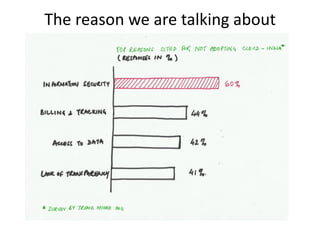
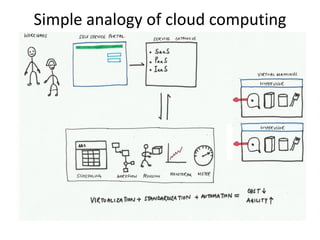
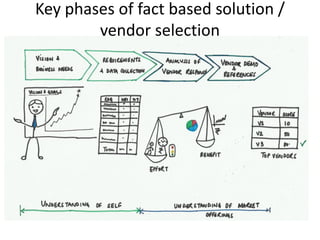
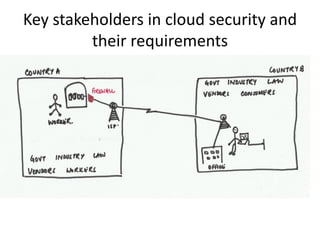
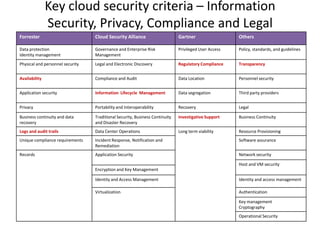
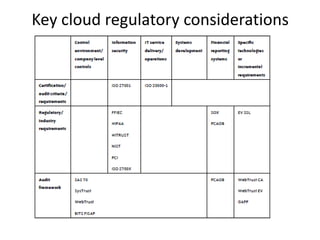
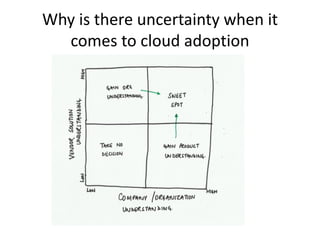
This document discusses key security considerations when selecting a cloud computing vendor. It outlines several criteria to evaluate including personnel security, legal issues, oversight of third party providers, and network security. Sample questions are provided for each criteria to assess the vendor's security practices, policies, and controls. The document advises going through the vendor selection process step-by-step while carefully evaluating each of the outlined security criteria.