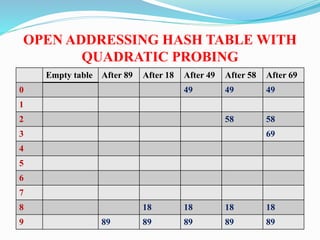
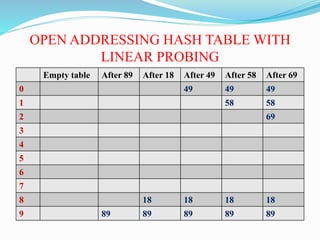
The document discusses different techniques for handling collisions in hash tables, including separate chaining and open addressing. Separate chaining uses linked lists to chain together elements that hash to the same slot, while open addressing resolves collisions by probing to alternate slots using functions like linear probing, quadratic probing, and double hashing. Pseudocode is provided for initializing and inserting elements into a hash table using separate chaining with linked lists.






![Insert routine for separate chaining Hash table
Void
Insert(ElementType key,HashTable H)
{
Position pos,Newcell;
List L;
/*1*/ Pos=Find(key, H);
/*2*/if (pos==NULL)/*Key is not found*/
/*3*/Newcell=malloc(sizeof(struct ListNode));
/*4*/if(Newcell==NULL)
/*5*/ Fatalerror(“Out of space”);
else
{
/*6*/ L=H->The Lists[Hash(Key,H->TableSize)];
/*7*/Newcell->Next=L->Next;
/*8*/Newcell->Element=key; /*Probably need strcpy!*/
/*9*/L->Next =NewCell;
}
}
}](https://image.slidesharecdn.com/openaddressiingrehashingextendiblevhashing-181003130854/85/Open-addressing-amp-rehashing-extendable-hashing-7-320.jpg)
![Initialization routine for separate
chaining hash table
HashTable
InitializeTable(int Tablesize)
{
HashTable H;
int I;
/*1*/ if (TableSize<MinTableSize)
{
/*2*/ Error (“table size too small”);
/*3*/ return NULL;
}
/*Allocate table*/
/*4*/H=malloc(sizeof(struct HashTbl));
/*5*/if(H==NULL)
/*6*/FatalError(“Out of space!!!”);
/*7*/H->Tablesize = Nextprime(TableSize)
/*Allocate arraay of list*/
/*8*/H->The lists =malloc (sizeof(List)*H-
>TableSize);
/*9*/if (H->TheLists==NULL)
/*10*/ FatalError(“Out of space!!!”);
/*Allocate list header*/
/*11*/ for (i=0;i<H->TableSize;i++)
{
/*12*/H->The Lists [i]=malloc(Sizeof(struct
ListNode));
/*13*/if (H->The lists[i]==NULL)
/*14*/FatalError(“Out of space!!!”);
else
/*15*/ H->The lists[i]->Next=NULL;
}
/*16*/ return H;
}](https://image.slidesharecdn.com/openaddressiingrehashingextendiblevhashing-181003130854/85/Open-addressing-amp-rehashing-extendable-hashing-8-320.jpg)






![Quadratic Probing:
Success guarantee for < ½
• show for all 0 i,j size/2 and i j
(h(x) + i2) mod size (h(x) + j2) mod size
• by contradiction: suppose that for some i j:
(h(x) + i2) mod size = (h(x) + j2) mod size
i2 mod size = j2 mod size
(i2 - j2) mod size = 0
[(i + j)(i - j)] mod size = 0
Because size is prime(i-j)or (i+j) must be zero, and
neither can be](https://image.slidesharecdn.com/openaddressiingrehashingextendiblevhashing-181003130854/85/Open-addressing-amp-rehashing-extendable-hashing-16-320.jpg)