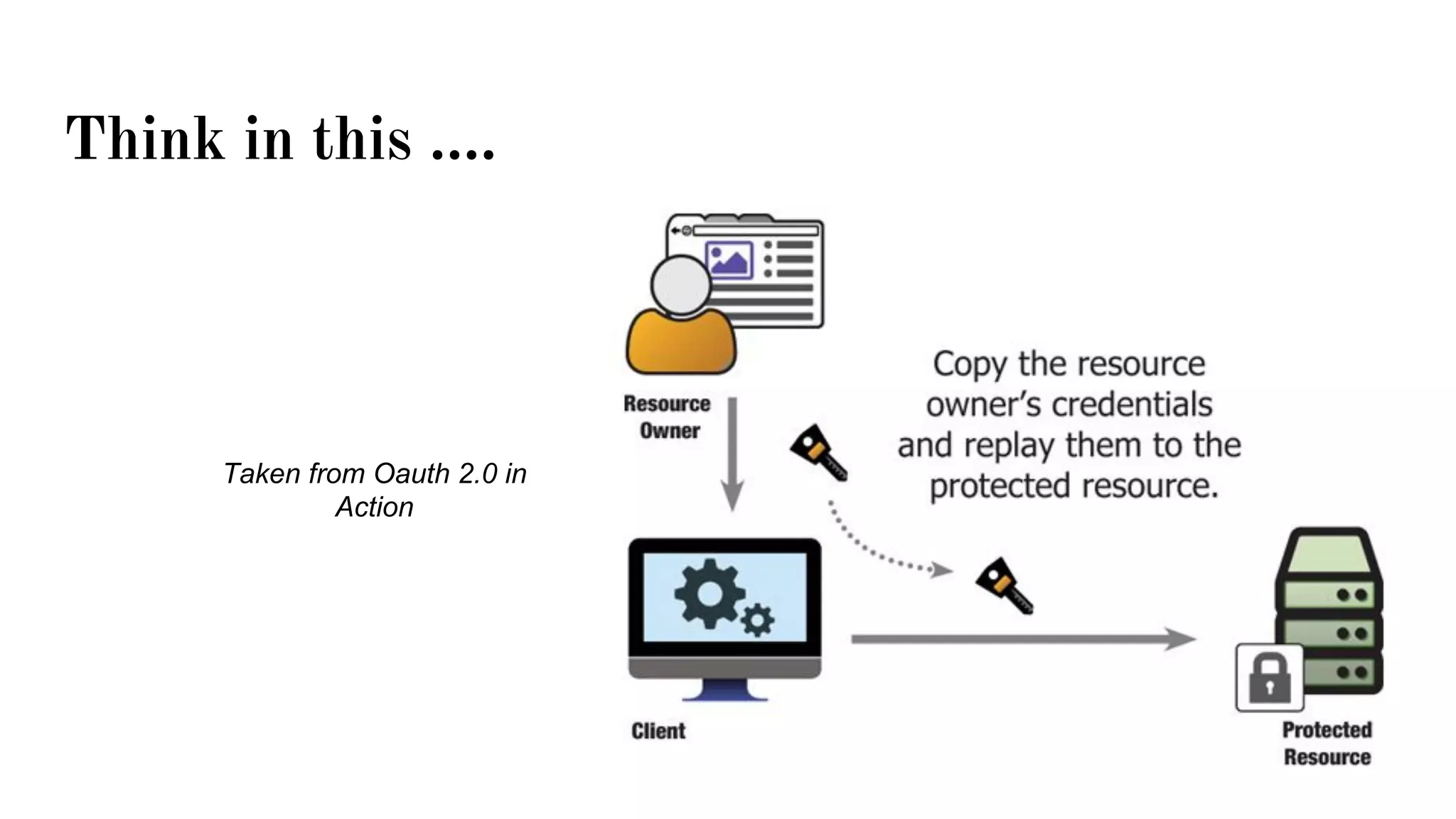
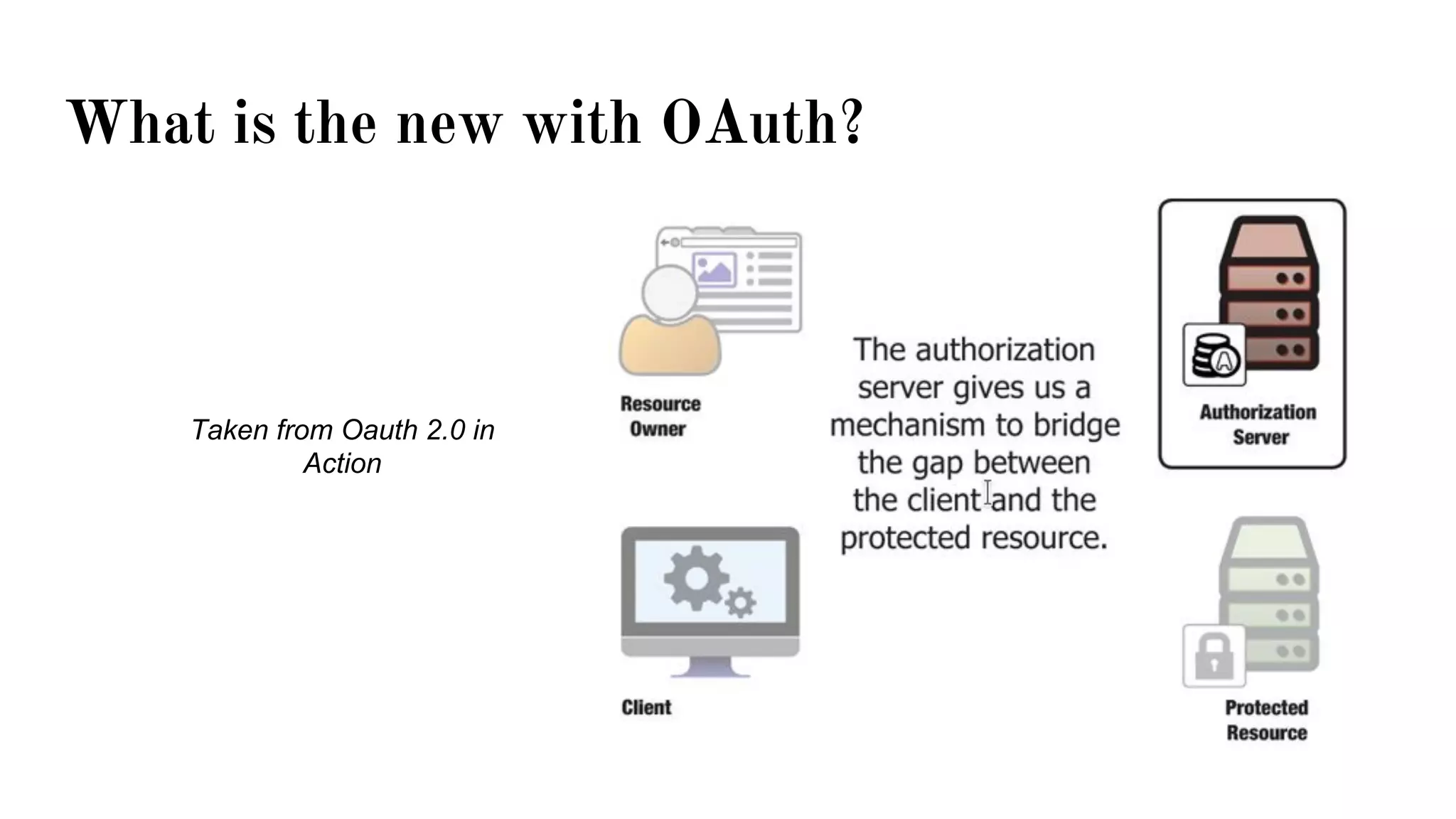
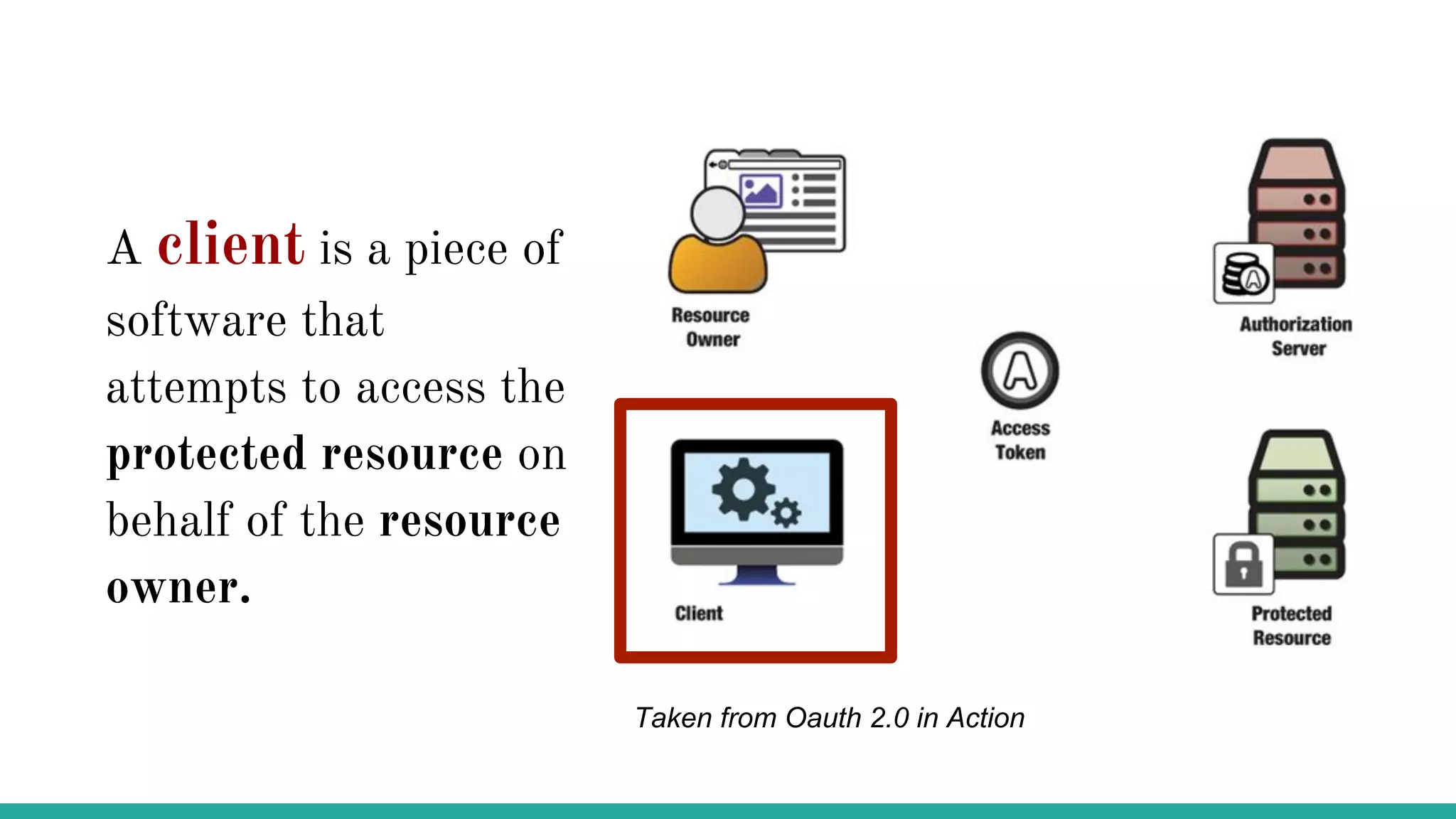
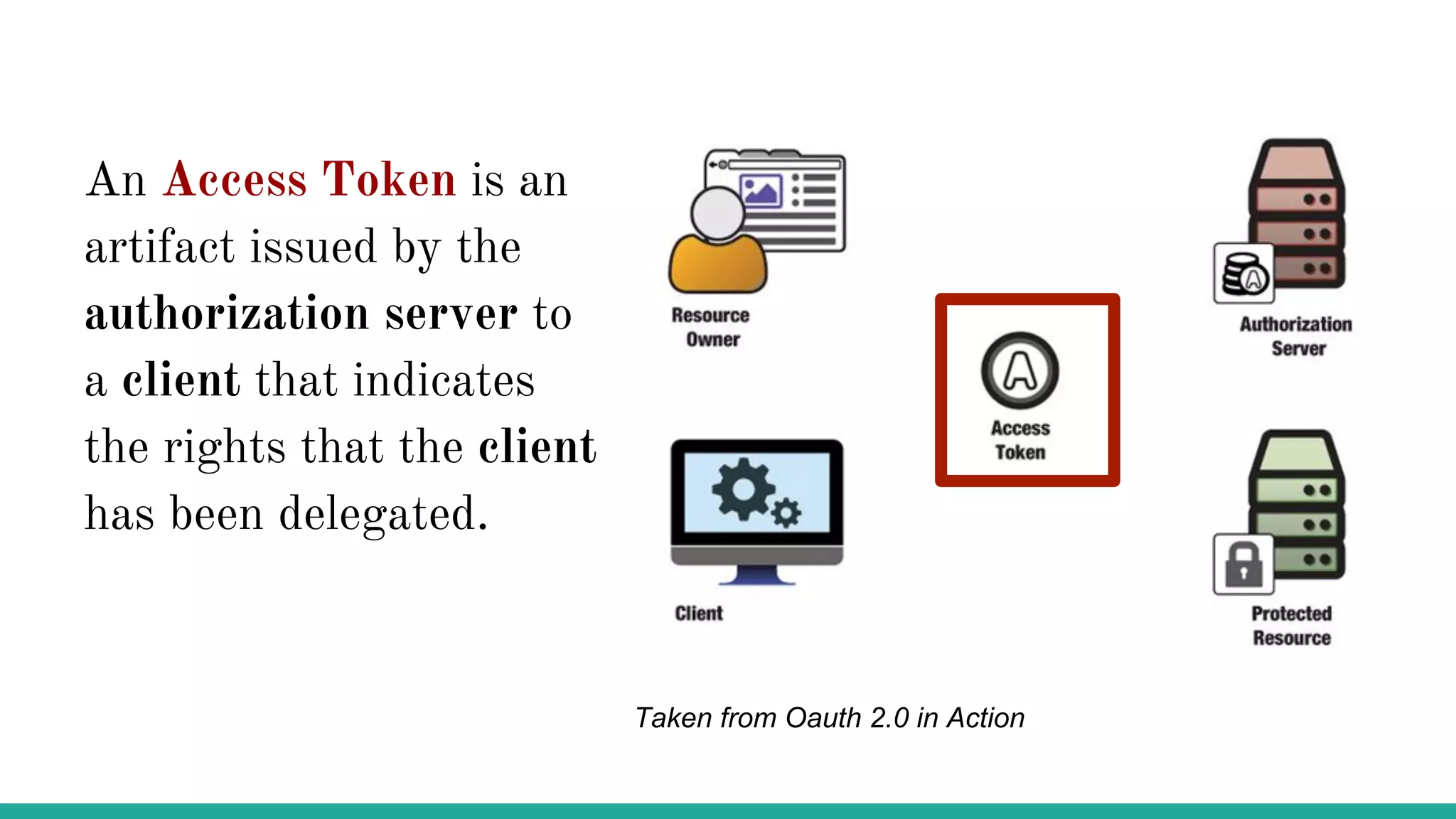
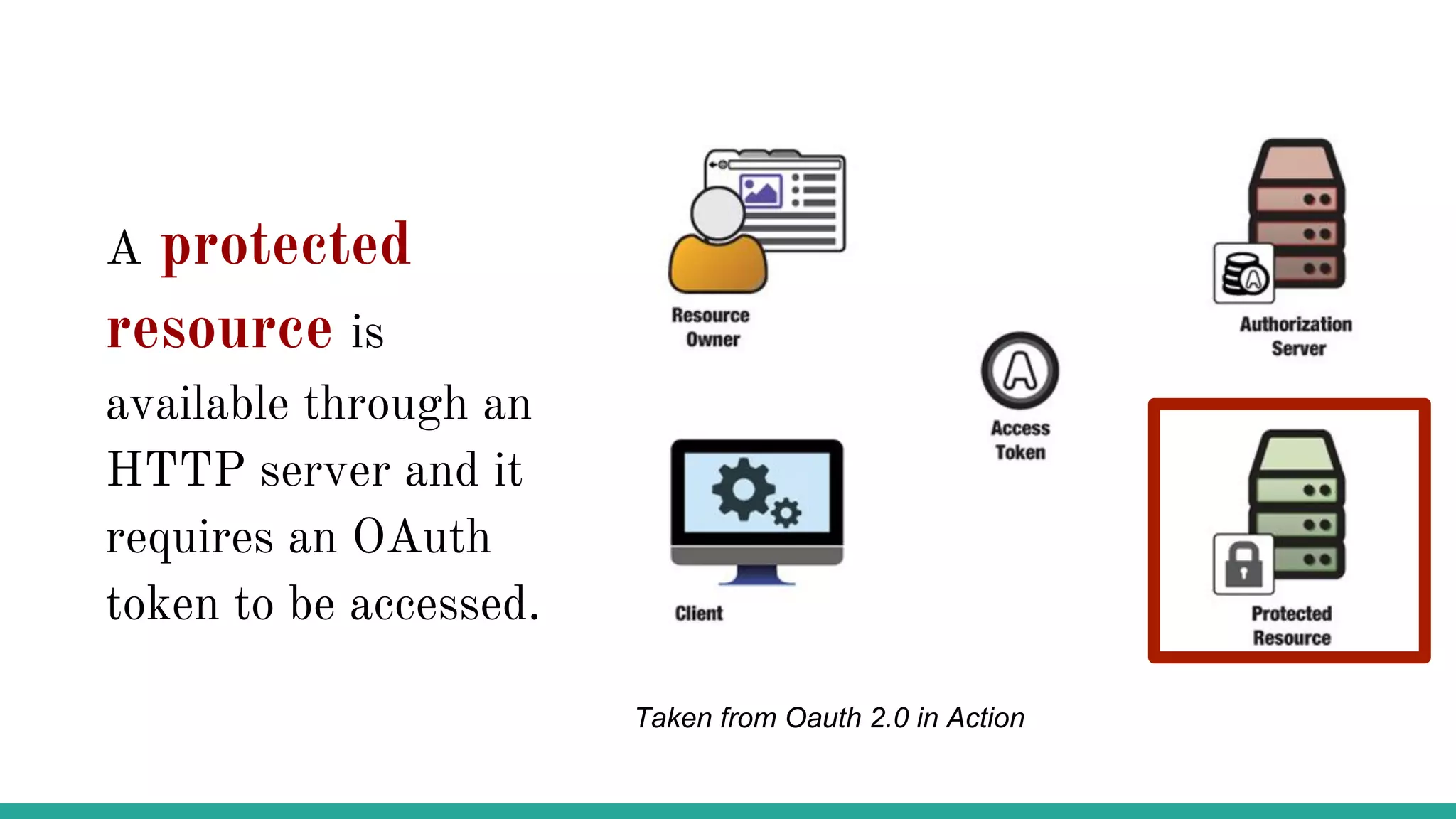
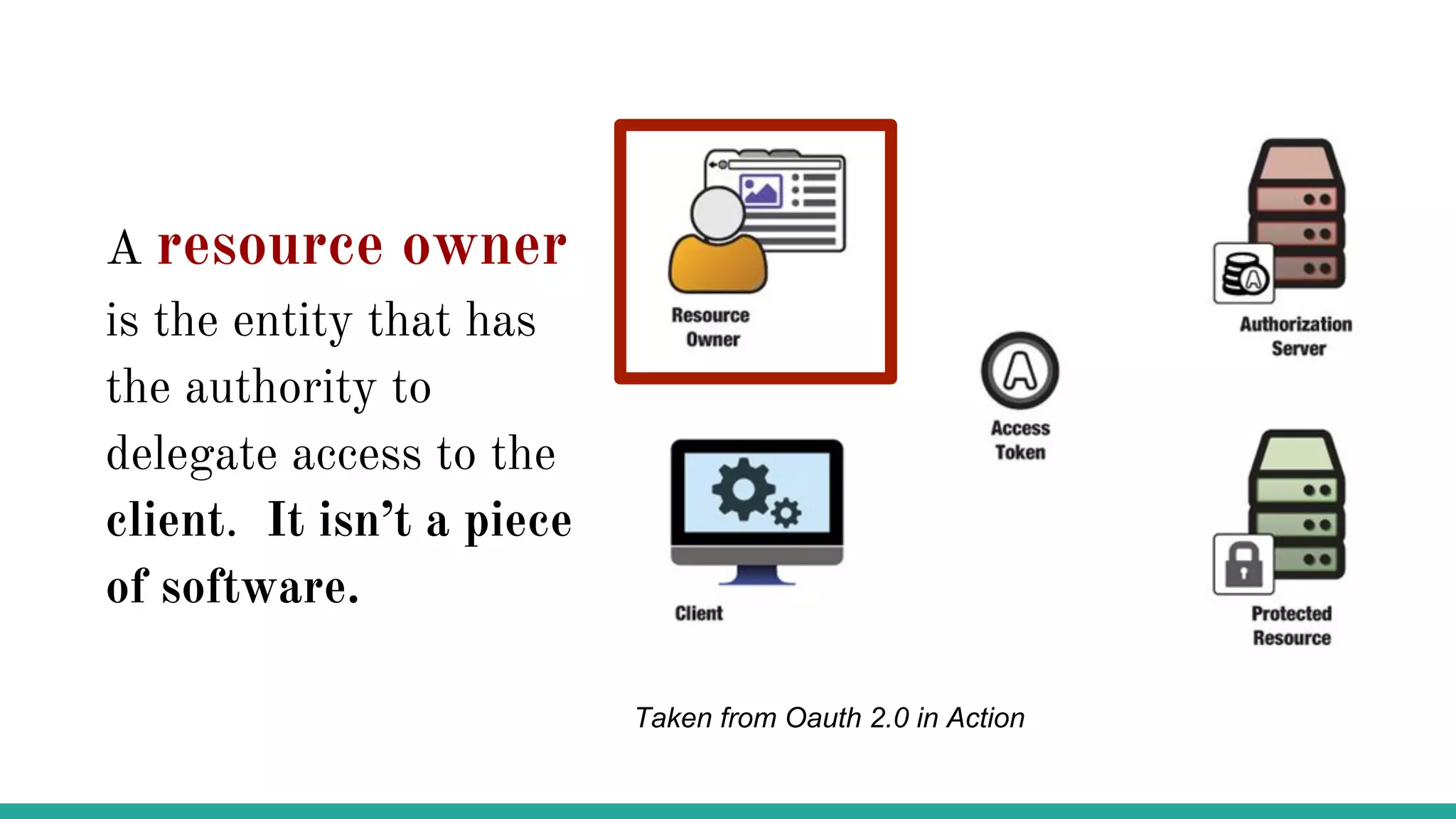
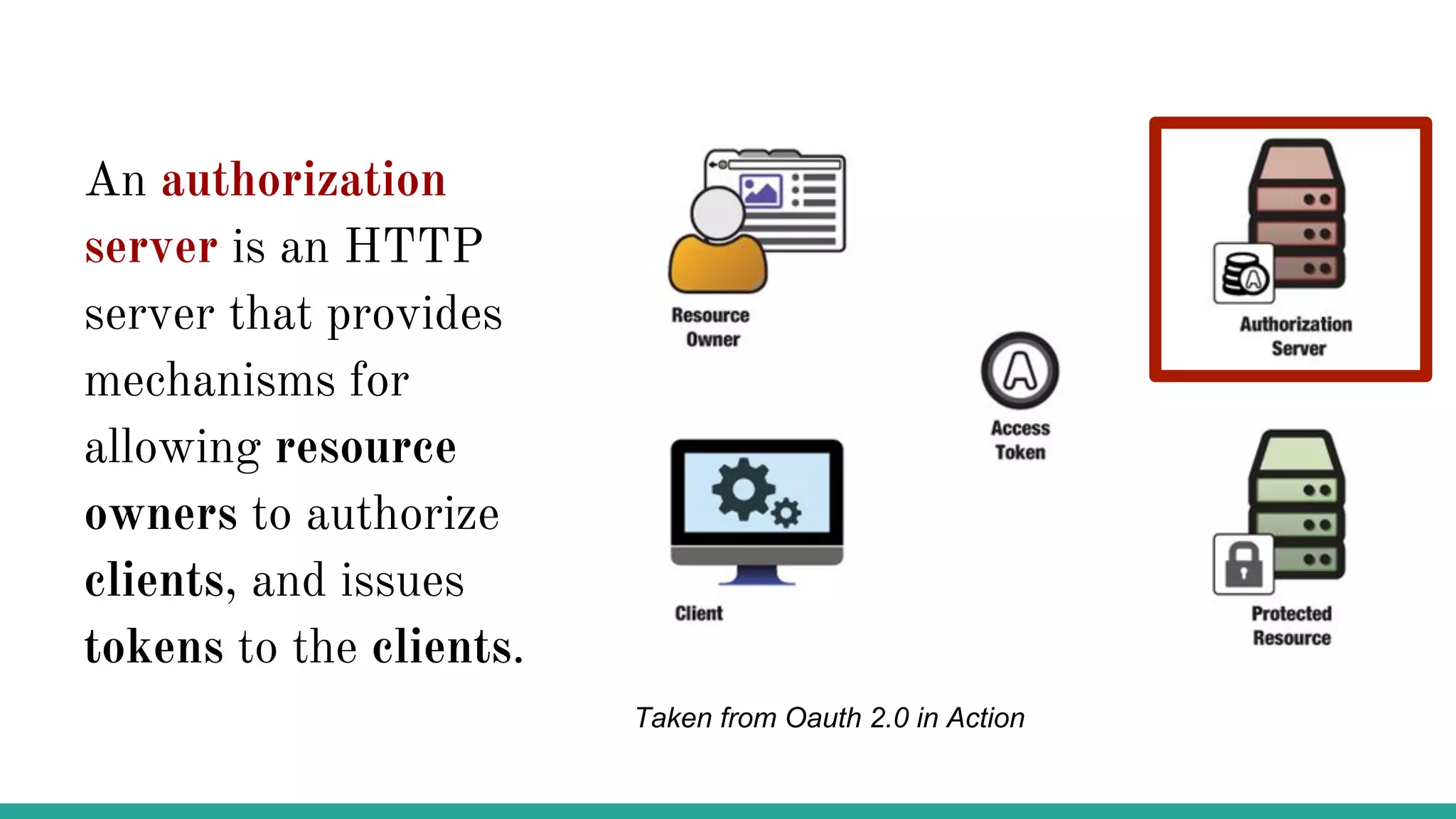
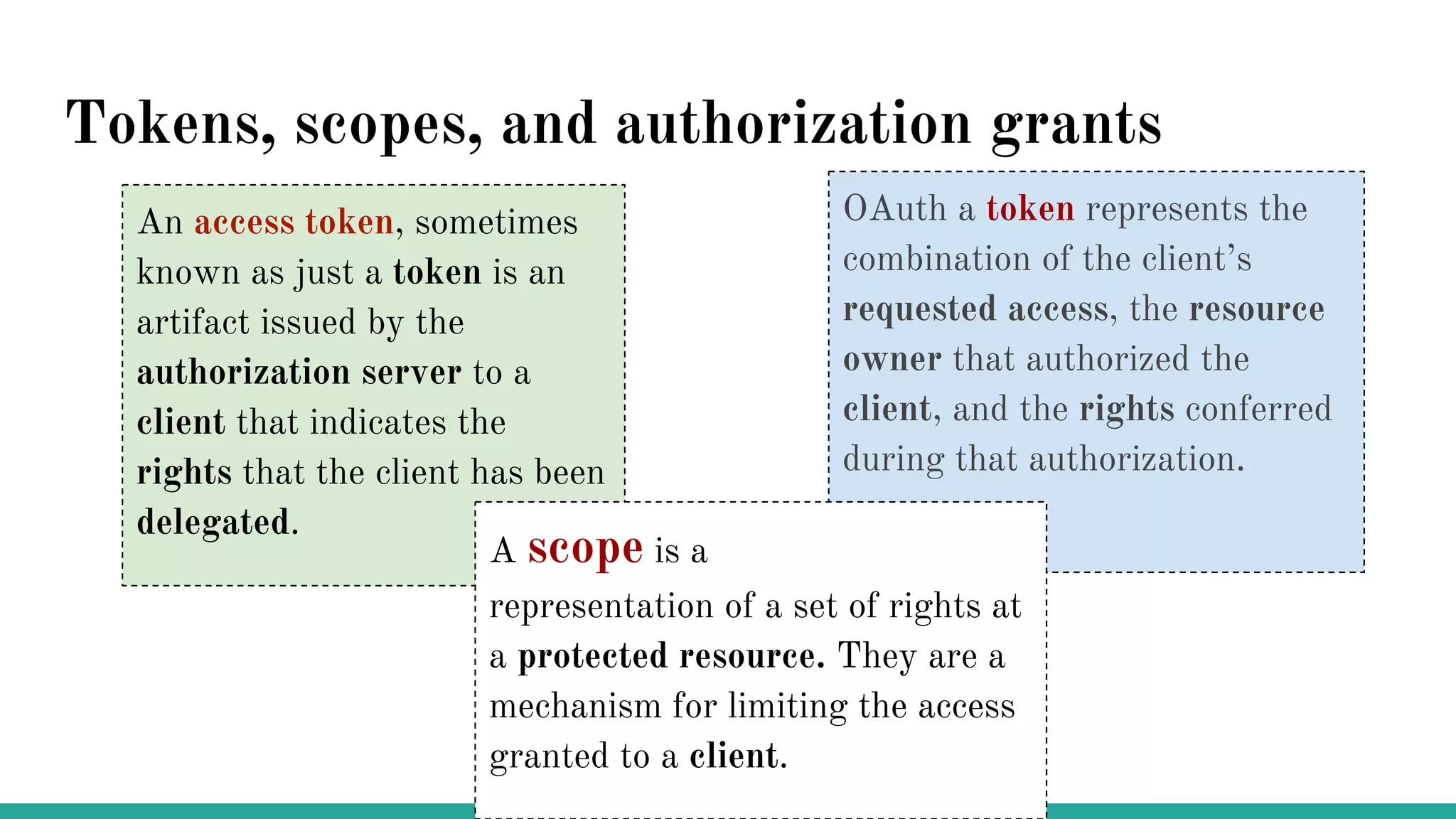
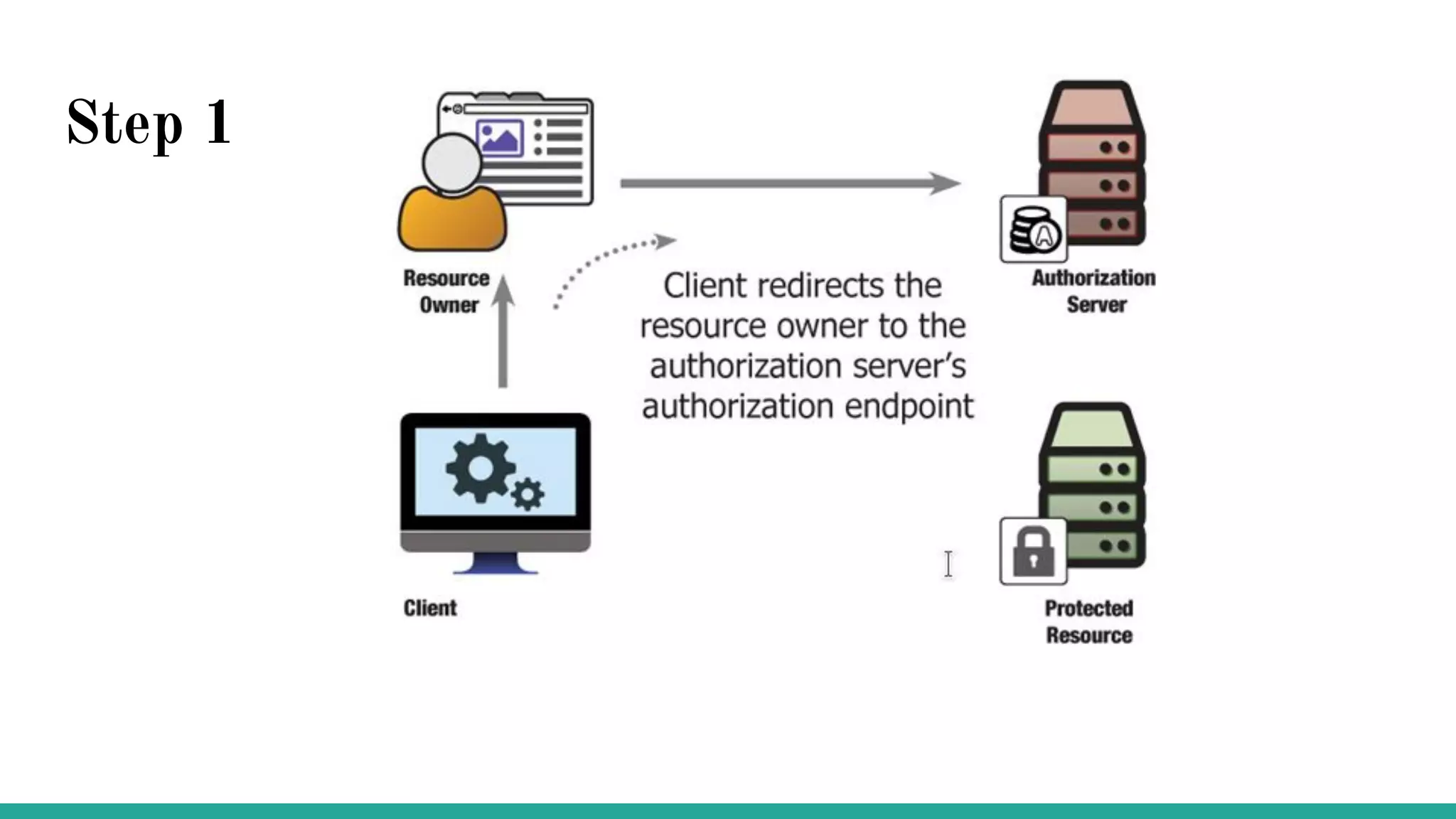
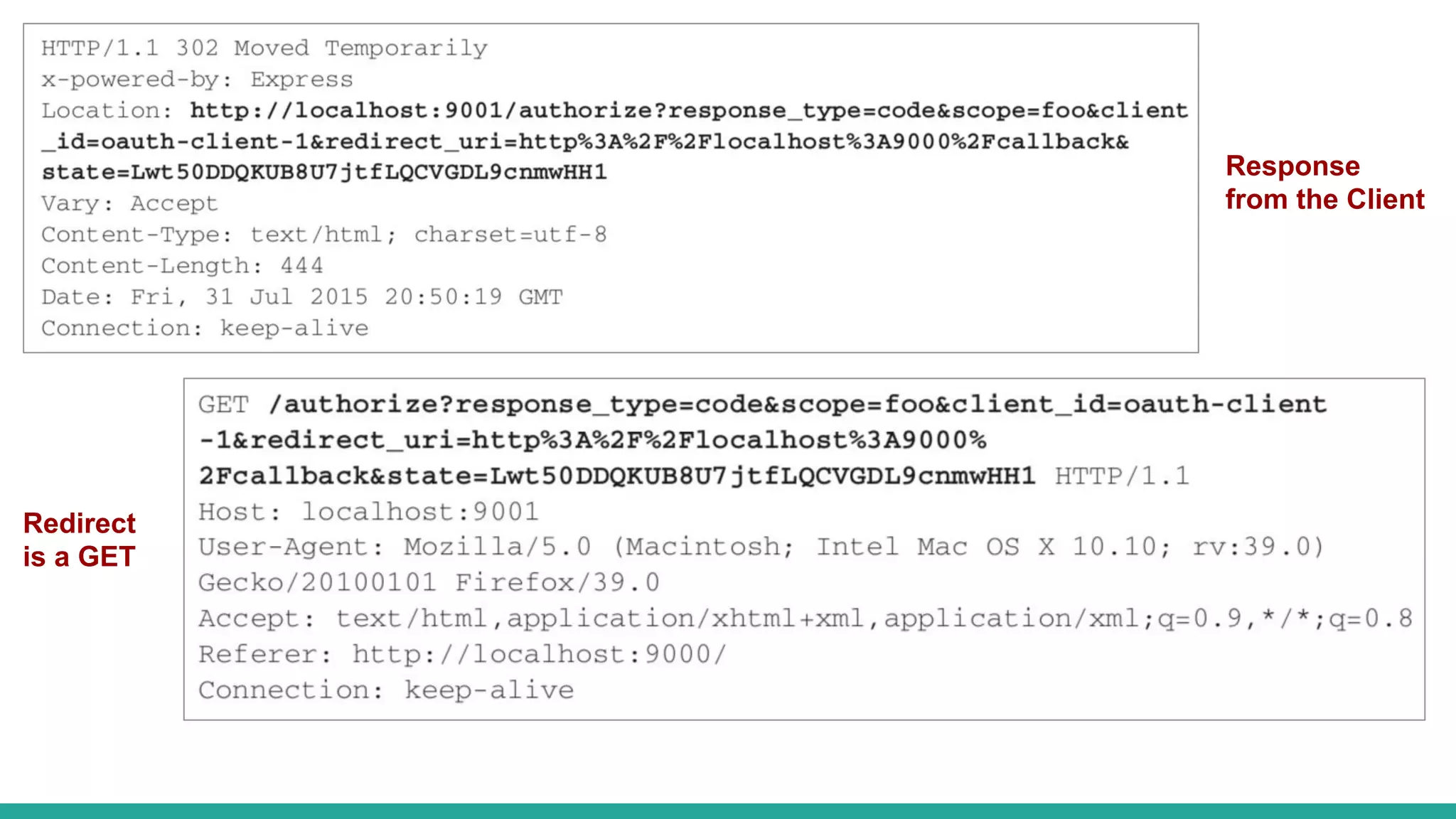
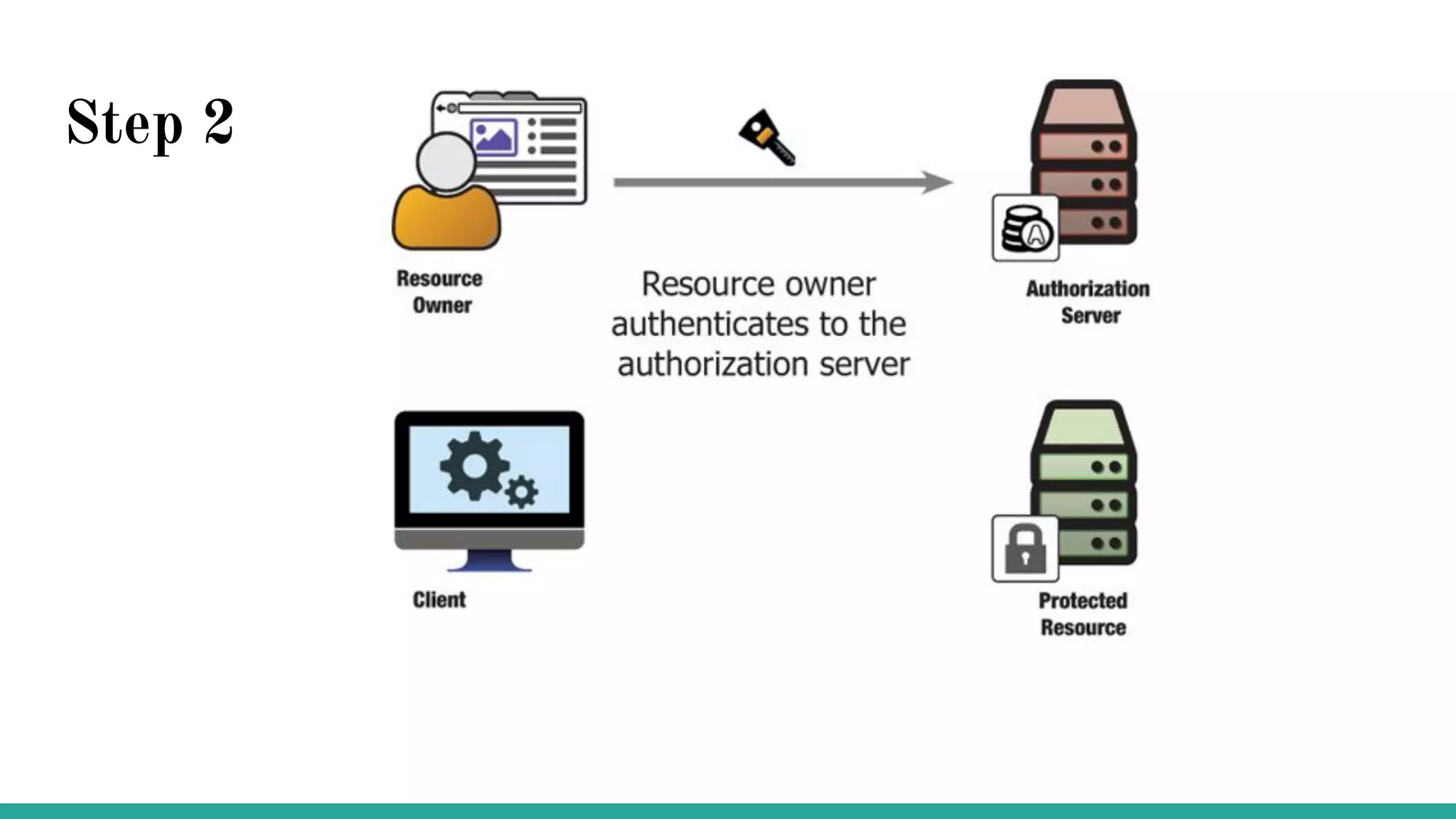
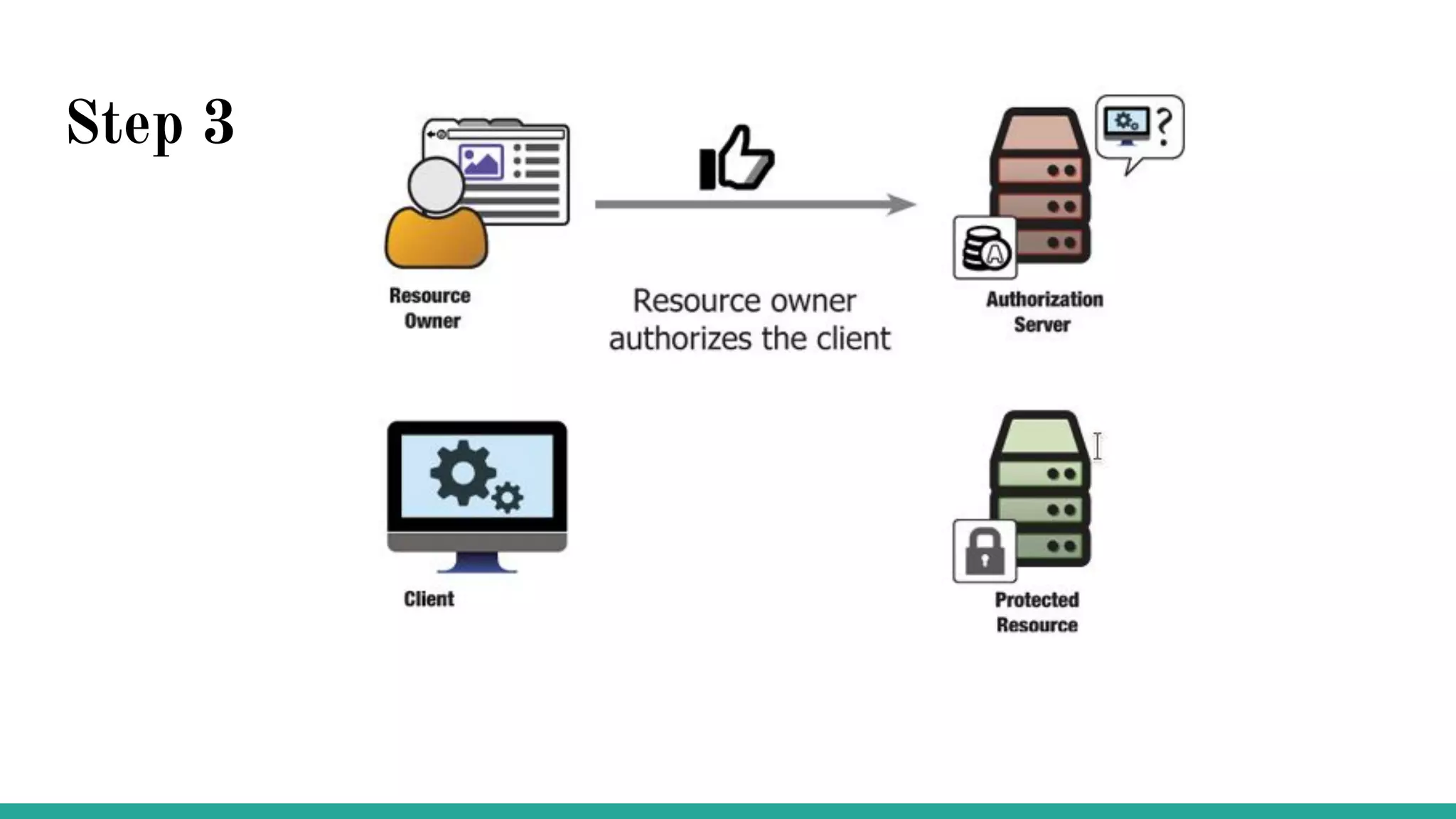
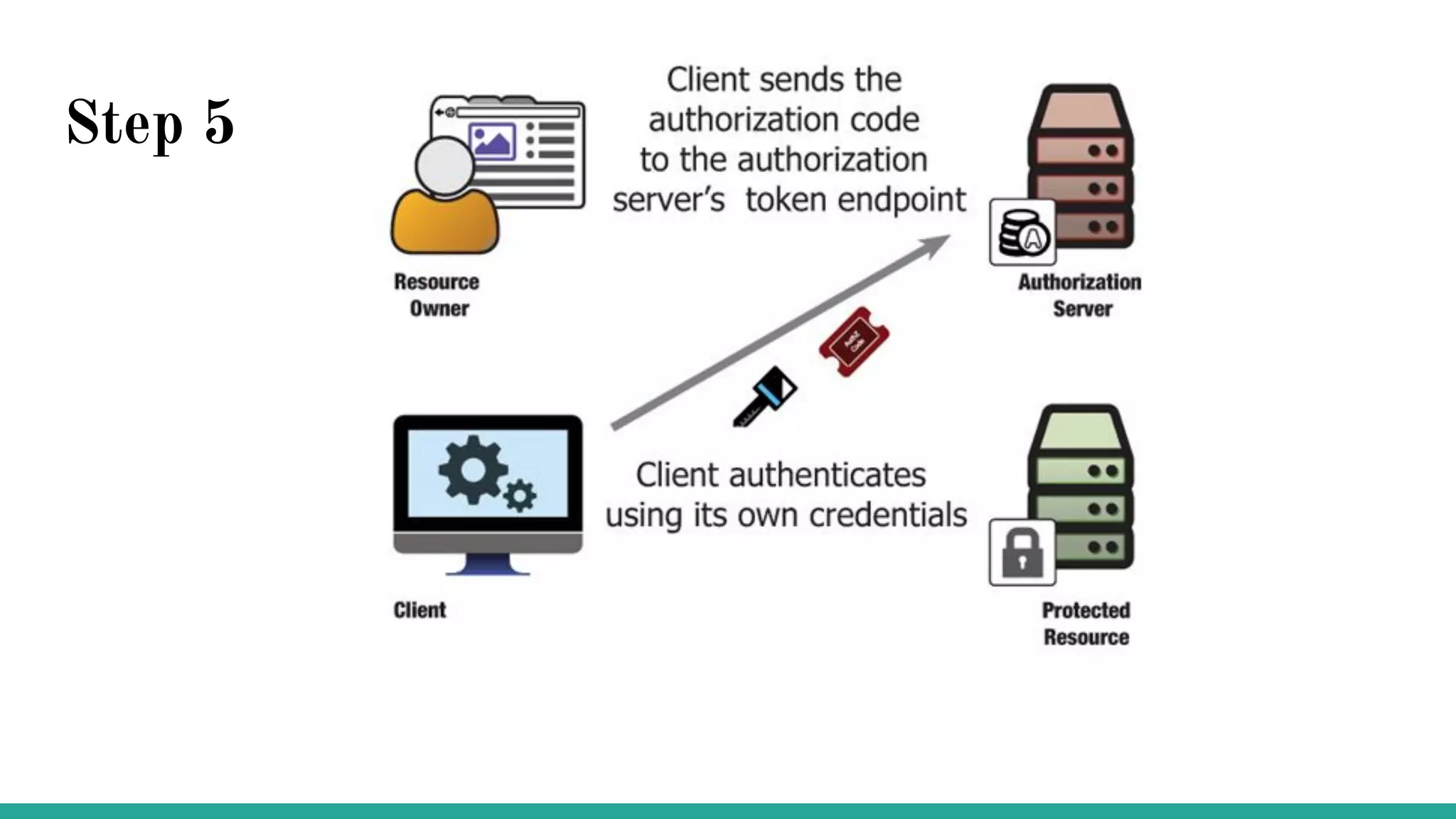
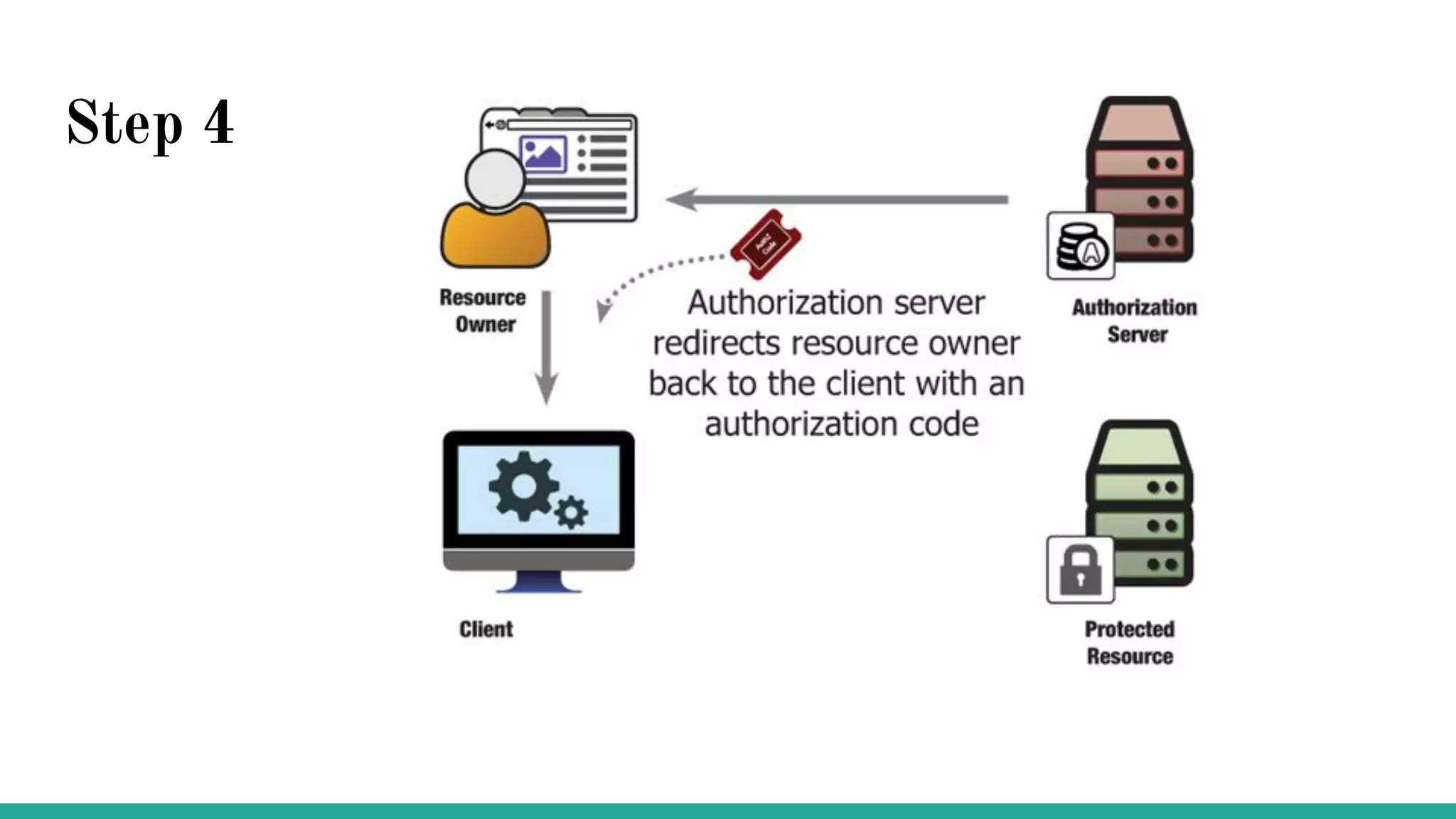
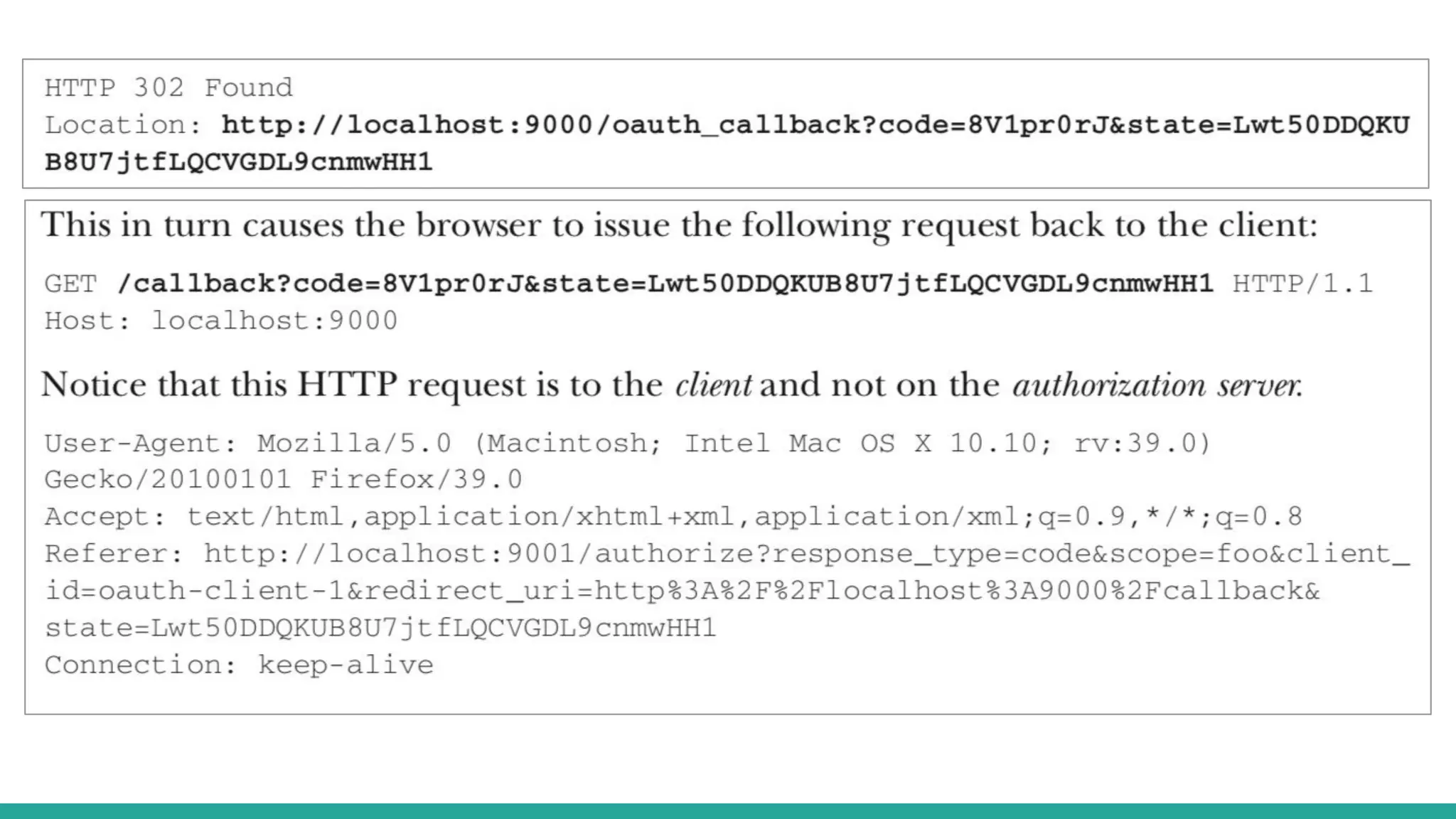
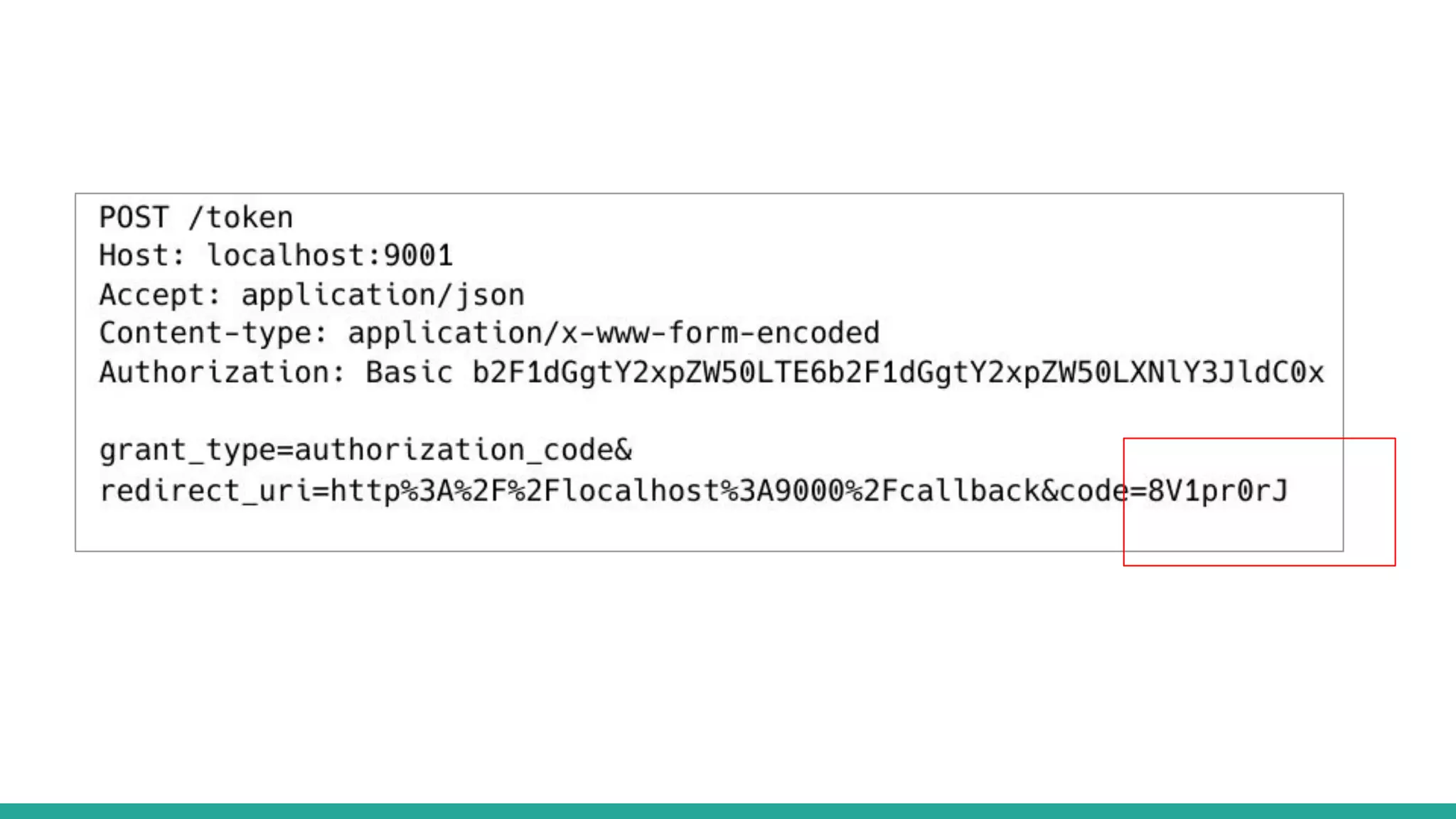
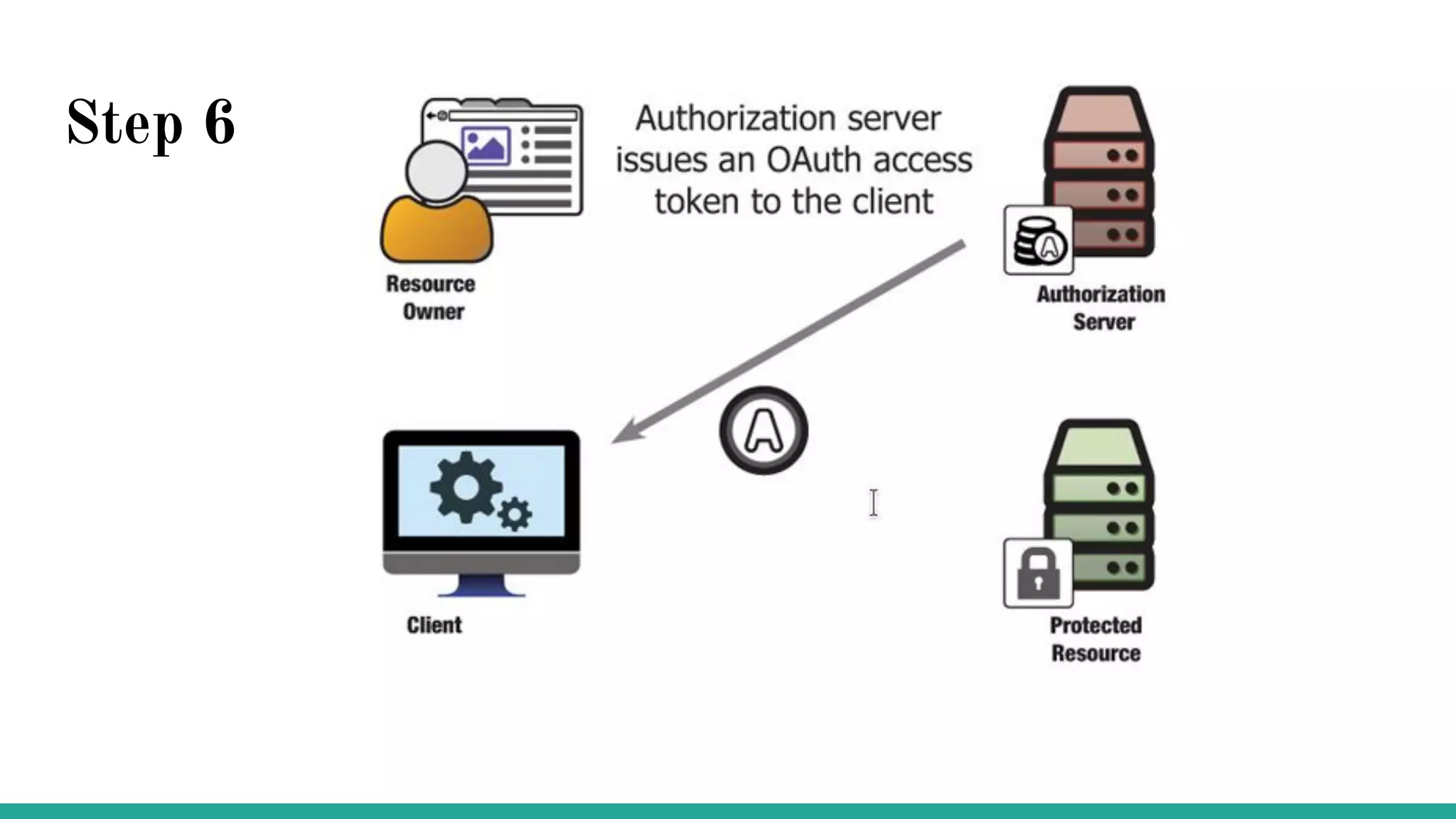
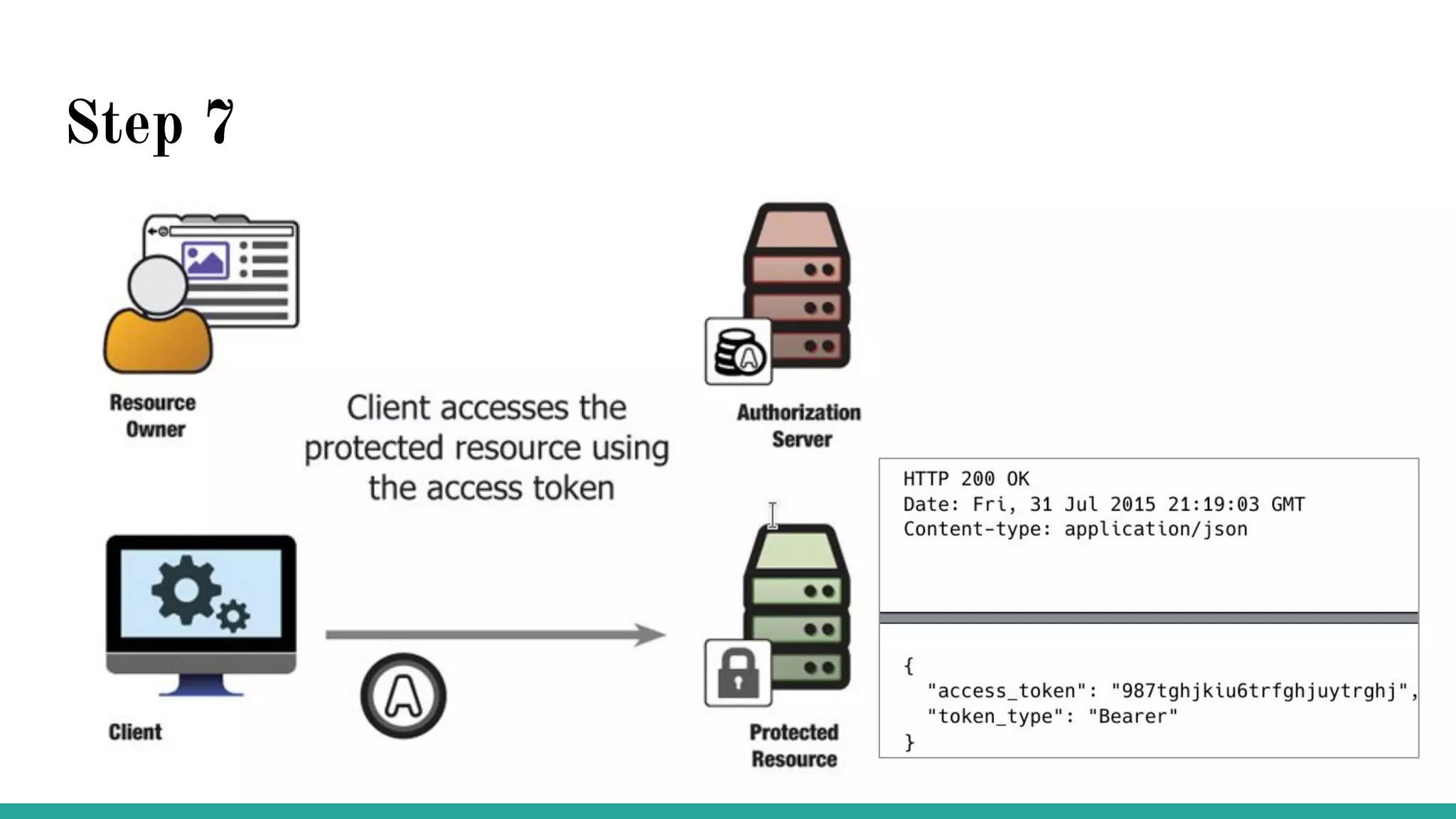
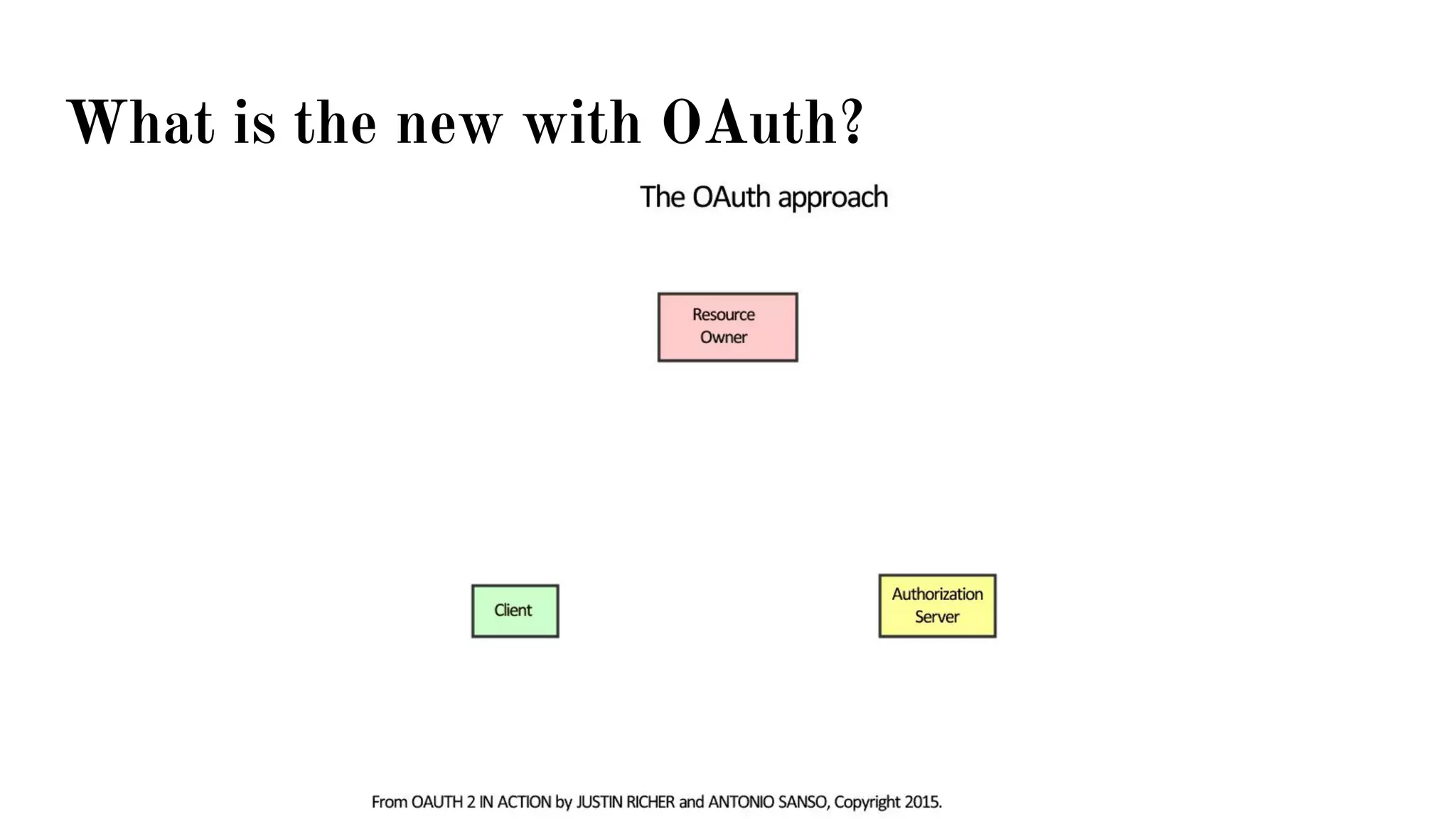
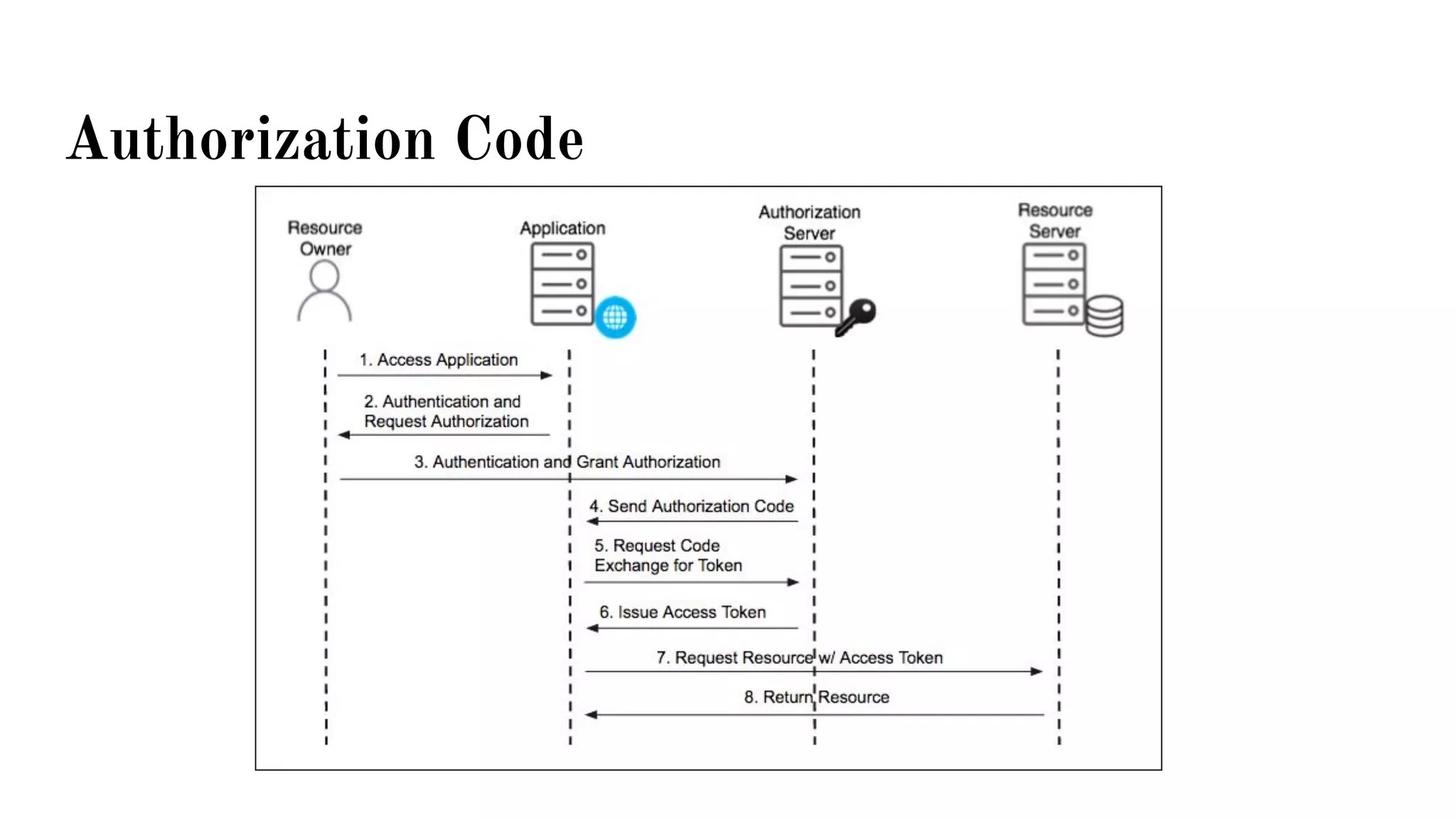
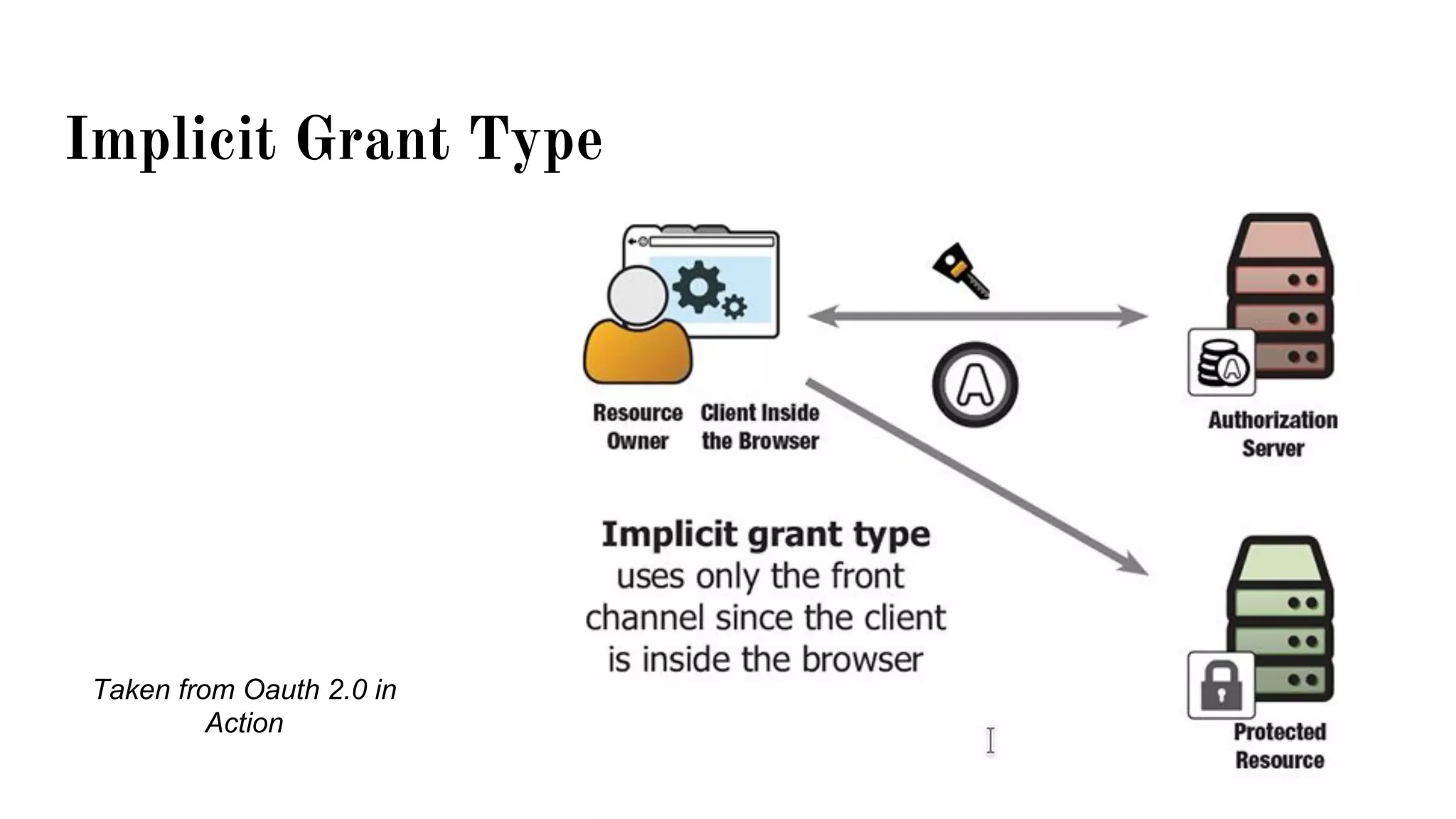
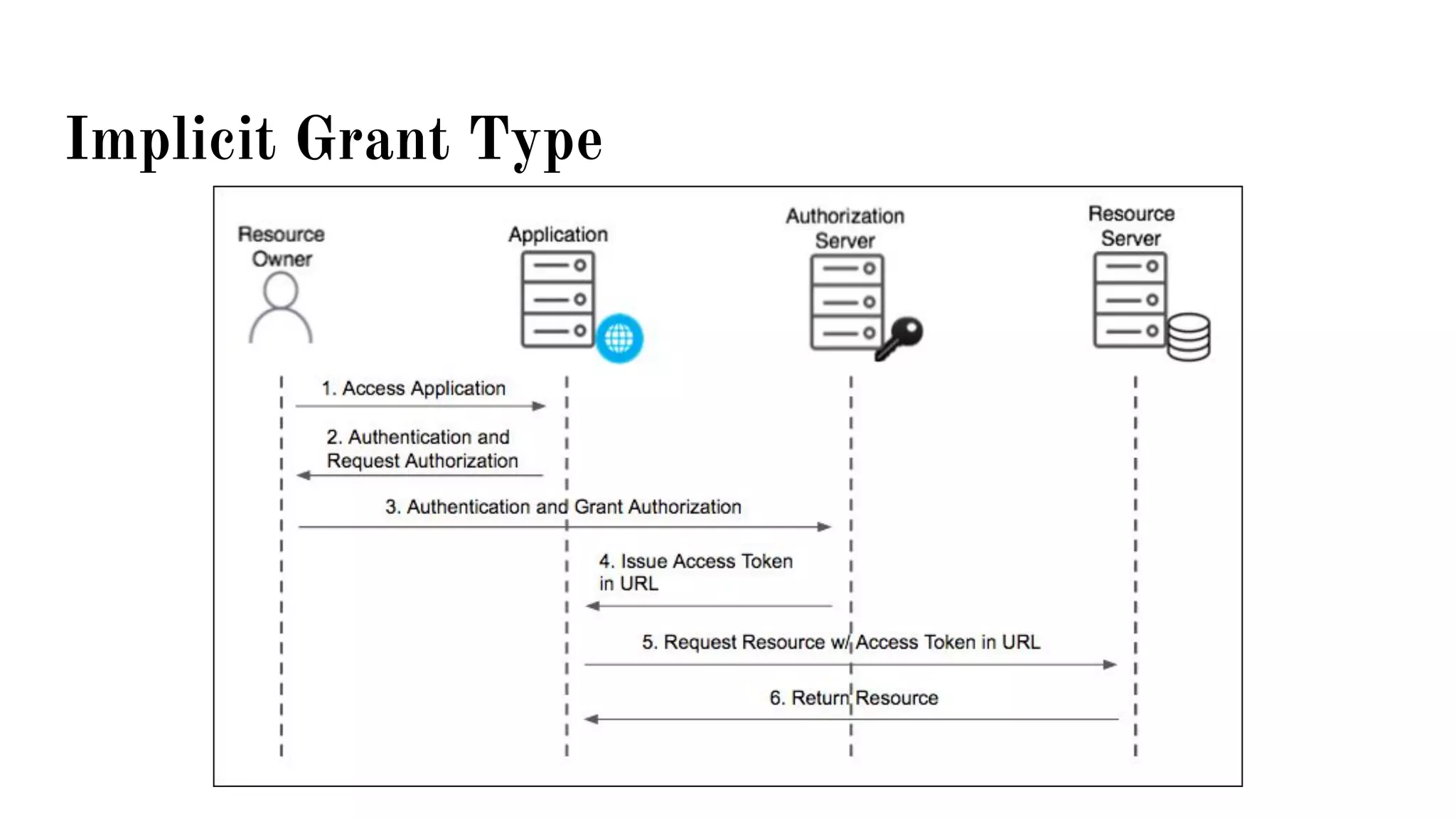
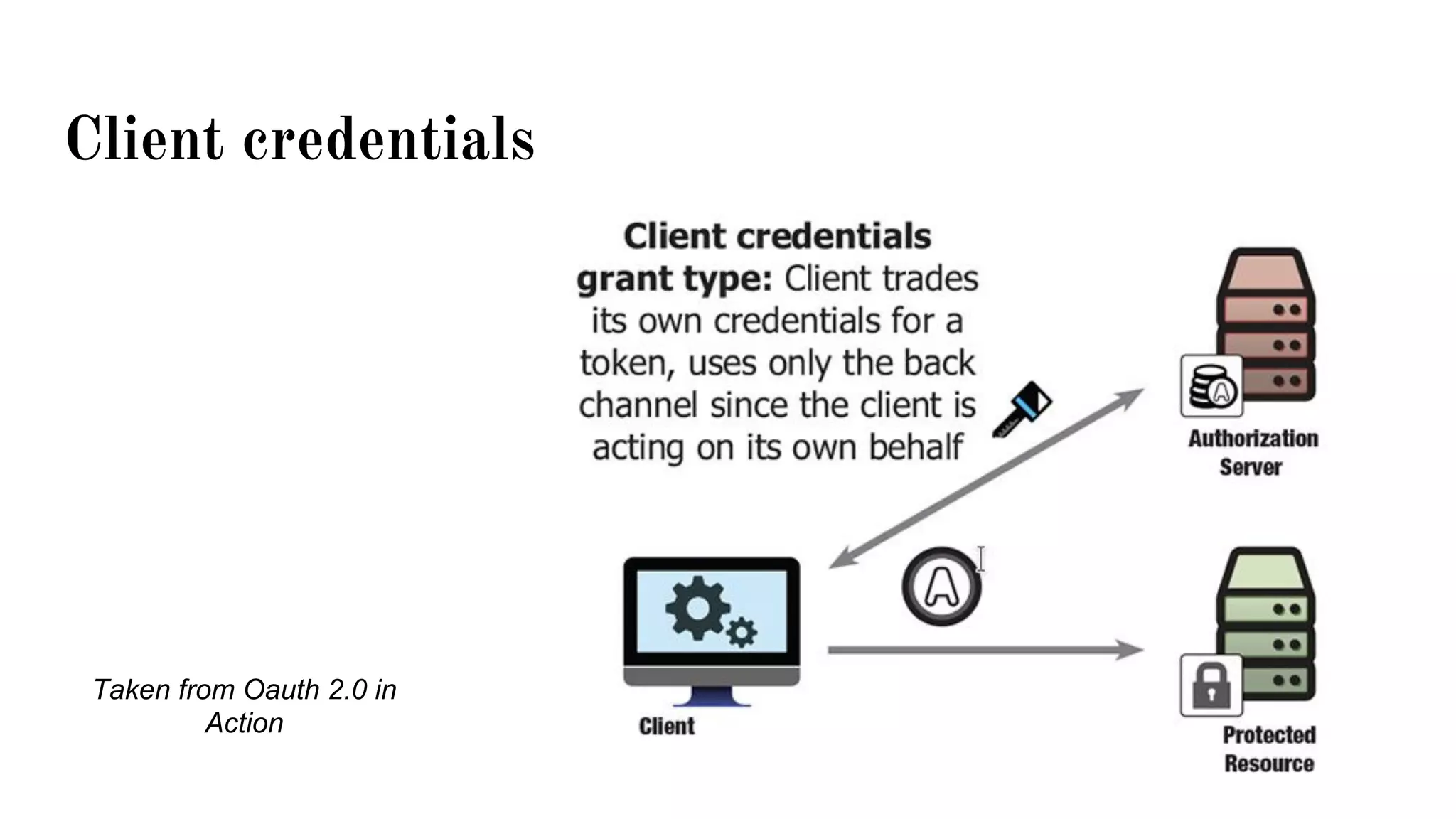
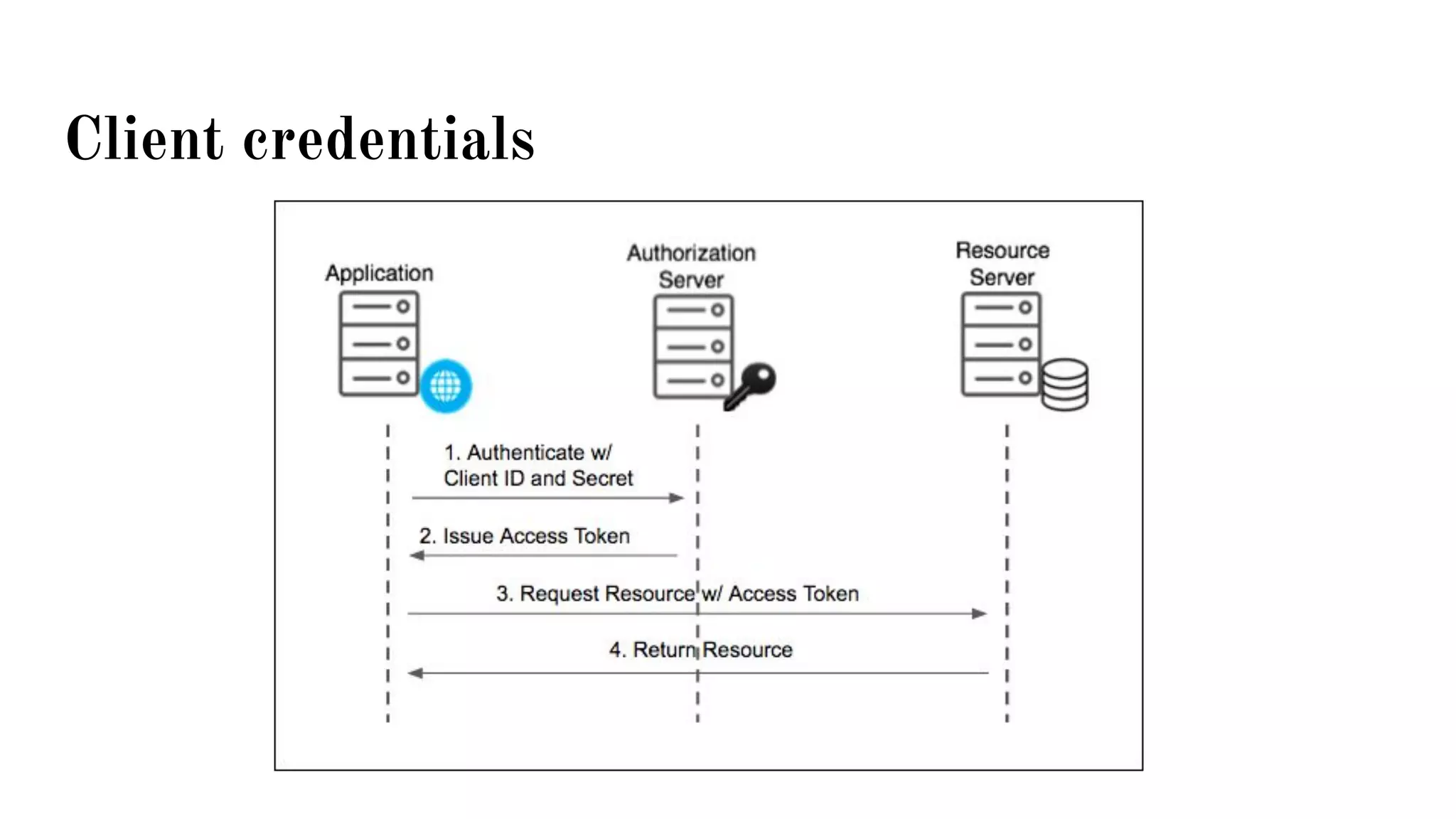
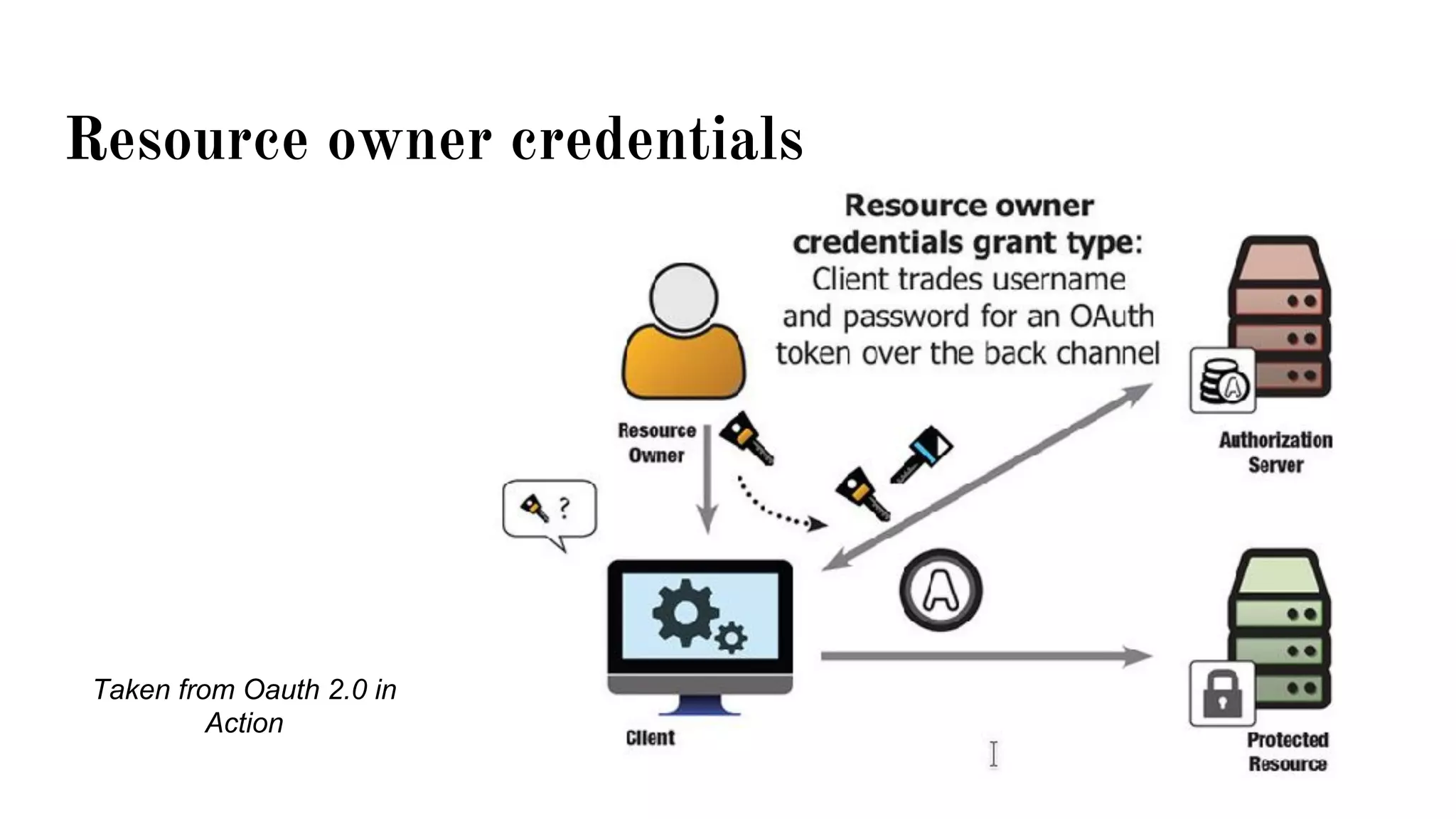
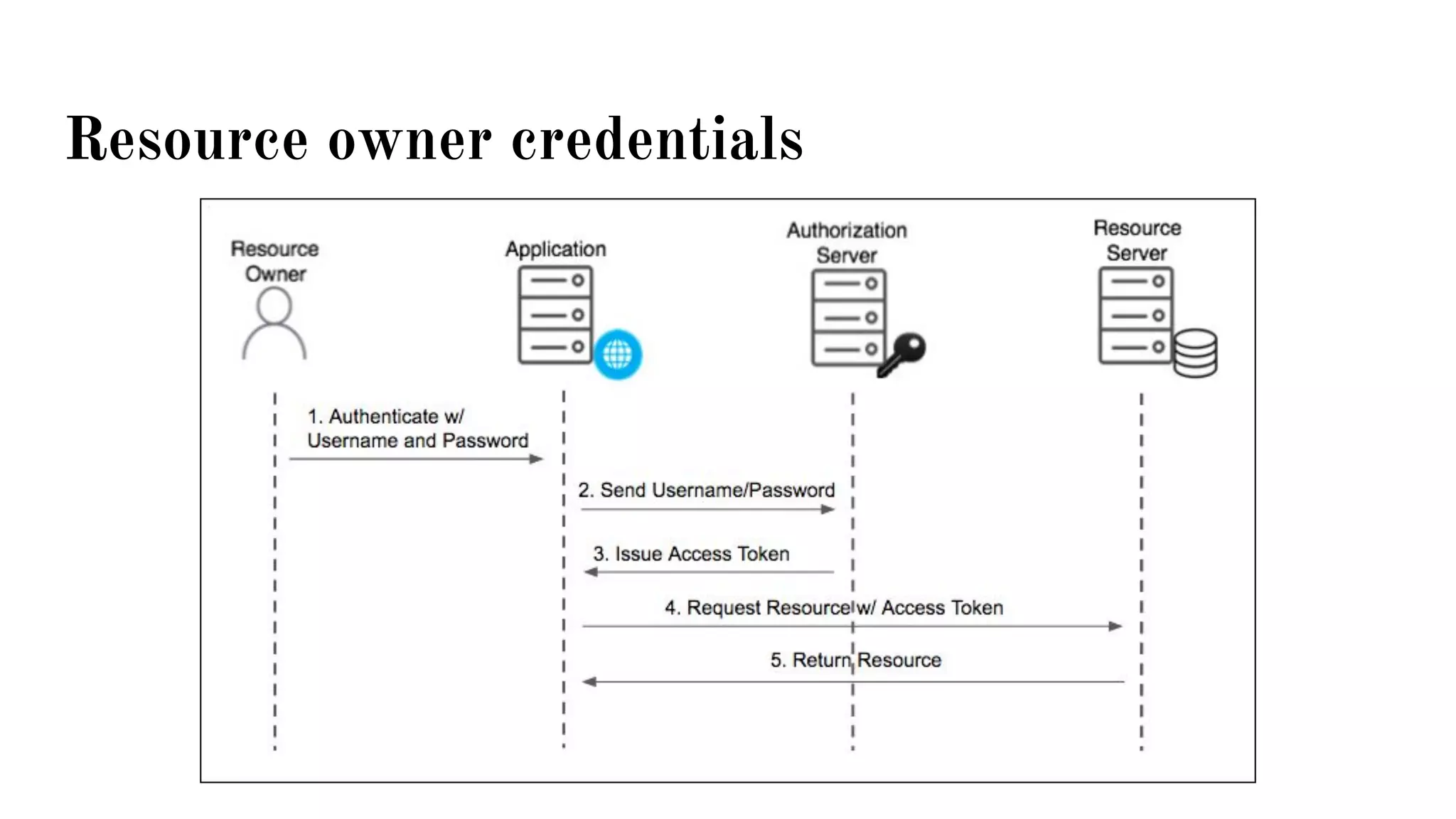
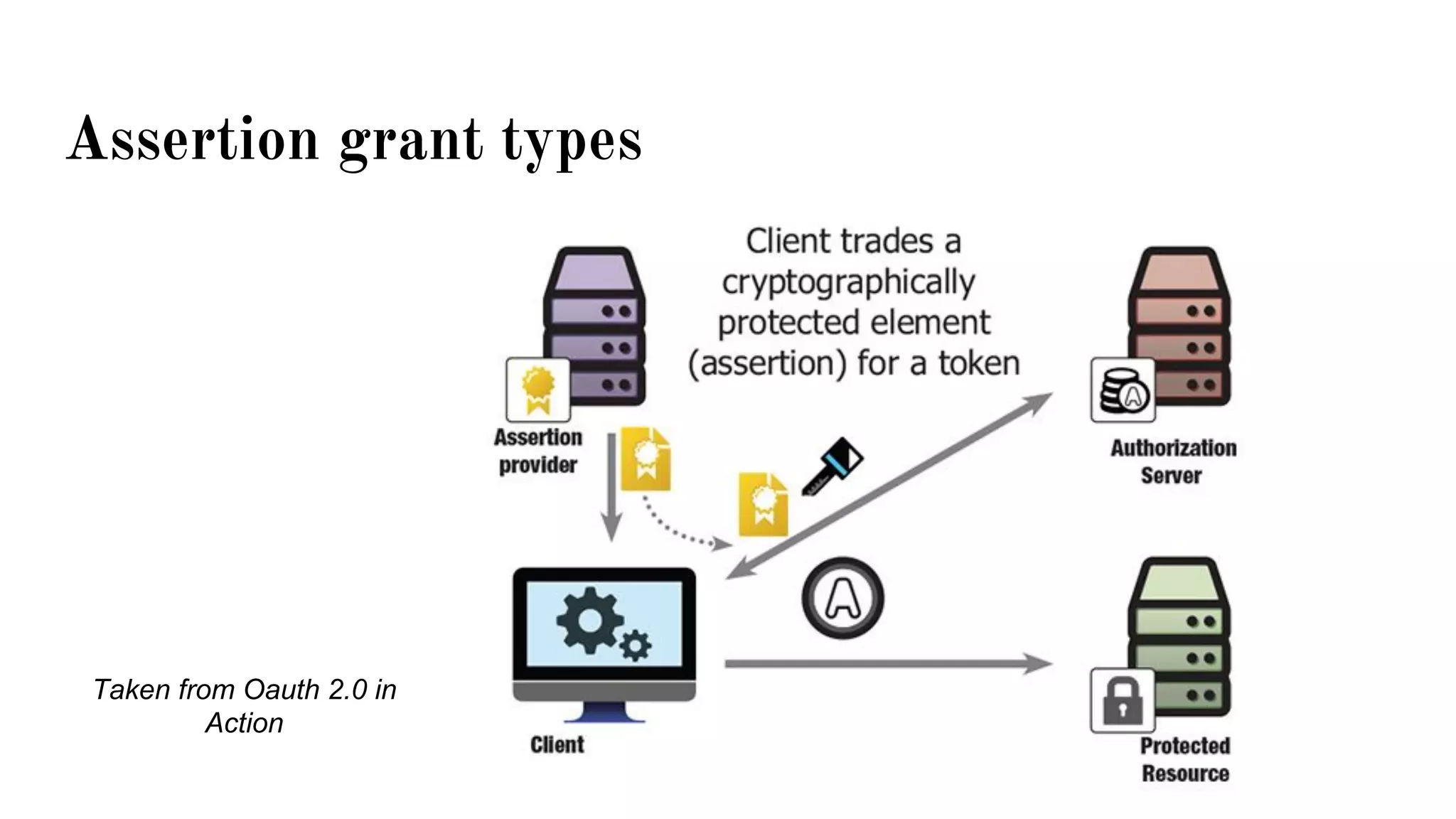
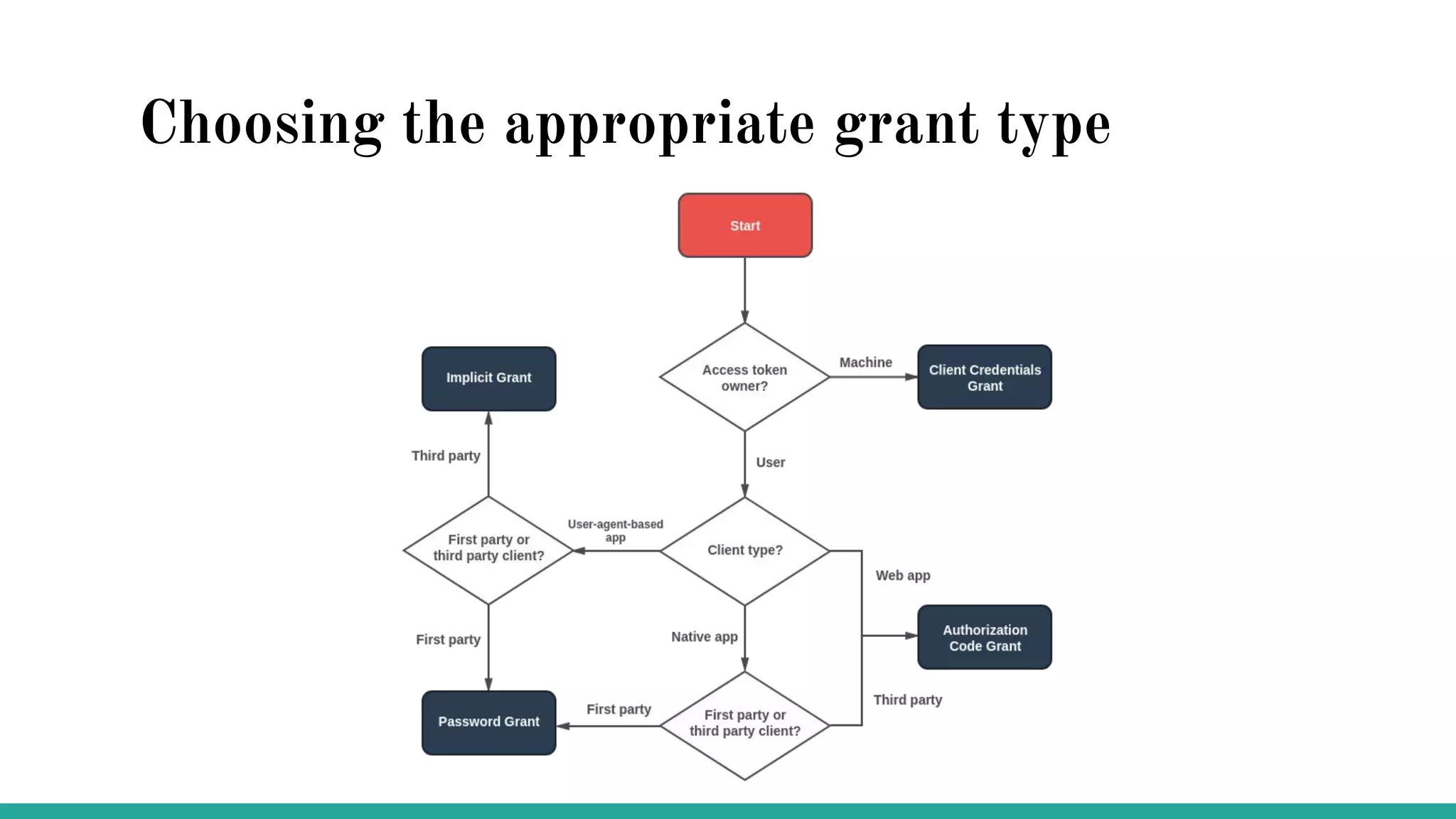
OAuth is a protocol that allows clients limited access to protected resources on behalf of a resource owner through delegated authorization. It addresses issues with directly sharing user credentials by using tokens issued by an authorization server to represent temporary and limited authorization to access a resource on behalf of a resource owner. The key components in OAuth are the resource owner, client, authorization server, and protected resource. OAuth uses grant types like authorization code, implicit, client credentials, and resource owner password credentials to obtain access tokens from the authorization server to access protected resources.