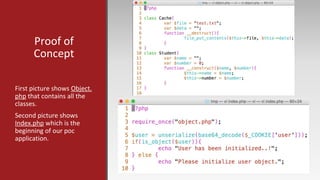
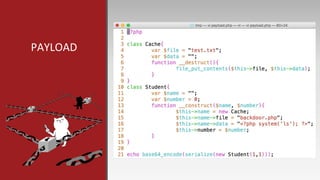
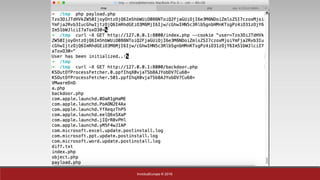
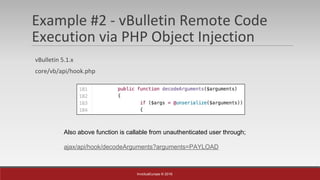
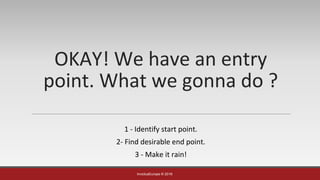
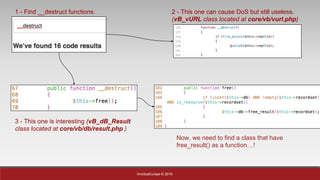
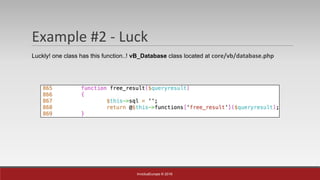
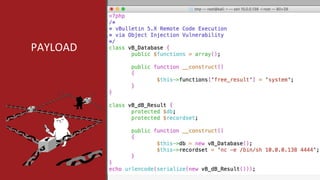
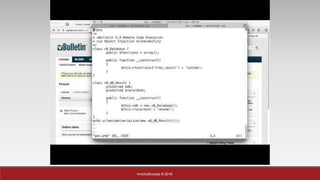
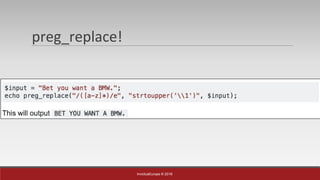
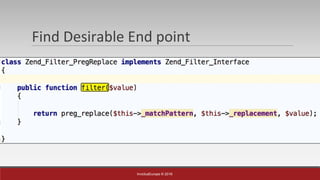
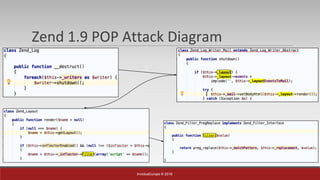
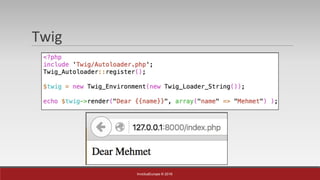
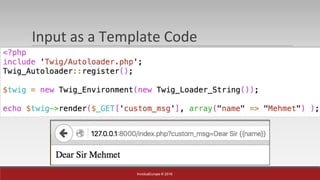
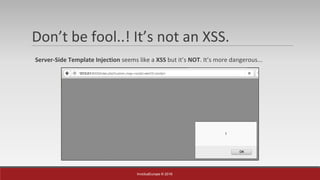
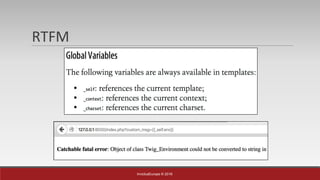
The document is a presentation by Mehmet Ince, a senior penetration tester, discussing web application frameworks and security practices. It highlights the importance of secure coding, risk assessments, and methodologies to prevent vulnerabilities such as SQL injection and PHP object injection. The document emphasizes the need for regular updates, validation of input, and secure deployment practices to safeguard applications.






![InvictusEurope © 2016
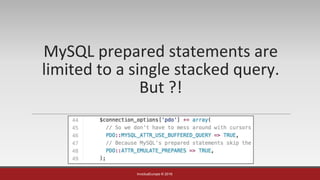
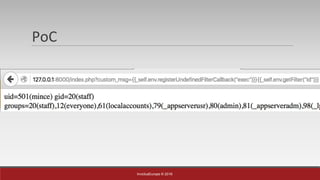
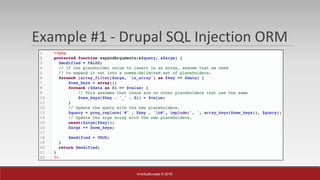
Example #1 - Drupal SQL Injection ORM
User input is array E.g : ids[]=1&ids[]=2&ids[]=3](https://image.slidesharecdn.com/without0day-breakingtheframeworkscore-160522112353/85/Breaking-The-Framework-s-Core-PHPKonf-2016-10-320.jpg)
![InvictusEurope © 2016
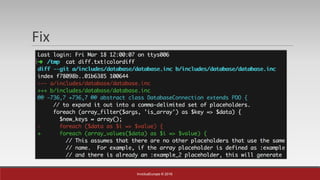
Example #1 - Drupal SQL Injection ORM
User input is array E.g : ids[0); DROP TABLE foo; --]=1&ids[]=2](https://image.slidesharecdn.com/without0day-breakingtheframeworkscore-160522112353/85/Breaking-The-Framework-s-Core-PHPKonf-2016-11-320.jpg)