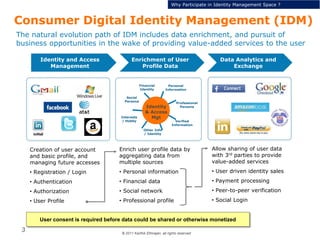
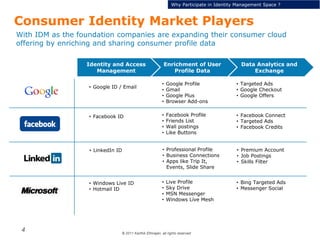
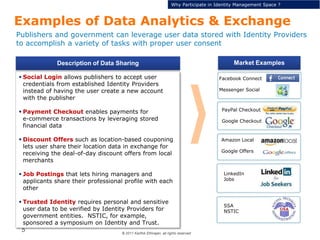
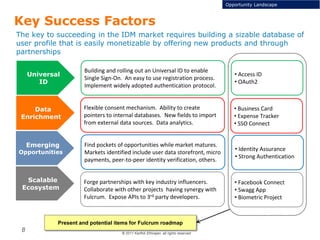
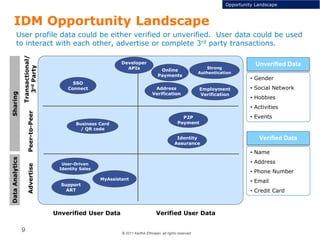
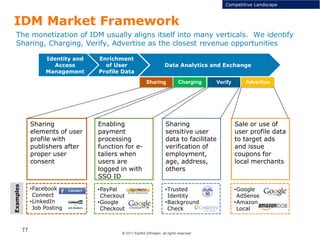
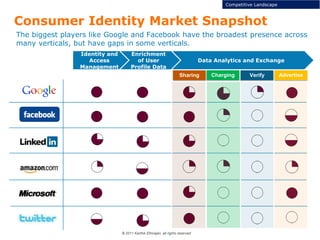
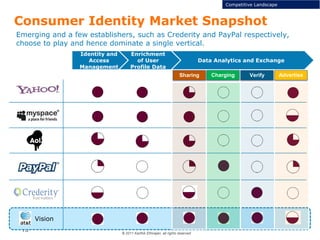
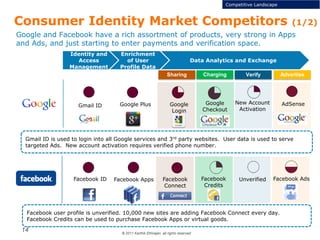
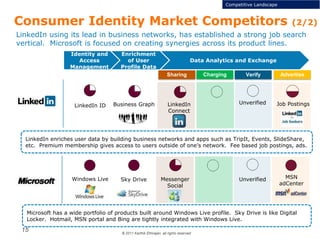
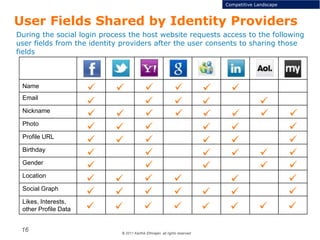
This document discusses single sign-on identity management (IDM) and its value. It begins by outlining the typical components of IDM - identity and access management, enrichment of user profile data, and data analytics and exchange. It then discusses why companies participate in the IDM space and how they expand their cloud offerings using IDM. Examples of Google and Facebook's IDM strategies are provided. The document also covers the opportunity landscape, competitive landscape categorized by sharing, charging, verifying and advertising user data, and profiles some of the major IDM players including Google, Facebook, LinkedIn and Microsoft.