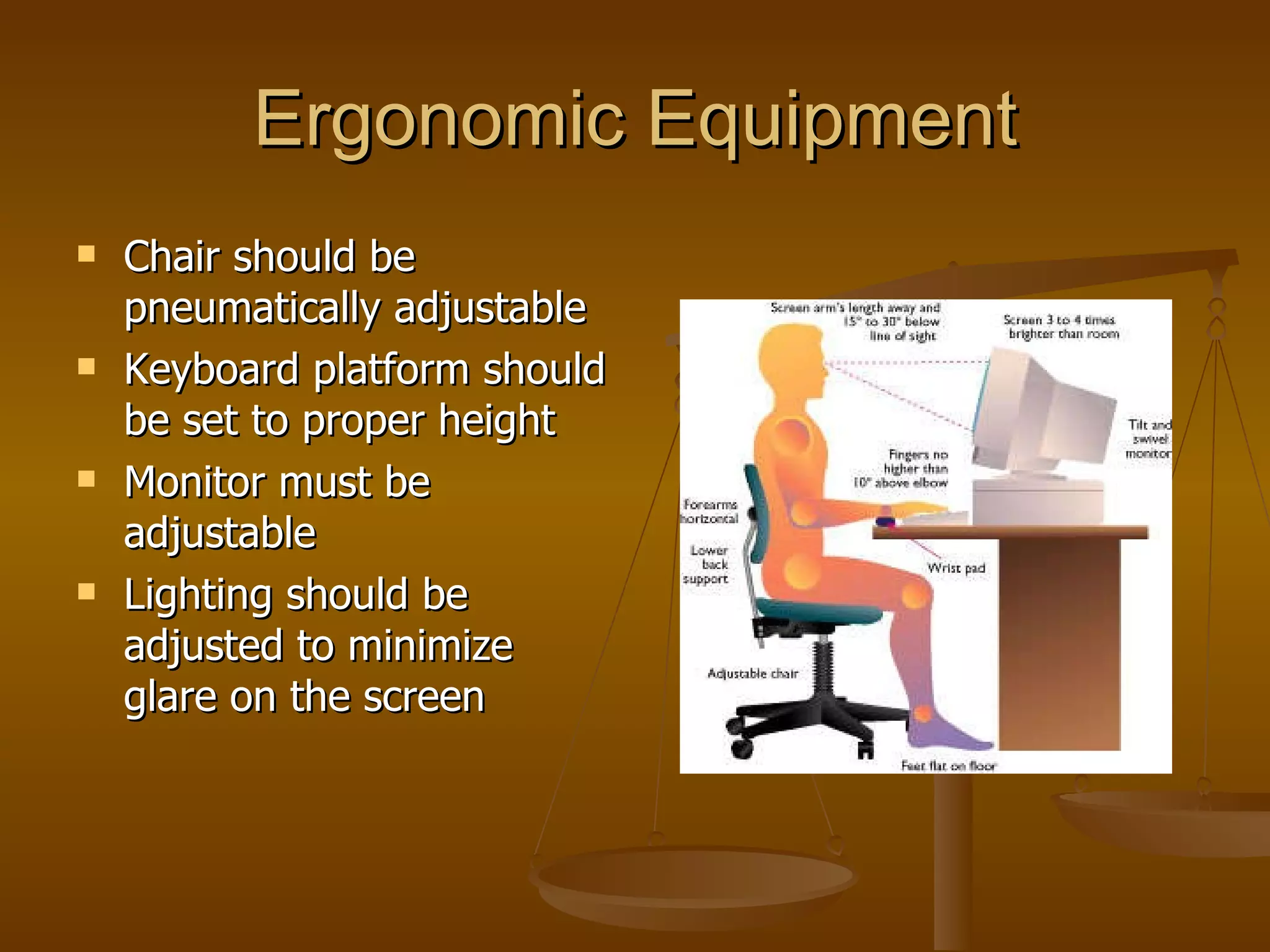
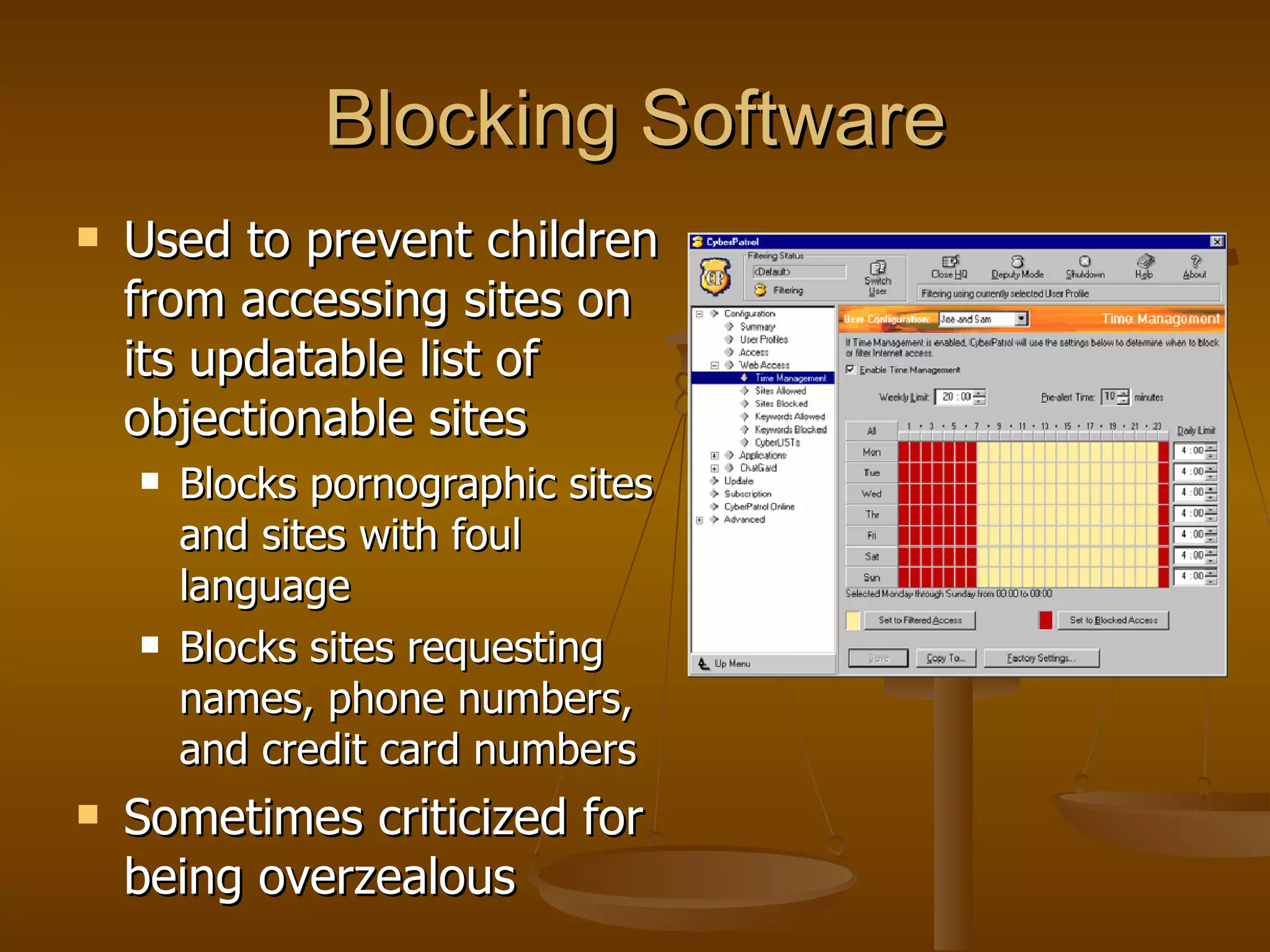
The document discusses several social and ethical issues related to computing. It describes the digital divide between those with and without access to computers and the internet. It also outlines some workplace issues like employee monitoring and ergonomics. The document examines legal issues around different jurisdictions and laws to protect children online. Finally, it discusses the importance of ethics in computing and intellectual property rights.