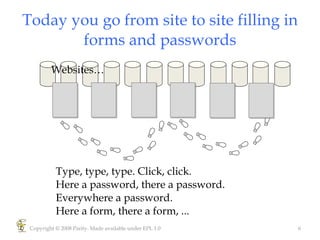
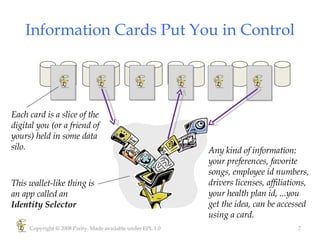
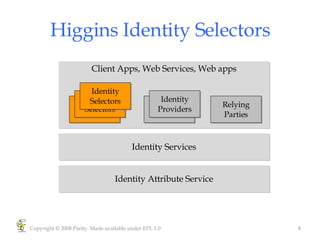
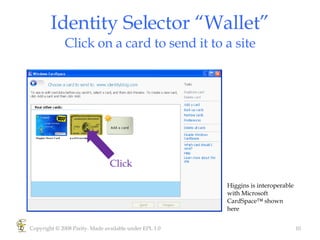
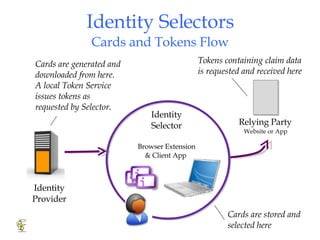
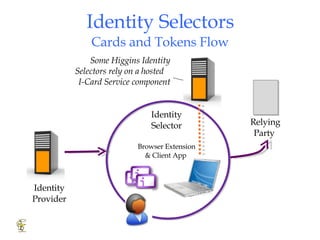
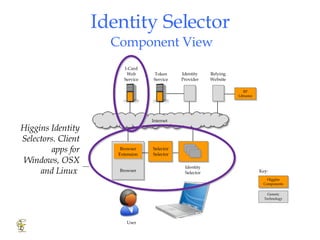
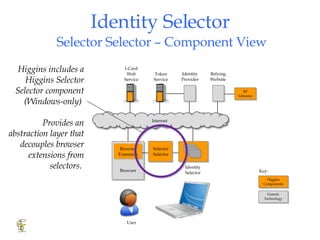
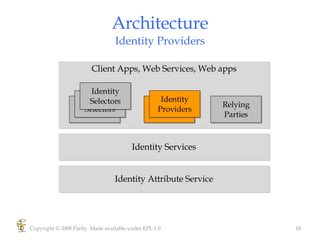
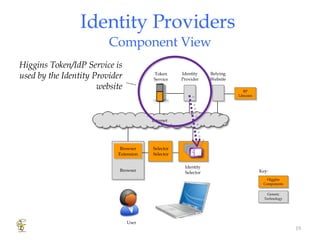
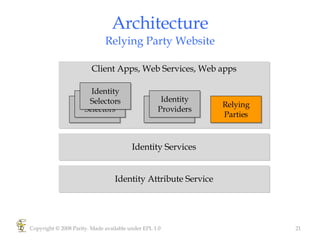
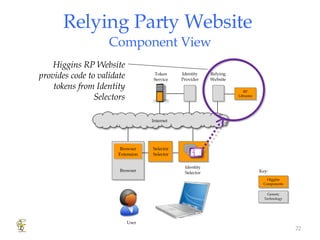
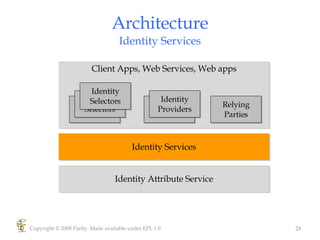
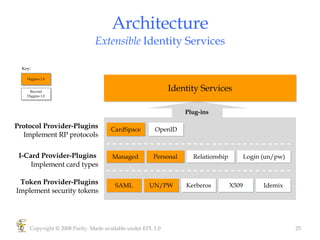
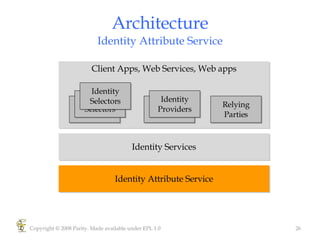
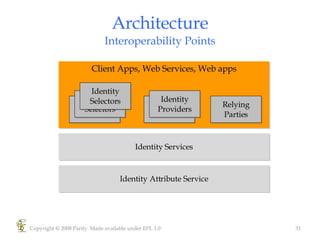
Higgins is an open source identity framework that provides a consistent user experience for managing identity data across multiple sources through the use of "information cards". It allows users to control their personal information distributed across different systems from a single point. The framework includes plug-ins to integrate various identity sources and provides APIs for applications to access identity attributes. Future versions aim to support additional card types, social relationships and improve access control and interoperability with other standards.





![How to Use I-Cards By clicking on a card you can log into sites. No more passwords You can share cards with friends and businesses you trust Some [relationship] cards create permanent connections to your friends, communities and businesses](https://image.slidesharecdn.com/higginsoverview2008-1226948670782159-8/85/Higgins-9-320.jpg)


















![Other New Card Types Username/Password Card To log in to traditional un/pw sites SAML Card (aka S-card) [maybe] Uses SAML protocol to retrieve token Idemix card (aka Z-card) [maybe] Support for a new privacy-enhancing token type based on zero-knowledge proofs Improved support for selective disclosure Copyright © 2008 Parity. Made available under EPL 1.0](https://image.slidesharecdn.com/higginsoverview2008-1226948670782159-8/85/Higgins-43-320.jpg)



![Project Co-leads http://higgins-project.org Paul Trevithick Mary Ruddy [email_address] [email_address] +1.617.513.7924 +1.617.290.8591 Copyright © 2008 Parity. Made available under EPL 1.0](https://image.slidesharecdn.com/higginsoverview2008-1226948670782159-8/85/Higgins-49-320.jpg)





