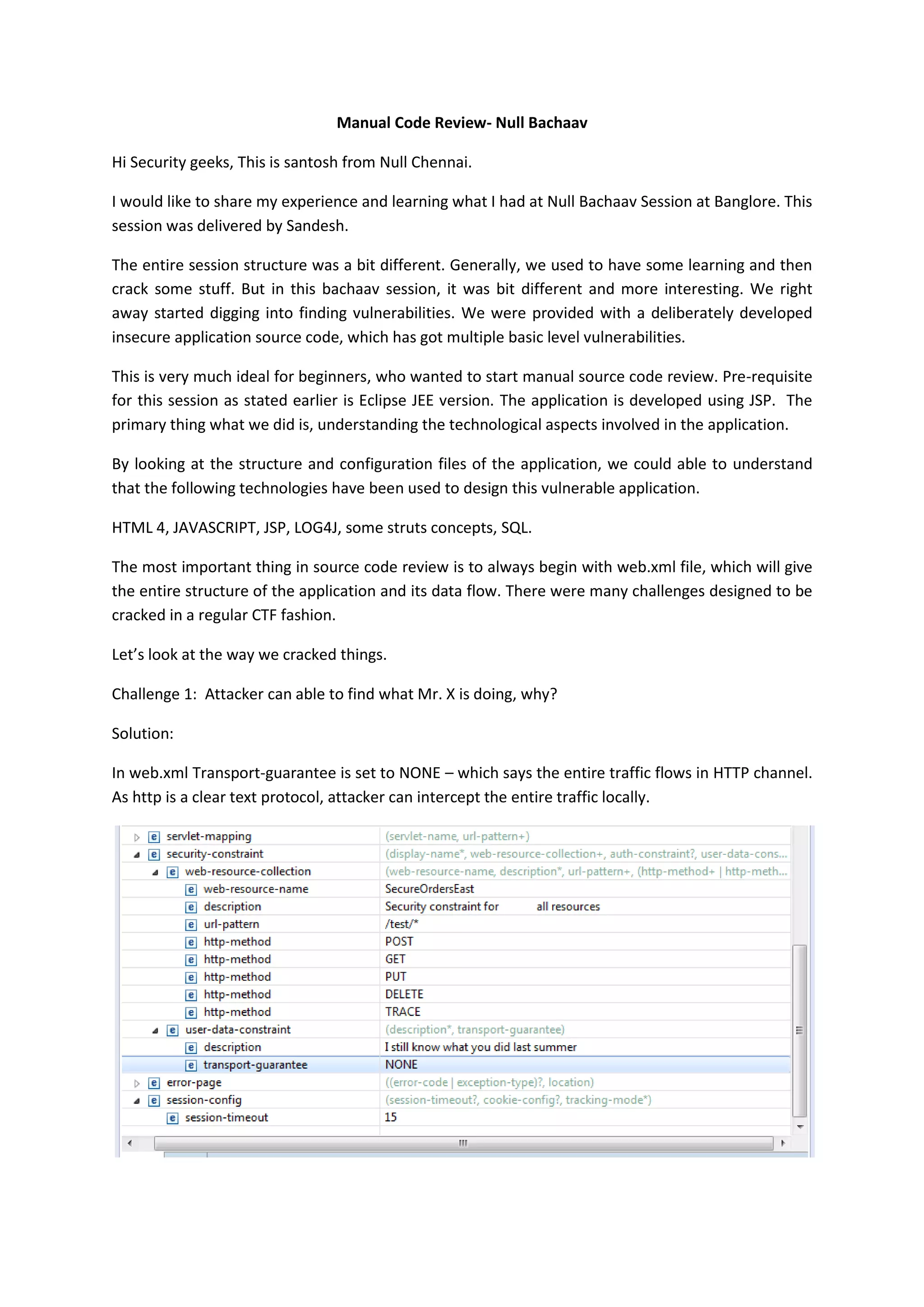
The document summarizes a manual code review session where attendees analyzed vulnerabilities in insecure application source code. The session involved multiple challenges where attendees had to find vulnerabilities like intercepting HTTP traffic, error code disclosure, sensitive data exposure, password hash cracking, XSS filtering bypass, insecure redirects, log injection, privilege escalation via cookie tampering, and lack of CSRF protection. The document outlines solutions and observations for each challenge that demonstrate vulnerabilities in technologies like JSP, Log4j, password hashing, and lack of defenses like input validation, access control, and TLS.