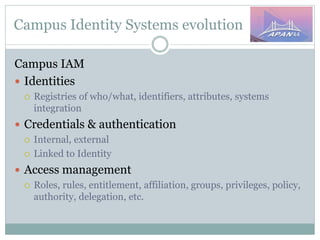
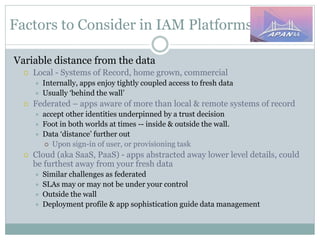
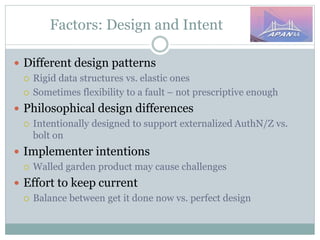
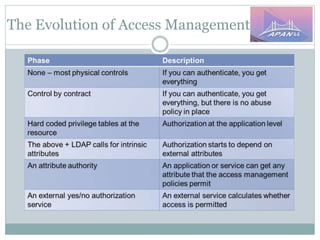
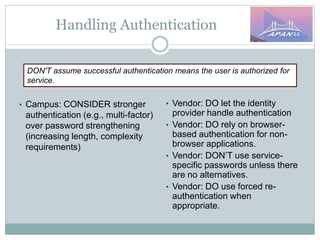
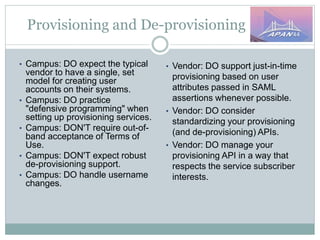
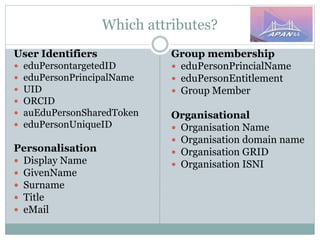
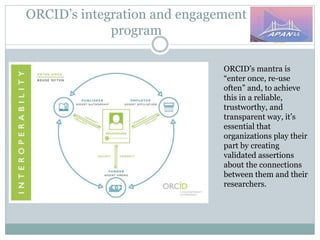
The document discusses identity and access management (IAM) on campus and its evolution to federated identity systems. It covers topics such as the role of campus identity in supporting single sign-on, the importance of defining users and attributes for federated systems, and the benefits of identity federations for service providers. Additionally, it highlights best practices for managing identity services and the collaborative opportunities available through existing federations.