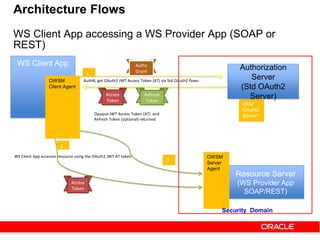
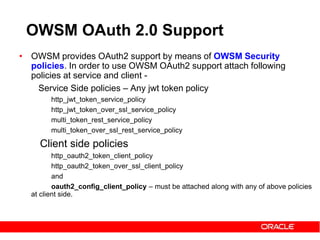
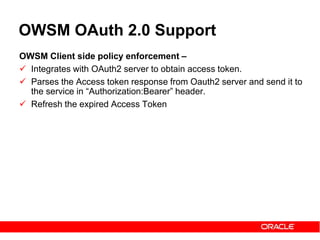
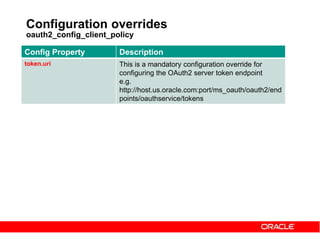
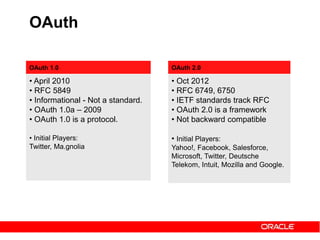
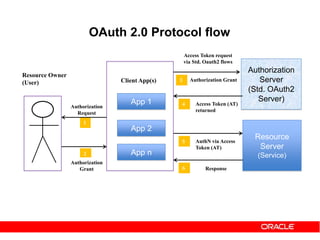
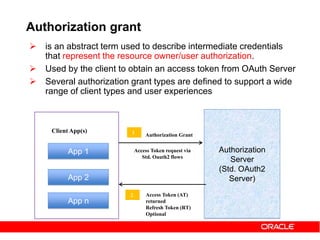
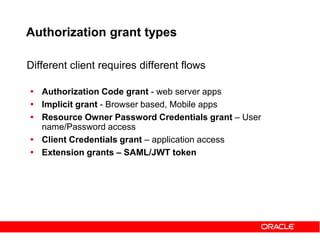
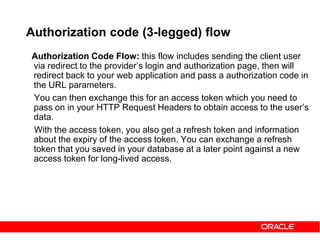
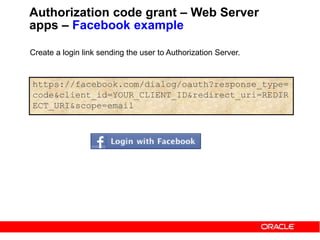
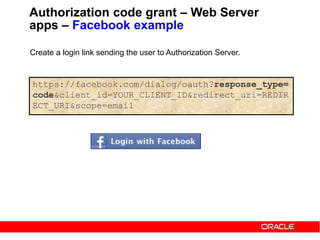
The document discusses OAuth 2.0 and how it addresses issues with traditional approaches to authorizing third party access to user accounts and resources. It provides an overview of OAuth 2.0 concepts like authorization grants, access tokens, refresh tokens, and the roles of the client, resource owner, authorization server and resource server. It then describes the authorization code grant flow and client credentials flow in more detail through examples. The goal is to explain how OAuth 2.0 works and how it can be used to securely authorize access to resources while avoiding the risks of directly sharing user credentials.



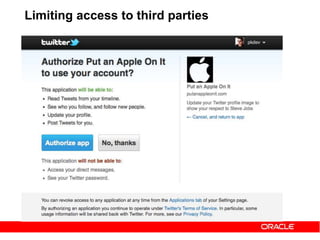
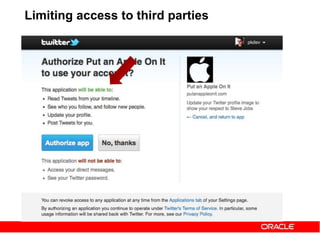
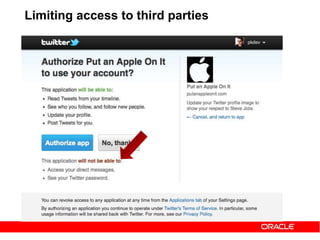
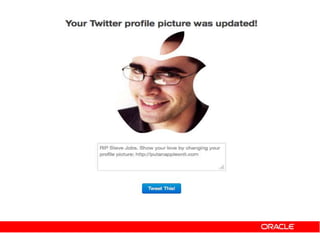





![https://example.com/auth?code=eyJhbGciOi[....... omitted for brevity]mljZUluc3RhbmNlMS5BTEwiLC
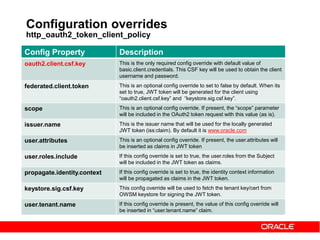
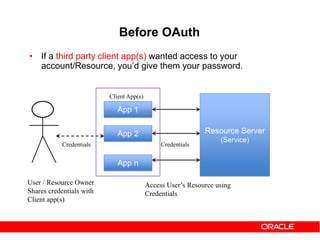
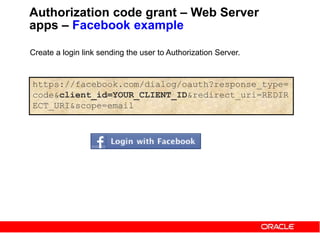
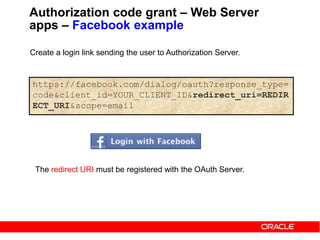
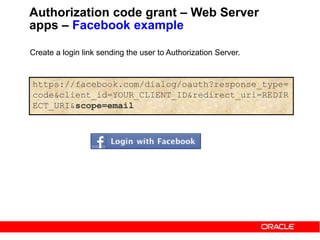
Authorization code grant – Web Server
apps
On success, user is redirected back to your site with auth code
POST /token HTTP/1.1
Host: server.example.com
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW
Content-Type: application/x-www-form-urlencoded
grant_type=authorization_code&code=eyJhbGciOi[....... omitted for brevity]mljZU
&redirect_uri=https%3A%2F%2Fclient%2Eexample%2Ecom%2Fcb
Client app sends Access Token Request to OAuth server
Here code is the authz code received from OAuth server.
grant_type must be authorization_code](https://image.slidesharecdn.com/29ba9b5f-6cb0-4b28-a2da-4ef46dc7e3a3-151014091335-lva1-app6892/85/Oauth2-and-OWSM-OAuth2-support-31-320.jpg)
![HTTP/1.1 200 OK
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Content-Type: application/json
{
"expires_in":604800,
"token_type":"Bearer","
“refresh_token":“ghtyhjh [...omitted for brevity...]FI“ ,
"access_token":"eyJhbG[...omitted for brevity...]FI“ }
Authorization server responds with Access Token in Response
HTTP/1.1 400 Bad Request
Content-Type: application/json;charset=UTF-8
Cache-Control: no-store Pragma: no-cache
{ "error":"invalid_request" }
In case of error Authz server responds with an Error Response](https://image.slidesharecdn.com/29ba9b5f-6cb0-4b28-a2da-4ef46dc7e3a3-151014091335-lva1-app6892/85/Oauth2-and-OWSM-OAuth2-support-32-320.jpg)
![HTTP/1.1 200 OK
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Content-Type: application/json
{ "expires_in":604800,
"token_type":"Bearer","
"oracle_tk_context":"client_assertion",
"oracle_client_assertion_type":"urn:ietf:params:oauth:client-assertion-type:jwt-bearer",
"access_token":"eyJhbG[...omitted for brevity...]FI“ }
POST /ms_oauth/oauth2/endpoints/oauthservice/tokens HTTP/1.1
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Authorization: Basic T1dTTUNsaWVudElkOndlbGNvbWUx
Host: 127.0.0.1:2001
Accept: text/html, image/gif, image/jpeg, */*; q=.2
grant_type=client_credentials
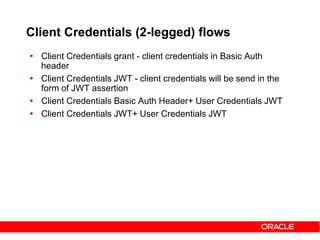
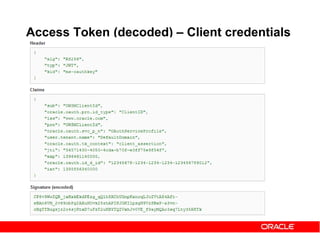
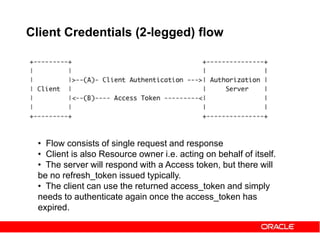
Client Credentials grant – Basic Auth
Access Token Request -
Access Token Response](https://image.slidesharecdn.com/29ba9b5f-6cb0-4b28-a2da-4ef46dc7e3a3-151014091335-lva1-app6892/85/Oauth2-and-OWSM-OAuth2-support-34-320.jpg)