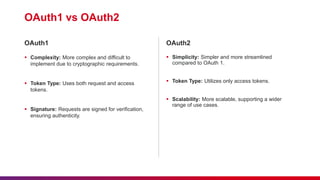
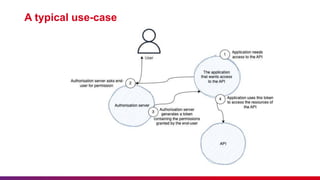
The document outlines the implementation of OAuth 2.0 and its significance in securing API access through a framework allowing third-party applications to access resources with user permission. It covers key concepts such as authorization roles, grant types, the authorization process, and differences between OAuth 1.0 and 2.0. Additionally, it emphasizes the importance of etiquette during sessions and provides guidance on submitting feedback and minimizing disturbances.