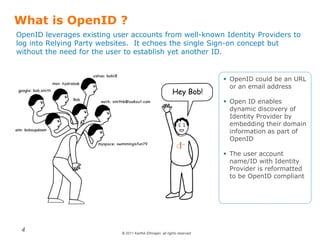
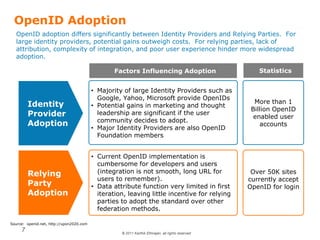
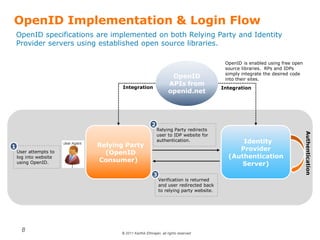
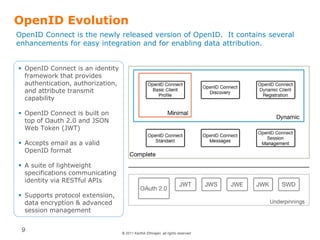
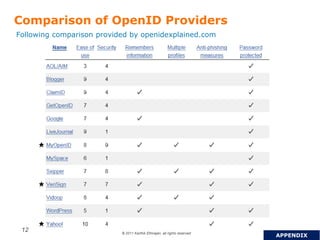
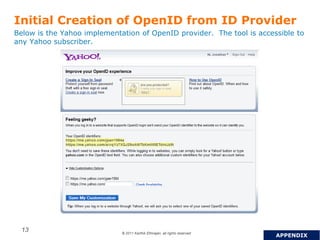
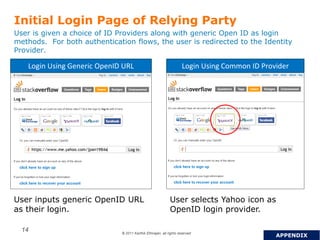
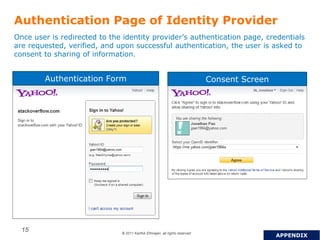
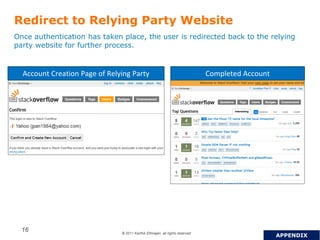
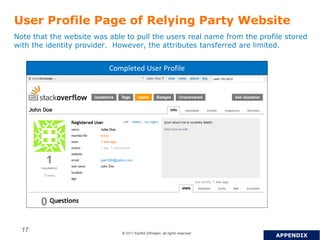
OpenID is a decentralized authentication protocol that allows users to log into third-party websites using their existing account credentials from major identity providers like Google, Yahoo, and Facebook. While many large identity providers support OpenID, adoption among relying parties has been limited due to complexity of integration and a poor user experience. The newer OpenID Connect standard aims to address these issues through enhancements like support for user attribute sharing and compatibility with OAuth 2.0 and JSON Web Tokens. The document recommends implementing OpenID Connect and consulting Gigya to help with integration.