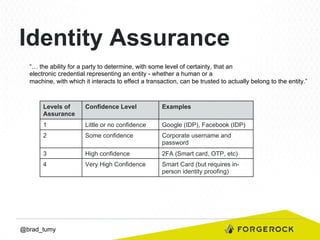
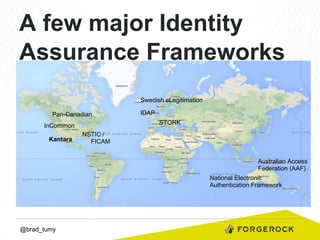
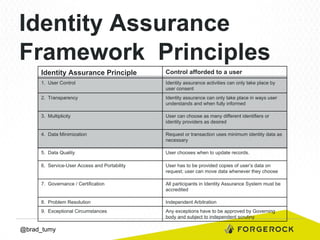
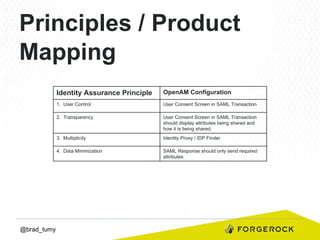
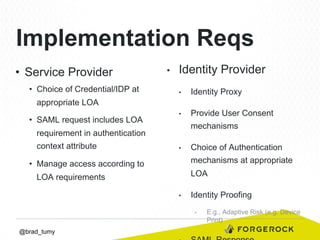
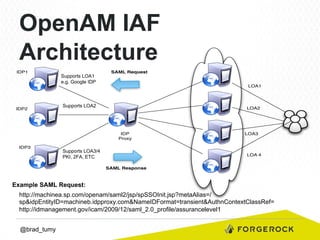
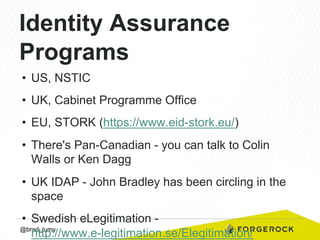
Brad Tumy gave a presentation on identity assurance at the 2013 Open Stack Identity Summit in France. The presentation covered topics such as levels of identity assurance, common identity assurance frameworks, implementation requirements, and a typical identity assurance architecture model. It discussed using identity assurance to determine the level of certainty that an electronic credential represents the actual entity it claims to.